})
diff --git a/docs/integrations/microsoft-azure/microsoft-entra-id-protection.md b/docs/integrations/microsoft-azure/microsoft-entra-id-protection.md
deleted file mode 100644
index 76ce618163..0000000000
--- a/docs/integrations/microsoft-azure/microsoft-entra-id-protection.md
+++ /dev/null
@@ -1,52 +0,0 @@
----
-id: microsoft-entra-id-protection
-title: Microsoft Entra ID Protection
-sidebar_label: Microsoft Entra ID Protection
-description: The Sumo Logic App for Microsoft Entra ID Protection outlines the steps required to collect and analyze the alert data from the Azure security platform to the Sumo Logic platform.
----
-
-import useBaseUrl from '@docusaurus/useBaseUrl';
-
-
})
-
-Microsoft Entra ID Protection is a cloud-based identity security solution that helps you detect, investigate, and remediate identity-based risks in real time. It is a key component of the Microsoft Entra suite, which focuses on securing access to applications and data across cloud and on-premises environments.
-
-This document outlines the steps required to collect and analyse the [Microsoft Entra ID Protection](https://learn.microsoft.com/en-us/entra/id-protection/overview-identity-protection) alerts in the Sumo Logic platform.
-
-## Set up collection
-
-:::note
-Skip this step if you have already configured the Microsoft Graph Security API Source.
-:::
-
-Use the [Cloud-to-Cloud Integration for Microsoft Graph Security API](/docs/send-data/hosted-collectors/cloud-to-cloud-integration-framework/microsoft-graph-security-api-source/) to ingest security alerts data from the Microsoft Entra ID Protection to the Sumo Logic platform.
-
-## Search alerts
-
-Use the following query to retrieve alerts generated by the Microsoft Entra ID Protection.
-
-```sql
-_sourcecategory=Labs/MicrosoftGraphSecurity
-| json field=_raw "serviceSource" as service_source
-| where service_source = "azureAdIdentityProtection"
-```
-
-## Analyse alerts
-
-Use the following query to extract detailed insights from the alert data:
-
-```sql
-_sourceCategory=Labs/MicrosoftGraphSecurity
-|json"id","status","severity","category","title","description","classification","determination","serviceSource","detectionSource","alertWebUrl" ,"comments[*]","evidence[*]"as alert_id,status,severity,category,title,description,classification,determination,service_source,detection_source,alert_url,comments,evidence_info nodrop
-| where service_source = "azureAdIdentityProtection"
-| where severity matches "*" and status matches "*" and classification matches "*"
-| if(isNull(category),"-",category) as category
-| if(isNull(classification),"-",classification) as classification
-| if(isNull(determination),"-",determination) as determination
-| count by _messageTime,status,severity,category,title,description,classification,determination,alert_url,alert_id
-| formatDate(toLong(_messageTime), "dd-MM-yyyy HH:mm:ss") as time
-| tourl (alert_url,alert_id) as alert_id
-| fields time,alert_id,title,description,alert_url,status,severity,category,classification,determination
-| fields -_messageTime
-| sort by time
-```
\ No newline at end of file
diff --git a/docs/integrations/product-list/product-list-a-l.md b/docs/integrations/product-list/product-list-a-l.md
index 0338850540..fe393d7fdf 100644
--- a/docs/integrations/product-list/product-list-a-l.md
+++ b/docs/integrations/product-list/product-list-a-l.md
@@ -119,7 +119,7 @@ For descriptions of the different types of integrations Sumo Logic offers, see [
|
})
| [AWS Simple Notification Service](https://aws.amazon.com/sns/) | Automation integration: [AWS Simple Notification Service](/docs/platform-services/automation-service/app-central/integrations/aws-simple-notification-service/) |
|
})
| [AWS WAF](https://aws.amazon.com/waf/) | Apps:
- [AWS WAF](/docs/integrations/amazon-aws/waf/)
- [AWS WAF Cloud Security Monitoring and Analytics](/docs/integrations/cloud-security-monitoring-analytics/aws-waf/)
Automation integration: [AWS WAF](/docs/platform-services/automation-service/app-central/integrations/aws-waf/)
Cloud SIEM integration: [Amazon AWS - Web Application Firewall (WAF)](https://github.com/SumoLogic/cloud-siem-content-catalog/blob/master/products/072b85a2-1765-45c2-911d-b0509880326e.md) |
|
})
| [Axonius](https://www.axonius.com/) | Automation integration: [Axonius](/docs/platform-services/automation-service/app-central/integrations/axonius/) |
-|
})
| [Azure](https://azure.microsoft.com/en-us) | Apps:
- [Azure Analysis Services](/docs/integrations/microsoft-azure/azure-analysis-services/)
- [Azure API Management](/docs/integrations/microsoft-azure/azure-api-management/)
- [Azure App Configuration](/docs/integrations/microsoft-azure/azure-app-configuration/)
- [Azure Application Gateway](/docs/integrations/microsoft-azure/azure-application-gateway/)
- [Azure App Service Environment](/docs/integrations/microsoft-azure/azure-app-service-environment/)
- [Azure App Service Plan](/docs/integrations/microsoft-azure/azure-app-service-plan/)
- [Azure Audit](/docs/integrations/microsoft-azure/audit/)
- [Azure Automation](/docs/integrations/microsoft-azure/azure-automation/)
- [Azure Backup](/docs/integrations/microsoft-azure/azure-backup/)
- [Azure Batch](/docs/integrations/microsoft-azure/azure-batch/)
- [Azure Cache for Redis](/docs/integrations/microsoft-azure/azure-cache-for-redis/)
- [Azure Cognitive Search](/docs/integrations/microsoft-azure/azure-cognitive-search/)
- [Azure Container Instances](/docs/integrations/microsoft-azure/azure-container-instances/)
- [Azure Cosmos DB](/docs/integrations/microsoft-azure/azure-cosmos-db/)
- [Azure Cosmos DB for PostgreSQL](/docs/integrations/microsoft-azure/azure-cosmos-db-for-postgresql/)
- [Azure Data Explorer](/docs/integrations/microsoft-azure/azure-data-explorer/)
- [Azure Data Factory](/docs/integrations/microsoft-azure/azure-data-factory/)
- [Azure Database for MariaDB](/docs/integrations/microsoft-azure/azure-database-for-mariadb/)
- [Azure Database for MySQL](/docs/integrations/microsoft-azure/azure-database-for-mysql/)
- [Azure Database for PostgreSQL](/docs/integrations/microsoft-azure/azure-database-for-postgresql/)
- [Azure Event Grid](/docs/integrations/microsoft-azure/azure-event-grid/)
- [Azure Event Hubs](/docs/integrations/microsoft-azure/azure-event-hubs/)
- [Azure Front Door](/docs/integrations/microsoft-azure/azure-front-door/)
- [Azure Functions](/docs/integrations/microsoft-azure/azure-functions/)
- [Azure HDInsight](/docs/integrations/microsoft-azure/azure-hdinsight/)
- [Azure IoT Hub](/docs/integrations/microsoft-azure/azure-iot-hub/)
- [Azure Key Vault](/docs/integrations/microsoft-azure/azure-key-vault/)
- [Azure Kubernetes Service (AKS) - Control Plane](/docs/integrations/microsoft-azure/kubernetes/)
- [Azure Load Balancer](/docs/integrations/microsoft-azure/azure-load-balancer/)
- [Azure Logic App](/docs/integrations/microsoft-azure/azure-logic-app/)
- [Azure Machine Learning](/docs/integrations/microsoft-azure/azure-machine-learning/)
- [Azure Monitor Logs](/docs/send-data/collect-from-other-data-sources/azure-monitoring/ms-azure-event-hubs-source)
- [Azure Monitor Metrics](/docs/send-data/collect-from-other-data-sources/azure-monitoring/collect-metrics-azure-monitor/)
