-
Notifications
You must be signed in to change notification settings - Fork 129
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
[feature] workflow for publishing source code archives as release assets #2951
Comments
|
Hi, thanks for the issue. You can achieve this today using the generator https://github.com/slsa-framework/slsa-github-generator/blob/main/internal/builders/generic/README.md and setting the |
|
I'm confident that it would, but the idea here is to spare every project the |
|
I understand the |
|
Just to be clear, the idea is not to generate the source code archives manually. (GitHub already does that automatically.) The reason to do the |
|
ah, I missed this. Thank you. I'm not super familiar how |
|
As linked above, https://blog.bazel.build/2023/02/15/github-archive-checksum.html describes the situation quite well, I think, with the screenshot illustrating the difference between I should just clarify that the filenames in the
Likewise, |
|
Maybe this could be an option on the generic generator? I'm not sure we need a totally separate workflow. WDYT? |
|
I had "do one thing and do it well" in mind, I think, when I suggested another workflow. |
|
Yeah. I hear that. I think 95% of the code would be the same though. The only difference would be that we could omit |
|
Fair enough. :) |
|
In light of CVE-2024-3094, could this effort possibly be prioritised? ;) |
|
In case it helps, I wrote https://github.com/google/re2/blob/main/.github/workflows/release.yml earlier today. :) |
|
Hey, sorry for the late reply. Thank for putting an example together. We could support this using BYOB https://slsa.dev/blog/2023/08/bring-your-own-builder-github and https://github.com/slsa-framework/slsa-github-generator/blob/main/BYOB.md We should be able to take your example and wrap it in a BYOB fairly easily. This would let your users (and other projects' users) to use the slsa-verifier to verify, out of the box, with a common builder. The only thing we need to change is that the command Would that work? Happy to help make that happen |
|
IIUC, yes, the PW would run |
You would not need the sigstore signatures, but the SLSA builders use Sigstore too :) There are 2 (related) advantages to a common builder:
If you're OK with all that, I can ahead and turn your example into a SLSA builder |
SGTM. Thanks! :D |
|
Hey, a few months ago GitHub made (then reverted) the tarballs non-deterministic, see https://github.com/orgs/community/discussions/45830. To avoid this sort of problems in the future, the builder could create the archives itself and upload them to the release. That will also let us support other types or archive (if we need to) in the future. Wdut of this approach? |
|
Downloading the source code archives and uploading them as release assets is sufficient, AFAIK, because that's what confers stability. I reckon that creating them (i.e. explicitly) wouldn't add value... but would add complexity. If somebody downloads a slightly different one later because they clicked or pasted the wrong link, I don't think it actually matters who or what created the one at the right link. Or am I misunderstanding a risk from a trust perspective here? |
Not super complicated I think. The BYOB framework already clones the repo, so code is available. We would just need to zip / tar it which does not seem too complicated.
stability requires that archives downloaded from GitHub (with the same link) to be deterministic. The link above shows that GitHub generates archives on the fly when they are requested (to save up storage space I think). This means the signature would fail if the archive is different at download vs when it was first signed. In the link above, that had changed the compression algo so there was a mismatch between sign-time vs download-time of the archive. Lmk what you think. |
|
I think you might be confusing source code archives and release assets. The image below (taken from the Bazel blog) hopefully clarifies: Note well that downloading the source code archives and uploading them as release assets makes them stable as release assets, not as source code archives. That's why I'm arguing that, at release time, it doesn't matter whether the source code archives are deterministic. If somebody ends up using a copy of a nondeterministic file, then it really doesn't matter how the deterministic file was created, does it? |
|
My bad, I had not seen that you're re-uploading the source archives as release assets. I thought your example workflow only signed the downloaded source archives without re-uploading them. Re-creating or downloading existing source archives works. Is it fair to say that how the archive is created is an implementation detail you don't care too much about? Or you do care? I'll probably download them to simplify the first iteration, but would like to know if it makes a different for your use case, in particular security wise. |
|
To date, manual manipulation of the source code archives is the big problem. Trusting their creation to GitHub seems no more risky than trusting everything else to GitHub, honestly, so obtaining them from GitHub – as opposed to creating them explicitly – suits me just fine. |
|
Release artifacts are mutable. I think if we can guarantee the archives to be reproducible, we should try to do it. |
|
Draft PR is #3587. I think we need to tweak it to reduce permissions by using https://github.com/slsa-framework/slsa-github-generator/blob/main/.github/workflows/delegator_lowperms-generic_slsa3.yml, then we're good to go |
Is your feature request related to a problem? Please describe.
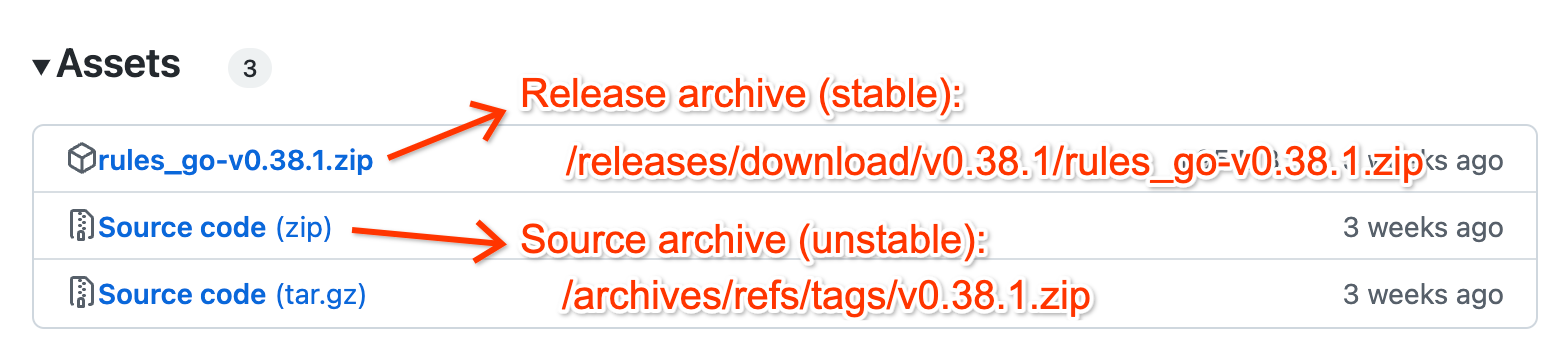
Bazel recommends publishing source code archives as release assets – and Bazel Central Registry verifies stability by checking for
…/releases/download/…in GitHub URLs. Usinggh release downloadandgh release upload, GitHub Actions can automate this trivially, but OpenSSF punishes projects whose release assets lack signature and provenance.Describe the solution you'd like
SLSA should provide a workflow for publishing source code archives as release assets with signature and provenance. Ideally, any project's
releaseworkflow could include a job specifying onlypermissionsanduseskeys and get.zip,.zip.intoto.jsonl,.tar.gzand.tar.gz.intoto.jsonlfiles attached to the release.Describe alternatives you've considered
Letting N different projects implement this themselves in approximately N different ways. ;)
Additional context
N/A
The text was updated successfully, but these errors were encountered: