 +
+
+
+
 App Control for Business Resources
>
-> ###
App Control for Business Resources
>
-> ###  The WDACConfig Module for App Control for Business
+> ###
The WDACConfig Module for App Control for Business
+> ###  AppControl Manager application
>
> ###
AppControl Manager application
>
> ###  Read the Rationale Behind This GitHub Repository
@@ -99,6 +99,30 @@ Unprotect-WindowsSecurity
Read the Rationale Behind This GitHub Repository
@@ -99,6 +99,30 @@ Unprotect-WindowsSecurity
 +
+
+
+
+
+ +
+
+
+ +
+
+
+
-YOUTUBE VIDEO: How to easily protect against BYOVD attack scenarios with WDAC policy in Windows
-
-  -
-
-
-
 +
+
%20Policies.png) -
-
-
-%20Policy.png) diff --git a/Wiki posts/Windows Defender Application Control (WDAC)/EKUs in WDAC, App Control for Business, Policies.md b/Wiki posts/Windows Defender Application Control (WDAC)/EKUs in WDAC, App Control for Business, Policies.md
index 548c27a62..6be49b67b 100644
--- a/Wiki posts/Windows Defender Application Control (WDAC)/EKUs in WDAC, App Control for Business, Policies.md
+++ b/Wiki posts/Windows Defender Application Control (WDAC)/EKUs in WDAC, App Control for Business, Policies.md
@@ -1,4 +1,4 @@
-# EKUs in WDAC, App Control for Business, Policies
+# EKUs in App Control for Business Policies
diff --git a/Wiki posts/Windows Defender Application Control (WDAC)/EKUs in WDAC, App Control for Business, Policies.md b/Wiki posts/Windows Defender Application Control (WDAC)/EKUs in WDAC, App Control for Business, Policies.md
index 548c27a62..6be49b67b 100644
--- a/Wiki posts/Windows Defender Application Control (WDAC)/EKUs in WDAC, App Control for Business, Policies.md
+++ b/Wiki posts/Windows Defender Application Control (WDAC)/EKUs in WDAC, App Control for Business, Policies.md
@@ -1,4 +1,4 @@
-# EKUs in WDAC, App Control for Business, Policies
+# EKUs in App Control for Business Policies
 @@ -355,9 +355,9 @@ In every Signer, the `CertEKU` node should only be placed directly after `CertRo
## Continue Reading
+* [AppControl Manager](https://github.com/HotCakeX/Harden-Windows-Security/wiki/AppControl-Manager)
* [App Control Policy for BYOVD Kernel Mode Only Protection](https://github.com/HotCakeX/Harden-Windows-Security/wiki/WDAC-policy-for-BYOVD-Kernel-mode-only-protection)
* [WDAC Notes](https://github.com/HotCakeX/Harden-Windows-Security/wiki/WDAC-Notes)
-* [WDACConfig Module](https://github.com/HotCakeX/Harden-Windows-Security/wiki/WDACConfig)
@@ -355,9 +355,9 @@ In every Signer, the `CertEKU` node should only be placed directly after `CertRo
## Continue Reading
+* [AppControl Manager](https://github.com/HotCakeX/Harden-Windows-Security/wiki/AppControl-Manager)
* [App Control Policy for BYOVD Kernel Mode Only Protection](https://github.com/HotCakeX/Harden-Windows-Security/wiki/WDAC-policy-for-BYOVD-Kernel-mode-only-protection)
* [WDAC Notes](https://github.com/HotCakeX/Harden-Windows-Security/wiki/WDAC-Notes)
-* [WDACConfig Module](https://github.com/HotCakeX/Harden-Windows-Security/wiki/WDACConfig)
 diff --git a/Wiki posts/Windows Defender Application Control (WDAC)/How to Create and Deploy a Signed WDAC Policy.md b/Wiki posts/Windows Defender Application Control (WDAC)/How to Create and Deploy a Signed WDAC Policy.md
index 256dcc734..3073e2cc6 100644
--- a/Wiki posts/Windows Defender Application Control (WDAC)/How to Create and Deploy a Signed WDAC Policy.md
+++ b/Wiki posts/Windows Defender Application Control (WDAC)/How to Create and Deploy a Signed WDAC Policy.md
@@ -1,7 +1,7 @@
# Create and Deploy Signed Application Control (WDAC) Policies
> [!IMPORTANT]\
-> [WDACConfig module](https://github.com/HotCakeX/Harden-Windows-Security/wiki/Build-WDACCertificate) can easily and quickly generate a Code Signing certificate to be used for signing App Control policies.
+> [AppControl Manager](https://github.com/HotCakeX/Harden-Windows-Security/wiki/AppControl-Manager) can easily and quickly generate a Code Signing certificate to be used for signing App Control policies.
>
> This guide is only for those who want to learn how to setup a Windows Server with Active Directory and Certification Authority roles and create their own CA.
@@ -14,7 +14,7 @@
* [Refer to Microsoft's website](https://learn.microsoft.com/en-us/windows/security/application-security/application-control/app-control-for-business/design/appcontrol-design-guide) or [my other wiki posts](https://github.com/HotCakeX/Harden-Windows-Security/wiki/Introduction) If you want to learn about App Control itself and how to create a customized App Control policy for your own environment.
* Always test and deploy your App Control policy in Audit mode first to make sure it works correctly, before deploying the Signed version of it.
- - The [WDACConfig](https://github.com/HotCakeX/Harden-Windows-Security/wiki/WDACConfig) module has an optional parameter called `-TestMode` that will deploy the policies with ***Boot Audit on Failure*** and ***Advanced Boot Options Menu*** policy rule options.
+ - The [AppControl Manager](https://github.com/HotCakeX/Harden-Windows-Security/wiki/AppControl-Manager) has a ***Test Mode*** feature that will deploy the policies with ***Boot Audit on Failure*** and ***Advanced Boot Options Menu*** policy rule options.
* Keep the xml file(s) of the deployed base policy(s) in a safe place, they are needed if you decide to disable or modify the signed deployed App Control policy later on.
@@ -288,30 +288,14 @@ The [Personal Information Exchange (.pfx)](https://learn.microsoft.com/en-us/win
diff --git a/Wiki posts/Windows Defender Application Control (WDAC)/How to Create and Deploy a Signed WDAC Policy.md b/Wiki posts/Windows Defender Application Control (WDAC)/How to Create and Deploy a Signed WDAC Policy.md
index 256dcc734..3073e2cc6 100644
--- a/Wiki posts/Windows Defender Application Control (WDAC)/How to Create and Deploy a Signed WDAC Policy.md
+++ b/Wiki posts/Windows Defender Application Control (WDAC)/How to Create and Deploy a Signed WDAC Policy.md
@@ -1,7 +1,7 @@
# Create and Deploy Signed Application Control (WDAC) Policies
> [!IMPORTANT]\
-> [WDACConfig module](https://github.com/HotCakeX/Harden-Windows-Security/wiki/Build-WDACCertificate) can easily and quickly generate a Code Signing certificate to be used for signing App Control policies.
+> [AppControl Manager](https://github.com/HotCakeX/Harden-Windows-Security/wiki/AppControl-Manager) can easily and quickly generate a Code Signing certificate to be used for signing App Control policies.
>
> This guide is only for those who want to learn how to setup a Windows Server with Active Directory and Certification Authority roles and create their own CA.
@@ -14,7 +14,7 @@
* [Refer to Microsoft's website](https://learn.microsoft.com/en-us/windows/security/application-security/application-control/app-control-for-business/design/appcontrol-design-guide) or [my other wiki posts](https://github.com/HotCakeX/Harden-Windows-Security/wiki/Introduction) If you want to learn about App Control itself and how to create a customized App Control policy for your own environment.
* Always test and deploy your App Control policy in Audit mode first to make sure it works correctly, before deploying the Signed version of it.
- - The [WDACConfig](https://github.com/HotCakeX/Harden-Windows-Security/wiki/WDACConfig) module has an optional parameter called `-TestMode` that will deploy the policies with ***Boot Audit on Failure*** and ***Advanced Boot Options Menu*** policy rule options.