- [Azure Monitoring](/docs/send-data/collect-from-other-data-sources/azure-monitoring/)
- [Azure Network Interface](/docs/integrations/microsoft-azure/azure-network-interface/)
- [Azure Network Watcher](/docs/integrations/microsoft-azure/network-watcher/)
- [Azure Notification Hubs](/docs/integrations/microsoft-azure/azure-notification-hubs/)
- [Azure OpenAI](/docs/integrations/microsoft-azure/azure-open-ai/)
- [Azure Public IP Addresses](/docs/integrations/microsoft-azure/azure-public-ipAddress/)
- [Azure Relay](/docs/integrations/microsoft-azure/azure-relay/)
- [Azure Security -Advisor](/docs/integrations/microsoft-azure/azure-security-advisor/)
- [Azure Security - Defender for Cloud](/docs/integrations/microsoft-azure/azure-security-defender-for-cloud/)
- [Azure Security - Microsoft Defender for Cloud Apps](/docs/integrations/microsoft-azure/azure-security-microsoft-defender-for-cloud-apps/)
- [Azure Security - Microsoft Defender for Endpoint](/docs/integrations/microsoft-azure/microsoft-defender-for-endpoint/)
- [Azure Security - Microsoft Defender for Identity](/docs/integrations/microsoft-azure/azure-security-microsoft-defender-for-identity)
- [Azure Security - Microsoft Defender for Office 365](/docs/integrations/microsoft-azure/azure-security-microsoft-defender-for-office-365)
- [Azure Service Bus](/docs/integrations/microsoft-azure/azure-service-bus/)
- [Azure SQL](/docs/integrations/microsoft-azure/sql/)
- [Azure SQL Elastic Pool](/docs/integrations/microsoft-azure/azure-sql-elastic-pool/)
- [Azure SQL Managed Instance](/docs/integrations/microsoft-azure/azure-sql-managed-instance/)
- [Azure Storage](/docs/integrations/microsoft-azure/azure-storage/)
- [Azure Stream Analytics](/docs/integrations/microsoft-azure/azure-stream-analytics/)
- [Azure Synapse Analytics](/docs/integrations/microsoft-azure/azure-synapse-analytics/)
- [Azure Virtual Network](/docs/integrations/microsoft-azure/azure-virtual-network/)
- [Azure Virtual Machine](/docs/integrations/microsoft-azure/azure-virtual-machine/)
- [Azure Web Apps](/docs/integrations/microsoft-azure/web-apps/)
Automation integration: [Azure AD](/docs/platform-services/automation-service/app-central/integrations/azure-ad/)
Collectors:
- [Azure Blob Storage](/docs/send-data/collect-from-other-data-sources/azure-blob-storage/block-blob/collect-logs)
- [Azure Event Hubs Source](/docs/send-data/hosted-collectors/cloud-to-cloud-integration-framework/azure-event-hubs-source/)
- [Migrating to Azure Event Hubs Cloud-to-Cloud Source](/docs/send-data/collect-from-other-data-sources/azure-monitoring/azure-event-hubs-source-migration)
Webhook: [Webhook Connection for Microsoft Azure Functions](/docs/alerts/webhook-connections/microsoft-azure-functions/) |
+|
})
| [Azure](https://azure.microsoft.com/en-us) | Apps:
- [Azure Analysis Services](/docs/integrations/microsoft-azure/azure-analysis-services/)
- [Azure API Management](/docs/integrations/microsoft-azure/azure-api-management/)
- [Azure App Configuration](/docs/integrations/microsoft-azure/azure-app-configuration/)
- [Azure Application Gateway](/docs/integrations/microsoft-azure/azure-application-gateway/)
- [Azure App Service Environment](/docs/integrations/microsoft-azure/azure-app-service-environment/)
- [Azure App Service Plan](/docs/integrations/microsoft-azure/azure-app-service-plan/)
- [Azure Audit](/docs/integrations/microsoft-azure/audit/)
- [Azure Automation](/docs/integrations/microsoft-azure/azure-automation/)
- [Azure Backup](/docs/integrations/microsoft-azure/azure-backup/)
- [Azure Batch](/docs/integrations/microsoft-azure/azure-batch/)
- [Azure Cache for Redis](/docs/integrations/microsoft-azure/azure-cache-for-redis/)
- [Azure Cognitive Search](/docs/integrations/microsoft-azure/azure-cognitive-search/)
- [Azure Container Instances](/docs/integrations/microsoft-azure/azure-container-instances/)
- [Azure Cosmos DB](/docs/integrations/microsoft-azure/azure-cosmos-db/)
- [Azure Cosmos DB for PostgreSQL](/docs/integrations/microsoft-azure/azure-cosmos-db-for-postgresql/)
- [Azure Data Explorer](/docs/integrations/microsoft-azure/azure-data-explorer/)
- [Azure Data Factory](/docs/integrations/microsoft-azure/azure-data-factory/)
- [Azure Database for MariaDB](/docs/integrations/microsoft-azure/azure-database-for-mariadb/)
- [Azure Database for MySQL](/docs/integrations/microsoft-azure/azure-database-for-mysql/)
- [Azure Database for PostgreSQL](/docs/integrations/microsoft-azure/azure-database-for-postgresql/)
- [Azure Event Grid](/docs/integrations/microsoft-azure/azure-event-grid/)
- [Azure Event Hubs](/docs/integrations/microsoft-azure/azure-event-hubs/)
- [Azure Front Door](/docs/integrations/microsoft-azure/azure-front-door/)
- [Azure Functions](/docs/integrations/microsoft-azure/azure-functions/)
- [Azure HDInsight](/docs/integrations/microsoft-azure/azure-hdinsight/)
- [Azure IoT Hub](/docs/integrations/microsoft-azure/azure-iot-hub/)
- [Azure Key Vault](/docs/integrations/microsoft-azure/azure-key-vault/)
- [Azure Kubernetes Service (AKS) - Control Plane](/docs/integrations/microsoft-azure/kubernetes/)
- [Azure Load Balancer](/docs/integrations/microsoft-azure/azure-load-balancer/)
- [Azure Logic App](/docs/integrations/microsoft-azure/azure-logic-app/)
- [Azure Machine Learning](/docs/integrations/microsoft-azure/azure-machine-learning/)
- [Azure Monitor Logs](/docs/send-data/collect-from-other-data-sources/azure-monitoring/ms-azure-event-hubs-source)
- [Azure Monitor Metrics](/docs/send-data/collect-from-other-data-sources/azure-monitoring/collect-metrics-azure-monitor/)
- [Azure Monitoring](/docs/send-data/collect-from-other-data-sources/azure-monitoring/)
- [Azure Network Interface](/docs/integrations/microsoft-azure/azure-network-interface/)
- [Azure Network Watcher](/docs/integrations/microsoft-azure/network-watcher/)
- [Azure Notification Hubs](/docs/integrations/microsoft-azure/azure-notification-hubs/)
- [Azure OpenAI](/docs/integrations/microsoft-azure/azure-open-ai/)
- [Azure Public IP Addresses](/docs/integrations/microsoft-azure/azure-public-ipAddress/)
- [Azure Relay](/docs/integrations/microsoft-azure/azure-relay/)
- [Azure Security -Advisor](/docs/integrations/microsoft-azure/azure-security-advisor/)
- [Azure Security - Defender for Cloud](/docs/integrations/microsoft-azure/azure-security-defender-for-cloud/)
- [Azure Security - Microsoft Defender for Cloud Apps](/docs/integrations/microsoft-azure/azure-security-microsoft-defender-for-cloud-apps/)
- [Azure Security - Microsoft Defender for Endpoint](/docs/integrations/microsoft-azure/microsoft-defender-for-endpoint/)
- [Azure Security - Microsoft Defender for Identity](/docs/integrations/microsoft-azure/azure-security-microsoft-defender-for-identity)
- [Azure Security - Microsoft Defender for Office 365](/docs/integrations/microsoft-azure/azure-security-microsoft-defender-for-office-365)
- [Azure Security - Microsoft Entra ID Protection](/docs/integrations/microsoft-azure/azure-security-microsoft-entra-id-protection/)
- [Azure Service Bus](/docs/integrations/microsoft-azure/azure-service-bus/)
- [Azure SQL](/docs/integrations/microsoft-azure/sql/)
- [Azure SQL Elastic Pool](/docs/integrations/microsoft-azure/azure-sql-elastic-pool/)
- [Azure SQL Managed Instance](/docs/integrations/microsoft-azure/azure-sql-managed-instance/)
- [Azure Storage](/docs/integrations/microsoft-azure/azure-storage/)
- [Azure Stream Analytics](/docs/integrations/microsoft-azure/azure-stream-analytics/)
- [Azure Synapse Analytics](/docs/integrations/microsoft-azure/azure-synapse-analytics/)
- [Azure Virtual Network](/docs/integrations/microsoft-azure/azure-virtual-network/)
- [Azure Virtual Machine](/docs/integrations/microsoft-azure/azure-virtual-machine/)
- [Azure Web Apps](/docs/integrations/microsoft-azure/web-apps/)
Automation integration: [Azure AD](/docs/platform-services/automation-service/app-central/integrations/azure-ad/)
Collectors:
- [Azure Blob Storage](/docs/send-data/collect-from-other-data-sources/azure-blob-storage/block-blob/collect-logs)
- [Azure Event Hubs Source](/docs/send-data/hosted-collectors/cloud-to-cloud-integration-framework/azure-event-hubs-source/)
- [Migrating to Azure Event Hubs Cloud-to-Cloud Source](/docs/send-data/collect-from-other-data-sources/azure-monitoring/azure-event-hubs-source-migration)
Webhook: [Webhook Connection for Microsoft Azure Functions](/docs/alerts/webhook-connections/microsoft-azure-functions/) |
## B
diff --git a/sidebars.ts b/sidebars.ts
index abf4bce0af..3e4a956d67 100644
--- a/sidebars.ts
+++ b/sidebars.ts
@@ -2248,9 +2248,9 @@ integrations: [
'integrations/microsoft-azure/azure-security-microsoft-defender-for-cloud-apps',
'integrations/microsoft-azure/azure-security-microsoft-defender-for-identity',
'integrations/microsoft-azure/azure-security-microsoft-defender-for-office-365',
+ 'integrations/microsoft-azure/azure-security-microsoft-entra-id-protection',
'integrations/microsoft-azure/microsoft-defender-for-endpoint',
'integrations/microsoft-azure/microsoft-dynamics365-customer-insights',
- 'integrations/microsoft-azure/microsoft-entra-id-protection',
'integrations/microsoft-azure/microsoft-purview-data-loss-prevention',
'integrations/microsoft-azure/network-watcher',
'integrations/microsoft-azure/sql',
diff --git a/static/img/integrations/microsoft-azure/azure-security-microsoft-entra-id-protection.png b/static/img/integrations/microsoft-azure/azure-security-microsoft-entra-id-protection.png
new file mode 100644
index 0000000000..5e15781e5b
Binary files /dev/null and b/static/img/integrations/microsoft-azure/azure-security-microsoft-entra-id-protection.png differ
})
})
}) +
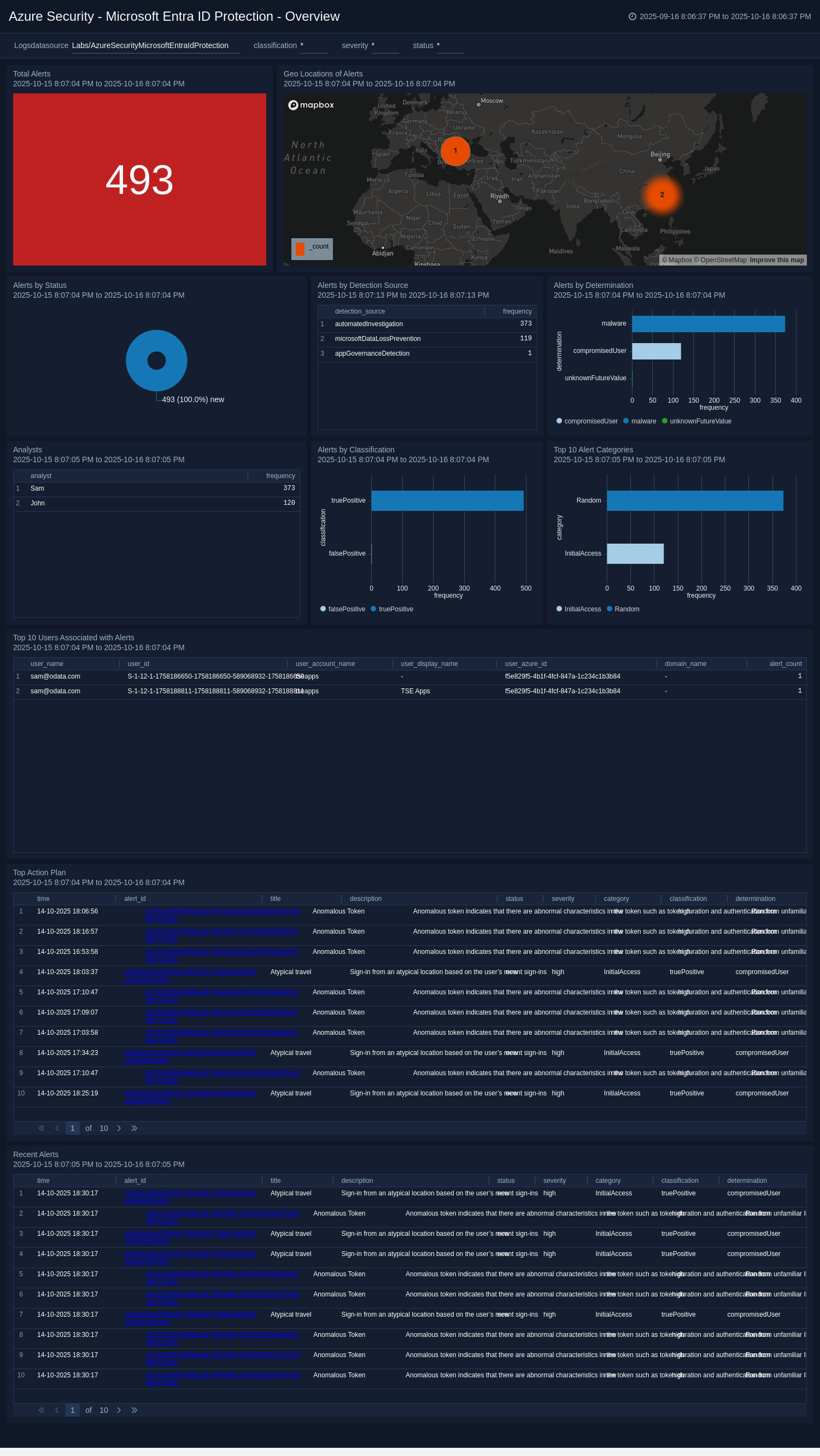
+The Azure Security – Microsoft Entra ID Protection application strengthens identity security within Azure environments by proactively detecting, investigating, and mitigating identity-related risks. It helps organizations safeguard user accounts and credentials against potential compromise, ensuring secure access to critical cloud resources
+
+The Sumo Logic app for Azure Security - Microsoft Entra ID Protection provides interactive dashboards and visual tools. The app supports incident identification, user activity tracking, and access monitoring for sensitive data. These features enable faster response times and more agile decision-making, ultimately helping organizations enhance their overall security posture. By delivering a comprehensive view of cloud app security, the app empowers you to manage threats efficiently and ensures robust protection of critical Azure-based assets.
+
+## Log Types
+
+The Azure Security – Microsoft Entra ID Protection uses Sumo Logic’s Microsoft Graph Security source to collect [alerts](https://learn.microsoft.com/en-us/graph/api/security-list-alerts_v2?view=graph-rest-1.0&tabs=http) from the Microsoft Graph Security source.
+
+### Sample log messages
+
+
+
+The Azure Security – Microsoft Entra ID Protection application strengthens identity security within Azure environments by proactively detecting, investigating, and mitigating identity-related risks. It helps organizations safeguard user accounts and credentials against potential compromise, ensuring secure access to critical cloud resources
+
+The Sumo Logic app for Azure Security - Microsoft Entra ID Protection provides interactive dashboards and visual tools. The app supports incident identification, user activity tracking, and access monitoring for sensitive data. These features enable faster response times and more agile decision-making, ultimately helping organizations enhance their overall security posture. By delivering a comprehensive view of cloud app security, the app empowers you to manage threats efficiently and ensures robust protection of critical Azure-based assets.
+
+## Log Types
+
+The Azure Security – Microsoft Entra ID Protection uses Sumo Logic’s Microsoft Graph Security source to collect [alerts](https://learn.microsoft.com/en-us/graph/api/security-list-alerts_v2?view=graph-rest-1.0&tabs=http) from the Microsoft Graph Security source.
+
+### Sample log messages
+
+ +
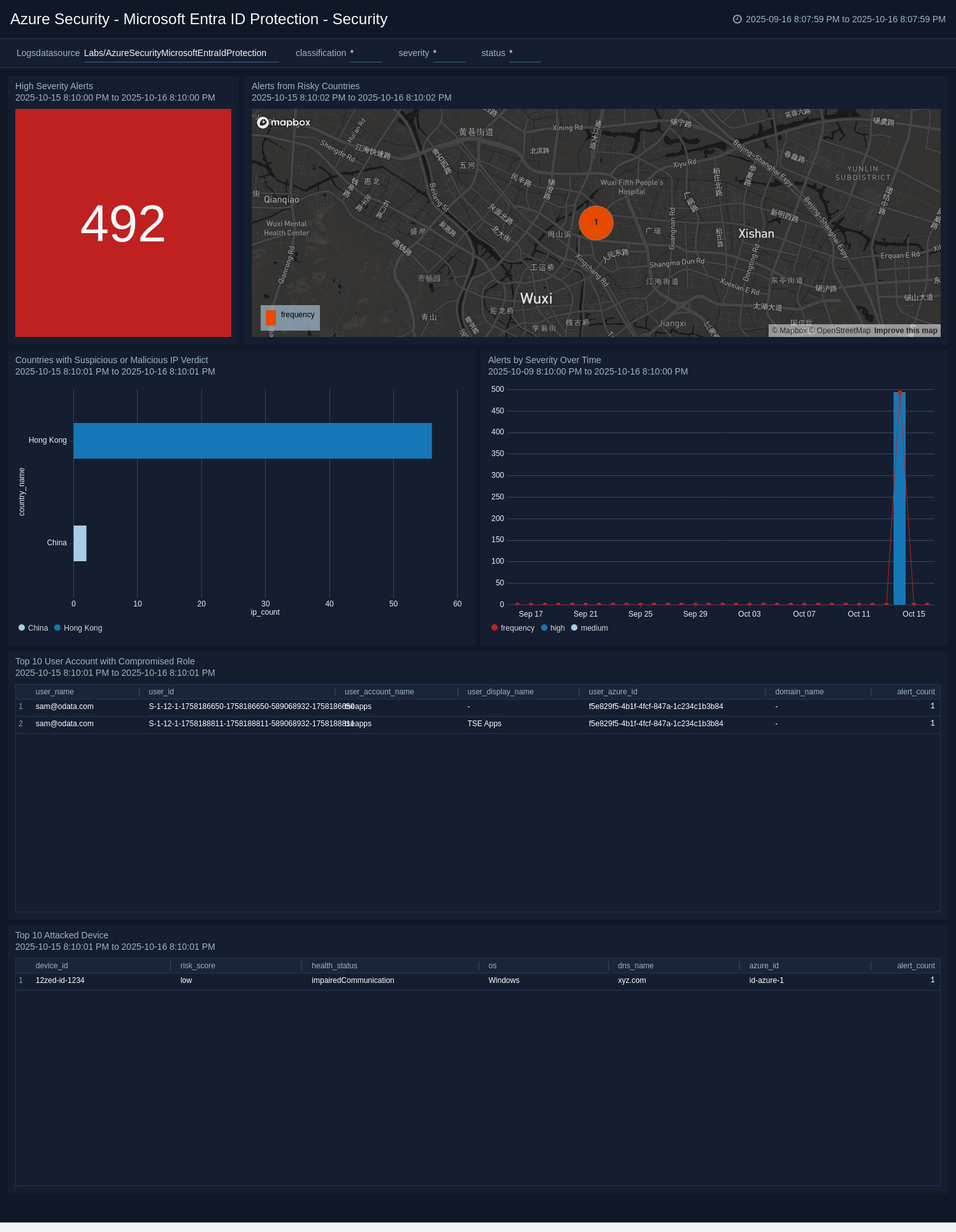
+### Security
+
+The **Azure Security - Microsoft Entra ID Protection - Security** dashboard provides a comprehensive overview of identity-related threats within the organization, enabling teams to pinpoint where identity risks are concentrated and how they evolve over time. Visual trend panels display fluctuations in user and sign-in risk levels, helping analysts assess whether identity-based attacks are increasing and prioritize mitigation accordingly.
+
+Key insights include compromised user accounts, frequently attacked devices, and countries linked to malicious IPs, enabling targeted defense strategies. By combining trend analysis with threat origins and user risk data, the dashboard empowers proactive threat response and strengthens overall security posture.
+
+
+### Security
+
+The **Azure Security - Microsoft Entra ID Protection - Security** dashboard provides a comprehensive overview of identity-related threats within the organization, enabling teams to pinpoint where identity risks are concentrated and how they evolve over time. Visual trend panels display fluctuations in user and sign-in risk levels, helping analysts assess whether identity-based attacks are increasing and prioritize mitigation accordingly.
+
+Key insights include compromised user accounts, frequently attacked devices, and countries linked to malicious IPs, enabling targeted defense strategies. By combining trend analysis with threat origins and user risk data, the dashboard empowers proactive threat response and strengthens overall security posture.
+ +
+## Upgrade/Downgrade the Azure Security - Microsoft Entra ID Protection app (Optional)
+
+import AppUpdate from '../../reuse/apps/app-update.md';
+
+
+
+## Upgrade/Downgrade the Azure Security - Microsoft Entra ID Protection app (Optional)
+
+import AppUpdate from '../../reuse/apps/app-update.md';
+
+})
}) diff --git a/docs/integrations/microsoft-azure/microsoft-entra-id-protection.md b/docs/integrations/microsoft-azure/microsoft-entra-id-protection.md
deleted file mode 100644
index 76ce618163..0000000000
--- a/docs/integrations/microsoft-azure/microsoft-entra-id-protection.md
+++ /dev/null
@@ -1,52 +0,0 @@
----
-id: microsoft-entra-id-protection
-title: Microsoft Entra ID Protection
-sidebar_label: Microsoft Entra ID Protection
-description: The Sumo Logic App for Microsoft Entra ID Protection outlines the steps required to collect and analyze the alert data from the Azure security platform to the Sumo Logic platform.
----
-
-import useBaseUrl from '@docusaurus/useBaseUrl';
-
-
diff --git a/docs/integrations/microsoft-azure/microsoft-entra-id-protection.md b/docs/integrations/microsoft-azure/microsoft-entra-id-protection.md
deleted file mode 100644
index 76ce618163..0000000000
--- a/docs/integrations/microsoft-azure/microsoft-entra-id-protection.md
+++ /dev/null
@@ -1,52 +0,0 @@
----
-id: microsoft-entra-id-protection
-title: Microsoft Entra ID Protection
-sidebar_label: Microsoft Entra ID Protection
-description: The Sumo Logic App for Microsoft Entra ID Protection outlines the steps required to collect and analyze the alert data from the Azure security platform to the Sumo Logic platform.
----
-
-import useBaseUrl from '@docusaurus/useBaseUrl';
-
-}) -
-Microsoft Entra ID Protection is a cloud-based identity security solution that helps you detect, investigate, and remediate identity-based risks in real time. It is a key component of the Microsoft Entra suite, which focuses on securing access to applications and data across cloud and on-premises environments.
-
-This document outlines the steps required to collect and analyse the [Microsoft Entra ID Protection](https://learn.microsoft.com/en-us/entra/id-protection/overview-identity-protection) alerts in the Sumo Logic platform.
-
-## Set up collection
-
-:::note
-Skip this step if you have already configured the Microsoft Graph Security API Source.
-:::
-
-Use the [Cloud-to-Cloud Integration for Microsoft Graph Security API](/docs/send-data/hosted-collectors/cloud-to-cloud-integration-framework/microsoft-graph-security-api-source/) to ingest security alerts data from the Microsoft Entra ID Protection to the Sumo Logic platform.
-
-## Search alerts
-
-Use the following query to retrieve alerts generated by the Microsoft Entra ID Protection.
-
-```sql
-_sourcecategory=Labs/MicrosoftGraphSecurity
-| json field=_raw "serviceSource" as service_source
-| where service_source = "azureAdIdentityProtection"
-```
-
-## Analyse alerts
-
-Use the following query to extract detailed insights from the alert data:
-
-```sql
-_sourceCategory=Labs/MicrosoftGraphSecurity
-|json"id","status","severity","category","title","description","classification","determination","serviceSource","detectionSource","alertWebUrl" ,"comments[*]","evidence[*]"as alert_id,status,severity,category,title,description,classification,determination,service_source,detection_source,alert_url,comments,evidence_info nodrop
-| where service_source = "azureAdIdentityProtection"
-| where severity matches "*" and status matches "*" and classification matches "*"
-| if(isNull(category),"-",category) as category
-| if(isNull(classification),"-",classification) as classification
-| if(isNull(determination),"-",determination) as determination
-| count by _messageTime,status,severity,category,title,description,classification,determination,alert_url,alert_id
-| formatDate(toLong(_messageTime), "dd-MM-yyyy HH:mm:ss") as time
-| tourl (alert_url,alert_id) as alert_id
-| fields time,alert_id,title,description,alert_url,status,severity,category,classification,determination
-| fields -_messageTime
-| sort by time
-```
\ No newline at end of file
diff --git a/docs/integrations/product-list/product-list-a-l.md b/docs/integrations/product-list/product-list-a-l.md
index 0338850540..fe393d7fdf 100644
--- a/docs/integrations/product-list/product-list-a-l.md
+++ b/docs/integrations/product-list/product-list-a-l.md
@@ -119,7 +119,7 @@ For descriptions of the different types of integrations Sumo Logic offers, see [
|
-
-Microsoft Entra ID Protection is a cloud-based identity security solution that helps you detect, investigate, and remediate identity-based risks in real time. It is a key component of the Microsoft Entra suite, which focuses on securing access to applications and data across cloud and on-premises environments.
-
-This document outlines the steps required to collect and analyse the [Microsoft Entra ID Protection](https://learn.microsoft.com/en-us/entra/id-protection/overview-identity-protection) alerts in the Sumo Logic platform.
-
-## Set up collection
-
-:::note
-Skip this step if you have already configured the Microsoft Graph Security API Source.
-:::
-
-Use the [Cloud-to-Cloud Integration for Microsoft Graph Security API](/docs/send-data/hosted-collectors/cloud-to-cloud-integration-framework/microsoft-graph-security-api-source/) to ingest security alerts data from the Microsoft Entra ID Protection to the Sumo Logic platform.
-
-## Search alerts
-
-Use the following query to retrieve alerts generated by the Microsoft Entra ID Protection.
-
-```sql
-_sourcecategory=Labs/MicrosoftGraphSecurity
-| json field=_raw "serviceSource" as service_source
-| where service_source = "azureAdIdentityProtection"
-```
-
-## Analyse alerts
-
-Use the following query to extract detailed insights from the alert data:
-
-```sql
-_sourceCategory=Labs/MicrosoftGraphSecurity
-|json"id","status","severity","category","title","description","classification","determination","serviceSource","detectionSource","alertWebUrl" ,"comments[*]","evidence[*]"as alert_id,status,severity,category,title,description,classification,determination,service_source,detection_source,alert_url,comments,evidence_info nodrop
-| where service_source = "azureAdIdentityProtection"
-| where severity matches "*" and status matches "*" and classification matches "*"
-| if(isNull(category),"-",category) as category
-| if(isNull(classification),"-",classification) as classification
-| if(isNull(determination),"-",determination) as determination
-| count by _messageTime,status,severity,category,title,description,classification,determination,alert_url,alert_id
-| formatDate(toLong(_messageTime), "dd-MM-yyyy HH:mm:ss") as time
-| tourl (alert_url,alert_id) as alert_id
-| fields time,alert_id,title,description,alert_url,status,severity,category,classification,determination
-| fields -_messageTime
-| sort by time
-```
\ No newline at end of file
diff --git a/docs/integrations/product-list/product-list-a-l.md b/docs/integrations/product-list/product-list-a-l.md
index 0338850540..fe393d7fdf 100644
--- a/docs/integrations/product-list/product-list-a-l.md
+++ b/docs/integrations/product-list/product-list-a-l.md
@@ -119,7 +119,7 @@ For descriptions of the different types of integrations Sumo Logic offers, see [
| }) | [AWS Simple Notification Service](https://aws.amazon.com/sns/) | Automation integration: [AWS Simple Notification Service](/docs/platform-services/automation-service/app-central/integrations/aws-simple-notification-service/) |
|
| [AWS Simple Notification Service](https://aws.amazon.com/sns/) | Automation integration: [AWS Simple Notification Service](/docs/platform-services/automation-service/app-central/integrations/aws-simple-notification-service/) |
| }) | [AWS WAF](https://aws.amazon.com/waf/) | Apps:
| [AWS WAF](https://aws.amazon.com/waf/) | Apps: }) | [Axonius](https://www.axonius.com/) | Automation integration: [Axonius](/docs/platform-services/automation-service/app-central/integrations/axonius/) |
-|
| [Axonius](https://www.axonius.com/) | Automation integration: [Axonius](/docs/platform-services/automation-service/app-central/integrations/axonius/) |
-| }) | [Azure](https://azure.microsoft.com/en-us) | Apps:
| [Azure](https://azure.microsoft.com/en-us) | Apps: }) | [Azure](https://azure.microsoft.com/en-us) | Apps:
| [Azure](https://azure.microsoft.com/en-us) | Apps: