-
Notifications
You must be signed in to change notification settings - Fork 1
Report
Table of Contents generated with DocToc
- Abstract
- Introduction
- Background
- Design
- Implementation
- Testing and Analysis
- Conclusion
- References
Security is a major concern in the modern day and age. A number of defensive techniques are used in order to secure your data from attackers. This project aims to focuses on providing the user with data integrity and non-repudiation. It does so by taking hash of all the files inside a folder, storing them inside a JSON (JavaScript Object Notation) file and then encrypting them with public key cryptography. This application has several other modes to provide simpler functionality when the additional security is not required and what required is a faster way to hash all your files. For hash MD5, SHA1, SHA256 and SHA512 are used and for encryption AES and RSA is utilized. The intention is to make application easily available on all popular operating systems and easily usable.
OS (Operating Systems) are the programs which are responsible for the functionality of your computer. At the core of the OS lies a computer program which is responsible for establishing communication between the software and the hardware of your computer known as the kernel. With the help of kernel, the OS reads and writes data to your storage drive in form of files. These files on a disk are then organized with the help of directories which may consist of multiple directories or files inside them effectively forming a tree of directories.
The issue is that these files are susceptible to data corruption due to some hardware issues or forced by a person trying to compromise the integrity of our files. Some examples of data corruption caused without the involvement of a third party possessing ill intent consist of data corruption due to networking issues, removal of removable storage while still being in usage or physical damage to storage drive. These are files also susceptible to undesired data alteration by an attacker, a person who intends to expose, alter, disable, destroy, steal or gain unauthorized access to or make unauthorized use of an Asset.
A simple way to make sure your files did not lose their integrity is to utilize hashing functions. A hash function is a function which maps data of arbitrary size to that of a fixed size. This data of fixed size is known as a Hash. The hashing function always generates the same hash for every instance of same data provided to it.
Now the issue we face with hashes is that they consist of very random combinations of characters. For example, the MD5 hash, which is quite an old and vulnerable hash, of the string 12345 is the following:
827CCB0EEA8A706C4C34A16891F84E7B
Due to its randomization it would not be possible to memorize these hashes and currently used hashes being much larger than length as compared to a MD5 hash further removes any possibility. Thus they are usually stored in files. Now this can be used to detect unintentional corruption of our data which we took the hash of.
With this we solved the issue of detecting unintentional data corruption but an attacker can still easily fool the user. Consider a directory which contains data.txt which contains some data and hash.txt which contains hash of data.txt. Now let's say an attacker wants to modify the contents of data.txt while still fooling the user into thinking that has data's integrity has not been compromised. All the attacker now has to do is after he modifies data.txt into his desired data he will take hash of data.txt and now he places this hash inside hash.txt. Now when the user will check for integrity he will think that the data did not lose its integrity when in fact integrity has now been lost.
Now the solution which will utilize to solve this problem in that we will now encrypt the hash.txt so that the attacker is no longer able to edit the hash of data.txt.
We also encounter another relatively smaller problem if we want to verify the integrity of multiple files which is that it can be a very time exhaustive process to manually take hash of each and every file and then also verify it one at a time.
In order to solve this problem, we make use an automated function provided by the application which will recursively traverse the file tree and calculate the hashes of all files existing and keep them inside a JSON file. And then at the time of verification using this JSON file to verify the integrity of all the files consisting inside the directory.
In the current age of technical advancements, the most valuable resource is digital data. It is due to this fact that it is very important to ensure the integrity of this digital data. Integrity is the quality of digital data which means that it has not lost its true form. The process used to verify the integrity of a file is known as file verification. The most common form of file verification consists of utilizing hashing functions.
Attackers aim to compromise other people's data in order to get their desired outcome. There are 3 basic types of attackers.
- Who do it for fun
- Who do it to gain financial advantage
- Who do it to impact society
Our goal is to be able to identify if they altered the data or not.
A hash function is a function which maps data of arbitrary size to that of a fixed size. This data of fixed size is known as a Hash. The process of converting data into hash is known as hashing. The hashing function always generates the same hash for every instance of same data provided to it.
An ideal cryptographic hash function has five main properties:
- It is deterministic so the same message always results in the same hash
- It is quick to compute the hash value for any given message
- It is infeasible to generate a message from its hash value except by trying all possible messages
- A small change to a message should change the hash value so extensively that the new hash value appears uncorrelated with the old hash value
- It is infeasible to find two different messages with the same hash value
Encryption is the method by which plain text or any other type of data is converted from a readable form to an encoded version that can only be decoded by another entity if they have access to a decryption key. Encryption is one of the most important methods for providing data security, especially for end-to-end protection of data transmitted across networks.
This process is done by utilizing one or more keys and then passing these and the data to encrypt to an encrypting algorithm, known as ciphers, which in turn will give us with encrypted data also known as cipher text.
In order to read this cipher text, we now have to reverse encryption, which is also known as decryption. In order to successfully perform decryption, we need both the cipher text and the key utilized.
There are two major types of ciphers:
- Symmetric Key Ciphers: They utilize a single key commonly referred as "Secret Key" in order to encrypt plain text. The same key is required for decryption too. Common example of Symmetric Key Cipher is that of AES (Advanced Encryption Standard) which was designed to protect government classified information.
- Asymmetric Key Cipher: Utilizes two different but mathematically linked keys, one public and one private. The public key can be shared with everyone, whereas the private key must be kept secret. Both these keys can be used to encrypt and then you have the utilize the other key for decryption. The most common algorithm of this type is RSA.
This project is designed such that it can easily provide the facility of file verification on all major operating systems. The base functionality is taking the hash of all the files inside a directory recursively and then storing them inside a JSON file and then later using this file to check the integrity of the files.
The base functionality can be split into two use cases which are explained below.
The first use case is to generate the hashes of all the files inside a directory and then save these into a JSON file so that we can verify the integrity of these files later.

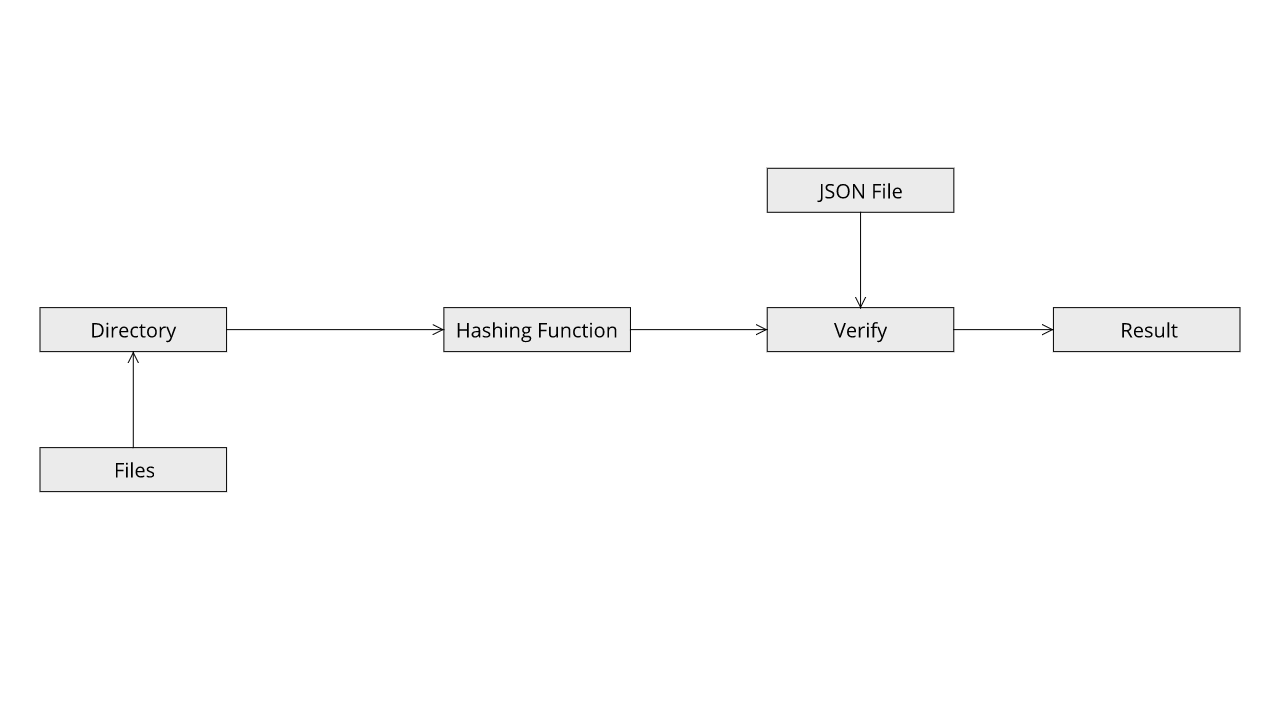
The second use case is to take the hash of all the files inside the directory again and compare them all to the hashes previously stored inside the JSON to verify file integrity. The result will tell if the files are OK or damaged.
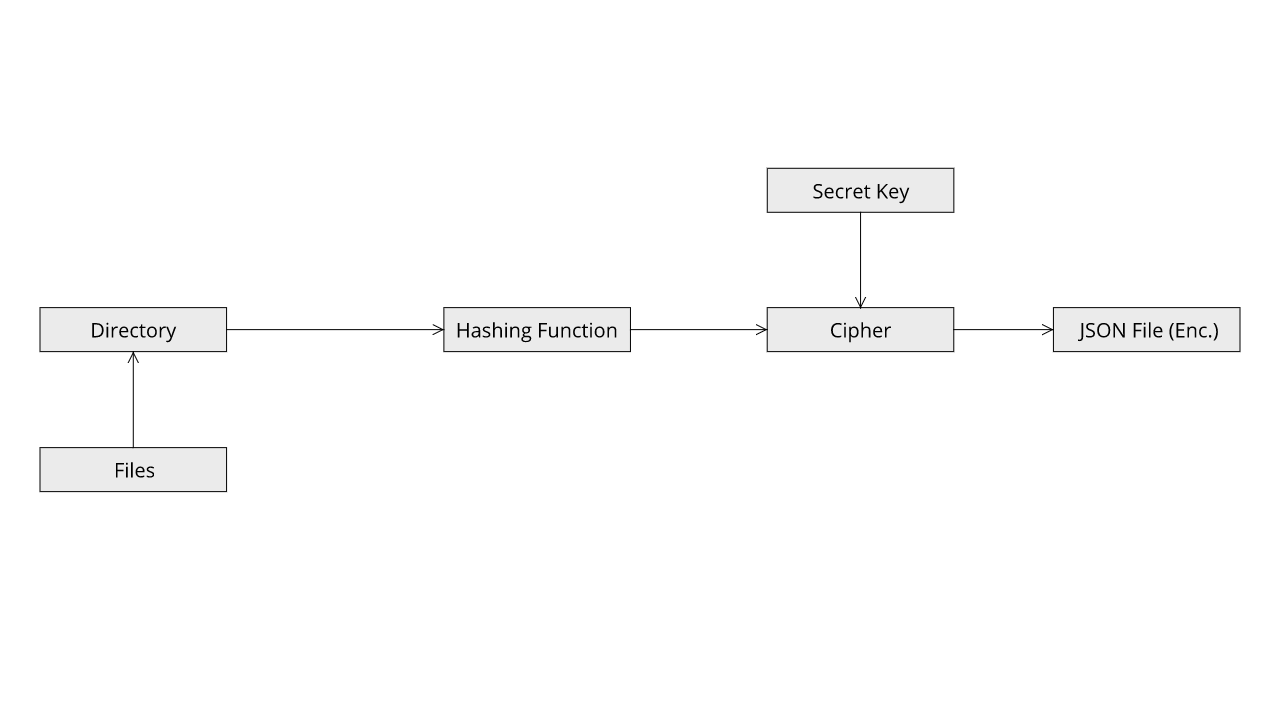
This mode expands on the base functionality of the application and encrypts the JSON File produced in the end so that it cannot be altered by an attacker.
The first use case in this mode is that we store hashes of all the files in a directory so that we can later use it to verify the integrity of the files while also making sure that no one is able to alter the contents of the JSON File. This is achieved by encrypting the JSON File.
The second use case in this mode is to verify the integrity of all the files in the directory use the previously generated Encrypted JSON File. To do this we first we have to decrypt the JSON File and then compare all the hashes.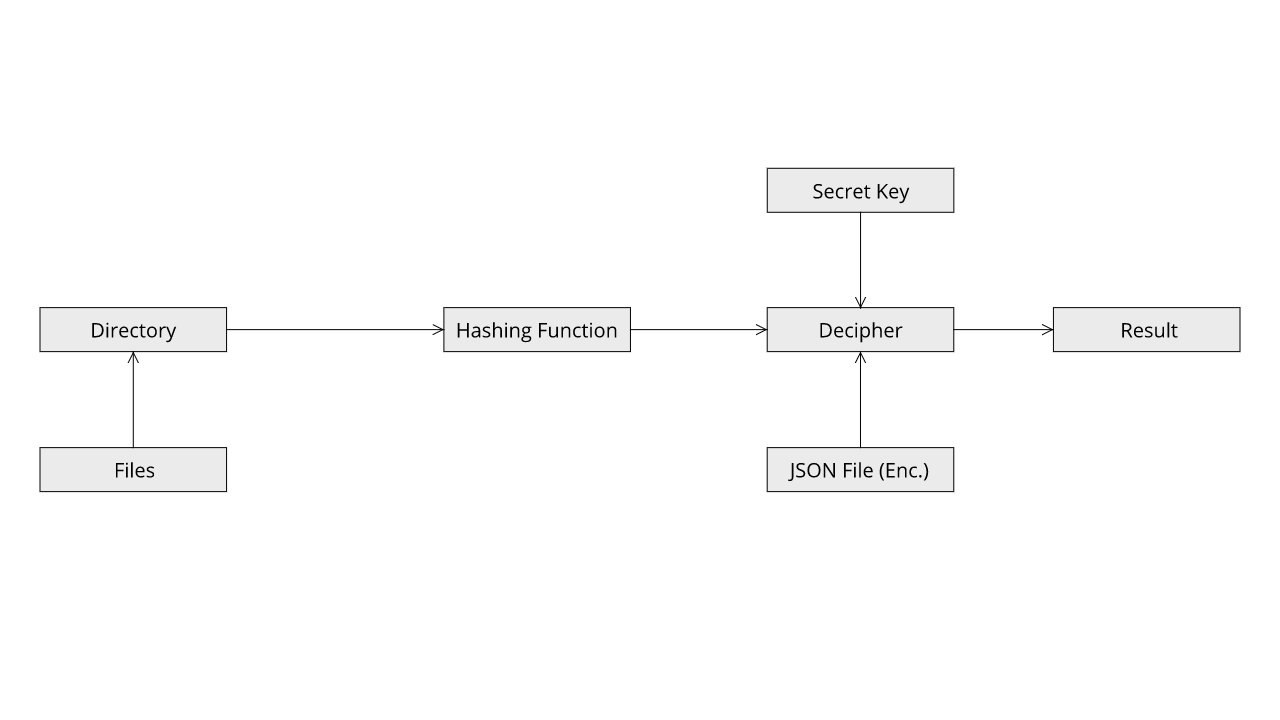
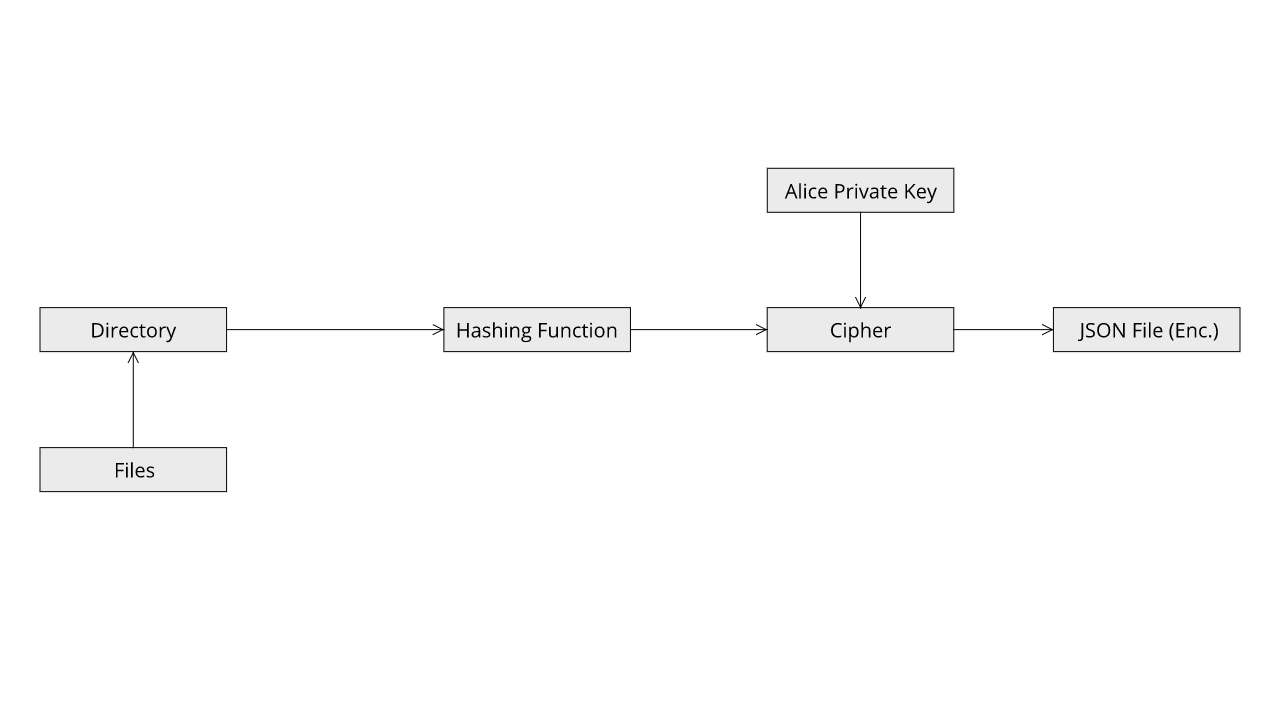
The mode is to be utilized when there are multiple parties that want to share data while making sure that they do not lose file integrity. Let us consider the two parties Alice (A) and Bob (B). Alice wants to send data to Bob and does not wants to go through that hassle of sharing a secret key. In this case all she has to do is that she will encrypt the JSON using her private key and send the data along with the JSON file to Bob.
Now that Bob has received the data and the JSON file which was encrypted using Alice's Private Key. He needs to have the public key of Alice in order to first decrypt the JSON file and then compare the hashes. The advantage provided by this mode is that Bob can safely assume that the sender of these files was Alice while also making sure no one altered the hashes.
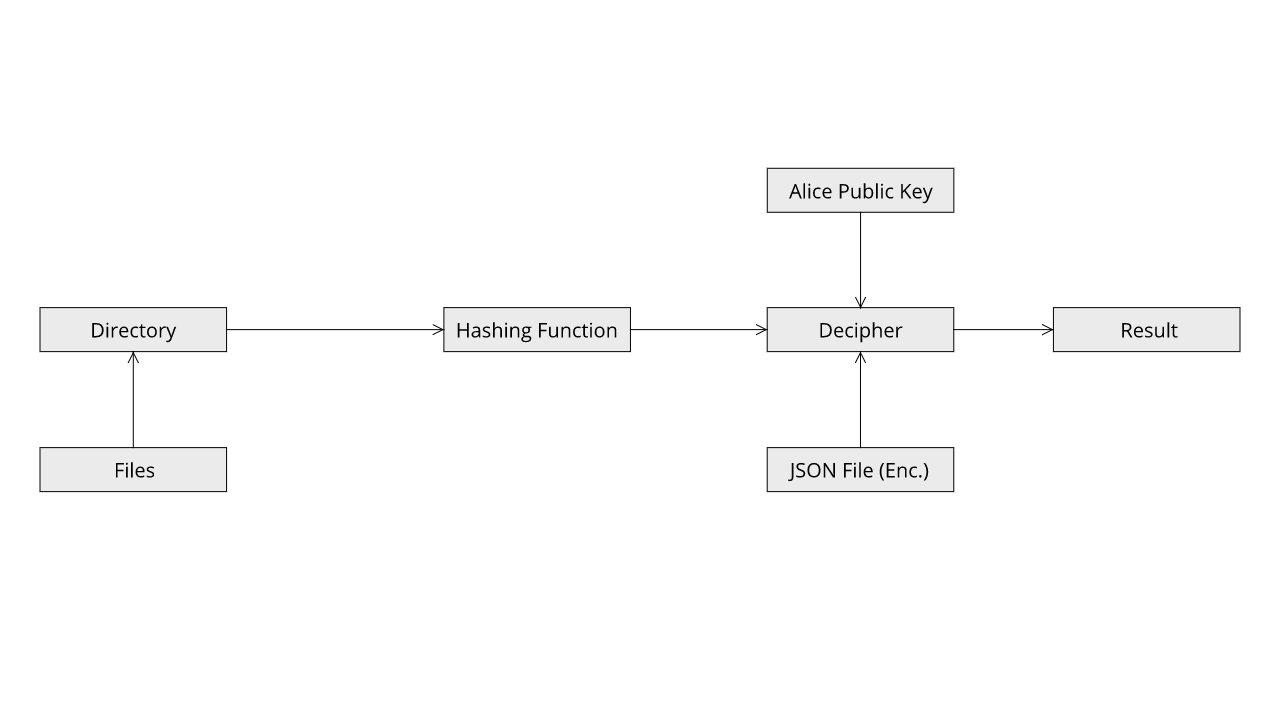
This is the most secure mode available in the application. It makes sure that both parties know who will be receiving and sending the data.
In this use case Alice also want to make sure that receiver of the hashes in no other than Bob himself. In order to achieve this task, she will provide the application with the directory which contains the files to hash along with her private key and Bob's Public Key. The application will first encrypt the generated JSON file with Alice's private key and then with Bob's Public key.

Now Bob has received the encrypted hashes and the data he wants to verify. In order to verify then files he first needs to decrypt is hashes. In order to do this Bob has to provide the application with his Private key and Alice's Public key. The application will first decrypt the hashes using Bob's private key and then decrypt the result using Alice's Public key. Then this decrypted JSON file will be used to verify the files.
This section will go through the different parts of the application and explain how they were implemented. The main language utilized to program this application is Node JS which was utilized on top of Electron. Electron is a very powerful frameworks which utilizes the well-known Google Chrome's Open Source version known as Chromium and Node JS and builds cross platform applications.
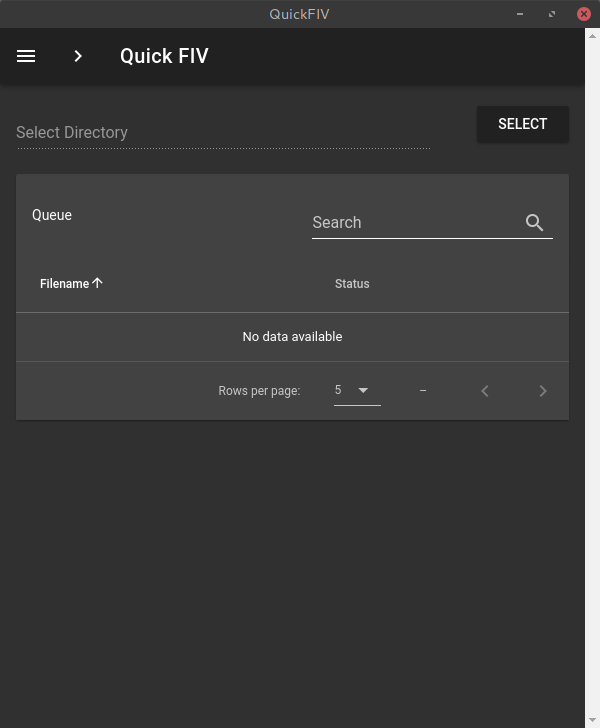
The first thing the user looks at when he opens the application is the user interface. This user interface is implemented using Material UI Framework called Veutify and JS Framework Vue.js.
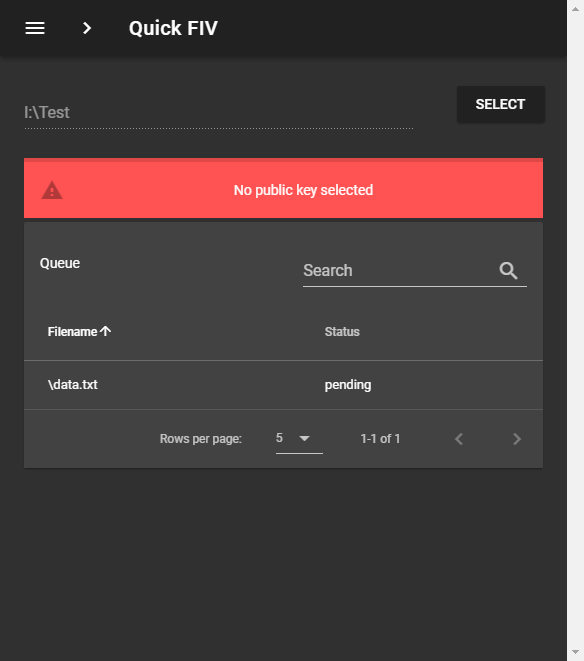
The home page consists of a Select button and a table which is used to display data later on. The below image shows us how the application looks when no work has been done.
After we have selected a directory and application completes its processing the table gets populated and the a notification telling the user that the operation is completed is shown.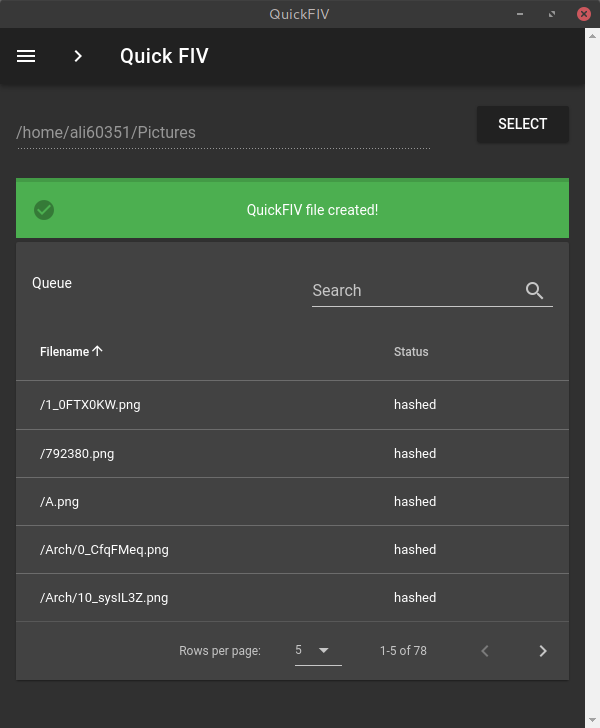
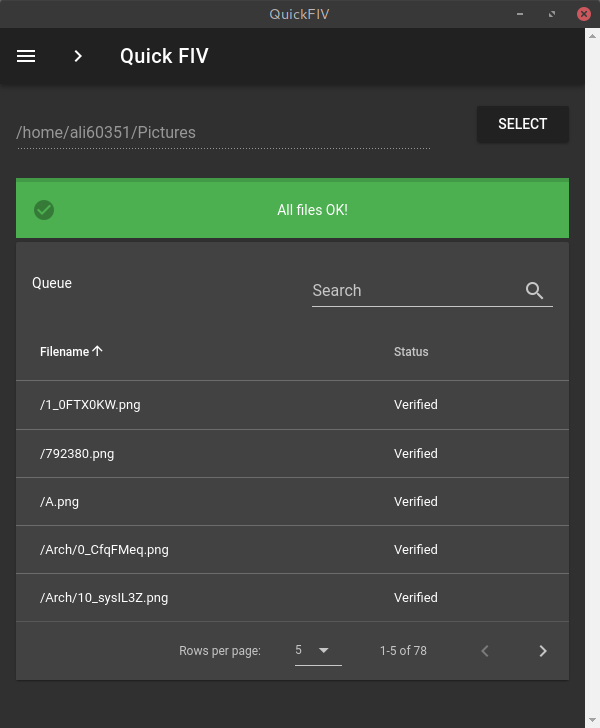
The settings page is where the user can select different modes and algorithms and generate a public key pair if he requires one.
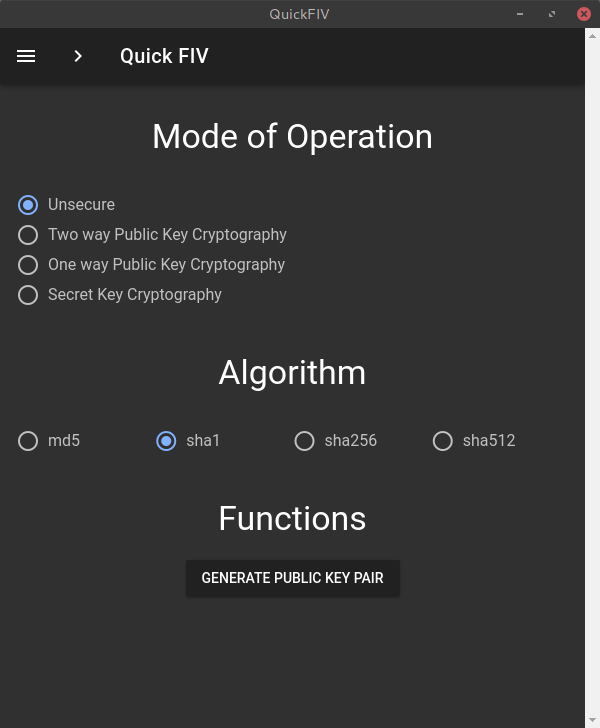
The basic functionality is split into two parts as told previously. Before a task can be classified we have to wait for the user to select a directory after he presses the select button. Then this selected directory is analyzed if it contains a file named QuickFIV.json or not. If the file exists, then we enter the Hash Verification mode and Hash Generation mode otherwise.
For the purpose of demonstration, we will use a directory named Test which contains a single file named data.txt.
After we select this directory in the application it uses File System Module of Node JS to read the directory recursively and since in this case our directory doesn't contains a QuickFIV.json, it will enter Hash Generation mode. After this we utilize an open source module known as hash-files which is available to the public via Node Package Manager at hash-files. Now we configure the module to hash in the user's selected Hashing Algorithm as shown in the UI above. The available choices are MD5, SHA1, SHA256 and SHA512. In this case we are using the default algorithm which is SHA1. For our directory the application will generate a file named QuickFIV.json whose contents will be like this.
[
{
"file": "/data.txt",
"md5": "",
"sha1": "58d3f35ebda104f0cc7ff419cc946832154581fc",
"sha256": "",
"sha512": ""
}
]Since our directory only contained a single file we only have a single object inside the array. The object contains 5 properties as visible. The first one being the file property which tell the path of the file relative to the directory selected. The rest 4 properties being the hashes of the file. As in this case we only took the SHA1 hash, only that property is populated.
If we select the same directory again the application will assume that we want to verify the files present in the directory since it now contains a file named QuickFIV.json. Now just like the other mode this mode will also utilize hash-files and Node File System Module and gather the hashes of the files inside the directory. Now it will compare this computed hash to the ones stored in the QuickFIV.json and tell if they are same or not. In order to demonstrate how errors are handles in basic procedure I edited the contents of data.txt and added a new file named new.txt after the hash was computed.
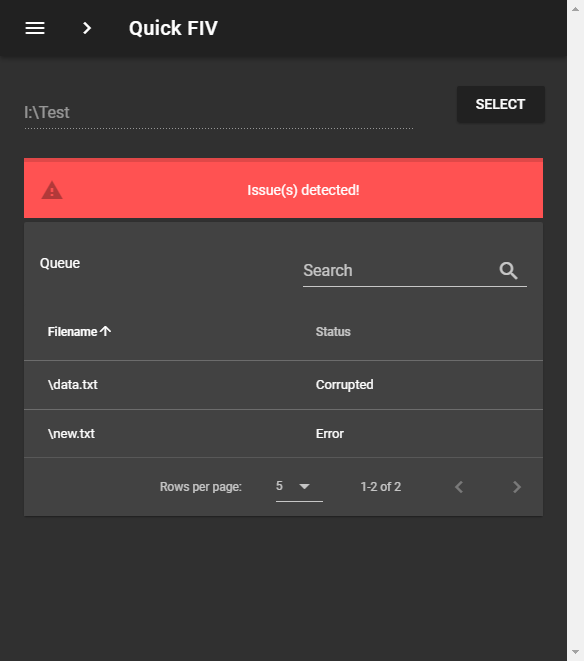
We can see application is telling that data.txt is Corrupted and giving an error next to new.txt since it wasn't hashed before. If nothing is disturbed, then we see something similar to the window below.
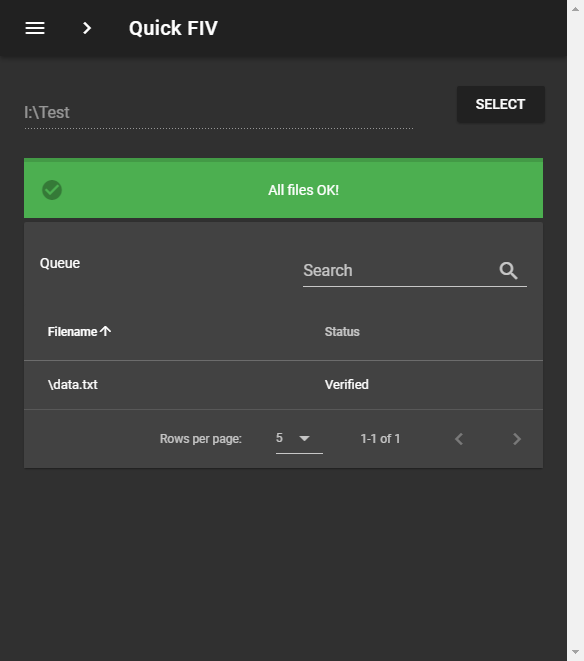
This mode builds upon the base functionality and provides the facility to encrypt the QuickFIV.json so that no one is able to successfully change the hashes unless he knows of the secret key used. The QuickFIV.json is very likely to get destroyed if altered. A slight UI change is also made when this mode is activated.
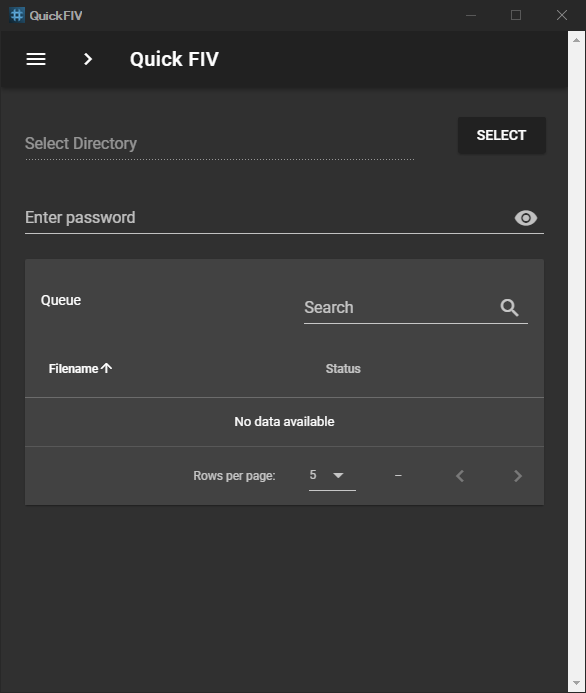
Now we have a new text input which the user will use to input the secret key. The user is required to input the secret key before he selects the directory.
After following the base procedure defined inside the Base Functionality (Unsecure Mode) the application will utilize the crypto-js module and import AES algorithm from it. Then using this AES algorithm and the secret key provided inside the UI, the QuickFIV.json will be encrypted and look like this when opened in a text editor.
U2FsdGVkX1/KKtPKP4PPtdeJ0/S4vlEJFx6Apwj7N9B4x+KVqf+Tp0Bk6sFlgfve0AKs/JOeyOcTfXVml737+wIh8EPbTxcGc7zYu8emZ+XKnmDB69gGO5gGVYi9FTwb/38B5JGBuJze6tWUMc5yfD0PIPc0OZxydAHElGcLsrs=
In addition to the unsecured mode the user now has to provide the application with a secret key in order to first decrypt the QuickFIV.json and then if the secret key entered is correct the usual verification will be carried out. If the key is incorrect an error message will be displayed.
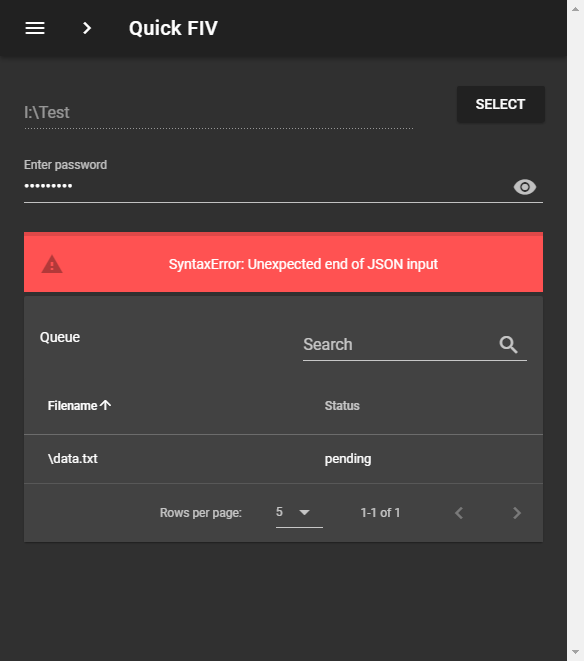
We get this error because if we use an incorrect key the data is transformed into something else instead of the original JSON content.
Before we dive into the public key modes we first need public key pairs. For this we can just simply click the Generate Public Key Pair button inside the Settings Page of the application. Clicking the button will ask the user to input the directory where he wants to save the public and private keys. After the location to save is confirmed the application will utilize Node RSA module and generate 512 bit keys.
Like the Secret Key Mode this mode also builds upon the Unsecured Mode but it provides additional features as compared to Secret Key Mode. It encrypts the data so that it cannot be edited but it also lets the user identify who generated the QuickFIV.json which is now encrypted.
In this case let's say Alice wants to send data to Bob and facilitate Bob in file verification. To achieve this task Alice will supply the application with her Private Key. The application will use Node RSA and the private key and encrypt the QuickFIV.json. Now after the encryption the contents of QuickFIV.json are no longer readable.
3431 3333 2035 6636 3120 6562 6666 2063
3063 6420 6563 6537 2066 3431 3420 3362
3561 2031 3064 660a 6534 3565 2066 3938
3520 3264 3535 2039 6238 6320 6434 3161
2037 6564 6220 6139 3266 2066 6136 650a
3030 3036 2066 3362 6620 3136 3035 2066
3733 6220 3935 3031 2034 3734 3320 3930
3834 2063 3837 660a 6532 3330 2032 3830
6420 3936 3766 2061 6565 6120 3664 6665
2064 6631 6420 6232 3431 2031 3930 330a
6338 6432 2033 3437 3220 3534 3636 2065
3665 3620 6438 6234 2037 6431 6620 6462
3937 2035 6463 330a 3165 3766 2030 3466
6120 6437 6162 2066 3930 3320 6238 3363
2034 6362 6220 3830 6365 2034 3739 360a
3139 6164 2064 6236 6620 3736 6530 2038
6336 6320 6462 3431 2062 3730 6120 6232
6665 2038 6235 390a 3139 3365 2063 6264
3320 3963 3939 2035 3764 3020 6165 3239
2037 6534 6120 3035 3632 2063 3235 350a
3236 6366 2032 6562 3220 3739 3866 2034
6535 6220 3030 3234 2065 3866 3320 3766
3466 2031 3439 360a 3933 6231 2031 6533
3720 6330 3261 2062 3964 3520 6230 3862
2035 3665 3920 6161 3833 2064 3231 310a
6630 3266 2063 6435 6420 6535 6233 2037
3162 3920 6632 6539 2065 3063 6320 3634
3537 2036 3866 630a 6562 3634 2037 6132
3220 3030 3636 2038 3637 3520 3637 3738
2063 6338 6420 6139 3364 2030 3163 630a
3836 6231 2038 6438 3520 6431 3362 2065
6339 6520 6364 3430 2063 3038 6120 3933
3636 2034 3130 340a 6266 3934 2038 3265
3420 6162 6237 2063 3637 6320 3665 6437
2035 3230 6320 6338 3832 2032 3832 660a
6134 6539 2030 3133 3720 3235 3163 2031
3237 6320 3534 6231 2066 6362 3420 3865
3963 2033 3438 360a 3430 6632 2039 3862
6420 3265 6232 2066 3337 6420 3862 3532
2033 3431 3320 3665 3565 2031 6566 650a
3431 3332 2032 3030 3320 6531 6564 2035
3765 3020 3864 3132 2035 6134 6620 6635
3735 2066 3830 660a 6336 6537 2066 3536
3720 6131 3031 2063 3733 6120 6537 6339
2065 3338 6520 6632 6335 2033 6430 640a
3236 6135 2061 6265 6320 3932 3136 2039
6631 3720 3632 3062 2063 3838 3720 3938
3262 2036 6135 370a 6463 3935 2031 6461
6420 3731 3363 2062 6263 6420 6632 3431
2031 6335 3720 3866 3636 2037 6262 610a
Now after Bob has received the data and the encrypted QuickFIV.json, in order to verify his files, he need to supply the application with Public Key of Alice. After that the application will use Node RSA to decrypt the file against the public key. If the key is correct base procedure will continue otherwise an error will be displayed.
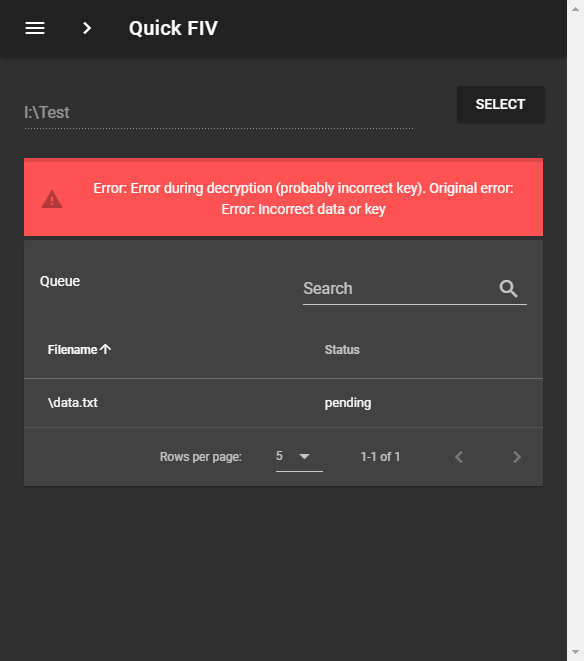
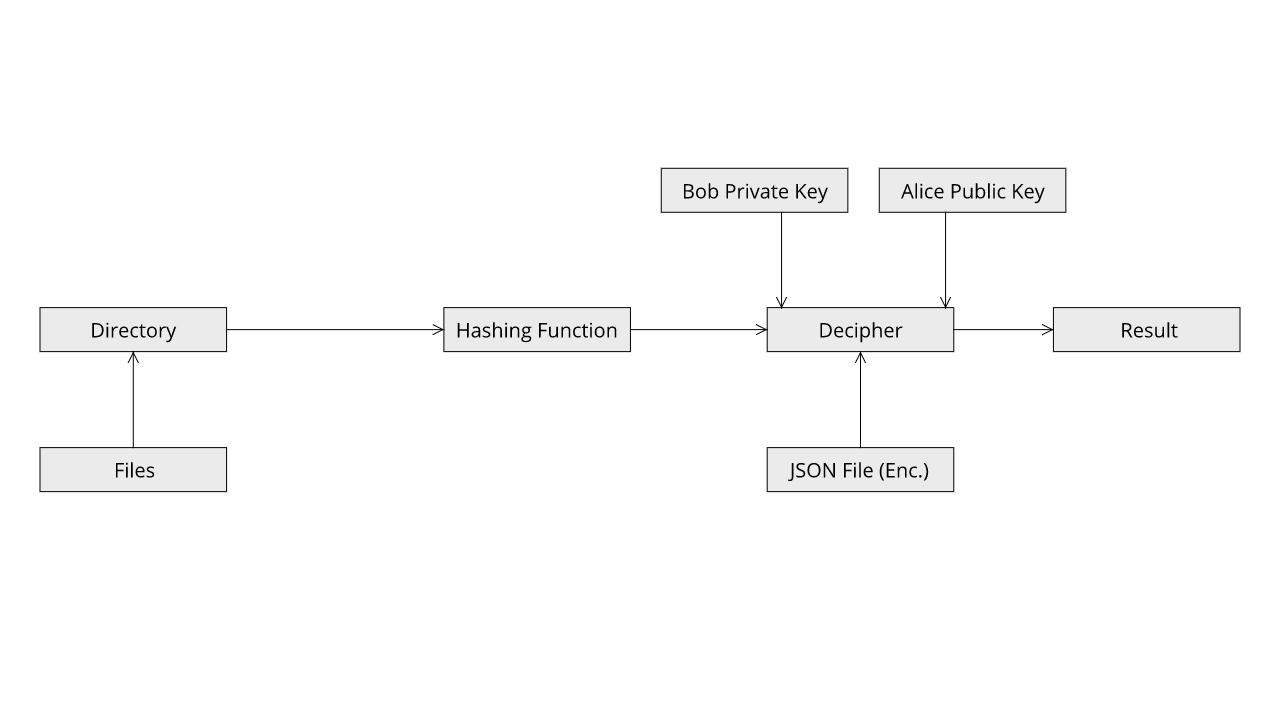
Now this mode is an extension of the Single Public Key Mode. It has the advantage that now the sender can also make sure only the receiver is able to read the contents of the QuickFIV.json.
Now is this mode we will utilize an additional Public Key pair. Alice will now provide the application with her Private key and also the Public key of Bob. Now the application after generating the QuickFIV.json file will encrypt the file with Alice's Private Key and then Bob's Public Key. After the encryption the file looks like a total disaster. It contains so many special characters that most text editors will not be able to render its content.
After Bob has received the data he now needs to provide the application with his own Private key and Alice's Public key. Now the application will use Node RSA and decrypt the QuickFIV.json file twice. First using the Private key of Bob and then using Alice's Public key. If the keys are correct the base procedure will be followed otherwise an error similar to previous case will be displayed.
Now are explained the internal functionalities which the application utilizes itself but are not so apparent to the user.
In order to allow the user to select the directory or file we open native system dialogs. To do this we utilize system dialogs provided inside Electron. Electron automatically detects the OS and displays the system dialogs. Below is an image of a system dialog working as expected inside a heavily customized Windows 10 OS.
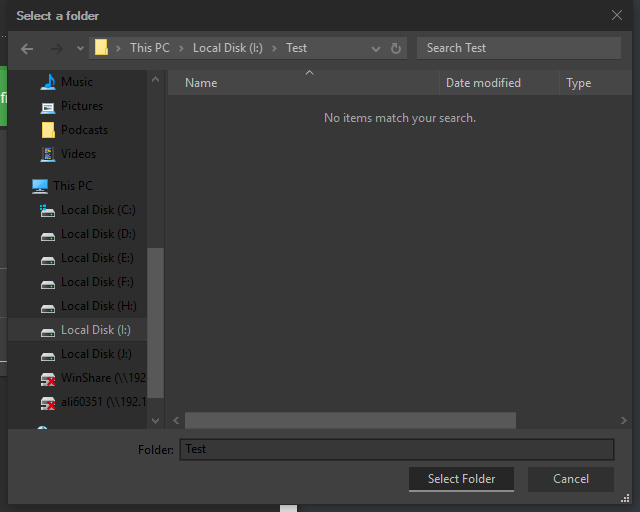
Below is an image of System Dialog running on an Arch Linux Distro (Antergos OS) running the Gnome 3 Desktop Environment and custom themes.
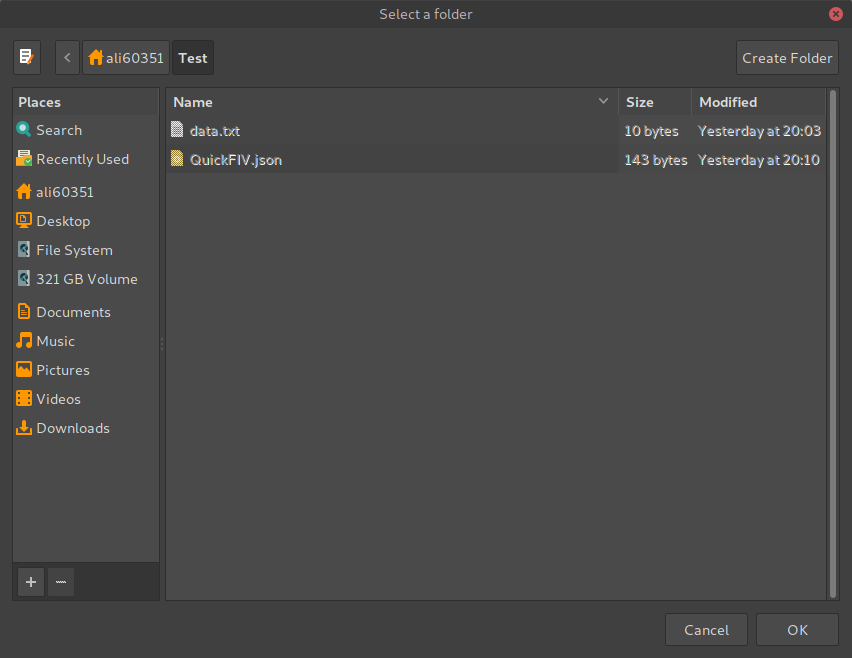
The advantage of Native System Dialogs is that they are usually faster and do not feel out of place when running inside the OS.
In order to gracefully keep the application, it is necessary not to try any JSON actions on something that is not our desired JSON file. First we make sure that the data we are trying to read is in fact a JSON file. We do this simply by executing the following code.
try
{
arr = JSON.parse(data);
}
catch (err)
{
return false;
}Then we check if the JSON is in fact not any other JSON but the one we generated using the application. In order to achieve this we use Is My JSON Valid Module. We provide it will a schema against which it analyzes the JSON file. The schema used for this is the following
var schema = {
required: true,
type: 'object',
properties: {
file: {
required: true,
type: 'string'
},
md5: {
required: true,
type: 'string'
},
sha1: {
required: true,
type: 'string'
},
sha256: {
required: true,
type: 'string'
},
sha512: {
required: true,
type: 'string'
}
}
};Using several try catch blocks and Vuetify Alerts many errors are handled so that the application doesn't crashes whenever an error occurs. Vuetify Alerts are used to tell the user of what the error occurred. The red bar seen below is made using Vuetify Alerts.
During the verification it is very important to make sure that we go to correct paths. I shall demonstrate this issue with an example. Let us consider the two major OS Windows and Linux. Now one major difference in them is that they both handle file paths differently. Consider a folder named test which contains a file named data.txt. Now in Windows the path will be
.\test\data.txt
and in Linux the path will be
./test/data.txt
Now in order to correctly read the relative path from QuickFIV.json we have to first convert the path into the one valid for the OS running the application. This issue is resolved by using a module known as upath.
After properly setting each package.json properly and settings the file structure builds can be easily compiled. The structure used is commonly known as two package.json structure. The tools used to build the installer is known as Bozon. The configuration used at the moment of writing this report is the following.
"build": {
"appId": "com.electron.quickfiv",
"win": {},
"mac": {
"category": "your.app.category.type"
},
"linux": {
"target": [
{
"target": "deb",
"arch": [
"x64"
]
},
{
"target": "tar.gz",
"arch": [
"x64"
]
},
{
"target": "pacman",
"arch": [
"x64"
]
}
],
"category": "Utility"
}
}The configuration works successfully for Windows and Linux. Mac OS has not be testing due to the unavailability of a modern Mac Desktop. Before starting building we have to make sure we have the required tools installed. Install the latest version of Node JS. Then install bozon using the following command.
npm install -g bozon
To package for Windows, you have to first clone the repository and then after entering the directory use
yarn
if you have yarn installed or use
npm install
to fetch all the dependencies and then execute the following command to package the application
bozon package windows
does this will log something similar to the following text on your CMD.
Your log will vary from the following because I have most of the resources cached. Make sure you have internet before executing these commands.
[02:48:00] Using gulpfile I:\Dev\Github\QuickFIV\Quick-FIV\gulpfile.js
[02:48:00] Starting 'html'...
[02:48:00] Starting 'images'...
[02:48:00] Starting 'styles'...
[02:48:00] Starting 'scripts:main'...
[02:48:00] Starting 'scripts:renderer'...
[02:48:02] Finished 'images' after 1.41 s
[02:48:02] Version: webpack 1.15.0
Asset Size Chunks Chunk Names
application.js 3.5 kB 0 [emitted] main
[02:48:02] Finished 'html' after 1.69 s
[02:48:02] Finished 'scripts:renderer' after 1.67 s
[02:48:02] Finished 'styles' after 1.69 s
[02:48:02] Finished 'scripts:main' after 1.73 s
[02:48:02] Starting 'prepare:app'...
[02:48:02] Finished 'prepare:app' after 96 ms
• electron-builder version=20.10.0
• loaded configuration file=package.json ("build" field)
• no native production dependencies
• packaging platform=win32 arch=x64 electron=1.8.4 appOutDir=packages\win-unpacked
• building target=nsis file=packages\QuickFIV Setup 0.1.0.exe archs=x64 oneClick=true
• building block map blockMapFile=packages\QuickFIV Setup 0.1.0.exe.blockmap
Now we can simply install the app by double clicking QuickFIV Setup 0.1.0.exe.
To package for Linux, you have to first clone the repository and then after entering the directory use
yarn
if you have yarn installed or use
npm install
to fetch all the dependencies and then execute the following command to package the application
bozon package linux
does this will log something similar to the following text on your terminal.
Your log will vary from the following because I have most of the resources cached. Make sure you have internet before executing these commands.
[02:58:38] Using gulpfile ~/Dev/Github/Quick-FIV/gulpfile.js
[02:58:38] Starting 'html'...
[02:58:38] Starting 'images'...
[02:58:38] Starting 'styles'...
[02:58:38] Starting 'scripts:main'...
[02:58:38] Starting 'scripts:renderer'...
[02:58:39] Finished 'images' after 620 ms
[02:58:39] Finished 'html' after 789 ms
[02:58:39] Version: webpack 1.15.0
Asset Size Chunks Chunk Names
application.js 3.44 kB 0 [emitted] main
[02:58:39] Finished 'styles' after 911 ms
[02:58:39] Finished 'scripts:renderer' after 908 ms
[02:58:39] Finished 'scripts:main' after 961 ms
[02:58:39] Starting 'prepare:app'...
[02:58:41] Finished 'prepare:app' after 1.72 s
• electron-builder version=20.10.0
• loaded configuration file=package.json ("build" field)
• no native production dependencies
• packaging platform=linux arch=x64 electron=1.8.4 appOutDir=packages/linux-unpacked
• building target=tar.gz arch=x64 file=packages/QuickFIV-0.1.0.tar.gz
• building target=deb arch=x64 file=packages/QuickFIV_0.1.0_amd64.deb
• building target=pacman arch=x64 file=packages/QuickFIV-0.1.0.pacman
Now depending upon your Linux Distro you have to choose different options to install.
Debian / Ubuntu and derivatives
sudo apt install QuickFIV_0.1.0_amd64.deb
Arch users and derivatives
sudo pacman -U QuickFIV-0.1.0.pacman
Rest of Linux distros can use the tar.gz archive.
Continuous Integration (CI) and Continuous Development (CD) are advanced tools used to test and deploy applications. For this application we are using AppVeyor. First we have to configure it so that it can understand how to compile our application. For these we have written configurations inside appveyor.yml which contains the following text.
platform:
- x64
cache:
- node_modules
- app\node_modules
- '%USERPROFILE%\.electron'
- '%LOCALAPPDATA%\Yarn'
- '%LOCALAPPDATA%\electron-builder\cache'
init:
- git config --global core.autocrlf input
install:
- ps: Install-Product node 9 x64
- git reset --hard HEAD
- yarn add bozon
- yarn
build_script:
- node --version
- yarn --version
- yarn bozon package windows
artifacts:
- path: 'packages\*.exe'
name: Quick-FIV
test: offNow whenever a new commit in the repository is made compilation starts online and here is a log it generated.
Build started
git config --global core.autocrlf input
git clone -q --branch=master https://github.com/Ali60351/Quick-FIV.git C:\projects\quick-fiv
git checkout -qf 4bc83f423cdd594da6a6aff8422819f85eb18bc4
Running Install scripts
Install-Product node 9 x64
Uninstalling node 4.8.7 (x86)...
Installing node 9.11.1 (x64)...
git reset --hard HEAD
HEAD is now at 4bc83f4 Updated cache and inserted badge
yarn add bozon
yarn add v1.5.1
info No lockfile found.
[1/4] Resolving packages...
warning electron > electron-download > nugget > progress-stream > through2 > xtend > [email protected]:
warning gulp > [email protected]: gulp-util is deprecated - replace it, following the guidelines at https://medium.com/gulpjs/gulp-util-ca3b1f9f9ac5
warning gulp > vinyl-fs > [email protected]: please upgrade to graceful-fs 4 for compatibility with current and future versions of Node.js
warning gulp > vinyl-fs > glob-stream > [email protected]: Please update to minimatch 3.0.2 or higher to avoid a RegExp DoS issue
warning gulp > vinyl-fs > glob-stream > glob > [email protected]: Please update to minimatch 3.0.2 or higher to avoid a RegExp DoS issue
warning gulp > vinyl-fs > graceful-fs > [email protected]: This module relies on Node.js's internals and will break at some point. Do not use it, and update to [email protected].
warning gulp > vinyl-fs > glob-watcher > gaze > globule > [email protected]: Please update to minimatch 3.0.2 or higher to avoid a RegExp DoS issue
warning gulp > vinyl-fs > glob-watcher > gaze > globule > glob > [email protected]: Please update to minimatch 3.0.2 or higher to avoid a RegExp DoS issue
warning gulp > vinyl-fs > glob-watcher > gaze > globule > glob > [email protected]: please upgrade to graceful-fs 4 for compatibility with current and future versions of Node.js
warning webpack-stream > [email protected]: gulp-util is deprecated - replace it, following the guidelines at https://medium.com/gulpjs/gulp-util-ca3b1f9f9ac5
[2/4] Fetching packages...
info [email protected]: The platform "win32" is incompatible with this module.
info "[email protected]" is an optional dependency and failed compatibility check. Excluding it from installation.
info [email protected]: The platform "win32" is incompatible with this module.
info "[email protected]" is an optional dependency and failed compatibility check. Excluding it from installation.
info [email protected]: The platform "win32" is incompatible with this module.
info "[email protected]" is an optional dependency and failed compatibility check. Excluding it from installation.
info [email protected]: The platform "win32" is incompatible with this module.
info "[email protected]" is an optional dependency and failed compatibility check. Excluding it from installation.
info [email protected]: The platform "win32" is incompatible with this module.
info "[email protected]" is an optional dependency and failed compatibility check. Excluding it from installation.
[3/4] Linking dependencies...
[4/4] Building fresh packages...
success Saved lockfile.
success Saved 490 new dependencies.
info Direct dependencies
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
└─ [email protected]
info All dependencies
├─ @types/[email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
├─ [email protected]
└─ [email protected]
$ install-app-deps
• please use as subcommand: electron-builder install-app-deps
• electron-builder version=20.11.1
• loaded configuration file=package.json ("build" field)
• installing production dependencies platform=win32 arch=x64 appDir=C:\projects\quick-fiv\app
Done in 69.00s.
yarn
yarn install v1.5.1
[1/4] Resolving packages...
success Already up-to-date.
$ install-app-deps
• please use as subcommand: electron-builder install-app-deps
• electron-builder version=20.11.1
• loaded configuration file=package.json ("build" field)
• installing production dependencies platform=win32 arch=x64 appDir=C:\projects\quick-fiv\app
Done in 2.73s.
node --version
v9.11.1
yarn --version
1.5.1
yarn bozon package windows
yarn run v1.5.1
$ C:\projects\quick-fiv\node_modules\.bin\bozon package windows
[13:36:24] Using gulpfile C:\projects\quick-fiv\gulpfile.js
[13:36:24] Starting 'html'...
[13:36:24] Starting 'images'...
[13:36:24] Starting 'styles'...
[13:36:24] Starting 'scripts:main'...
[13:36:24] Starting 'scripts:renderer'...
[13:36:25] Finished 'images' after 371 ms
[13:36:25] Version: webpack 1.15.0
Asset Size Chunks Chunk Names
application.js 3.44 kB 0 [emitted] main
[13:36:25] Finished 'html' after 525 ms
[13:36:25] Finished 'scripts:renderer' after 496 ms
[13:36:25] Finished 'styles' after 504 ms
[13:36:25] Finished 'scripts:main' after 531 ms
[13:36:25] Starting 'prepare:app'...
[13:36:25] Finished 'prepare:app' after 570 ms
• electron-builder version=20.11.1
• artifacts will be published if draft release exists reason=CI detected
• loaded configuration file=package.json ("build" field)
• no native production dependencies
• packaging platform=win32 arch=x64 electron=1.8.6 appOutDir=packages\win-unpacked
Downloading tmp-832-1-SHASUMS256.txt-1.8.6
[============================================>] 100.0% of 5.74 kB (5.74 kB/s)
• downloading path=C:\Users\appveyor\AppData\Local\electron-builder\cache\winCodeSign\winCodeSign-2.0.0 url=https://github.com/electron-userland/electron-builder-binaries/releases/download/winCodeSign-2.0.0/winCodeSign-2.0.0.7z
• building target=nsis file=packages\QuickFIV Setup 0.1.0.exe archs=x64 oneClick=true
• downloading path=C:\Users\appveyor\AppData\Local\electron-builder\cache\nsis\nsis-3.0.3.0 url=https://github.com/electron-userland/electron-builder-binaries/releases/download/nsis-3.0.3.0/nsis-3.0.3.0.7z
• downloading path=C:\Users\appveyor\AppData\Local\electron-builder\cache\nsis\nsis-resources-3.3.0 url=https://github.com/electron-userland/electron-builder-binaries/releases/download/nsis-resources-3.3.0/nsis-resources-3.3.0.7z
• building block map blockMapFile=packages\QuickFIV Setup 0.1.0.exe.blockmap
Done in 67.38s.
Collecting artifacts...
Found artifact 'packages\QuickFIV Setup 0.1.0.exe' matching 'packages\*.exe' path
Uploading artifacts...
[1/1] packages\QuickFIV Setup 0.1.0.exe (36,166,982 bytes)...100%
Updating build cache...
Cache 'node_modules' - Updated
Cache 'app\node_modules' - Updated
Cache 'C:\Users\appveyor\.electron' - Updated
Cache 'C:\Users\appveyor\AppData\Local\Yarn' - Updated
Cache 'C:\Users\appveyor\AppData\Local\electron-builder\cache' - Updated
Build success
Is this section we will go through different use cases that the user will go through if he uses this application. For the purpose of testing we are going to use the following directory. On a Windows 10 PC.
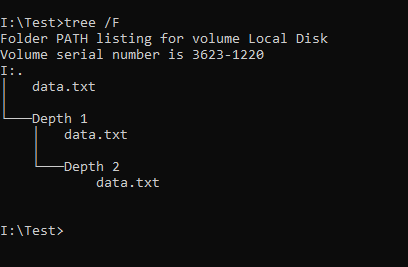
First we will check if all the hashing functions work properly. For these test we expect the application to generate the selected hash and store it inside QuickFIV.json and then properly verify them too. These same tests will also verify the Unsecured Mode at the same time.
First we go inside the application's Settings page and set the algorithm to MD5 and then go back to Home page and select our Test folder. As a result, we get a QuickFIV.json which contains the following text.
[
{
"file": "\\data.txt",
"md5": "f315202b28422ed5c2af4f843b8c2764",
"sha1": "",
"sha256": "",
"sha512": ""
},
{
"file": "\\Depth 1\\data.txt",
"md5": "9dad0e9306c92e7d09c76647d8988efe",
"sha1": "",
"sha256": "",
"sha512": ""
},
{
"file": "\\Depth 1\\Depth 2\\data.txt",
"md5": "2add6fdb6e3ea885b71e7ae19416415e",
"sha1": "",
"sha256": "",
"sha512": ""
}
]We expected the application to reclusively traverse the directory and take MD5 of them all. As we can see from the QuickFIV.json file above, the test succeeded. No errors are generated of Hash Verification too.
For this test we set the algorithm to SHA1 and then select our folder. The resultant QuickFIV.json contains the following text.
[
{
"file": "\\data.txt",
"md5": "",
"sha1": "cae99c6102aa3596ff9b86c73881154e340c2ea8",
"sha256": "",
"sha512": ""
},
{
"file": "\\Depth 1\\data.txt",
"md5": "",
"sha1": "c38851f89100d5095d998fdeef7806c17b8580d9",
"sha256": "",
"sha512": ""
},
{
"file": "\\Depth 1\\Depth 2\\data.txt",
"md5": "",
"sha1": "a79b93819c5f1f175d4e49a570676f2969c0ec3b",
"sha256": "",
"sha512": ""
}
]Hashes were generated properly and verification had no errors either.
For this test we set the algorithm to SHA256 and then select our folder. The resultant QuickFIV.json contains the following text.
[
{
"file": "\\data.txt",
"md5": "",
"sha1": "",
"sha256": "bcfe67172a6f4079d69fe2f27a9960f9d62edae2fcd4bb5a606c2ebb74b3ba65",
"sha512": ""
},
{
"file": "\\Depth 1\\data.txt",
"md5": "",
"sha1": "",
"sha256": "b44d9bfc84588c2d4abfd849a7635874c209d22ee3f030d3d4495c5f542b08aa",
"sha512": ""
},
{
"file": "\\Depth 1\\Depth 2\\data.txt",
"md5": "",
"sha1": "",
"sha256": "71bfacfa86c701f9f7a0ac57541ed48457897075359226906cd1e01f3f890435",
"sha512": ""
}
]Hashes were generated properly and verification had no errors either.
For this test we set the algorithm to SHA512 and then select our folder. The resultant QuickFIV.json contains the following text.
[
{
"file": "\\data.txt",
"md5": "",
"sha1": "",
"sha256": "",
"sha512": "439e4ceed9312fef2e554042c3d27d6ac31da9cf72ba866ba9b0e00328d06280797482bf2cd007e0808296db0b987b73fe1f953e97e25883263b9783513c2949"
},
{
"file": "\\Depth 1\\data.txt",
"md5": "",
"sha1": "",
"sha256": "",
"sha512": "02cb2166fb008f4bb5c20d69356efcb4b679da025f77b7a5db8d6650f403a000db5677f49b23090d9ad78b3fd4dba9dcaa2ac20eaadd785addb3d094882856eb"
},
{
"file": "\\Depth 1\\Depth 2\\data.txt",
"md5": "",
"sha1": "",
"sha256": "",
"sha512": "5c0b220d3e5039f2df0e85848f7521a7eb02eed6a2590c778c7e43dff04d0304eca7b862e59d423b8780447a44d5c41f20f83001cd1ee1680177f6db787b59c3"
}
]Hashes were generated properly and verification had no errors either.
Is this tests we will verify if the Secure Key Mode is working properly or not. The expected result is to get an encrypted QuickFIV.json after selected the test folder and then being able to properly verify the files after entering the correct secret key. For this test the password we use will be password. After selecting the directory, we get QuickFIV.json with this text inside it. The algorithm used for these test in the default one, which is SHA1.
U2FsdGVkX1+mJqqPPzgcGVJjS8G7zcTB9MV9pzOoVxlzzsAY87HAnA35PGw7R/R1VBnVPAW1zVrNSfYPedDNRsQj9vzPgGCUiTVTDTDrbZBoarokSEN3YSZjn7Zy5/Npy8jTy3yugpzTr1ZlrOTaifDiOFLxng1RQCceGX+2BBGS0EVnvgMj8JTRAaMfl9B3yDE1QkSoLSfXaEPw+bBKi+jUAbRGN6uwkCZmav2acFPPJ65YT6qVE901T20XK8FXgx28kE1kcUNx2H9aHb8oi1VwKcKzQjj5XrXXP1c/jFSqJEOJ3DyDB/44vyenfORMYkdr6Elfy8CpdE8cspJJ4sJjHui1HYK0pyRzH+0d2PrJgXb/0WyBBbfwfF8dR/DYuM4xU7dVEsSAHYUeJEDUEAkRmnmNceEMSPcMFVTaG2gsAb80kPYmuiIDYn7fwlRDsGJ4bRyD9OaMxdDLWFJpGE3CRGTqd4ahZ+nkFUDCqP4=
We successfully obtained an encrypted QuickFIV.json and then the verification was successful too.
In this test we will try to generate two public key pairs to use in our coming tests. First we go the the Settings page and then enter the destination as to where we want to save the public key and private key. The first pair we generated in the following.
-----BEGIN RSA PRIVATE KEY-----
MIIBPQIBAAJBAMwcoL86zZQewBfen/NJdScQm2spSDZCp0lFCFdN7t2Lh62R8RXa
oEtxODYRORNNZMI0cWnZvaE4WR+KnJtAzz8CAwEAAQJBAIWo6YrQUvb//AKlglCq
ddETCvNtoSAHHczZK9Ef85+XJom+7s8skKa4GIcG5R+pvnmxxRkHhE0dUBNHiXzG
CcECIQD7q2WTfZIWM6xX2qW/szWts9Aml8N5vYpN+CtdaEI+qQIhAM+fvVzqCIvi
/CpzC5Pegz3rYwjsyIUAR2+gic8+WtenAiEA1BzNa9X1/ohmxVUfRccBgvl+gkh/
FGhP3Q9BXWS2EKECIQC7Cb1OWaqvUiE2oIM6h4aVnlqOLLkLT9AK2IWtRBAUGwIh
AIJ2bIwUpoVuiSy+/HYuoWXes8DWyZ0MmqrosBZQqpgV
-----END RSA PRIVATE KEY----------BEGIN PUBLIC KEY-----
MFwwDQYJKoZIhvcNAQEBBQADSwAwSAJBAMwcoL86zZQewBfen/NJdScQm2spSDZC
p0lFCFdN7t2Lh62R8RXaoEtxODYRORNNZMI0cWnZvaE4WR+KnJtAzz8CAwEAAQ==
-----END PUBLIC KEY-----
The second pair we generated is the following.
-----BEGIN RSA PRIVATE KEY-----
MIIBOgIBAAJBALcGopQIetnfB6pbU1oo5B7UjVEBBhWvwhgmN1lXMpq4b6aL8Sl2
0LWJ3obf6m3hDLCx2kPv1xC1eqBd8nHheIECAwEAAQJAftm8aHkQHFy1xV6SgJSC
ttN+NjxNaU5taatjBSqoSg6HHw0N7M+mjHTMJTJggkQXRClbZjNp1vivfFBJDzS/
OQIhAPqSDYr0qu/fROivhOYFdz1/Odzkwc9m9xnaJ8hpktRnAiEAuv3nTYswHPYs
Syu8PZCeDttBo2aO9U9Zl4RfaYfoetcCIFTHYemoCsYKRuhrqo2hP80A5PUGOUUR
U33dwCQhBFr1AiBSwUO4obztVFVN/1ETvgj1cjueYSkrj66Ky96eCbPtiQIhALgl
IbyL2DLXQYaWUbAzZrnFj92gWWdMURKNo1yLNb1t
-----END RSA PRIVATE KEY-----
-----BEGIN PUBLIC KEY-----
MFwwDQYJKoZIhvcNAQEBBQADSwAwSAJBALcGopQIetnfB6pbU1oo5B7UjVEBBhWv
whgmN1lXMpq4b6aL8Sl20LWJ3obf6m3hDLCx2kPv1xC1eqBd8nHheIECAwEAAQ==
-----END PUBLIC KEY-----
The two pairs were successfully generated thus this test passed too.
For this test we will set the mode to One Way Public Key Cryptography and then select our folder. We supply the application with Private Key from the first pair. We expect to obtain an encrypted QuickFIV.json. The QuickFIV.json we obtain after selected the directory contains the following text.
4133 5f61 ebff c0cd ece7 f414 3b5a 10df
e45e f985 2d55 9b8c d41a 7edb a92f fa6e
0006 f3bf 1605 f73b 9501 4743 9084 c87f
e230 280d 967f aeea 6dfe df1d b241 1903
22d2 fb13 6426 11f4 d6b9 3859 8b8e 8cc4
e010 1514 ed90 51e8 f0bb debc ff17 1f3f
a4b0 a2e6 8c54 c42f ea67 b459 9b77 3056
3068 3362 eb43 5bcd 5754 92d8 9526 0261
200f afbe d5f8 1281 bc26 6826 f5b9 f0d4
9615 75df cd68 ba3f 755b b373 9617 d939
711c 7088 0540 de21 d070 a002 91ea 956d
9e26 16ad b6c4 8bed 9e9a cb72 d804 727c
7805 4c19 dbd1 7c9e 6795 e7e0 6271 80c9
ec19 9d97 0432 c448 703d 95b7 1e95 273d
cf95 23aa 29b6 7839 d6cc 4771 476c db33
f9e7 b498 33ee c4ed c03f 023f 44f4 5cfe
cb38 30c5 eb75 2a91 62ec e121 c61a ea3f
80ec e4dd 00b8 8cda baaf acdd 7c4e 2805
b94c b84c b457 d362 1075 3c8a 5265 9202
d589 2064 1b91 5343 570f 06c3 1b03 eb49
6ecb 6389 7bf0 026a 245e 47df b55b 519a
b9eb 2710 f0b7 5d22 4382 9319 6116 a12d
bc93 d742 dc4d b8c0 85b6 29f2 96b7 d315
595a 8810 6015 bdef 9894 085e 2101 09e9
a18e 741d 7f5d 2cf9 757c 823b f0a8 51be
8055 6005 bff2 0a6f 657f a9b1 053e 9c35
3554 058e 8fc6 57bc 178e 879a 9e84 3110
7417 3f81 267c 3a33 e987 daa7 9320 1ee9
6ce7 b191 90ce b5bc e517 2062 59ad f434
fc45 7a06 861e a888 af6a 42c2 65c9 8d9e
bd87 ab5e 17a6 70fa 0a19 f12f 283f 673d
a6ba 8105 f19d 58f6 e971 1b3f 0f24 af64
a94c 7899 0732 8aa6 f56c e033 cad1 cd75
c845 61c0 d219 50d6 8008 1524 23e4 fa0b
4114 2951 bab0 9f3a 533c 7ab3 93a5 34e6
c1dc 0dd0 e956 8568 1e0f 8db5 4207 fbeb
6de9 27a7 e421 ca75 3869 b65b 122d 178a
174d 1820 8214 368c 6ebe 57c5 c3f7 70f4
6d57 9221 1e9a 79e2 6a00 e410 8a23 cd73
52c0 68ac ef7b 4cd7 634d d121 0171 7e6c
26d2 360b 3dcf 5701 24d1 247b 9ae9 f1db
d39f 96bd 5016 91ad cad8 fa63 4bc8 d8d8
7d99 c0f9 6a2a 261c bbe5 0aaf cd83 d9a8
b256 7c0e 4584 a10a 2228 7c4e 4eff de6e
8110 6c0f 9e83 2614 65c2 baca e050 000f
e1b7 0374 68c2 eed5 649e 2127 d152 c7a8
d5cf c9e3 364c 4eaf fb87 f022 a4a4 c3f5
96b1 9fec c481 60aa 9d55 dee0 d56a c63d
299a 22c9 7b3c 8b7f 1112 68e7 a024 aaa3
1164 0866 dd8f 83d8 92fc be12 0442 5ac0
f25d f833 cee1 0f4a 80b2 10e1 6f20 4b18
50c1 f7c6 aa8c c303 686a 0a5d e821 3766
05ba 1405 27aa d289 111f 79cf e9b8 76d2
b5e7 0225 a884 c1e5 8a05 ca3a 5512 e118
56ea 7130 70ac c2f9 e995 9ed8 fa7b fb5b
a65f dec0 859e 30e8 7a4a ff89 6b41 ec89
01a1 404c c74c 4687 c45c a46a 5588 d5b1
8979 81a6 9110 b002 db92 bd6e 3630 8e40
d389 541a b4d8 0708 c53e 1642 ff7d 5c04
63b5 b629 de12 986e 9c35 534c 9822 f406
ca20 b229 feb4 b389 9ea6 90af b9f3 43c6
152a 02c2 fb89 b5e8 a550 f5bf 5230 4abc
9fd9 e603 0d88 fcf9 a024 29f0 6a76 e060
53da a52d 3e8a e8f2 1a33 0fc4 f109 c71a
After selecting the same directory again, the application asks us for the public key. As expected the application succeeded the verify the file upon providing the correct key.
For this test we will set the mode to Two Way Public Key Cryptography and then select our folder. We supply the application with Private Key from the first pair and then the Public Key from the second pair. We expect to obtain an encrypted QuickFIV.json. The QuickFIV.json we obtain after selected the directory contains the following text.
Simple Markdown won't be able to handle the text, thus I instead posted an image from Sublime Text 3 and Nano

Then we attempt to verify this folder by providing the private key from the second pair and then providing the public key from the first pair. As expected the verification succeeds so this test is cleared too.
Now we shall compare this application to the ones already available on the internet
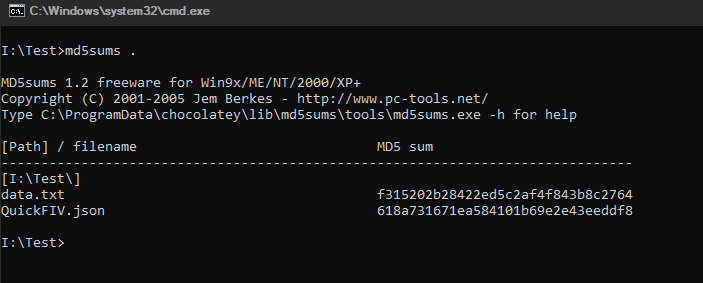
MD5sums is one of the most commonly available hashing application on the internet. Like our application it can read multiple files and take their hash but it cannot read files recursively, thus only reading files at zero depth of file tree. Also it lacks support for other algorithms and security features. It has a CLI as seen below.
md5deep is an advanced form of MD5sums. It supports multiple algorithm now and also supports recursive operations. It can also provide time estimation which our application currently doesn't. It lacks the encryption support which our application provides. This one also has a CLI like MD5sums.
QuickSFV uses SFV algorithm and has a GUI in contrast to the previous two options. Despite using a GUI it looks quite outdated visually. It also lacks encryption support. Is only available for Windows.
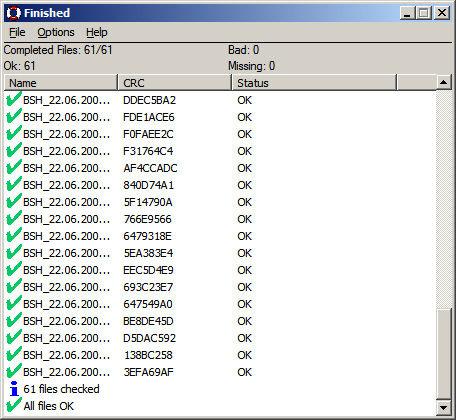
ComputeHash is also a GUI tool. It only supports a single file at a time. It lacks encryption features of our application and only supports Windows.

People seem to not realize how important some data can prove to be and how easily files can be modified by attackers and you shall never realize what they did. In order to make sure we can verify our files we need to use some method to ensure their integrity. The most common method to do so being hashing. It is also make sure to keep these hashes safe so that an attacker cannot fool you into misunderstanding the integrity of files. Since we generate so much data every day we need some way to automate the hash generation too.
Depending upon your use case this application can facilitate the hashing procedure while providing desired level of security.
Attack (computing) - Wikipedia
