Developing and deploying AI-powered systems and applications is a complex business, especially in our extended remote reality.
Developing and deploying AI-powered systems and applications is a complex business, especially in our extended remote reality.
 In this article, we’ll walk through SharePass’s patent-pending security funnel, providing a step-by-step guide to building out your security pipeline.
In this article, we’ll walk through SharePass’s patent-pending security funnel, providing a step-by-step guide to building out your security pipeline.
 Software Development Life Cycle is a framework that describes the software life cycle. Its purpose is to help build quality development processes.
Software Development Life Cycle is a framework that describes the software life cycle. Its purpose is to help build quality development processes.
 The rise in cybercrime and the sophistication of attacks has made security a crucial part of the development process and not just an afterthought.
The rise in cybercrime and the sophistication of attacks has made security a crucial part of the development process and not just an afterthought.
 In this article, we'll look at what are the security hazards in serverless and what factors will drive its development in the following years.
In this article, we'll look at what are the security hazards in serverless and what factors will drive its development in the following years.
 Application Security Posture Management (ASPM) is a holistic approach to managing the security posture of applications throughout their lifecycle.
Application Security Posture Management (ASPM) is a holistic approach to managing the security posture of applications throughout their lifecycle.
 Tools & Skills
Tools & Skills
 There's one area that some developers fall short on—security. The most widespread security vulnerability is leaving secrets in code.
There's one area that some developers fall short on—security. The most widespread security vulnerability is leaving secrets in code.
 Enterprises see open source as important, but they also find security to be a main barrier for adopting open source dependencies. Vulnerable software is by definition not secure, but that does not mean we judge security by the number of vulnerabilities. We highlight this by looking at two commonly used libraries, OpenSSL and GStreamer.
Enterprises see open source as important, but they also find security to be a main barrier for adopting open source dependencies. Vulnerable software is by definition not secure, but that does not mean we judge security by the number of vulnerabilities. We highlight this by looking at two commonly used libraries, OpenSSL and GStreamer.
 7 Strategies and associated tools for your container security workflows.
7 Strategies and associated tools for your container security workflows.
 When developers refer to secret sprawl they are typically referring to the unwanted distribution of secrets across multiple platforms, services and machines.
When developers refer to secret sprawl they are typically referring to the unwanted distribution of secrets across multiple platforms, services and machines.
 In this two-part series, we’re bringing you secure coding best practices and practical tips that you can lean on when integrating security into development
In this two-part series, we’re bringing you secure coding best practices and practical tips that you can lean on when integrating security into development
 What are the new up-and-coming trends for DevOps? We count to 5 and give you what is on the horizon for 2023.
What are the new up-and-coming trends for DevOps? We count to 5 and give you what is on the horizon for 2023.
 “Hey, can you meet with our SOC 2 auditors’ for a couple of hours next week to talk about our SDLC process?” Oh no! This question continually causes heartburn and eventual headachesfor software engineers. Spending multiple hours in a conference room explaining to auditors how your team deploys changes, what a pull request is and explaining how infrastructure as code works is not how engineers would describe a productive afternoon.
“Hey, can you meet with our SOC 2 auditors’ for a couple of hours next week to talk about our SDLC process?” Oh no! This question continually causes heartburn and eventual headachesfor software engineers. Spending multiple hours in a conference room explaining to auditors how your team deploys changes, what a pull request is and explaining how infrastructure as code works is not how engineers would describe a productive afternoon.
 As continuous software deployments grow and become the accepted standard, security measures gain even more importance. From development and all the way through to production, security requirements should be adopted by all teams in an organization.
As continuous software deployments grow and become the accepted standard, security measures gain even more importance. From development and all the way through to production, security requirements should be adopted by all teams in an organization.
 Zero Trust architecture is one method to secure your online infrastructure from unauthorized users. This guide covers the how and why of getting it to work.
Zero Trust architecture is one method to secure your online infrastructure from unauthorized users. This guide covers the how and why of getting it to work.
 The advantages of moving security into the DevOps lifecycle early are well-studied. For example, Puppet’s 2019 State of DevOps Report details numerous ways that both security and DevOps improve when security is integrated into DevOps earlier (aka: Shift Left).
The advantages of moving security into the DevOps lifecycle early are well-studied. For example, Puppet’s 2019 State of DevOps Report details numerous ways that both security and DevOps improve when security is integrated into DevOps earlier (aka: Shift Left).
 If you’re a Golang developer using Visual Studio Code, keeping at-risk Go Modules out of your apps just got easier, and for free.
If you’re a Golang developer using Visual Studio Code, keeping at-risk Go Modules out of your apps just got easier, and for free.
 Golang developers care a lot about security and as Go modules become more widely used, they need more ways to assure these publicly shared files are safe.
Golang developers care a lot about security and as Go modules become more widely used, they need more ways to assure these publicly shared files are safe.
 When an organization commits to DevSecOps, a fundamental shift takes place across teams. Security becomes everyone’s responsibility, which requires some rules.
When an organization commits to DevSecOps, a fundamental shift takes place across teams. Security becomes everyone’s responsibility, which requires some rules.
 DevSecOps is the theory of incorporating security activities within the process of DevOps.
DevSecOps is the theory of incorporating security activities within the process of DevOps.
 This article shows how to set up the Cognito UserPools JWT authentication flow and how it will integrate with an Angular Web Application.
This article shows how to set up the Cognito UserPools JWT authentication flow and how it will integrate with an Angular Web Application.
 In this post, we’ll discuss what shift left security is, what shift left security approaches there are and why, in the long run, it’s crucial to your success.
In this post, we’ll discuss what shift left security is, what shift left security approaches there are and why, in the long run, it’s crucial to your success.
 Collecting wide swaths of observability and security data is key to a high-quality digital experience. Find out what you need to know to get started.
Collecting wide swaths of observability and security data is key to a high-quality digital experience. Find out what you need to know to get started.
 We recently released the first versions of driftctl, a new open-source project for infrastructure developers, DevOps, SRE, and cloud practitioners, with the goal of helping manage all kinds of drifts.
We recently released the first versions of driftctl, a new open-source project for infrastructure developers, DevOps, SRE, and cloud practitioners, with the goal of helping manage all kinds of drifts.
 Software Engineering has Changed with CI/CD
Software Engineering has Changed with CI/CD
 Cybersecurity is a big concern for many companies. With data breaches happening more and more as attacks increase in sophistication, teams are looking at all of the options they have to prevent them.
Cybersecurity is a big concern for many companies. With data breaches happening more and more as attacks increase in sophistication, teams are looking at all of the options they have to prevent them.
 While API Architecture and API Design are different, when it comes to securing them, both need to be kept in focus.
While API Architecture and API Design are different, when it comes to securing them, both need to be kept in focus.
 Many software projects use secrets - usually, keys to external APIs or credentials to access an external resource such as a database. Your application needs these keys at runtime, so you need to be able to provide them when you deploy your application, or as a step in preparing your deployment environment.
Many software projects use secrets - usually, keys to external APIs or credentials to access an external resource such as a database. Your application needs these keys at runtime, so you need to be able to provide them when you deploy your application, or as a step in preparing your deployment environment.
 Efficiency, speed, transparency — all of this is possible with DevOps. In 2021, AI, data security, assembly lines, and more will take over as DevOps trends.
Efficiency, speed, transparency — all of this is possible with DevOps. In 2021, AI, data security, assembly lines, and more will take over as DevOps trends.
 When talking about infrastructure drift, you often get knowing glances and heated answers. Recording gaps in your infra between what you expected to be and the reality of what is, is a well known and widespread issue bothering hundreds of DevOps teams around the globe.
When talking about infrastructure drift, you often get knowing glances and heated answers. Recording gaps in your infra between what you expected to be and the reality of what is, is a well known and widespread issue bothering hundreds of DevOps teams around the globe.
 DevSecOps is a major evolution of the cybersecurity practice. Today, companies leverage several automated tools. This creates complexities in DevSecOps.
DevSecOps is a major evolution of the cybersecurity practice. Today, companies leverage several automated tools. This creates complexities in DevSecOps.
 Organization’s ability to cope with the complexity of delivering software at high velocity, with confidence and excellent quality, in a multi-speed IT landscape and hybrid environments has become a reality with the DevOps best practices like continuous integration, continuous delivery, and continuous deployment. But there have been shifting approaches that are confusing to Devops people, 'shift left' and 'shift right.' So, the question is, what exactly are we shifting here?
Organization’s ability to cope with the complexity of delivering software at high velocity, with confidence and excellent quality, in a multi-speed IT landscape and hybrid environments has become a reality with the DevOps best practices like continuous integration, continuous delivery, and continuous deployment. But there have been shifting approaches that are confusing to Devops people, 'shift left' and 'shift right.' So, the question is, what exactly are we shifting here?
