-
Notifications
You must be signed in to change notification settings - Fork 10
Home
- Overview
- The Contracts
- The Counterfactual Nature
- Meta Channels
- Design Paradigms
- Privacy Techniques
- High Speed Rails
State Channels allow the same security, privacy, trustless services as the Ethereum blockchain except with considerably less transaction fees (no transaction fees if parties are behaving honestly).
Figure 1: Playing Tic Tac Toe on State Channels
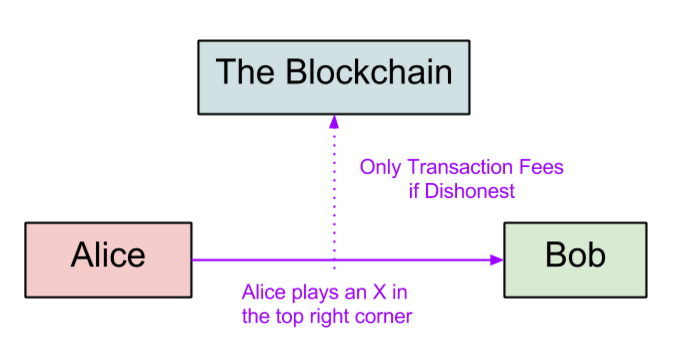
A simple example of the use of State Channels can be conceived if two parties, Alice and Bob decide to play a game of Tic Tac Toe together for money. Alice and Bob would open up a state channel with each other by writing up a smart contract and lock up their bets using this smart contract, as illustrated in Figure 1. Then, instead of telling the blockchain each and every one of their tic tac toe moves, they simply sign transactions between them with their corresponding moves. The key part is that the transactions are never published to the blockchain if both parties behave honestly, saving the network from doing extraneous calculations. If however, one party behaves dishonestly by going offline and is thus not able to sign any transactions, the other party can publish the latest transaction that was signed by both parties and the blockchain will fairly decide where the initial bets go. This system very much resembles the legal system where two parties will go to court and pay the legal fees to get an official ruling by a judge if and only if there is a disagreement between them. The difference between the adjudication process in state channels and the legal system is that adjudication processes have deterministic outcomes while legal systems are vulnerable to human subjectivity
As the Ethereum network expands, an array of problems begin to arrise ranging from an increase of block collisions to the danger of very few individuals possessing the ability to run full nodes leading to centralization, the opposite of what blockchain technology aims to accomplish. State Channels offer a simple solution to this problem since they are able to operate with minimal on chain transactions while taking a majority of would be on chain transactions off chain. In addition, transactions within channels could be processed much faster than the average time it takes to mine a block and fees would be almost negligent.
The Unanimous Consent Contract allows the consenters of the State Channel to do anything they would like with the channel if and only if all consenters have given their consent. This contract allows for consenters to give their consent for a certain course of action however this consent cannot be retracted. Furthermore, once a motion has reached unanimous consent, it will only be executed if it has not been executed before to prevent replay attacks. If the consenters wish to perform the same action again, the motion must once again receive consent from all consenters.
A potential problem with State Channels is its handling of information withholding attacks. The blockchain has no way of knowing whether the last state that it received is indeed the last state that was signed. The Adjudicator contract makes information withholding attacks more difficult by enforcing a timeout between when it asks for information and when it receives the information. This way if Alice is maliciously withholding the latest state from the blockchain, Bob has enough time to send in a more recent state. Once the timeout has expired, the latest state sent is assumed to be the final state. It is possible to avoid waiting for the timeout expire if all consenters send in a state with a nonce equaling the maximum value for an unsigned integer to indicate the finality of the state.
The Lock Adjudicator contract is a special type of Adjudicator that uses the Bulletin Board contract in order to determine which sub Adjudicator to use. The Lock Adjudicator allows for the State Channel to simultaneously be used for different purposes. For example, Alice and Bob could have a payment channel open while they play tic tac toe with each other while they play mahjong with Carol and Dave.
The Bulletin Board holds a counterfactual registry of the sub Adjudicators so that the Lock Adjudicator can counterfactually closeout a sub Adjudicator.
The Rules contract is called by the Adjudicator contract if someone has violated the terms and conditions of the state channel. Rules will check that someone was against the terms and conditions set in motion and will return its ruling to its corresponding Adjudicator.
The Lock Rules contract is a special type of Rules that is connected to the Lock Adjudicator.
Interested Bystanders could potentially be controlled by a contract. The Interested Bystanders would be able to consent or sign transactions on behalf of a consenter if the consenter has disconnected. It is important to make sure that the Interested Bystanders do not call the blockchain unnecessarily and that they cannot consent instead of a consenter who is available.
State Channels depend on an invisible trusted party to make sure that the participants of the channel are behaving honestly and fairly. This means that the blockchain--a trusted party due to its transparency and deterministic behaviour--will only be called if there is a need for it to sort out a disagreement between channel participants. As a result, the Adjudicator, Rules, Lock Adjudicator, and Lock Rules contract do not need to be instantiated, simply the threat of their instantiation is enough to keep participants honest.
To be written
To be written
Meta Channels allow for two parties to have a State Channel without opening a State Channel if they pass messages through some intermediary hub.
Figure 2: Meta Channels

A simple example is the case where A wants to pay B $X via State Channels without explicitly opening up a State Channel with B as seen in Figure 2. Since A and C have a State Channel and B and C have a State Channel, A and B can use C as an intermediary to get their payment done. A gives B a password and tells C that if C can get the password from B and then give it to A, A will give C $X plus some service fees. C then tells B that C will give B $X if B will give C the password that A was looking for. Now B gives C the password and receives $X. Then C gives A the password and receives $X plus service fees which ultimately results in A paying B $X.
To be written
To be written
To be written
To be written
To be written
To be written