+ - The [AppControl Manager](https://github.com/HotCakeX/Harden-Windows-Security/wiki/AppControl-Manager) has a ***Test Mode*** feature that will deploy the policies with ***Boot Audit on Failure*** and ***Advanced Boot Options Menu*** policy rule options.
* Keep the xml file(s) of the deployed base policy(s) in a safe place, they are needed if you decide to disable or modify the signed deployed App Control policy later on.
@@ -288,30 +288,14 @@ The [Personal Information Exchange (.pfx)](https://learn.microsoft.com/en-us/win
-## Use [WDACConfig module](https://github.com/HotCakeX/Harden-Windows-Security/wiki/Deploy-SignedWDACConfig) to sign and deploy App Control policies
+## Use [AppControl Manager](https://github.com/HotCakeX/Harden-Windows-Security/wiki/AppControl-Manager) to sign and deploy App Control policies
-
-
-WDACConfig module with the `Deploy-SignedWDACConfig` [cmdlet](https://github.com/HotCakeX/Harden-Windows-Security/wiki/Deploy-SignedWDACConfig) can automate the entire process of signing and deploying a signed App Control policy.
-
-```powershell
-Deploy-SignedWDACConfig -CertPath
-
-> [!NOTE]\
-> The `Deploy-SignedWDACConfig` cmdlet will offer to automatically download the `SignTool.exe` from the Microsoft server if it cannot find it on your system.
-
-If you want to manually download it, here are the steps:
-
-* [Download the latest Windows stable SDK **installer**](https://developer.microsoft.com/en-us/windows/downloads/windows-sdk/)
-* [Download the latest Windows Insider SDK **ISO**](https://www.microsoft.com/en-us/software-download/windowsinsiderpreviewSDK)
+It supports creating certificates and signing, deploying and removing signed policies.
-Run it and only select `Windows SDK Signing Tools for Desktop Apps` to install. After that `signtool.exe` will be placed at `C:\Program Files (x86)\Windows Kits\10\bin` and the WDACConfig module will automatically detect and use it for signing. You can even copy the executable to another location for later usage on another system where SDK is not installed and then use the optional `-SignToolPath
diff --git a/Wiki posts/Windows Defender Application Control (WDAC)/How to Use Microsoft Defender for Endpoint Advanced Hunting With WDAC App Control.md b/Wiki posts/Windows Defender Application Control (WDAC)/How to Use Microsoft Defender for Endpoint Advanced Hunting With WDAC App Control.md
index 2a75a0c3d..96c04bc25 100644
--- a/Wiki posts/Windows Defender Application Control (WDAC)/How to Use Microsoft Defender for Endpoint Advanced Hunting With WDAC App Control.md
+++ b/Wiki posts/Windows Defender Application Control (WDAC)/How to Use Microsoft Defender for Endpoint Advanced Hunting With WDAC App Control.md
@@ -4,7 +4,7 @@ App Control for Business is a highly effective security feature that empowers yo
The application whitelisting approach serves as a potent defense against emerging and unknown threats. By emphasizing the identification of trusted applications, it automatically blocks any software that falls outside this trusted realm.
-Microsoft Defender for Endpoint (MDE) is one of the tools that can be used by enterprises and organizations to develop the trusted applications policy and mange it at scale. MDE provides the intelligence and insights needed to create and maintain a robust application control policy through its Advanced Hunting feature. This feature uses KQL [(Kusto Query Language)](https://learn.microsoft.com/en-us/azure/data-explorer/kusto/query/) to query the data collected by MDE and using the WDACConfig module, we can turn this actionable data into App Control policies. We can then use Intune to deploy these policies to our endpoints. All of these tools are built for scalability.
+Microsoft Defender for Endpoint (MDE) is one of the tools that can be used by enterprises and organizations to develop a trusted application policy and manage it at scale. MDE provides the intelligence and insights needed to create and maintain a robust application control policy through its Advanced Hunting feature. This feature uses KQL [(Kusto Query Language)](https://learn.microsoft.com/en-us/azure/data-explorer/kusto/query/) to query the data collected by MDE and using the [AppControl Manager](https://github.com/HotCakeX/Harden-Windows-Security/wiki/AppControl-Manager), we can turn this actionable data into App Control policies. We can then use Intune to deploy these policies to our endpoints. All of these tools are built for scalability.
@@ -17,27 +17,11 @@ Microsoft Defender for Endpoint (MDE) is one of the tools that can be used by en
To start, we need our endpoints to be generating data and intelligence we can work with. These data points are the Code Integrity and AppLocker events. These events are generated when an application or file is blocked or audited by App Control, or when a script or MSI file is blocked or audited by AppLocker. We can trigger the data generation by deploying App Control policies to our endpoints in Audit mode. This mode will not block any applications, instead it will generate data points for any application, file, script, MSI file and so on that would have been blocked if the policy was in Enforce mode.
-You can create Audit mode policies using the WDACConfig module based on different levels of trust.
+You can create Audit mode policies using the [AppControl Manager](https://github.com/HotCakeX/Harden-Windows-Security/wiki/AppControl-Manager) based on different levels of trust. [Use this page](https://github.com/HotCakeX/Harden-Windows-Security/wiki/Create-App-Control-Policy) to see what kind of audit events each base policy template generates when deployed in audit mode.
-For instance, the following command will create an Audit mode policy that once deployed on an endpoint, starts generating Audit logs for any file that runs but is not part of the Windows by default.
+For instance, once the DefaultWindows template is deployed on an endpoint, it starts generating Audit logs for any file that runs but is not part of the Windows by default. On the other hand, deploying the AllowMicrosoft base policy in Audit mode starts generating Audit logs for any file that runs but is not signed by Microsoft certificates.
-```powershell
-New-WDACConfig -PolicyType DefaultWindows -Audit
-```
-
-
-
-Another option would be the following command, which will create an Audit mode policy that once deployed, starts generating Audit logs for any file that runs but is not signed by Microsoft certificates.
-
-```powershell
-New-WDACConfig -PolicyType AllowMicrosoft -Audit
-```
-
-
-
-Please refer to [this document](https://github.com/HotCakeX/Harden-Windows-Security/wiki/New-WDACConfig) for further info about the commands.
-
-You will then use Intune to deploy the generated policies to as many endpoints as you want.
+After generating the policy files using the app, you will then use Intune to deploy them to as many endpoints as you want.
> [!TIP]\
> [Deploy App Control policies using Mobile Device Management (MDM)](https://learn.microsoft.com/en-us/windows/security/application-security/application-control/app-control-for-business/deployment/deploy-appcontrol-policies-using-intune)
@@ -46,7 +30,7 @@ You will then use Intune to deploy the generated policies to as many endpoints a
## Collecting the Data from MDE Advanced Hunting
-Now we need to collect the data from MDE Advanced Hunting. We can customize this query to be more specific to our environment, for instance by targeting specific devices and so on, but the following query will give us a good starting point by collecting all of the Code Integrity and AppLocker events:
+Now we need to collect the data from MDE Advanced Hunting. The following query will give us a good starting point by collecting all of the Code Integrity and AppLocker events:
```kql
DeviceEvents
@@ -57,12 +41,27 @@ DeviceEvents
+We can customize the query to be more specific to our environment, for instance by targeting an specific device among all the devices:
+
+```kql
+
+DeviceEvents
+| where (ActionType startswith "AppControlCodeIntegrity"
+ or ActionType startswith "AppControlCIScriptBlocked"
+ or ActionType startswith "AppControlCIScriptAudited")
+ and DeviceName == "mainframe"
+```
+
+`mainframe` in this example is the name of our device.
+
+
+
> [!NOTE]\
> You can access Microsoft Defender for Endpoint's portal by navigating to: [https://security.microsoft.com](https://security.microsoft.com)
-That query generates a standard output of the data in CSV file format which is compatible with what the [WDACConfig module](https://github.com/HotCakeX/Harden-Windows-Security/wiki/WDACConfig) requires in order to generate App Control policies. If you want to customize the query further, make sure the subsequent filters are applied after the initial query to ensure correct data format.