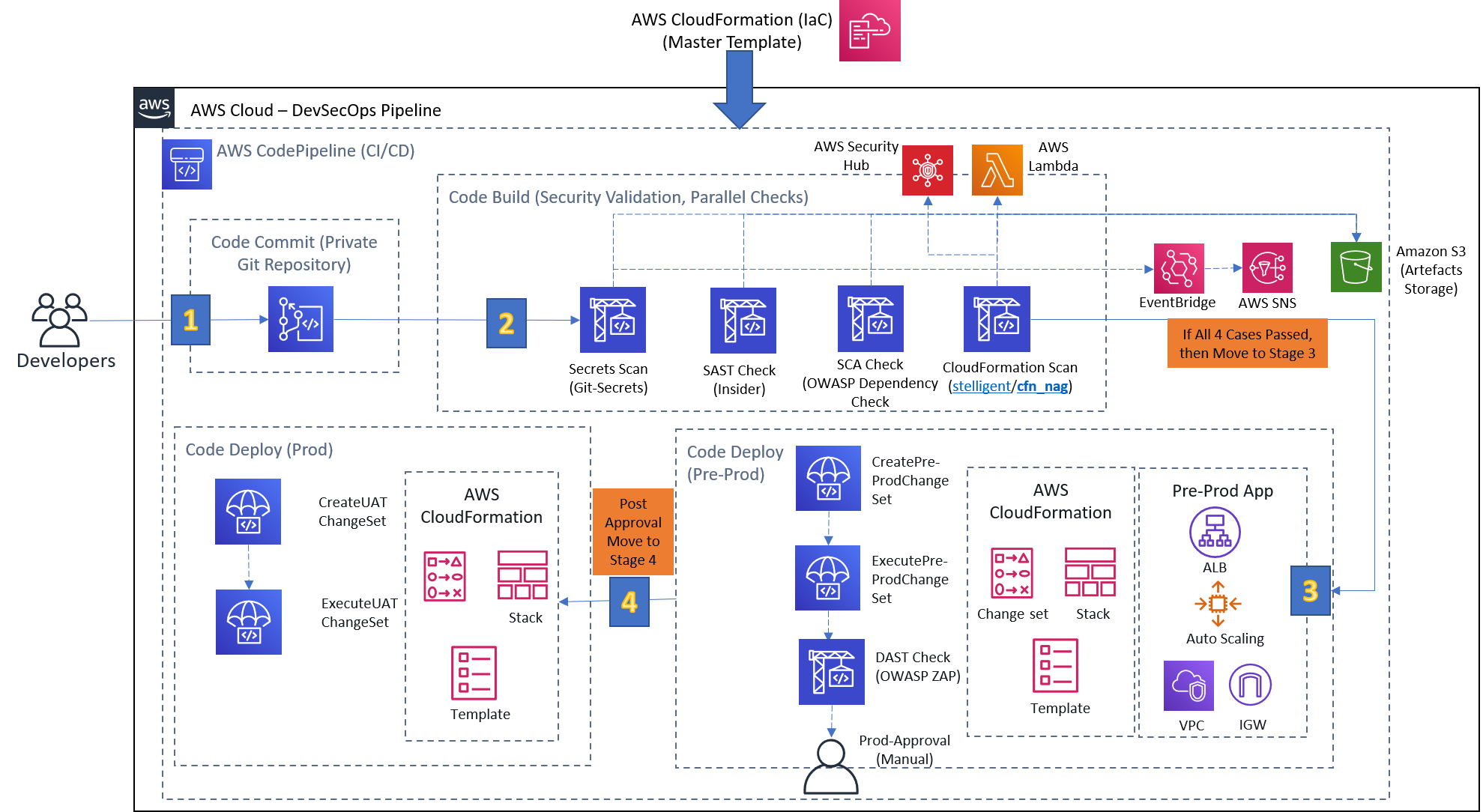
 Welcome to second part of the DevSecOps series. In the second part, we will turn ON/OFF the inbuilt led of ESP32 using AWS Device Shadow Service. Before starting, let's do a recap, in Part 1 we have connected the ESP32 MCU with AWS and able to publish Messages to IoT Core. The following series split into two parts (refer below) with very simple and clear instructions to provision a CI/CD pipeline adhering to DevSecOps principles in AWS. Everything covered from scratch you won't face any difficulty understanding. In case of any clarification, drop me a note on LinkedIn. Feel free to explore them with ease, skip to the one which is relevant to you.
Welcome to second part of the DevSecOps series. In the second part, we will turn ON/OFF the inbuilt led of ESP32 using AWS Device Shadow Service. Before starting, let's do a recap, in Part 1 we have connected the ESP32 MCU with AWS and able to publish Messages to IoT Core. The following series split into two parts (refer below) with very simple and clear instructions to provision a CI/CD pipeline adhering to DevSecOps principles in AWS. Everything covered from scratch you won't face any difficulty understanding. In case of any clarification, drop me a note on LinkedIn. Feel free to explore them with ease, skip to the one which is relevant to you.
 Vilicus is an open-source tool that orchestrates security scans of container images(Docker/OCI) and centralizes all results into a database for further analysis
Vilicus is an open-source tool that orchestrates security scans of container images(Docker/OCI) and centralizes all results into a database for further analysis
 In this series, I will describe what DevSecOps is, how we can implement it in AWS and how to can increase security in our operations.
In this series, I will describe what DevSecOps is, how we can implement it in AWS and how to can increase security in our operations.
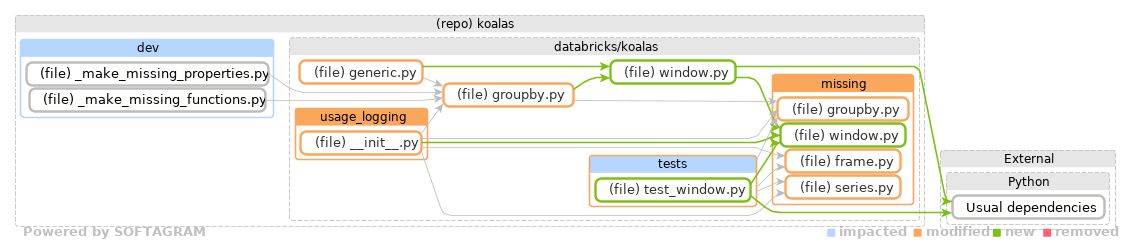
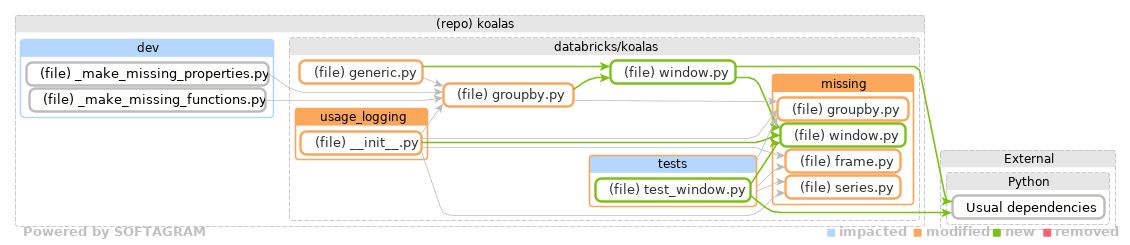 The story of Softagram is a long one and has many twists. Everything started in a small company long time ago, from the area of static analysis tools development. After many phases, Softagram is focusing on helping developers to get visual feedback on the code change: how is the software design evolving in the pull request under review.
The story of Softagram is a long one and has many twists. Everything started in a small company long time ago, from the area of static analysis tools development. After many phases, Softagram is focusing on helping developers to get visual feedback on the code change: how is the software design evolving in the pull request under review.
 In this second part of our series, we explain five additional tips to help you code more securely, from leveraging existing frameworks to protecting data.
In this second part of our series, we explain five additional tips to help you code more securely, from leveraging existing frameworks to protecting data.
 A lot of people have this mistaken notion that unikernels have this 'unhackable' characteristic about them. This is untrue. They absolutely are hackable depending on what is deployed and how they are configured.
A lot of people have this mistaken notion that unikernels have this 'unhackable' characteristic about them. This is untrue. They absolutely are hackable depending on what is deployed and how they are configured.
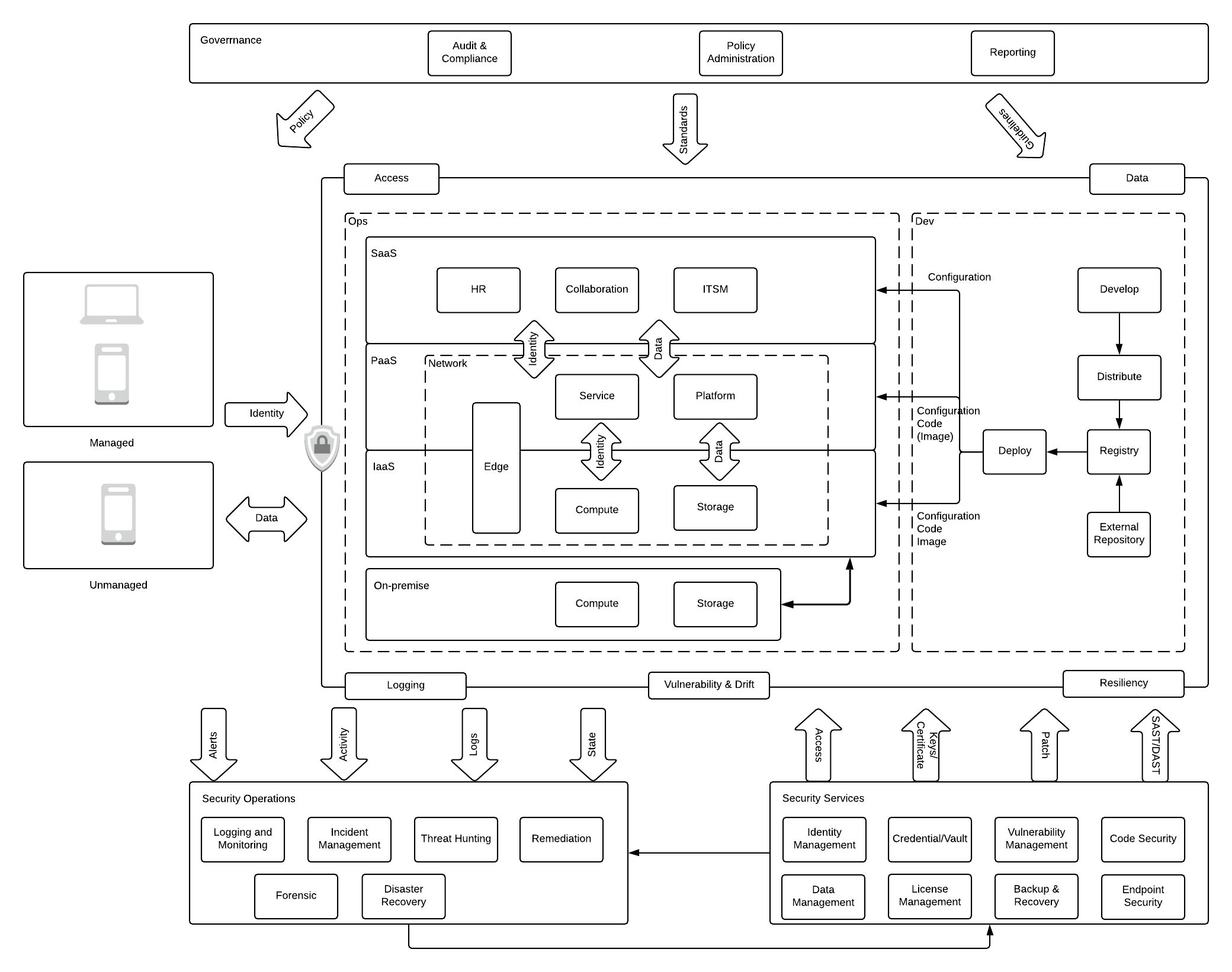 This article focuses on DevSecOps and explores how to secure applications during DevOps and the security of the platform itself.
This article focuses on DevSecOps and explores how to secure applications during DevOps and the security of the platform itself.
 What are ENV files and why as an industry should we move away from them?Three months ago we stopped using ENV files.
What are ENV files and why as an industry should we move away from them?Three months ago we stopped using ENV files.
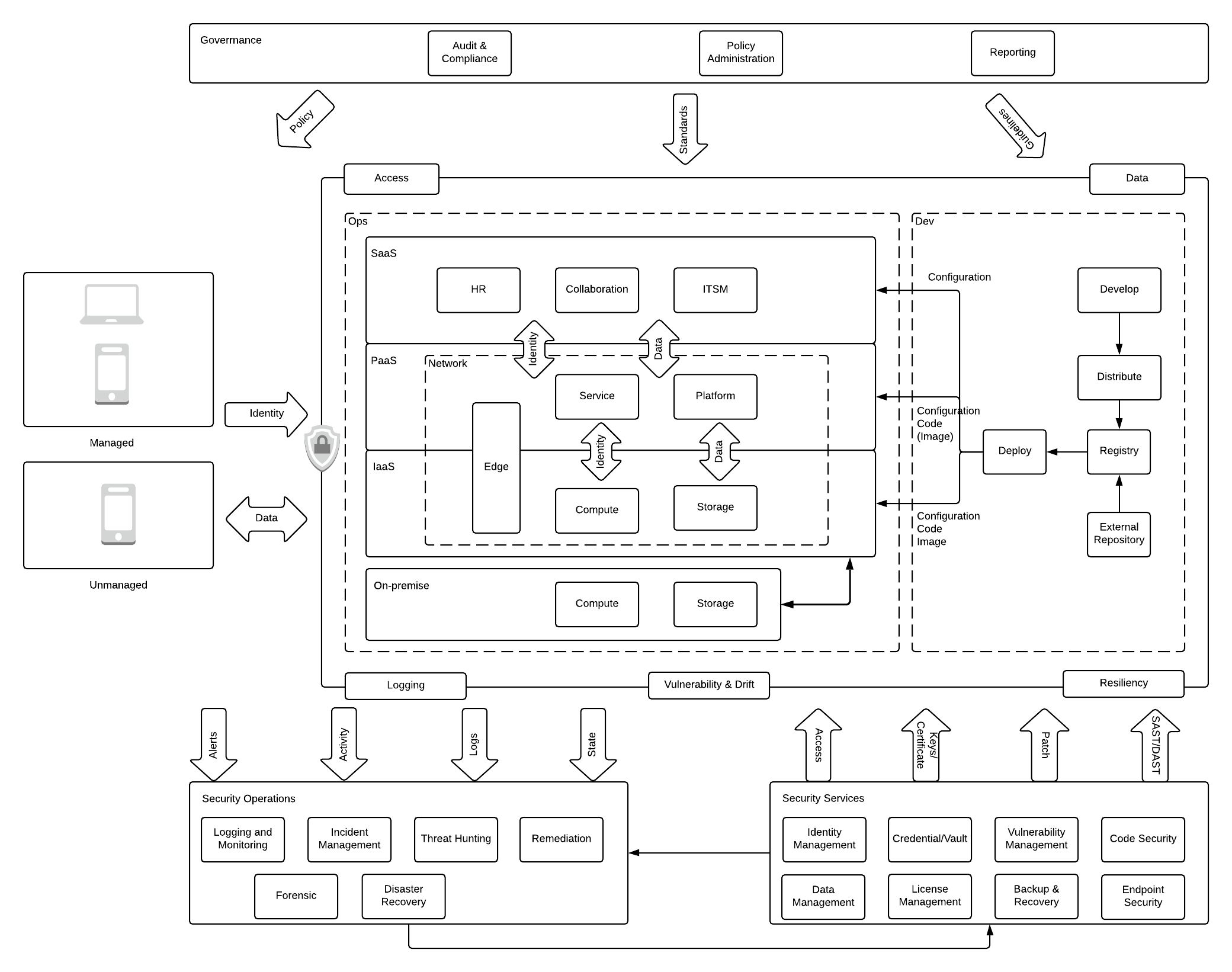
 Here, we talk about the various components within a Kubernetes architecture. Read further to know more!
Here, we talk about the various components within a Kubernetes architecture. Read further to know more!
 With the fast growth of the usage of open source in all industries, the need to track its components becomes dire as ever. Software Composition Analysis (SCA) is an open source component management solution for providing and automating visibility into the open source in your software.
With the fast growth of the usage of open source in all industries, the need to track its components becomes dire as ever. Software Composition Analysis (SCA) is an open source component management solution for providing and automating visibility into the open source in your software.
 Digital transformations is a top-of-mind task on every company's agenda. Recent data from Tech Pro Research survey proves it: last year 70% of organizations either pursued a digital transformation strategy or are
crafting one.
Digital transformations is a top-of-mind task on every company's agenda. Recent data from Tech Pro Research survey proves it: last year 70% of organizations either pursued a digital transformation strategy or are
crafting one.
 An Overview of DevSecOps and How to Automate It
An Overview of DevSecOps and How to Automate It
 The talks emerging around DevSecOps and SecDevOps, define and differentiate the other. While the overall goal may be the same, they are different in practice.
The talks emerging around DevSecOps and SecDevOps, define and differentiate the other. While the overall goal may be the same, they are different in practice.
 Urban myths about secure coding are easy to manage when you have the right tools in place and best practices to follow as guidelines.
Urban myths about secure coding are easy to manage when you have the right tools in place and best practices to follow as guidelines.
 What happens after you accidentally leak secrets to a public code repository.
What happens after you accidentally leak secrets to a public code repository.
 Software and systems are the backbone of most organizations. When an application fails or a system is breached, it can lead to dire loss and harm.
Software and systems are the backbone of most organizations. When an application fails or a system is breached, it can lead to dire loss and harm.
 The costs of security events are often far-reaching. Shifting security left to using policy as code can help to ensure security.
The costs of security events are often far-reaching. Shifting security left to using policy as code can help to ensure security.
 Enterprise networks and data security risks have never been this monumental as they are in today’s day and age. Nonetheless, traditional approaches, including those used by operators of public clouds, are essentially more or less the same.
Enterprise networks and data security risks have never been this monumental as they are in today’s day and age. Nonetheless, traditional approaches, including those used by operators of public clouds, are essentially more or less the same.
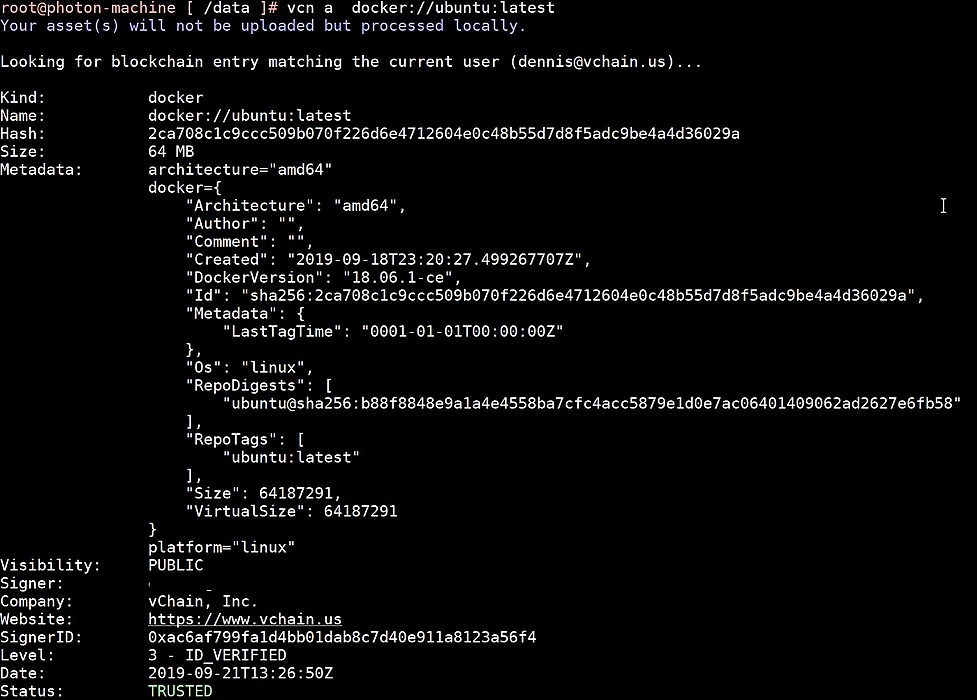 I still remember February 2018 very well. Many people were in a really bad mood when it came to Blockchain or Distributed Ledger Technology (DLT), mainly because the price of most cryptocurrencies made a nose dive and the Disillusionment started.
I still remember February 2018 very well. Many people were in a really bad mood when it came to Blockchain or Distributed Ledger Technology (DLT), mainly because the price of most cryptocurrencies made a nose dive and the Disillusionment started.
 DevSecOps is gaining popularity rapidly because it’s the only well-defined methodology to integrate the entire application development process while addressing security as well.
DevSecOps is gaining popularity rapidly because it’s the only well-defined methodology to integrate the entire application development process while addressing security as well.
 The article covers eight technologies that are worth to invest in 2023.
The article covers eight technologies that are worth to invest in 2023.
 Malware attacks in open source ecosystems have exponentially increased in the last 2 years. How do we build cybersecurity that scales to meet this challenge?
Malware attacks in open source ecosystems have exponentially increased in the last 2 years. How do we build cybersecurity that scales to meet this challenge?
 Security is of paramount importance to every DevOps team today. You can deliver excellent applications in lesser time due to agile development methodologies like DevOps and CI/CD pipelines. However, if your application is not extremely secure, there’s an imminent threat of attacks. Today, hackers are more proficient than ever, which means your applications need a security strategy that makes them impenetrable and keeps you one step ahead of hackers.
Security is of paramount importance to every DevOps team today. You can deliver excellent applications in lesser time due to agile development methodologies like DevOps and CI/CD pipelines. However, if your application is not extremely secure, there’s an imminent threat of attacks. Today, hackers are more proficient than ever, which means your applications need a security strategy that makes them impenetrable and keeps you one step ahead of hackers.
 With the latest news and advancements in the cybersecurity world, we will see how these new rules impact modern cloud applications.
With the latest news and advancements in the cybersecurity world, we will see how these new rules impact modern cloud applications.
 This blog post is a written transcript of the FOSDEM Talk: “Infrastructure drifts aren’t like Pokemon, you can’t catch ’em all”, by Stephane Jourdan – CTO and founder
This blog post is a written transcript of the FOSDEM Talk: “Infrastructure drifts aren’t like Pokemon, you can’t catch ’em all”, by Stephane Jourdan – CTO and founder
 Threat modeling is typically conducted from the design phase and onward in the development process.
Threat modeling is typically conducted from the design phase and onward in the development process.
 DevOps has transformed the way operational engineers and software developers reason. Gone are the days when a code was written, implemented, and managed by operations. The DevOps model has remodeled the system of product and application production. As a result, faster results have become the pinnacle of delivering at the speed which the market demands.
DevOps has transformed the way operational engineers and software developers reason. Gone are the days when a code was written, implemented, and managed by operations. The DevOps model has remodeled the system of product and application production. As a result, faster results have become the pinnacle of delivering at the speed which the market demands.
 With an emerging pattern of organizations embracing the DevOps framework, adopting Microservice Architecture is steadily gaining the respect it deserves.
With an emerging pattern of organizations embracing the DevOps framework, adopting Microservice Architecture is steadily gaining the respect it deserves.
 Every company claims to have a cloud/hybrid DevOps platform that enables and powers developers working remotely. Time to make order of the chaos.*
Every company claims to have a cloud/hybrid DevOps platform that enables and powers developers working remotely. Time to make order of the chaos.*
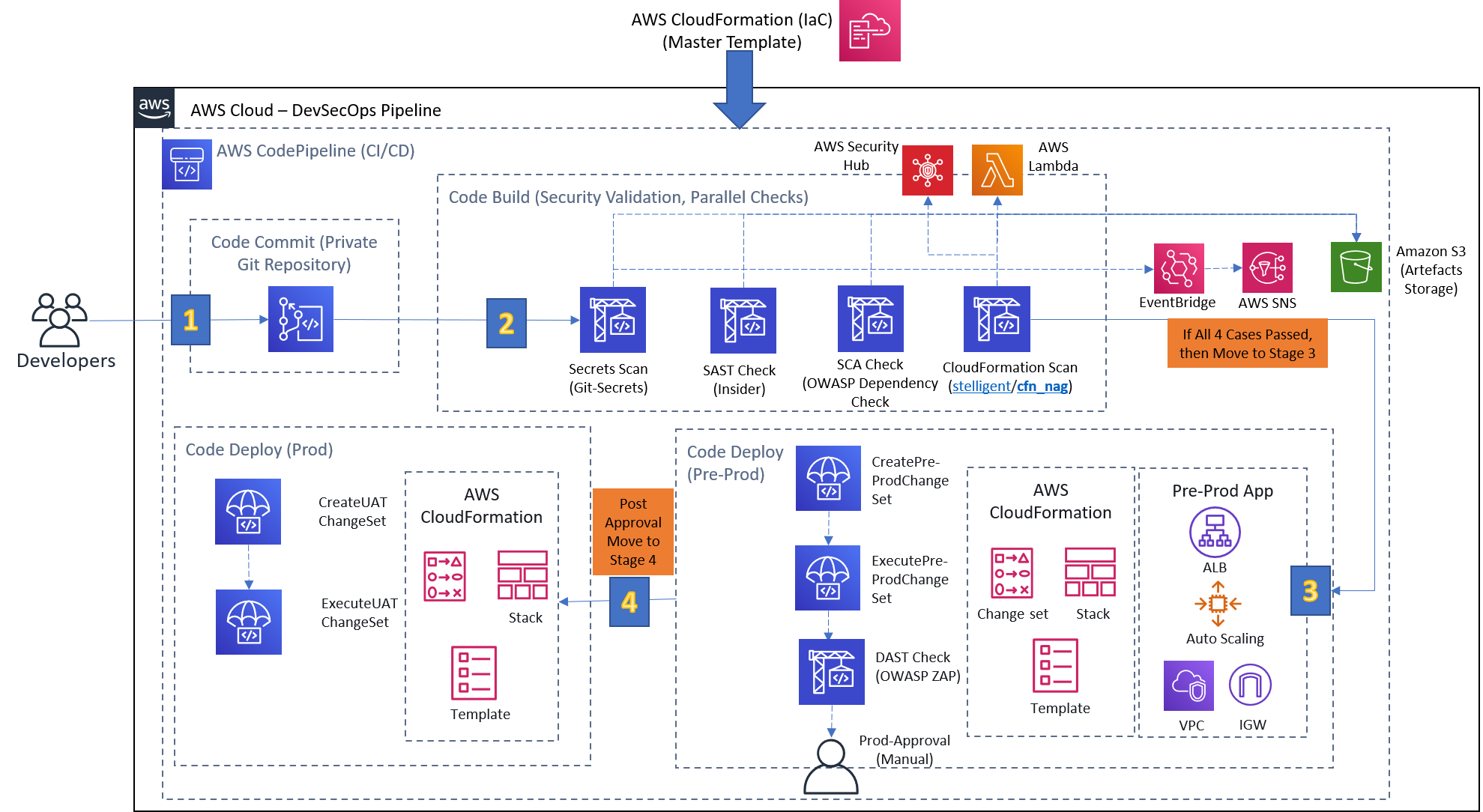 DevSecOps is the new buzz and definitely a potential candidate to scare people in the ever-changing software industry. When I heard the term for the first time, my inner voice said it out loud, "When just this Happened, and why SEC is sandwich between them ?". Later on, to look cool, I started adding DevSecOps on my profile, but the dire consequence was a complete disappointment. DevSecOps isn't just restricted to understand security by heart & fit it with DevOps. A good analogy would be not to imagine your ex with someone, especially with your girlfriend/wife. It is all about "Shift left on Security" i.e. to introduce security as early as possible in the SDLC. Though I am not going to bore you with the definitions and concepts as I am a practical person. Thus, my objective here is to demonstrate how DevSecOps works in reality. The following series split into two parts (refer below) with very simple and clear instructions to provision a CI/CD pipeline adhering to DevSecOps principles in AWS. Everything covered from scratch you won't face any difficulty understanding. In case of any clarification, drop me a note on LinkedIn. Feel free to explore them with ease, skip to the one which is relevant to you.
DevSecOps is the new buzz and definitely a potential candidate to scare people in the ever-changing software industry. When I heard the term for the first time, my inner voice said it out loud, "When just this Happened, and why SEC is sandwich between them ?". Later on, to look cool, I started adding DevSecOps on my profile, but the dire consequence was a complete disappointment. DevSecOps isn't just restricted to understand security by heart & fit it with DevOps. A good analogy would be not to imagine your ex with someone, especially with your girlfriend/wife. It is all about "Shift left on Security" i.e. to introduce security as early as possible in the SDLC. Though I am not going to bore you with the definitions and concepts as I am a practical person. Thus, my objective here is to demonstrate how DevSecOps works in reality. The following series split into two parts (refer below) with very simple and clear instructions to provision a CI/CD pipeline adhering to DevSecOps principles in AWS. Everything covered from scratch you won't face any difficulty understanding. In case of any clarification, drop me a note on LinkedIn. Feel free to explore them with ease, skip to the one which is relevant to you.