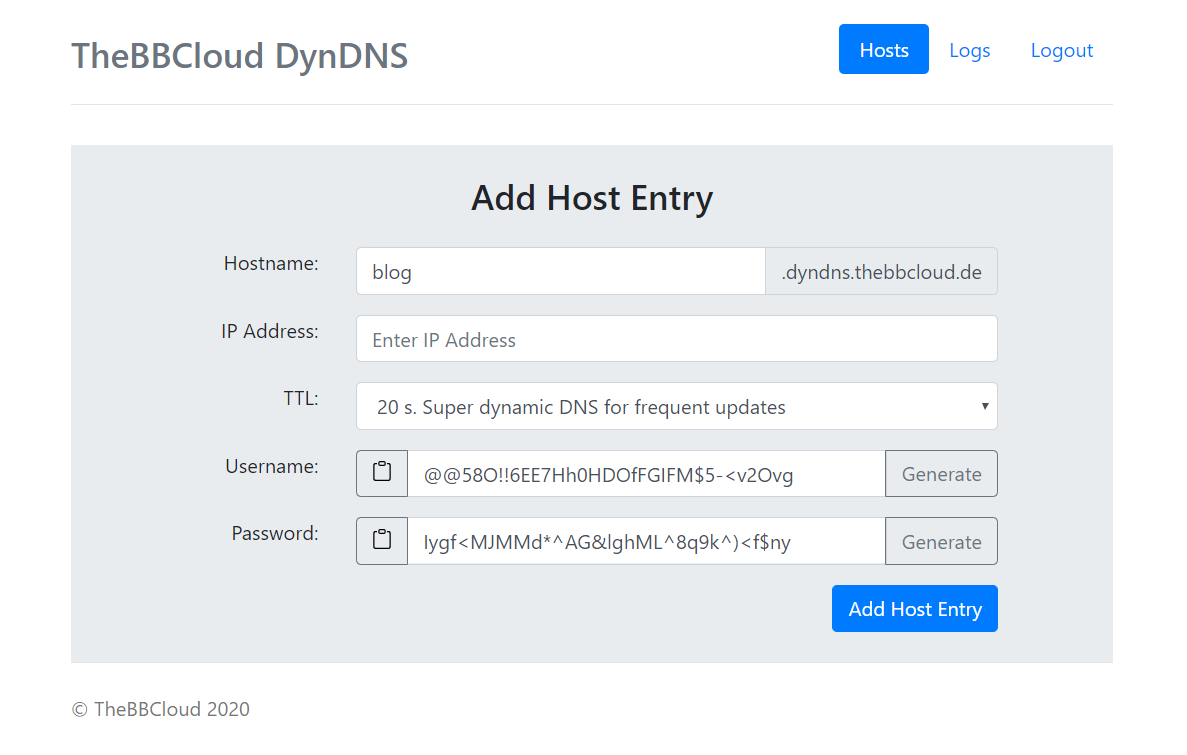
 -
-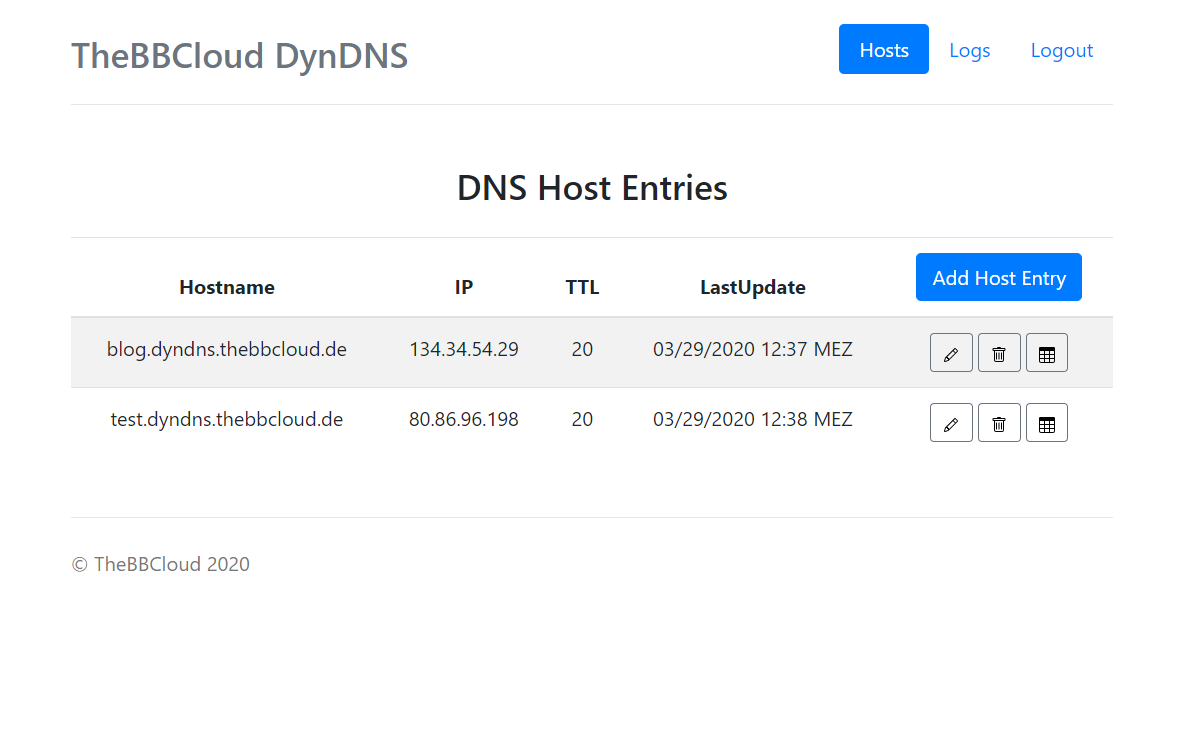 -
-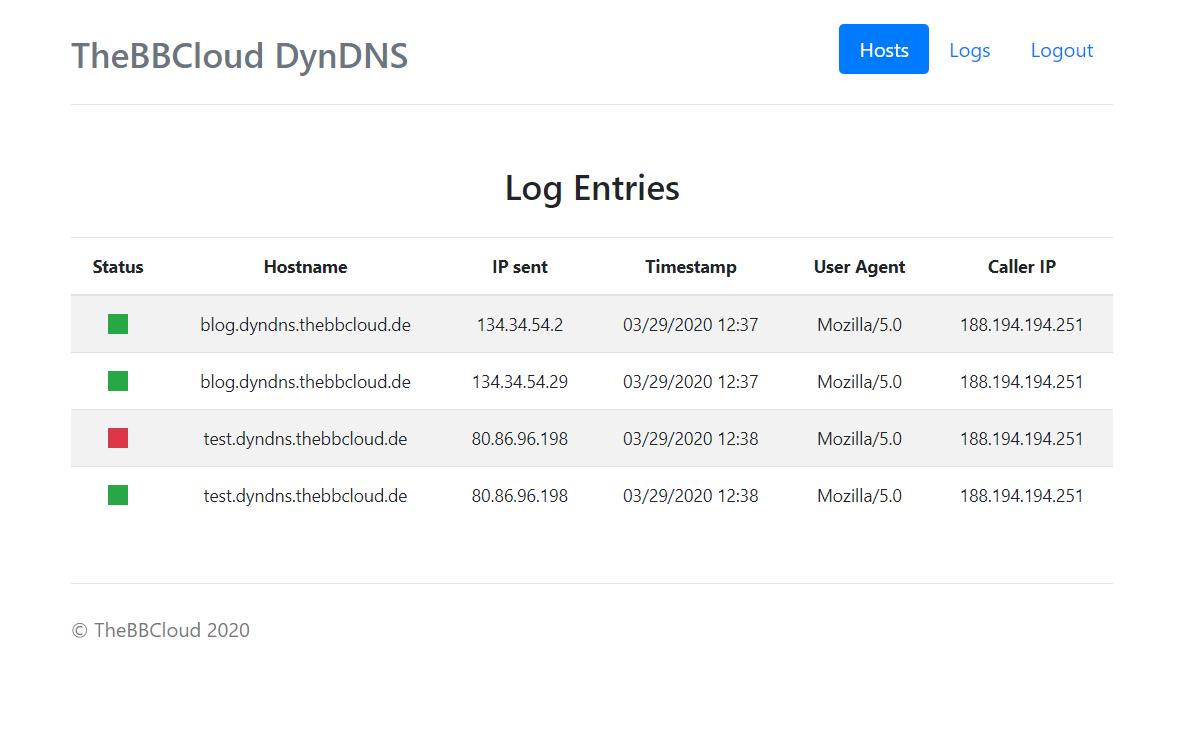 +
+ +
+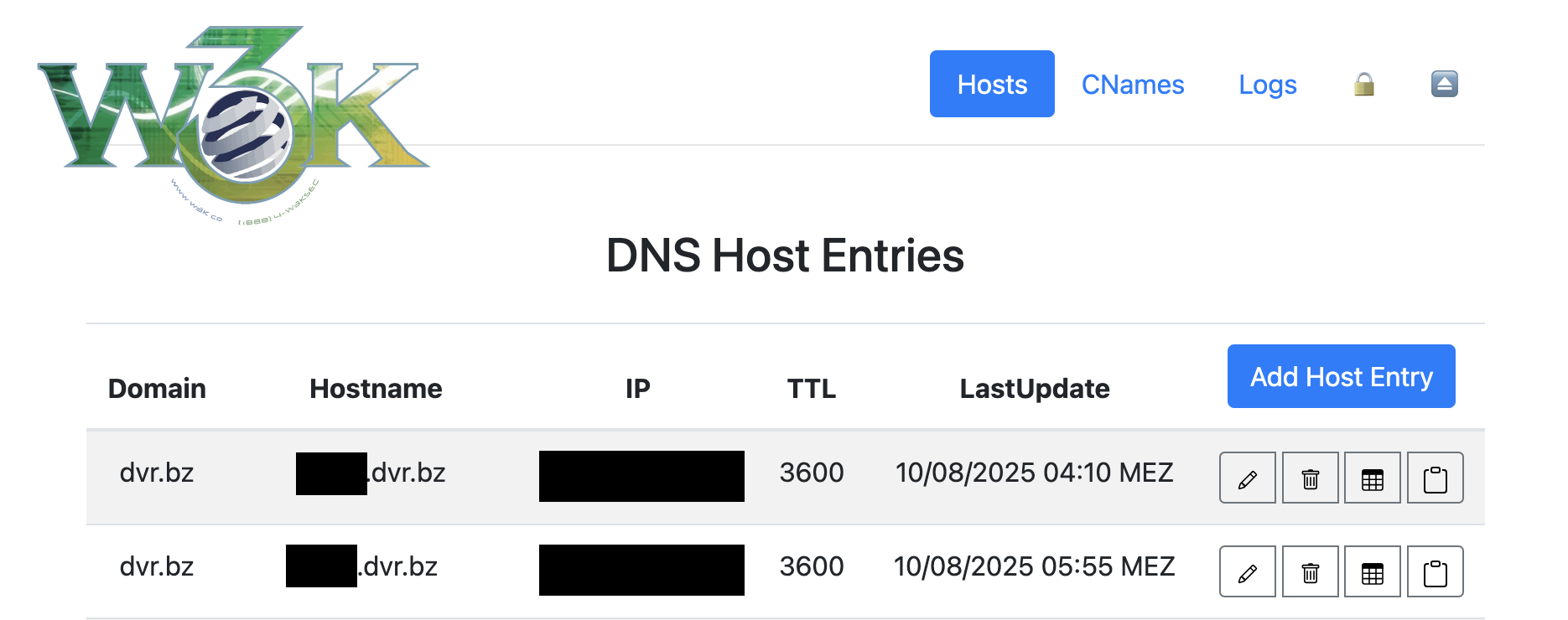 +
+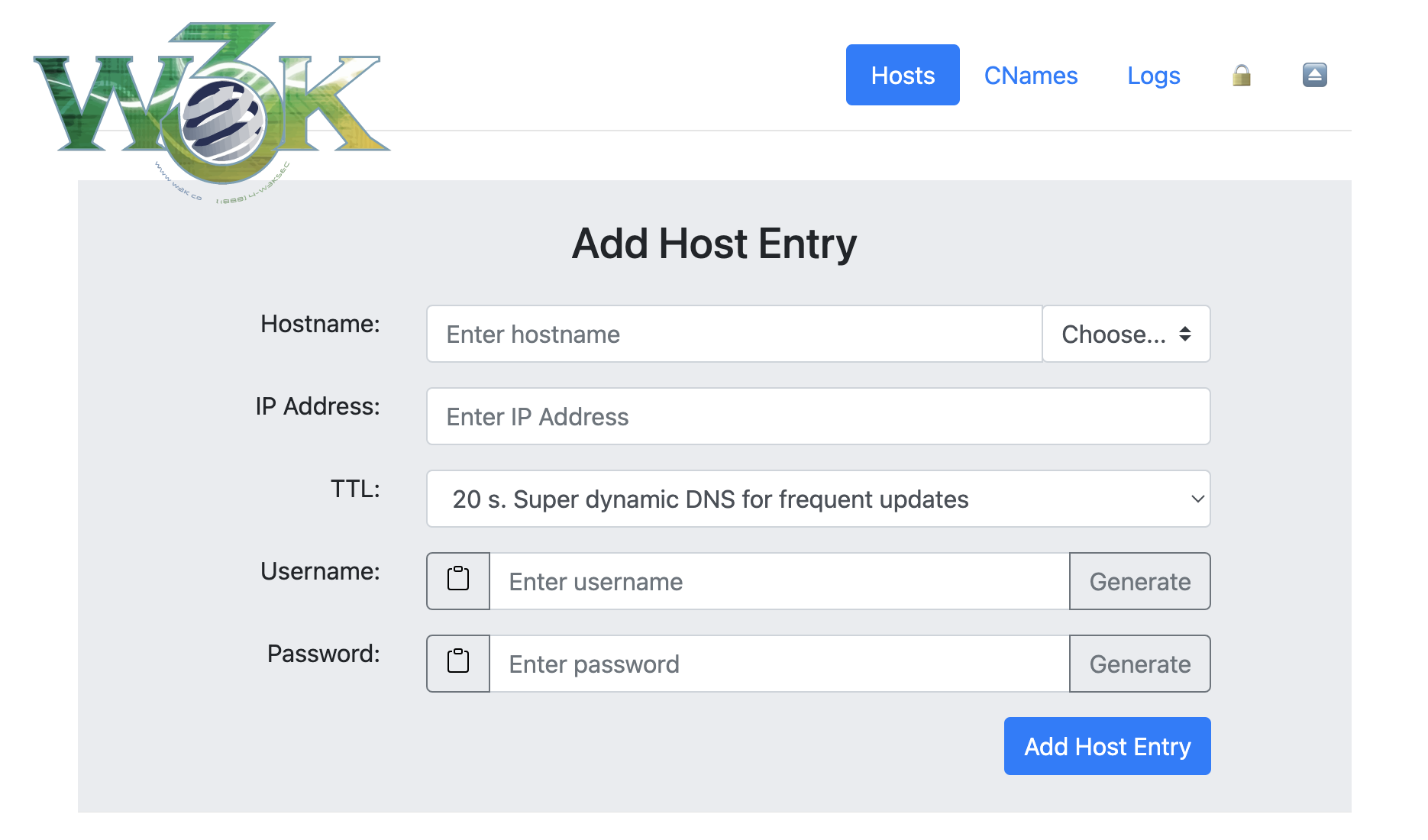 +
+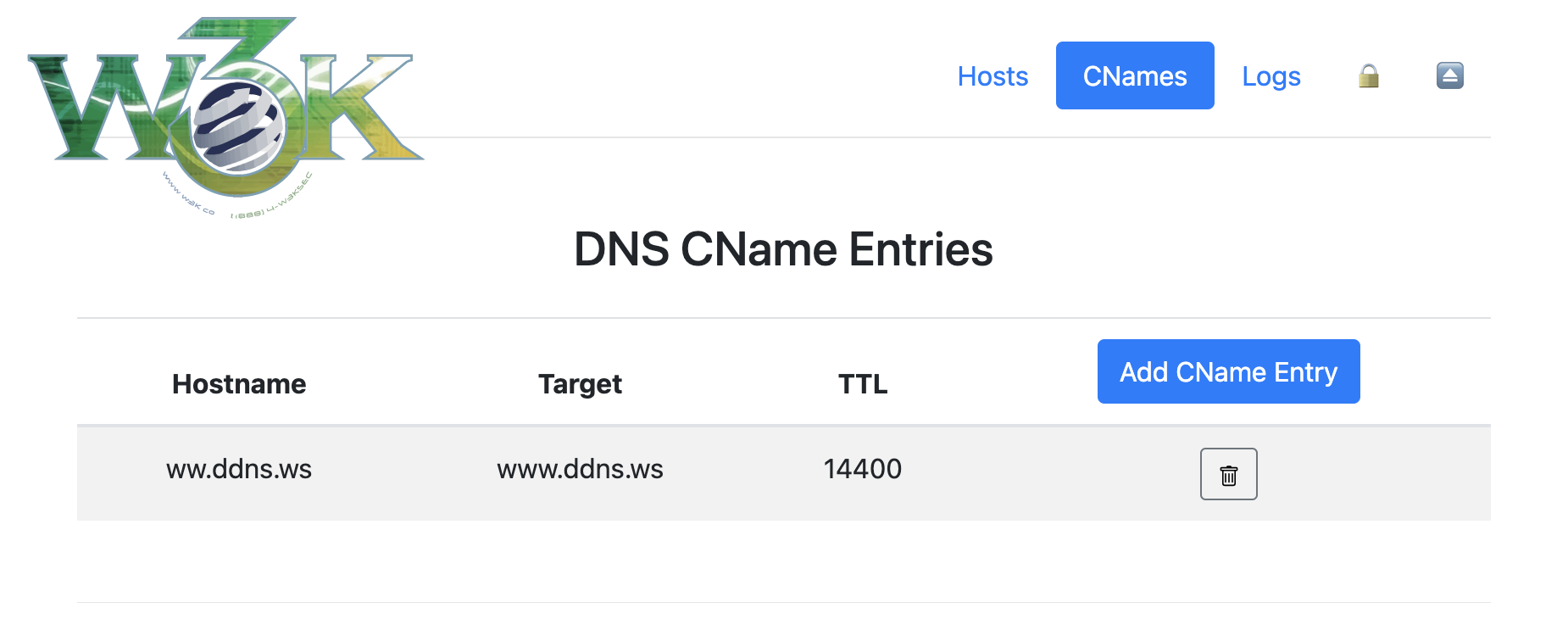 +
+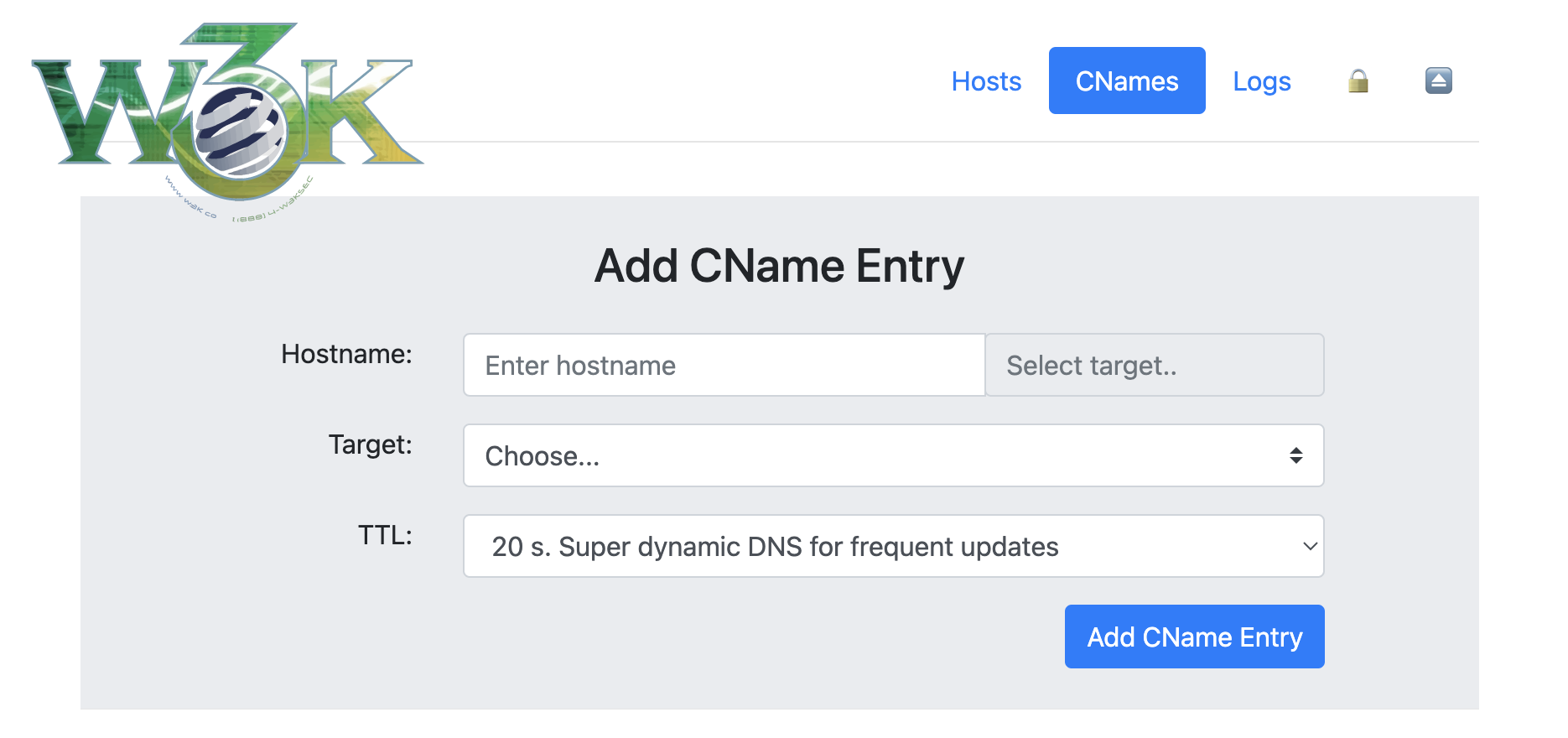 +
+ +
+ +
+
- -
- -
- +
+ +
+ +
+ +
+ +
+ +
+ +
+ +
+
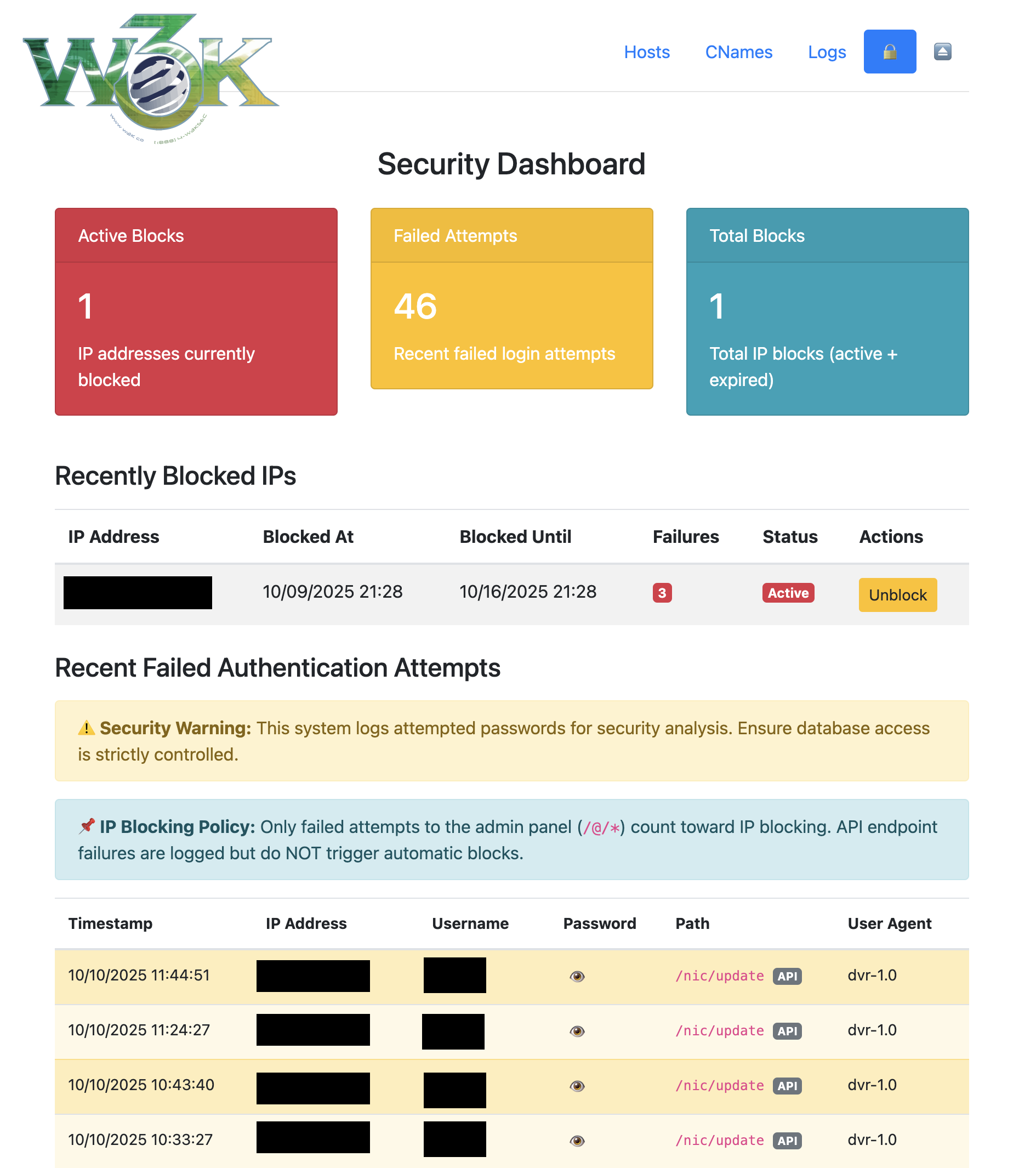
| IP Address | +Blocked At | +Blocked Until | +Last Attempt | +Failure Count | +Reason | +Status | +Actions | +
|---|---|---|---|---|---|---|---|
{{.IPAddress}} |
+ {{.BlockedAt.Format "01/02/2006 15:04"}} | +{{if .IsPermanent}} + Permanent + {{else}} + {{.BlockedUntil.Format "01/02/2006 15:04"}} + {{end}} | +{{.LastAttemptAt.Format "01/02/2006 15:04"}} | +{{.FailureCount}} | +{{.Reason}} | ++ {{if .IsBlocked}} + Active + {{else}} + Expired + {{end}} + | ++ {{if .IsBlocked}} + + {{else}} + N/A + {{end}} + | +
There are currently no blocked IP addresses. Your site security is doing great!
+/@/*) count toward IP blocking.
+ API endpoint failures (like /nic/update) are logged but do NOT trigger automatic IP blocks.
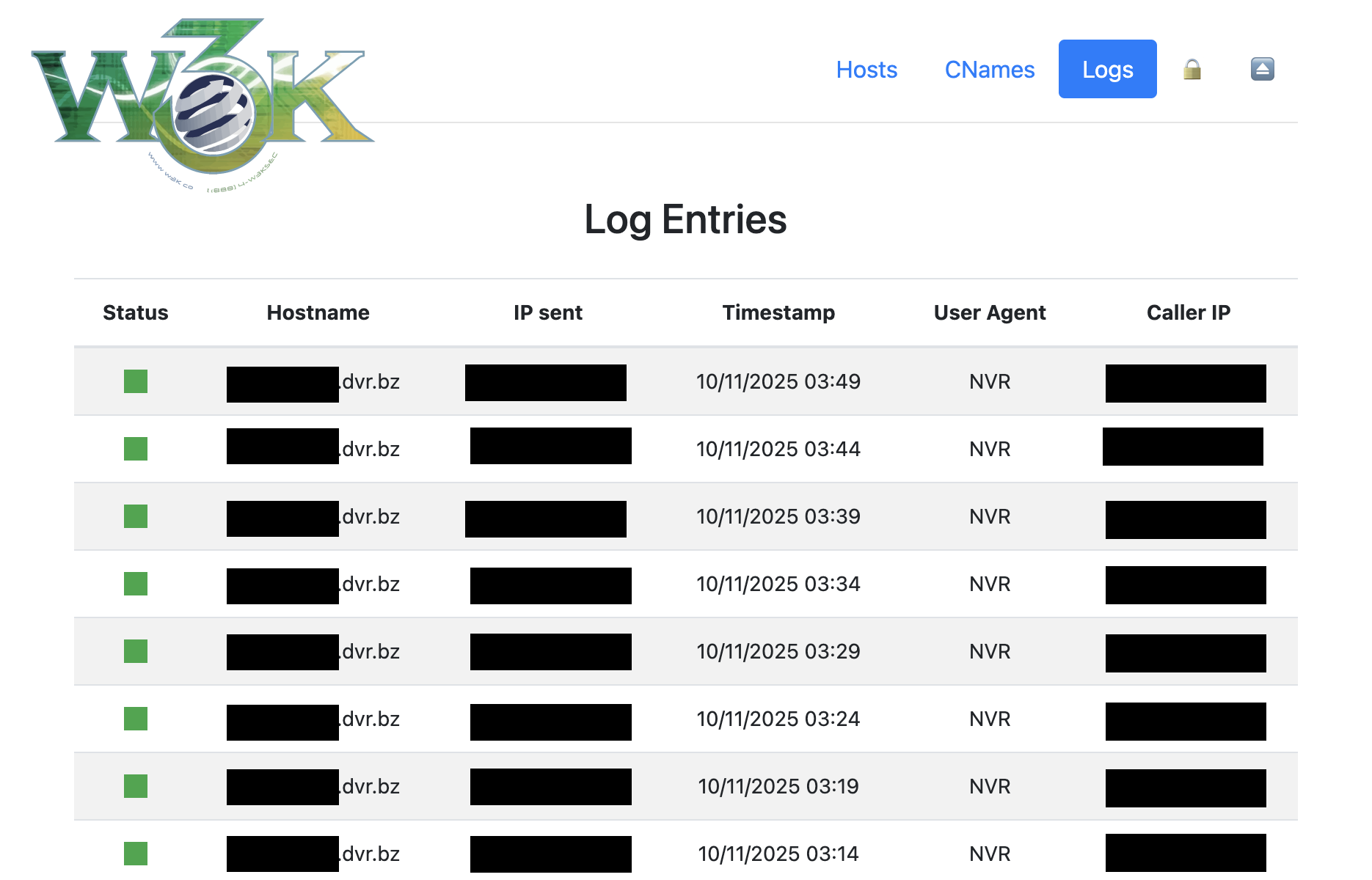
+ | Timestamp | +IP Address | +Username | +Password Attempted | +Path | +User Agent | +
|---|---|---|---|---|---|
| {{$auth.Timestamp.Format "01/02/2006 15:04:05"}} | +{{$auth.IPAddress}} |
+ {{if $auth.Username}}{{$auth.Username}}{{else}}no credentials{{end}} | +
+ {{if $auth.Password}}
+
+
+
+ {{else}}
+ no password
+ {{end}}
+
+
+ {{$auth.Password}}
+ |
+
+ {{$auth.Path}}
+ {{if hasPrefix $auth.Path "/@/"}}
+ Admin
+ {{else}}
+ API
+ {{end}}
+ |
+
+ {{if $auth.UserAgent}}
+ {{$ua := $auth.UserAgent}}
+ {{if gt (len $ua) 10}}
+
+
+
+ {{else}}
+ {{$ua}}
+ {{end}}
+ {{else}}
+ none
+ {{end}}
+
+ {{$ua}}
+
+ |
+
There are no recorded failed authentication attempts. Excellent!
+