+That query generates a standard output of the data in CSV file format which is compatible with what the [AppControl Manager](https://github.com/HotCakeX/Harden-Windows-Security/wiki/AppControl-Manager) requires in order to generate App Control policies. If you want to customize the query further, make sure the subsequent filters are applied after the initial query to ensure correct data format.
@@ -85,28 +84,20 @@ That query generates a standard output of the data in CSV file format which is c
## Generating the App Control Policies
-After exporting the data from MDE Advanced Hunting, we can use the [**WDACConfig module**](https://github.com/HotCakeX/Harden-Windows-Security/wiki/WDACConfig) to generate App Control policies. We need to feed the CSV file(s) we collected MDE Advanced Hunting data into the module like so:
-
-```powershell
-ConvertTo-WDACPolicy -Source MDEAdvancedHunting -MDEAHLogs
-### WDACConfig Features For MDE Advanced Hunting
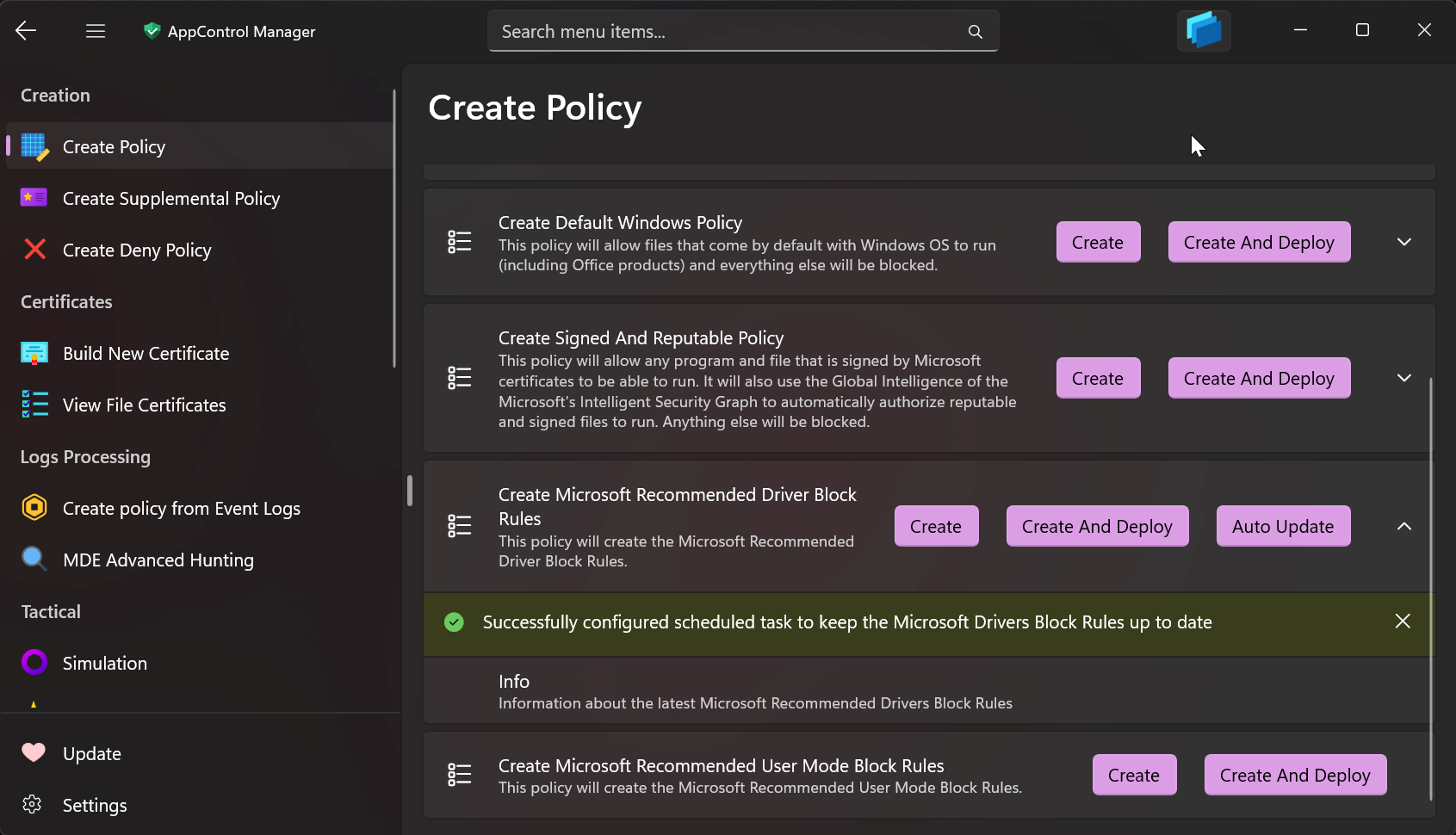
+### AppControl Manager Features For MDE Advanced Hunting
* Systematic approach for converting the MDE AH data to App Control policy with high precision and performance
* Uses parallel processing to speed up the policy generation process
* Provides a GUI for filtering the logs based on various criteria
* Never includes duplicate rules in the policy, regardless of the number of the duplicate logs you give it
-### The Module Can Create 3 Types of Rules for Files:
+### The App Can Create 3 Types of Rules for Files:
+
+You can choose the level based on which the logs will be scanned. By default, the following rules apply to the scan:
* If a file is unsigned then a hash rule will be created for it.
* If a file is signed then there are multiple possibilities:
@@ -117,29 +108,9 @@ These levels are selected based on their security. You can read more about the l
-### Video Demonstration
-
-The following video demonstrates the process of collecting the data from MDE Advanced Hunting and generating App Control policies using the WDACConfig module
-
- -
-
-
-
-
## Deploying the App Control Policies
-After generating the Supplemental policies based off of the MDE Advanced Hunting data, you need to remove the Audit mode policies you deployed to your endpoints initially and replace them with Enforced mode policies.
-
-#### [Generate Allow Microsoft Base Policy (Enforced Mode)](https://github.com/HotCakeX/Harden-Windows-Security/wiki/New-WDACConfig#new-wdacconfig--policytype)
-
-```powershell
-New-WDACConfig -PolicyType AllowMicrosoft
-```
-
-#### [Generate Default Windows Base Policy (Enforced Mode)](https://github.com/HotCakeX/Harden-Windows-Security/wiki/New-WDACConfig#new-wdacconfig--policytype)
-
-```powershell
-New-WDACConfig -PolicyType DefaultWindows
-```
+After generating the Supplemental policies based off of the MDE Advanced Hunting data, you need to remove the Audit mode policies you deployed to your endpoints initially and replace them with Enforced mode policies. [AppControl Manager offers an easy way to do so.](https://github.com/HotCakeX/Harden-Windows-Security/wiki/System-Information)
diff --git a/Wiki posts/Windows Defender Application Control (WDAC)/Introduction.md b/Wiki posts/Windows Defender Application Control (WDAC)/Introduction.md
index 37475834d..94d7b5912 100644
--- a/Wiki posts/Windows Defender Application Control (WDAC)/Introduction.md
+++ b/Wiki posts/Windows Defender Application Control (WDAC)/Introduction.md
@@ -1,7 +1,7 @@
# What is Application Control for Business?
 +
+
@@ -32,9 +32,9 @@ There are many ways you can utilize Application Control features and here they a
- [The built-in driver blocklist is updated with each new major release of Windows, typically 1-2 times per year.](https://learn.microsoft.com/en-us/windows/security/application-security/application-control/app-control-for-business/design/microsoft-recommended-driver-block-rules)
2. Update Microsoft recommended driver block rules outside of the twice a year schedule.
- - The drivers block list itself [is updated more frequently](https://github.com/MicrosoftDocs/windows-itpro-docs/commits/public/windows/security/application-security/application-control/windows-defender-application-control/design/microsoft-recommended-driver-block-rules.md) than twice a year schedule, [use the WDACConfig Module to setup a scheduled task that keeps the list up-to-date.](https://github.com/HotCakeX/Harden-Windows-Security/wiki/Fast-and-Automatic-Microsoft-Recommended-Driver-Block-Rules-updates)
+ - The drivers block list itself [is updated more frequently](https://github.com/MicrosoftDocs/windows-itpro-docs/commits/public/windows/security/application-security/application-control/windows-defender-application-control/design/microsoft-recommended-driver-block-rules.md) than twice a year schedule, [use the AppControl Manager to setup a scheduled task that keeps the list up-to-date.](https://github.com/HotCakeX/Harden-Windows-Security/wiki/Fast-and-Automatic-Microsoft-Recommended-Driver-Block-Rules-updates)
3. Use Microsoft recommended block rules + Recommended driver block rules
- - Use the [WDACConfig Module](https://github.com/HotCakeX/Harden-Windows-Security/wiki/New-WDACConfig#new-wdacconfig--getblockrules) to easily deploy the User-Mode Microsoft recommended block rules on your system.
+ - Use the [AppControl Manager](https://github.com/HotCakeX/Harden-Windows-Security/wiki/AppControl-Manager) to easily deploy the User-Mode Microsoft recommended block rules on your system.
4. Create WDAC policy for **Lightly managed devices**
- [Microsoft's guide: Create a WDAC policy for lightly managed devices](https://learn.microsoft.com/en-us/windows/security/application-security/application-control/app-control-for-business/design/create-appcontrol-policy-for-lightly-managed-devices)
- [My guide: WDAC for Lightly Managed Devices](https://github.com/HotCakeX/Harden-Windows-Security/wiki/WDAC-for-Lightly-Managed-Devices)
diff --git a/Wiki posts/Windows Defender Application Control (WDAC)/Script Enforcement and PowerShell Constrained Language Mode in WDAC App Control Policies.md b/Wiki posts/Windows Defender Application Control (WDAC)/Script Enforcement and PowerShell Constrained Language Mode in WDAC App Control Policies.md
index 893fe3ba5..23e524337 100644
--- a/Wiki posts/Windows Defender Application Control (WDAC)/Script Enforcement and PowerShell Constrained Language Mode in WDAC App Control Policies.md
+++ b/Wiki posts/Windows Defender Application Control (WDAC)/Script Enforcement and PowerShell Constrained Language Mode in WDAC App Control Policies.md
@@ -1,4 +1,4 @@
-# Script Enforcement and PowerShell Constrained Language Mode in WDAC App Control Policies
+# Script Enforcement and PowerShell Constrained Language Mode in App Control Policies
## Introduction
@@ -102,23 +102,22 @@ As you can see, we need the TBS Hash value of the root certificate.
-### Use the WDACConfig Module to Automatically Allow Certificates
+### Use the AppControl Manager to Automatically Allow Certificates
-You can use the WDACConfig module to create a supplemental policy that allows the certificates you select to be allowed by App Control. To do that, you can use the following command:
+You can use the [AppControl Manager](https://github.com/HotCakeX/Harden-Windows-Security/wiki/AppControl-Manager) to create a supplemental policy that allows the certificates you select to be allowed by App Control.
-```powershell
-New-SupplementalWDACConfig -Certificates -CertificatePaths "certificate.cer" -SuppPolicyName '
-A manual way to get the TBS Hash value of a certificate is using the following command, which also works for signed files and will show the details of the certificates in the chain as well.
-```powershell
-certutil.exe –v 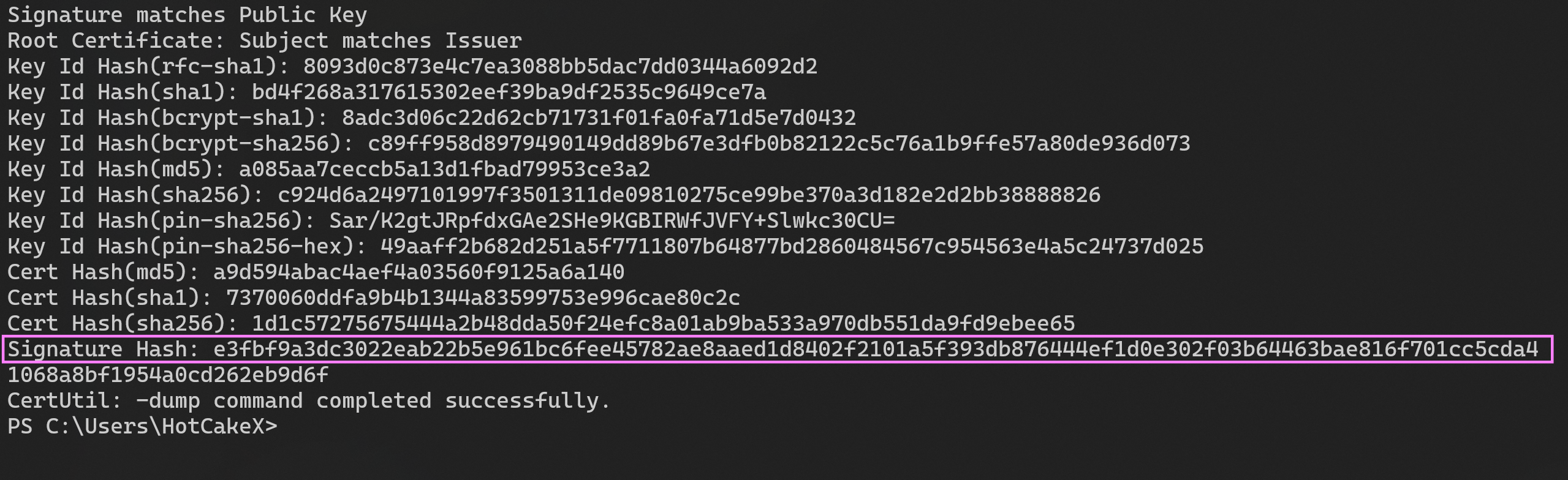 @@ -133,8 +132,3 @@ When an App Control policy with script enforcement is deployed and you try to im
* The module you're trying to load is signed but at least one of its files is tampered with and has a hash mismatch. Even adding a single space on an empty line causes hash mismatch, **which is expected**.
@@ -133,8 +132,3 @@ When an App Control policy with script enforcement is deployed and you try to im
* The module you're trying to load is signed but at least one of its files is tampered with and has a hash mismatch. Even adding a single space on an empty line causes hash mismatch, **which is expected**.
-
-> [!IMPORTANT]\
-> WDACConfig module is currently not compatible with constrained language mode due to using advanced PowerShell features that are not allowed in that mode.
-
-
diff --git a/Wiki posts/Windows Defender Application Control (WDAC)/WDAC Notes.md b/Wiki posts/Windows Defender Application Control (WDAC)/WDAC Notes.md
index 98f76e2ec..bd2b55725 100644
--- a/Wiki posts/Windows Defender Application Control (WDAC)/WDAC Notes.md
+++ b/Wiki posts/Windows Defender Application Control (WDAC)/WDAC Notes.md
@@ -1,4 +1,4 @@
-# Important Notes and Tips about WDAC policies
+# Important Notes and Tips about App Control policies
* App Control for Business was formerly known as WDAC (Windows Defender Application Control)
* It's used for Application and File whitelisting in Windows.
@@ -466,7 +466,7 @@ In order to automatically remove unnecessary things from a policy file, such as
Merge-CIPolicy .\Policy.xml -OutputFilePath .\Policy1.xml
```
-It essentially merges a policy with itself, adding `_0` to each ID and SignerID of the xml nodes which is easily removable using WDACConfig module, **although it's not necessary to remove them at all, they are perfectly fine.**
+It essentially merges a policy with itself, adding `_0` to each ID and SignerID of the xml nodes.
diff --git a/Wiki posts/Windows Defender Application Control (WDAC)/WDAC Rule Levels Comparison and Guide.md b/Wiki posts/Windows Defender Application Control (WDAC)/WDAC Rule Levels Comparison and Guide.md
index c8dd2c58f..9c1fb353f 100644
--- a/Wiki posts/Windows Defender Application Control (WDAC)/WDAC Rule Levels Comparison and Guide.md
+++ b/Wiki posts/Windows Defender Application Control (WDAC)/WDAC Rule Levels Comparison and Guide.md
@@ -1,4 +1,4 @@
-# WDAC Rule Levels Comparison and Guide
+# App Control Rule Levels Comparison and Guide
This document lists all of the levels of App Control rules. **From Top to bottom, from the most secure to the least secure**, the levels are: