From 064e77a85fe876cd935596dfe80ff6a2661eadcc Mon Sep 17 00:00:00 2001
From: Bharath Krishna <118433150+bharathk08@users.noreply.github.com>
Date: Mon, 8 Jul 2024 10:04:50 +0530
Subject: [PATCH 1/2] Added Troubleshooting doc for Salesforce (#440)
Added a new Troubleshooting doc & updated special NLPs doc for salesforce.
---
src/left-nav-title.json | 3 +-
.../docs/salesforce-testing/special-nlps.md | 36 +++++
.../salesforce-testing/most-common-issues.md | 126 ++++++++++++++++++
3 files changed, 164 insertions(+), 1 deletion(-)
create mode 100644 src/pages/docs/troubleshooting/salesforce-testing/most-common-issues.md
diff --git a/src/left-nav-title.json b/src/left-nav-title.json
index 01841ce5..286a1b2f 100644
--- a/src/left-nav-title.json
+++ b/src/left-nav-title.json
@@ -679,5 +679,6 @@
"object-learning": {"/docs/windows-automation/object-learning": "Object Learning (Using UFT One)"},
"import-tsrx-files": { "/docs/windows-automation/import-tsrx-files/": "Importing/Updating TSRx Files" },
"record-elements": {"/docs/elements/mobile-web-application/record-elements/": "Record Multiple Elements" },
- "add-test-cases-for-mobile-web-app": {"/docs/test-cases/manage/add-test-cases-for-mobile-web-app/": "Test Cases (Mobile Web App)" }
+ "add-test-cases-for-mobile-web-app": {"/docs/test-cases/manage/add-test-cases-for-mobile-web-app/": "Test Cases (Mobile Web App)" },
+ "most-common-issues": { "/docs/troubleshooting/salesforce-testing/most-common-issues/": "Most Common Issues" }
}
\ No newline at end of file
diff --git a/src/pages/docs/salesforce-testing/special-nlps.md b/src/pages/docs/salesforce-testing/special-nlps.md
index ad5d78a2..3a0ee7aa 100644
--- a/src/pages/docs/salesforce-testing/special-nlps.md
+++ b/src/pages/docs/salesforce-testing/special-nlps.md
@@ -15,6 +15,9 @@ contextual_links:
- type: link
name: "List of Special NLPs"
url: "#list-of-special-nlps"
+- type: link
+ name: "Using API NLP Test Steps"
+ url: "#using-api-nlp-test-steps"
---
---
@@ -55,4 +58,37 @@ With Testsigma's special NLPs, you can scale and enhance Salesforce Testing. The
| Edit record with **RECORD_ID** using **User Connection** in **Salesforce Object** | This NLP updates a record using RECORD\_ID for a specific Salesforce object using the update record API.
**User Inputs in NLP:**
1. RECORD_ID
2. User Connection
3. Salesforce Object |
| Delete record with **RECORD_ID** using **User Connection** in **Salesforce Object** | This NLP deletes a record using RECORD\_ID for a specific Salesforce object using the delete record API.
**User Inputs in NLP:**
1. RECORD_ID
2. User Connection
3. Salesforce Object |
+---
+
+## **Using API NLP Test Steps**
+
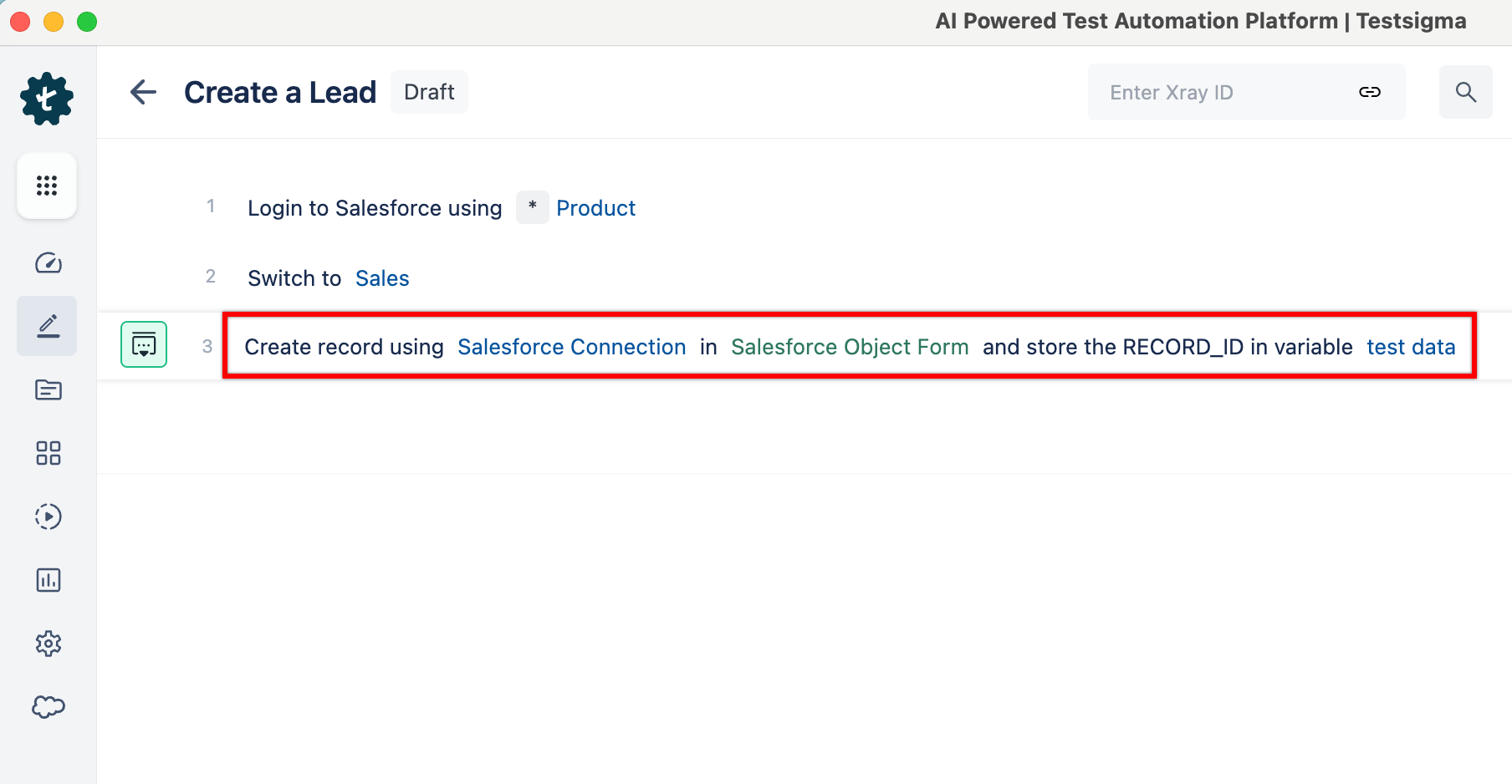
+1. Let's say you want to automate the creation of a Salesforce Lead record.
+
+ To create a lead record, navigate to the **Leads** tab, click **New**, and fill out the form with details such as the lead's name, company, contact information, and descriptions. After entering the necessary information, save the record. The lead will be available for future actions, such as follow-ups or conversion into an account, contact, or opportunity.
+
+ Guess what? With Testsigma, you can perform all these actions in a single API step using the following NLP:
+
+ 
+
+ Here’s a quick GIF demonstrating how to create a Salesforce lead record.
+
+ 
+
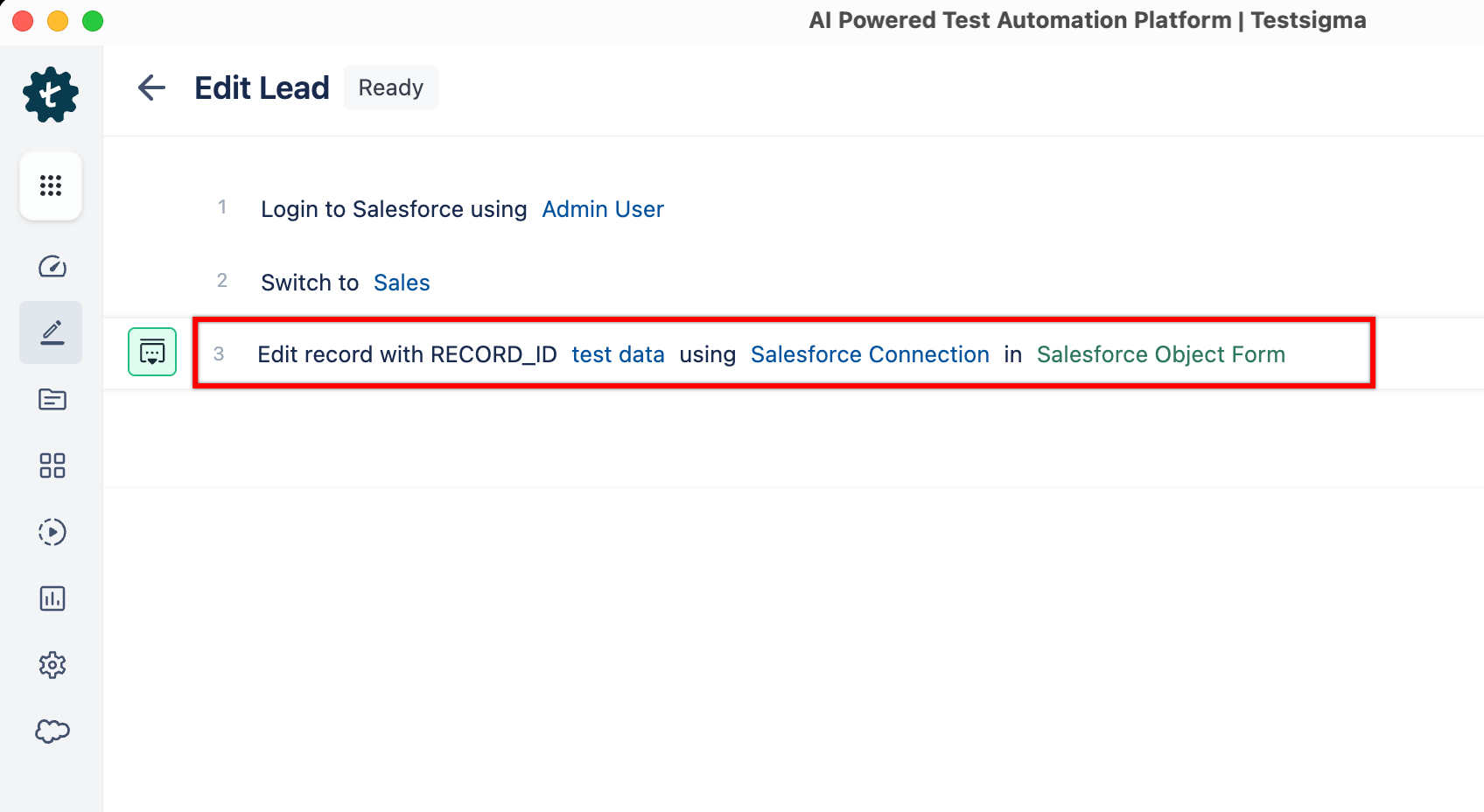
+2. To edit any lead record using **RECORD_ID**, you can use the following NLP:
+
+ 
+
+ Here’s a quick GIF demonstrating how to edit a Salesforce lead record.
+
+ 
+
+
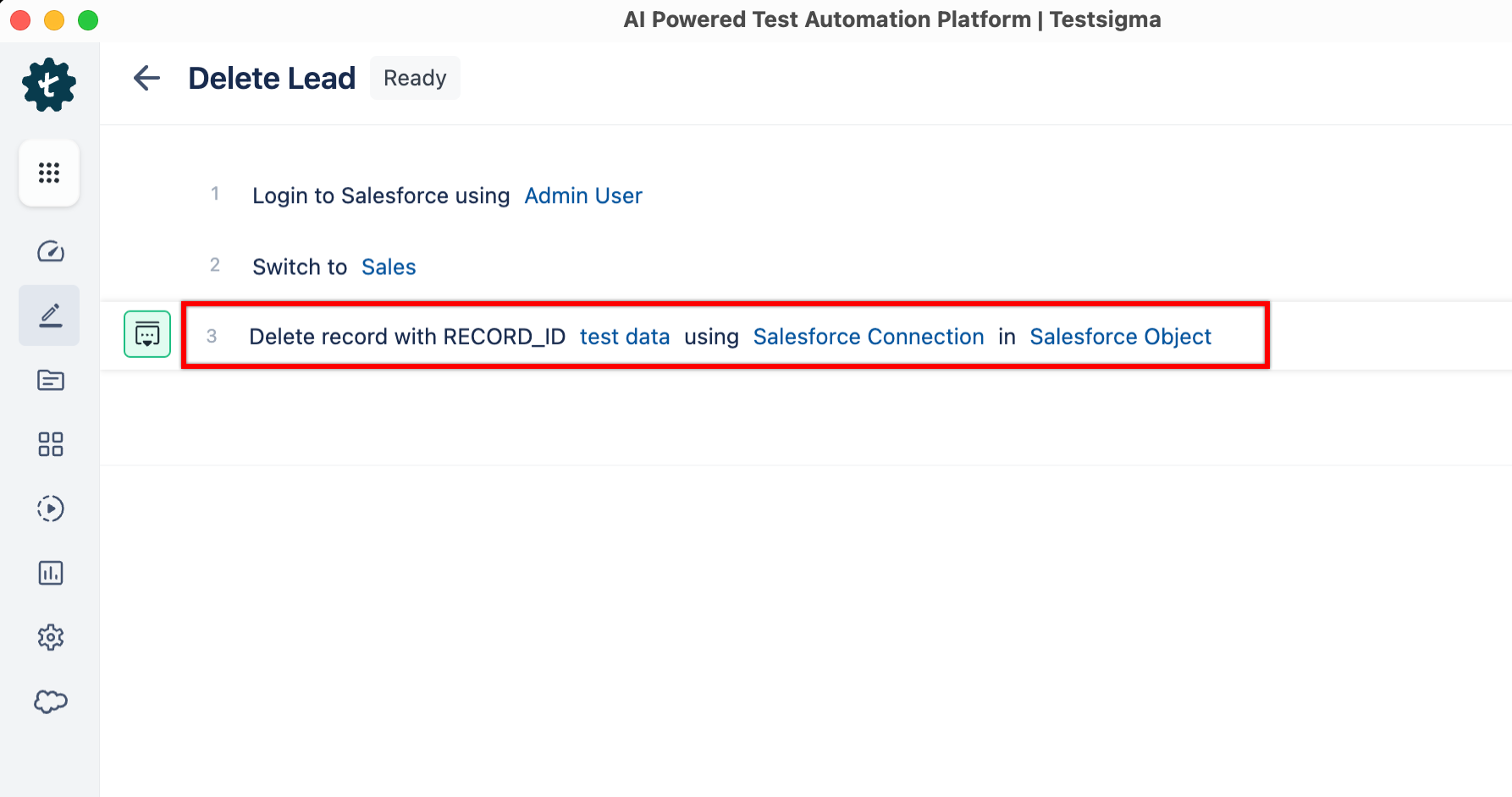
+3. To delete any lead record using **RECORD_ID**, you can use the following NLP:
+
+ 
+
+ Here’s a quick GIF demonstrating how to delete a Salesforce lead record.
+
+ 
+
---
\ No newline at end of file
diff --git a/src/pages/docs/troubleshooting/salesforce-testing/most-common-issues.md b/src/pages/docs/troubleshooting/salesforce-testing/most-common-issues.md
new file mode 100644
index 00000000..f8bc22c1
--- /dev/null
+++ b/src/pages/docs/troubleshooting/salesforce-testing/most-common-issues.md
@@ -0,0 +1,126 @@
+---
+title: "Issues While Testing Apps Built on Salesforce"
+page_title: "Troubleshooting Some General Issues"
+metadesc: "Learn how to resolve some of the general issues while testing applications built on Salesforce | Troubleshooting general issues in Salesforce Testing"
+noindex: false
+order: 23.911
+page_id: "Troubleshooting Guide for Salesforce Testing"
+warning: false
+contextual_links:
+- type: section
+ name: "Contents"
+- type: link
+ name: "Authorization Failure"
+ url: "#authorization-failure"
+- type: link
+ name: "Login NLP is Not Working"
+ url: "#login-nlp-is-not-working"
+- type: link
+ name: "MFA Challenge"
+ url: "#mfa-challenge"
+---
+
+---
+
+This troubleshooting guide for Salesforce Testing in Testsigma provides solutions to common issues while testing applications built on Salesforce.
+
+---
+
+## **Authorization Failure**
+
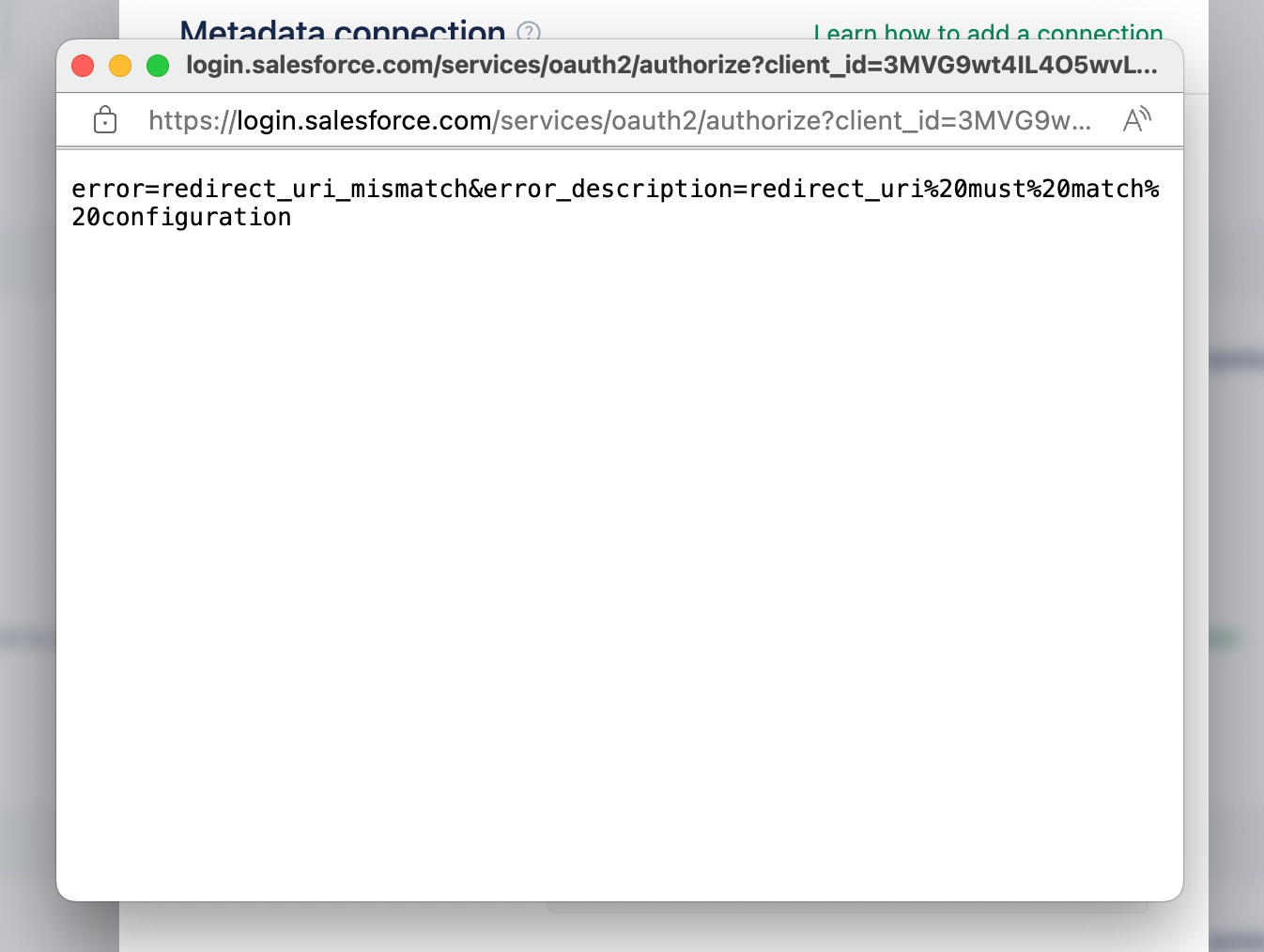
+### **Symptoms:**
+
+
+### **Possible Causes:**
+- **ClientId** and **Secret** are incorrect.
+- **Environment** might be wrong (e.g., production vs. development).
+- **Callback URL** is incorrect.
+
+### **Steps to Resolve**
+
+**1. Verify ClientId and Secret:**
+- Doubl check the **ClientId** and **Secret** provided by the service and ensure there are no typos.
+- Regenerate the **ClientId** and **Secret** if necessary.
+
+**2. Check Environment Settings:**
+- Ensure the correct **Environment** is selected (development, staging, production).
+- Confirm your application's configuration.
+
+**3. Check Callback URL:**
+- Ensure the **Callback URL** matches the service provider's settings and check if there are typos.
+- Ensure your server is configured to handle the callback request.
+
+**4. Additional Notes:**
+- Ensure the application's **permissions** and **scopes** are set correctly while creating a connected app.
+- Check network & firewall settings for blocks on the authorization endpoint.
+
+For more information, refer to [creating a connected application](https://testsigma.com/docs/salesforce-testing/connected-app/).
+
+---
+
+## **Login NLP is Not Working**
+
+### **Symptoms:**
+Users can sync metadata but the login step fails.
+
+
+### **Possible Causes:**
+
+- Salesforce **Access Token** and **Refresh Token** might have expired.
+- The same connected app is being used by multiple users simultaneously.
+- Users might have changed the connected app configuration in the Salesforce org.
+
+### **Steps to Resolve**
+
+**1. Re-authenticate Salesforce Connection:**
+
+- Try to authenticate the Salesforce connection again and obtain a new Access Token and Refresh Token.
+
+**2. Verify Connected App Settings:**
+
+- Check the connected app configuration in Salesforce and ensure all settings are correct.
+
+**3. Best Practices:**
+
+- Use different connections for different testing environments to avoid conflicts.
+
+
+---
+
+## **MFA Challenge**
+
+### **Symptoms:**
+Users can sync metadata but encounter an MFA challenge during the process.
+
+### **Possible Causes:**
+- Salesforce org configuration needs verification.
+
+### **Steps to Resolve**
+
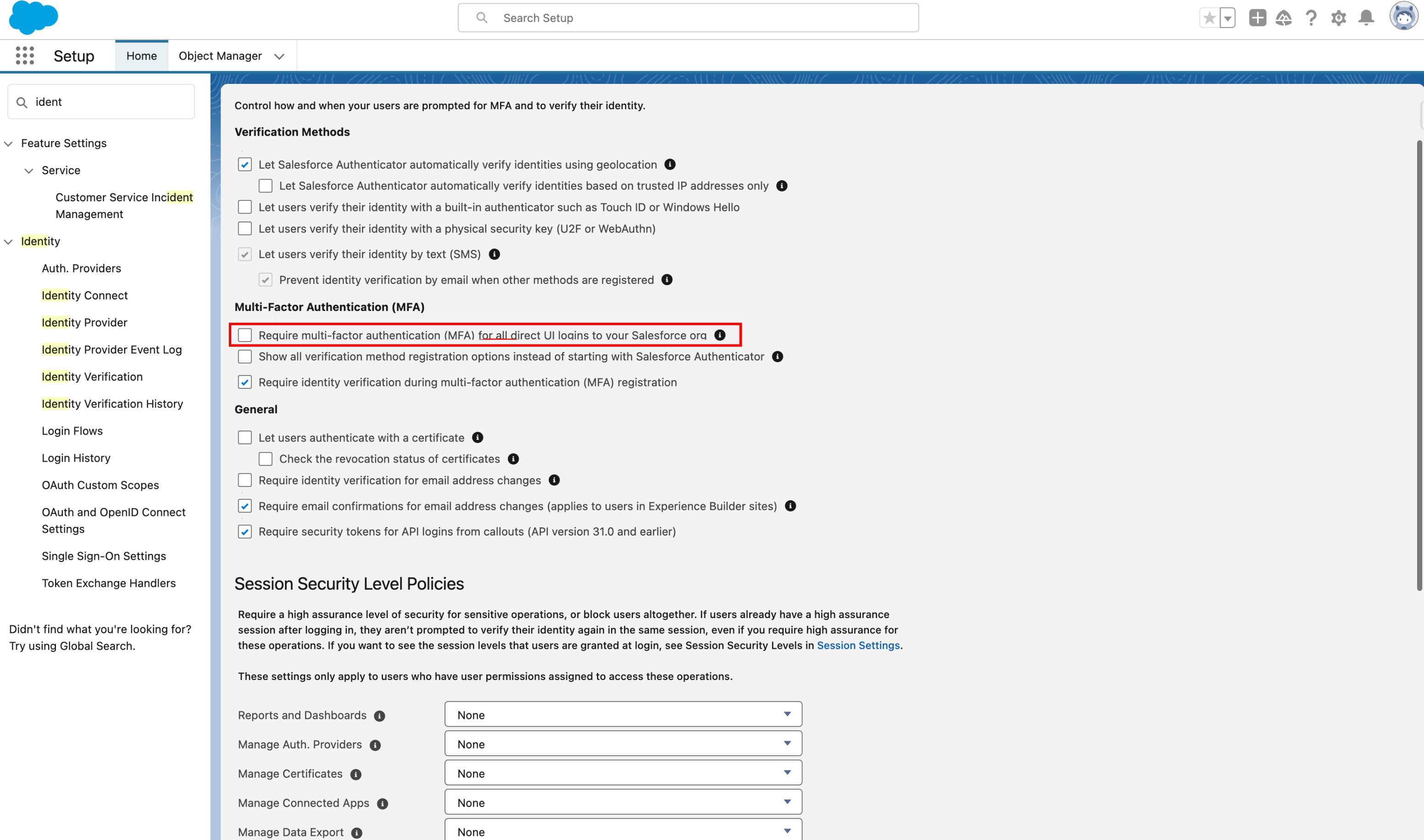
+**1. Disable Org Level MFA Configurations:**
+
+- Disable the **Require multi-factor authentication (MFA) for all direct UI logins to your Salesforce org** setting.
+ 
+
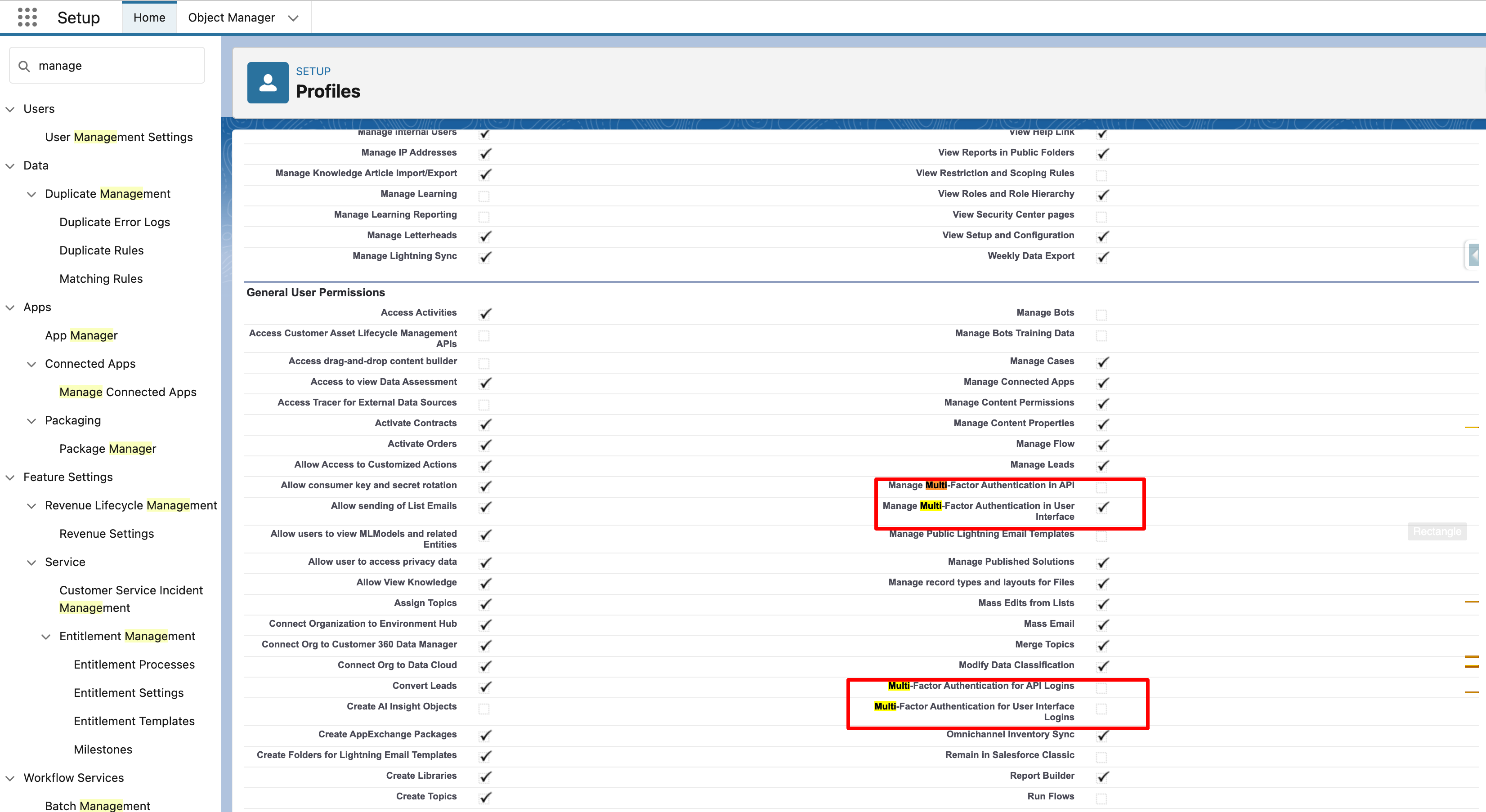
+**2. Disable User Level MFA Configurations:**
+- Ensure that user-level MFA settings follow the required configuration. If not, adjust them accordingly by navigating to **Account > Settings > Advanced User Settings > User Details > Profile**
+
+ 
+
+ 
+
+**3. Best Practices:**
+
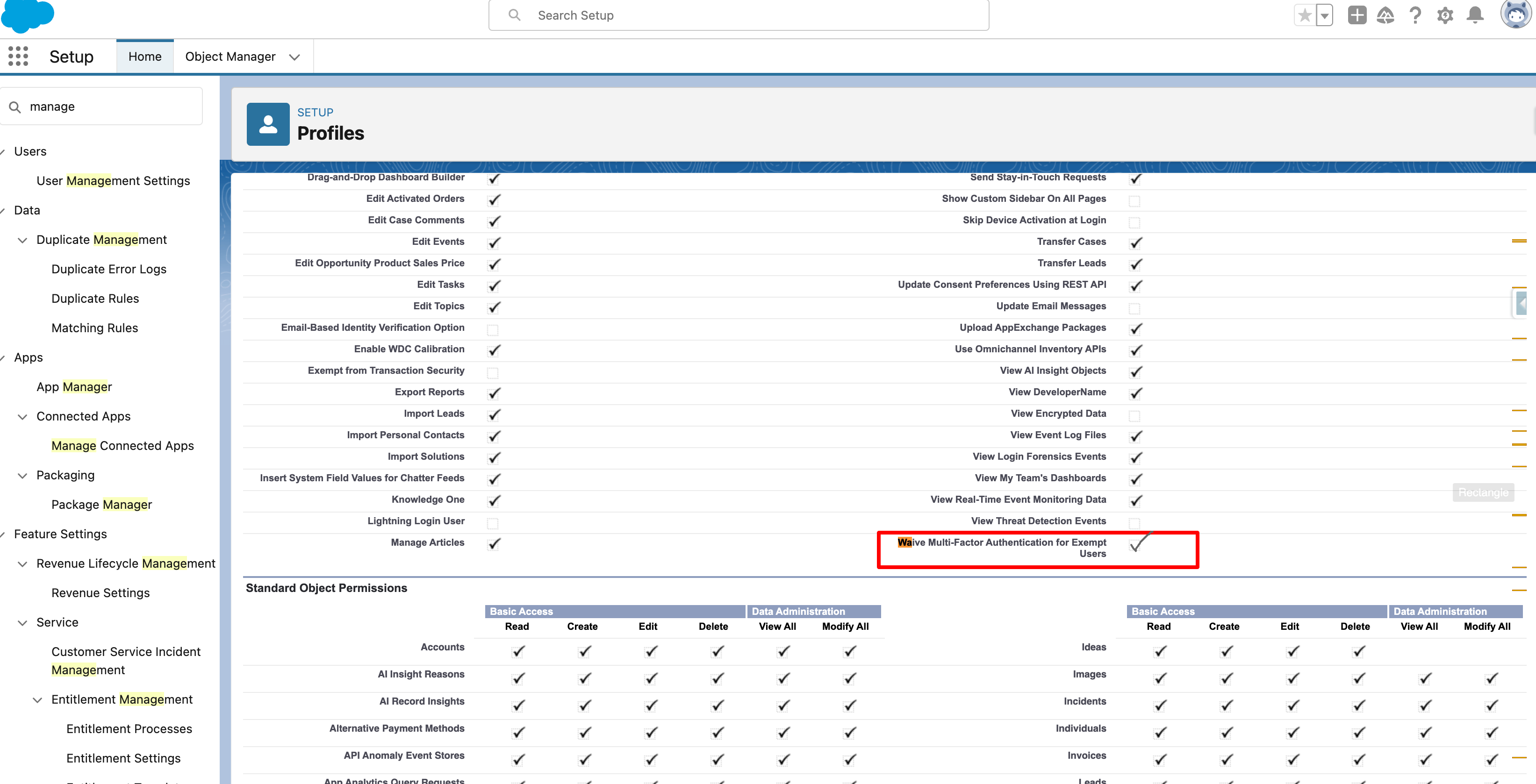
+**Waive MFA for Exempt Users:**
+
+ - Ask customers to enable **Waive Multi-Factor Authentication for Exempt Users** in Salesforce.
+ 
+
+
+**Create a Permission Set for Automation Users:**
+
+ - Create a new permission set specifically for automation users.
+
+ - Assign this permission set to users who are performing Salesforce authentication.
+
+---
\ No newline at end of file
From 8bb3c828d0e13596e7d67568165792e9e9238503 Mon Sep 17 00:00:00 2001
From: Sangith Ravichandran
<119392848+sangithravichandran@users.noreply.github.com>
Date: Mon, 8 Jul 2024 12:44:14 +0530
Subject: [PATCH 2/2] Updated SAML SSO document (#441)
Co-authored-by: Bharath Krishna <118433150+bharathk08@users.noreply.github.com>
---
.../docs/configuration/security/okta-sso.md | 169 +++++++-----------
1 file changed, 69 insertions(+), 100 deletions(-)
diff --git a/src/pages/docs/configuration/security/okta-sso.md b/src/pages/docs/configuration/security/okta-sso.md
index 328d32d2..354cffd3 100644
--- a/src/pages/docs/configuration/security/okta-sso.md
+++ b/src/pages/docs/configuration/security/okta-sso.md
@@ -1,10 +1,10 @@
---
title: "Setting Up Okta Single Sign-On Integration with SAML Login in Testsigma"
-page_title: "Configuring Okta Single Sign-On Integration with SAML in Testsigma"
+page_title: "Configuring Okta SSO Integration with SAML in Testsigma"
metadesc: "Single Sign-On (SSO) provides faster, easier, and trusted access to applications. Learn how to set up Single Sign-On (SSO) with SAML login easily in Testsigma."
noindex: false
order: 19.23
-page_id: "Setting Up Okta Single Sign-On Integration with SAML Login in Testsigma"
+page_id: "setting-up-okta-sso-with-saml--in-testsigma"
search_keyword: ""
warning: false
contextual_links:
@@ -14,133 +14,102 @@ contextual_links:
name: "Terminology"
url: "#terminology"
- type: link
- name: "I. Getting the Testsigma Configuration for Okta"
- url: "#i-getting-the-testsigma-configuration-for-okta"
+ name: "Getting the Testsigma Configuration for Okta"
+ url: "#getting-the-testsigma-configuration-for-okta"
- type: link
- name: "II. Create and configure OKTA"
- url: "#ii-create-and-configure-okta"
+ name: "Create and configure Okta"
+ url: "#create-and-configure-okta"
- type: link
- name: "III. Configuring Testsigma for Okta"
- url: "#iii-configuring-testsigma-for-okta"
+ name: "Configure Testsigma for Okta SSO"
+ url: "#configure-testsigma-for-okta-sso"
+- type: link
+ name: "Sign in to Testsigma with SAML SSO"
+ url: "#sign-in-to-testsigma-with-saml-sso"
+- type: link
+ name: "Disable Configured SSO"
+ url: "#disable-configured-sso"
---
---
-Single Sign-On (SSO) provides faster, easier, and trusted access to applications.
-
-With SSO, you are not required to store and manage passwords for the websites you use regularly. Instead of using passwords, applications that allow SSO login accept secured tokens that grant access to the application. This is mostly used for enterprises and SMBs for easy workforce identity management.
-
-You can enable Single Sign-On (SSO) in Testsigma with Okta. Once configured, you can log into your Okta Dashboard to see your SSO-supported applications, including Testsigma. Okta will verify the user's identity and permissions, and then grant them access to Testsigma.
-
+Single Sign-On (SSO) provides faster, easier, and more secure application access, enhancing user experience and security. SSO allows users to access multiple applications with a single login credentials, eliminating the need to remember multiple passwords. Instead of passwords, SSO uses secure tokens to grant access, making it a preferred solution for enterprises and SMBs to manage workforce identities efficiently. This guide will help you configure Okta and Testsigma to work together seamlessly, simplifying user access management and improving productivity.
---
+
## **Terminology**
-Here are a few entities that you need to be aware of before we move on to the details:
+Familiarise yourself with these key terms before proceeding:
-|A user|The person requesting access to the service. In this case, Testsigma App User|
-|-----|----------|
-|A service provider(SP)|The application that provides the service or protects the resource. In this case, Testsigma App|
-|An identity provider(IdP)|The service/ repository that manages the user information. It may be Okta, Onelogin, Azure AD, or an in-house IdP/IAM Implementation|
-|Entity ID|Entity ID is an identifier(an alphanumeric string or URI given by the Service Provider (SP) that uniquely identifies it. It's often part of a metadata file (an XML file with a certificate, entity ID, and endpoint URLs). You would get this from the IP (Okta, Onelogin e.t.c).|
+| Term | Definition |
+|----------------------------------|-------------------------------------------------------------------------------------|
+| User | The person requesting access to the service. In this case, the Testsigma app user. |
+| Service Provider (SP) | The application providing the service. Here, it's Testsigma. |
+| Identity Provider (IdP) | The service managing user information, such as Okta, OneLogin, or Azure AD. |
+| SAML Certificate/X.509 Certificate | A digital certificate used to verify the identity of the entities in SAML transactions. |
+| Single Sign-On URL | The URL where authentication requests are sent for SSO. |
+| Audience URI (SP Entity ID) | The unique identifier of the service provider, often a URL. |
+| Default RelayState | The URL to redirect users to after authentication. |
+| Name ID Format | The format of the user identifier sent in the SAML assertion, typically an email address. |
---
-## **I. Getting the Testsigma Configuration for Okta**
-
-Navigate to **Settings > Security**
-
-
-The security page looks as shown below if SSO has not been enabled yet:
+## **Getting the Testsigma Configuration for Okta**
+1. Navigate to **Settings** > **Security (SSO)**.
+2. On the **Security SSO** page, you will see options for **Google** and **SAML**. Enable the **SAML** toggle.
[[info | NOTE:]]
-|*If you are interested to know how you can set up Google SSO with Testsigma, refer [here](https://testsigma.com/docs/configuration/security/google-sso/)*.
-
-
-You will see two options here - **Google** and **SAML**. Choose SAML and click the **Proceed** button.
-
-
-
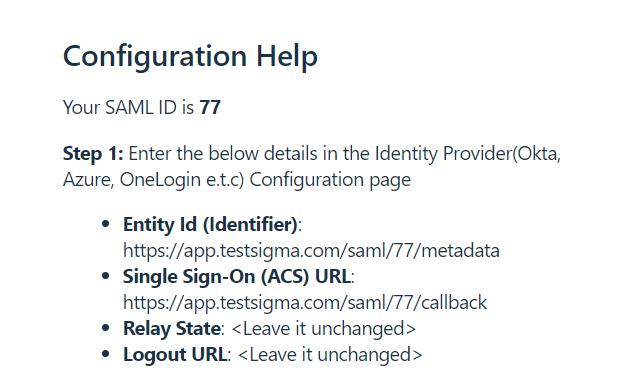
-You will find all the details you need to enter in Okta here as shown below:
-The important ones are **‘Entity ID’** and **‘Single Sign-On(ACS) URL’**(refer to the Terminology section).
-Note these down to use in the next section - section II.
+| You can use only one SSO for your account. If you are using Google SSO, turn it off first.
+3. In the **Enable SSO** pop-up, record the **Entity ID (Identifier)** and **Single Sign-On (ACS) URL** for use in Okta configuration. 
---
-## **II. Create and configure OKTA**
-
-[[info | NOTE:]]
-|*We strongly suggest you check with your IT team before trying the below steps since they might have exclusive admin access to the IdP configuration.*
-
-
-
-1. Navigate to https://www.okta.com/login and login to the Admin console in OKTA.
-
- **a.** In the Admin Console, under **Applications**, click **Create App Integration** to get the Create a new app integration form as shown below:
-
- 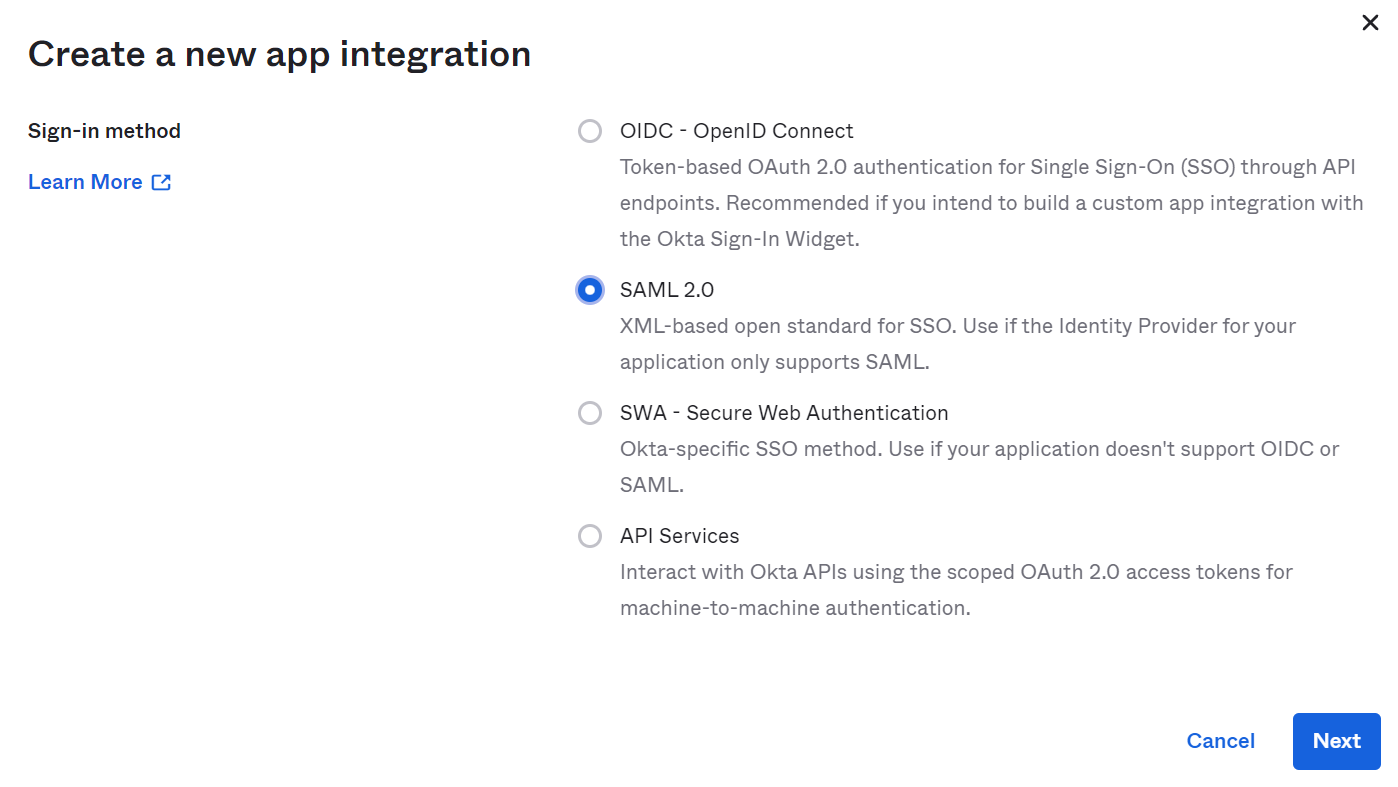
- **b.** Choose SAML 2.0 and click Next
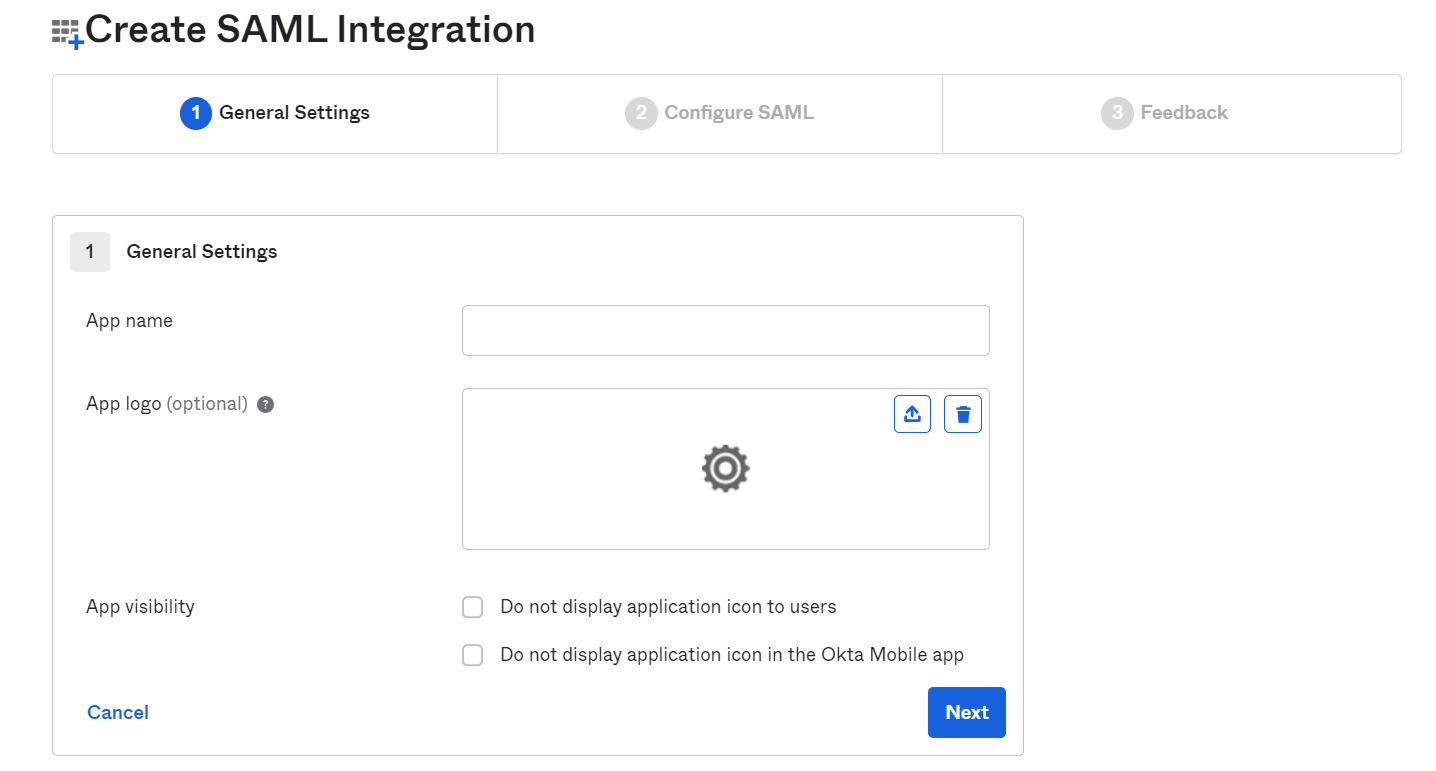
-2. On the first page - **General Settings,** you need to enter the details of the application (Testsigma) that you are integrating with SAML.
+## **Create and configure Okta**
- 
-
- **a.** **App Name:** Enter the application name, “Testsigma”, upload the logo (if required)
-
- **b.** **App logo and visibility:** Upload the app logo if you prefer.
-(You may choose to display or not display the icon of Testsigma to the users in the Okta app for both web and mobile)
-
-Click on **Next** to proceed.
-
-3. On the second page - **Configure SAML,** we need to provide the Configuration details we got from Testsigma App following the steps in section I.
-
- 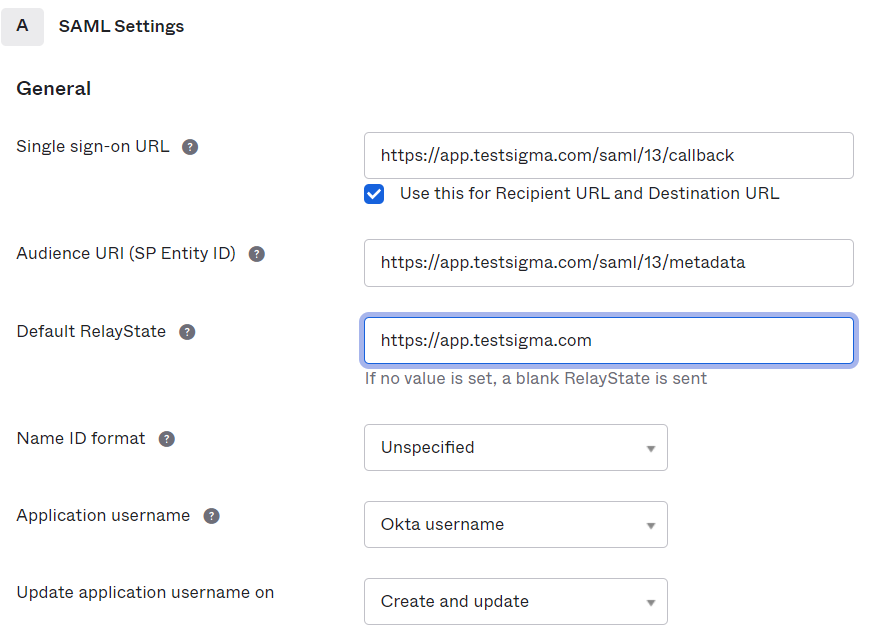
- **a.** **Single Sign-on URL:** https://app.testsigma.com/saml/77/metadata
-
- **b.** **Audience URI:** https://app.testsigma.com/saml/77/metadata
-
- **c.** **Default Relay State :** https://app.testsigma.com
-
- **d.** **Name ID Format :** EmailAddress (default)
-
- **e.** **Application Username :** Okta username (default)
-
- **f.** **Update application username on:** Create and update (default)
-
-4. On the next page, check the options, **“I'm an OKTA User and adding an Internal App”** and **“This is an internal app that we have created”** and click **Finish**.
-
-5. Next, you will see a **Sign-on methods** page. The sign-on method determines how a user signs into and manages their credentials for an application.
-
-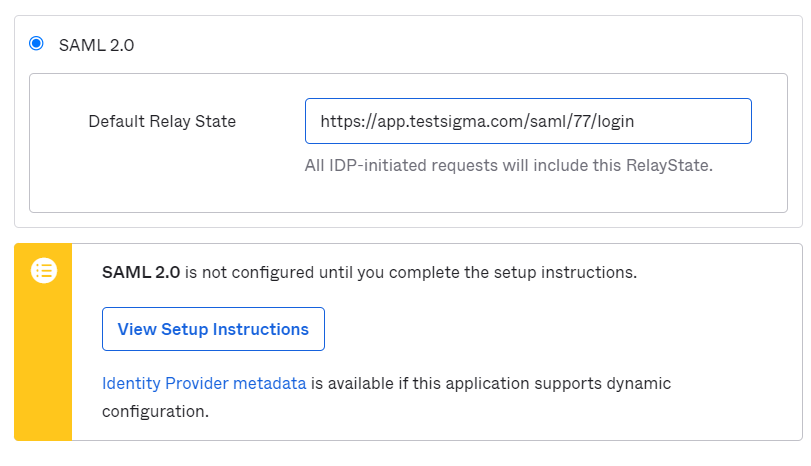
- **a.** Click on **'View Setup Instructions'**
-
-
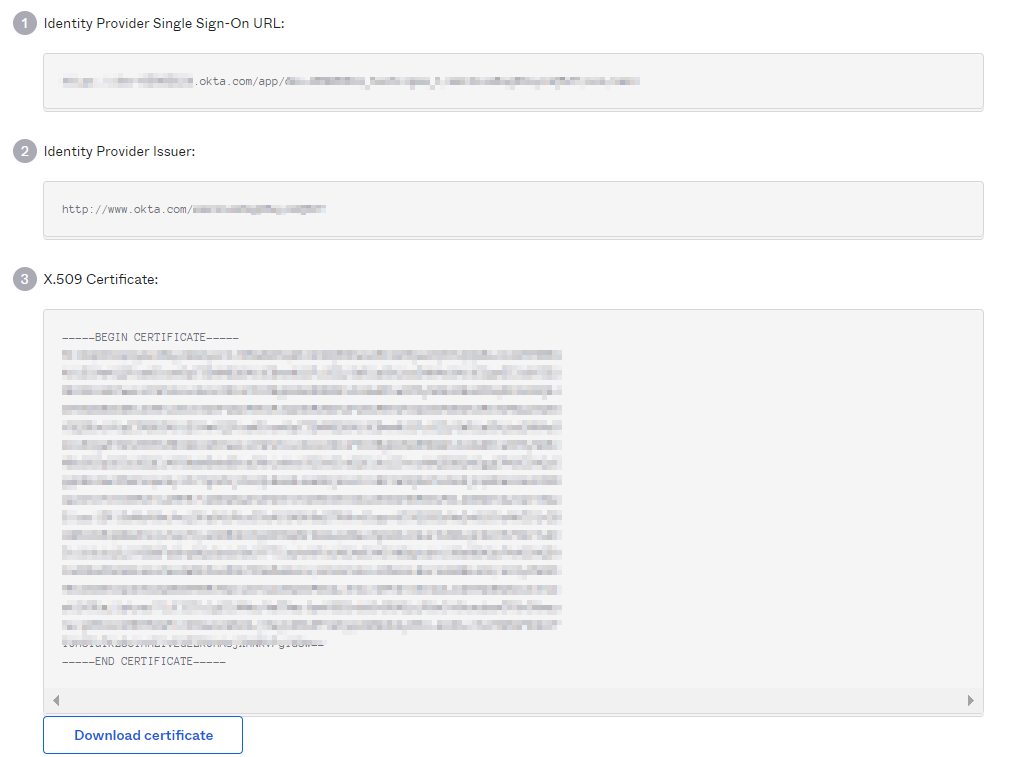
- **b.** Copy and note down the **'Identity Provider Issuer'**, **'Identity Provider Single Sign-On URL'**, and **'X.509 Certificate'** from this page.
-We will need the same on the Testsigma SAML SSO Configuration page in the next section - Section III.
-
-
-
-Now, let's move on to the configuration that we need to perform in the Testsigma App.
+1. Log in to the [Okta Admin Console](https://www.okta.com/login).
+[[info | NOTE:]]
+| Check with your IT team before proceeding, as they may have exclusive admin access to the IdP configuration.
+1. In the **Admin** Console, under **Applications**, click **Create App Integration**. Choose **SAML 2.0** and click **Next**.
+2. In **General Settings** tab fill below details and click **Next** to proceed.
+ - **App Name**: Enter Application name, example **Testsigma**:
+ - **App Logo and Visibility**: Upload the app logo if preferred. 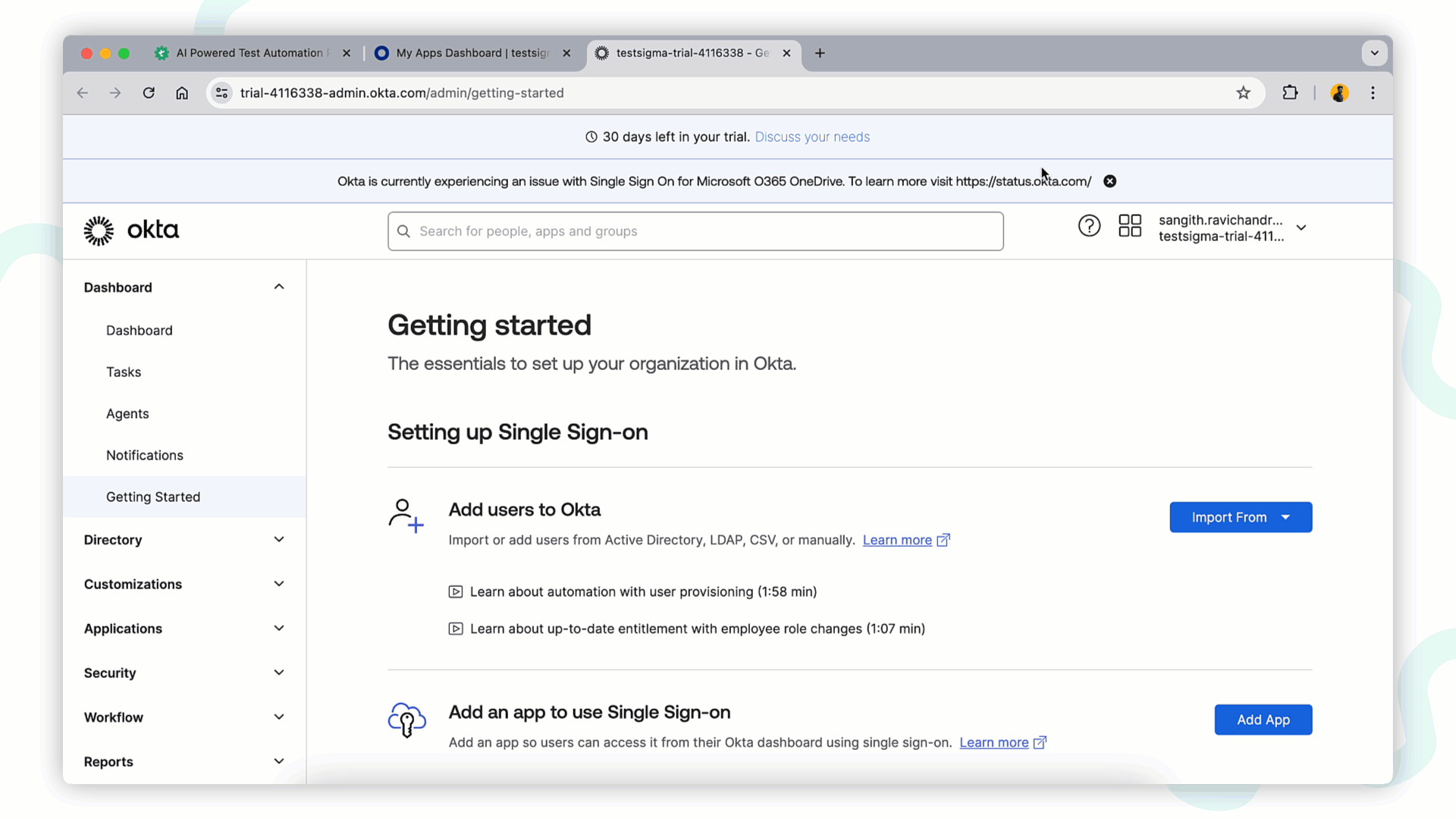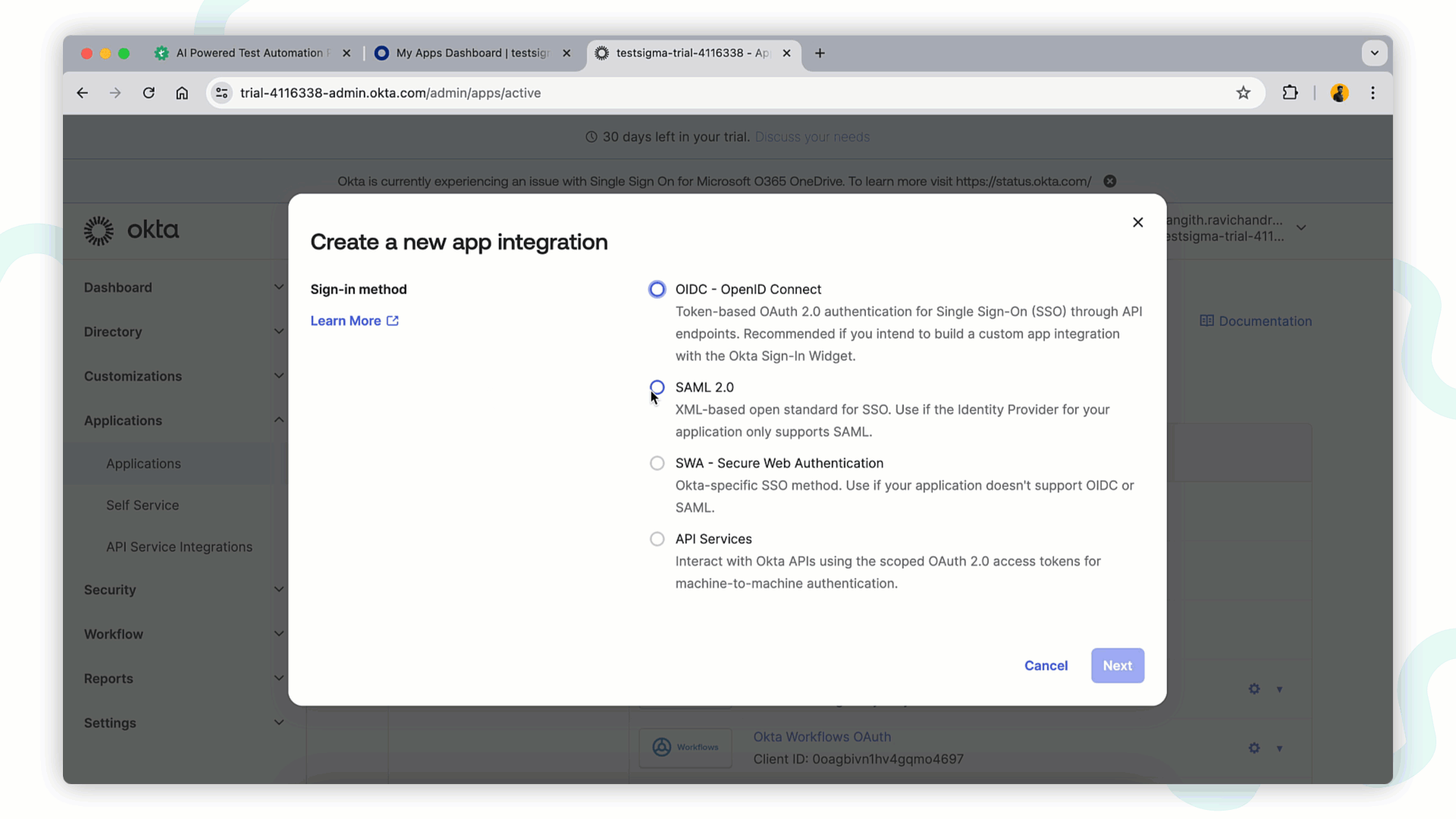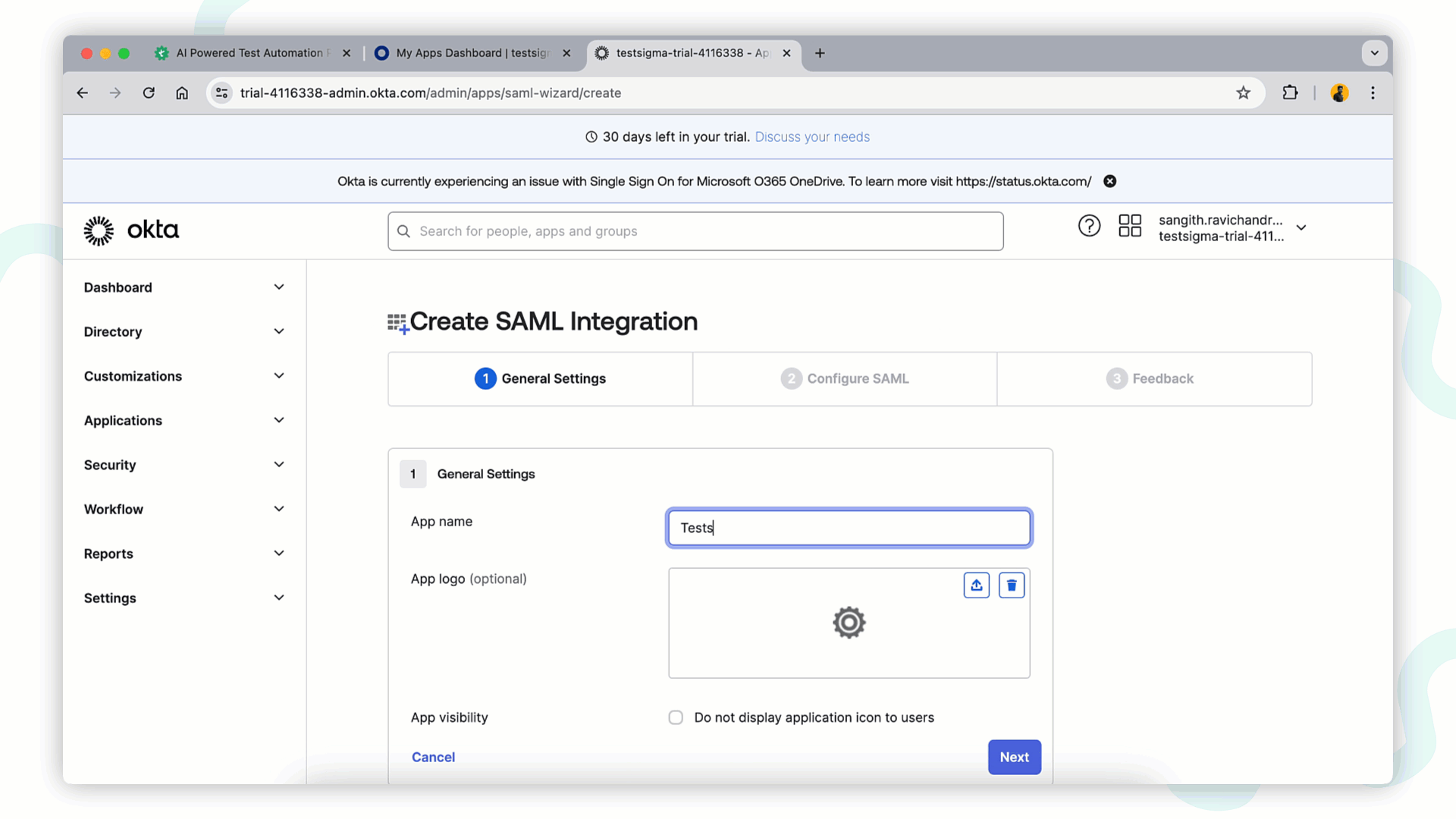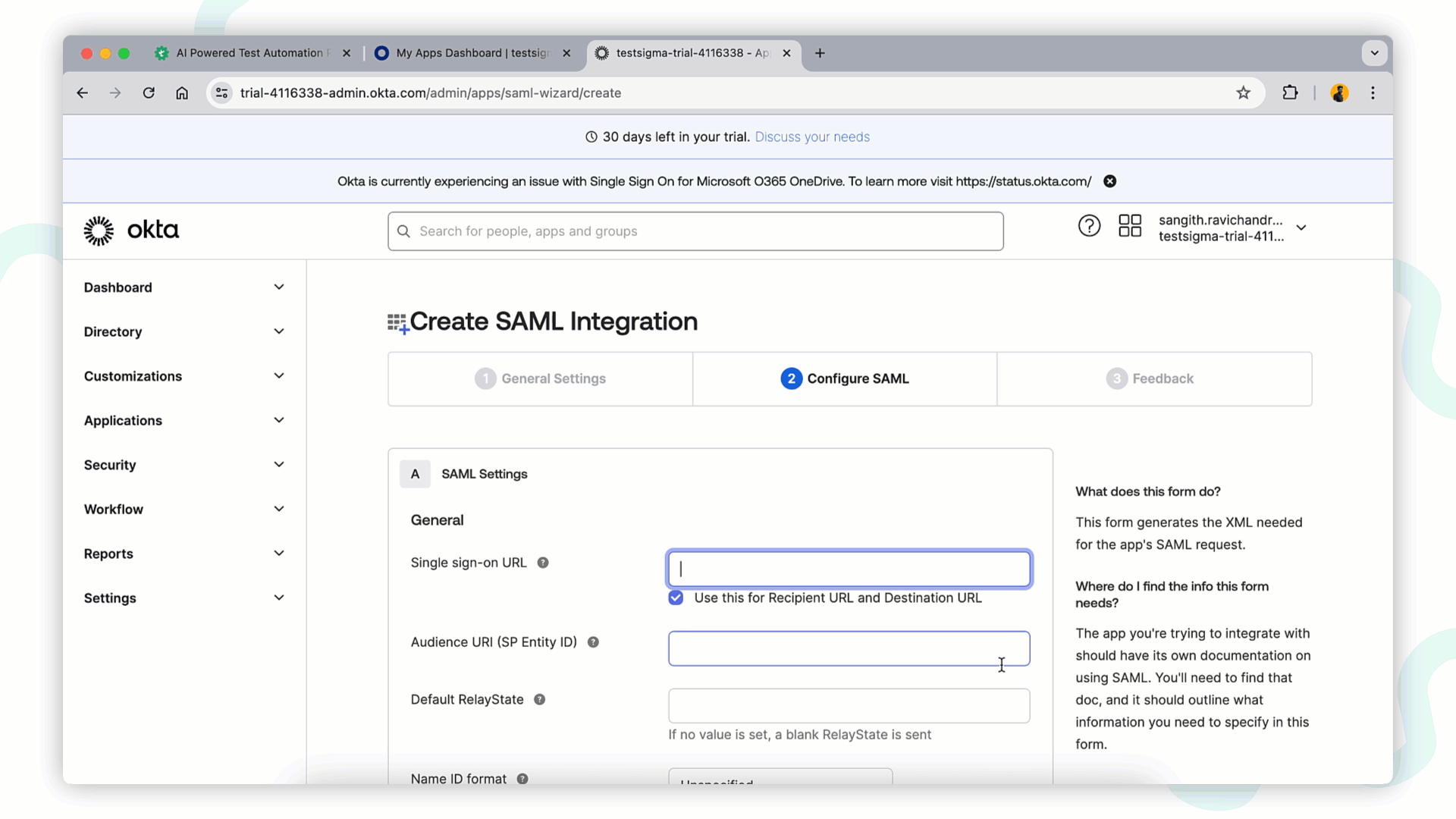
+3. Configure **SAML Settings** and click **Next** to proceed:
+ - **Single Sign-On URL**: https://app.testsigma.com/saml/250/callback
+ - **Audience URI (SP Entity ID)**: https://app.testsigma.com/saml/250/metadata
+ - **Default RelayState**: https://app.testsigma.com/ui/dashboard
+ - **Name ID Format**: Select EmailAddress from dropdown.
+ - **Application Username**: Okta username (default)
+ - **Update Application Username On**: Create and update (default)
+4. Finish Setup by selecting **"I'm an OKTA User and add an Internal App"** and **"This is an internal app we have created"**. Click **Finish**. 
+5. On the Sign-on methods page, click **View Setup Instructions**.
+6. Copy the **Identity Provider Issuer**, **Identity Provider Single Sign-On URL**, and **X.509 Certificate** for use in Testsigma.
---
-## **III. Configuring Testsigma for Okta**
-You would need to enter the Entity ID, SSO URL, and SAML Certificate you got from the last step (Step 5. b) in the previous section.
+## **Configure Testsigma for Okta SSO**
-You may notice some differences in the terminologies used within Testsigma and Okta.
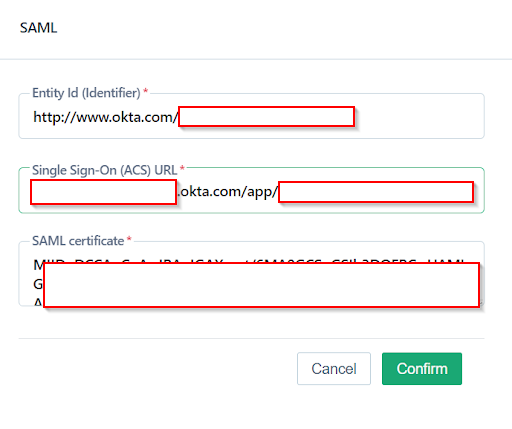
+1. In Testsigma, enter the **Entity ID**, **SSO URL**, and **SAML Certificate** recorded from Okta.
+2. Terminology Mapping:
+ - **Entity ID**: Same Identity Provider Issuer.
+ - **Identity Provider Single Sign-On URL**: Paste Single Sign-On (ACS) URL.
+ - **SAML Certificate**: Paste X.509 Certificate.
+3. Click **Confirm Credentials** to confirm the Configuration. 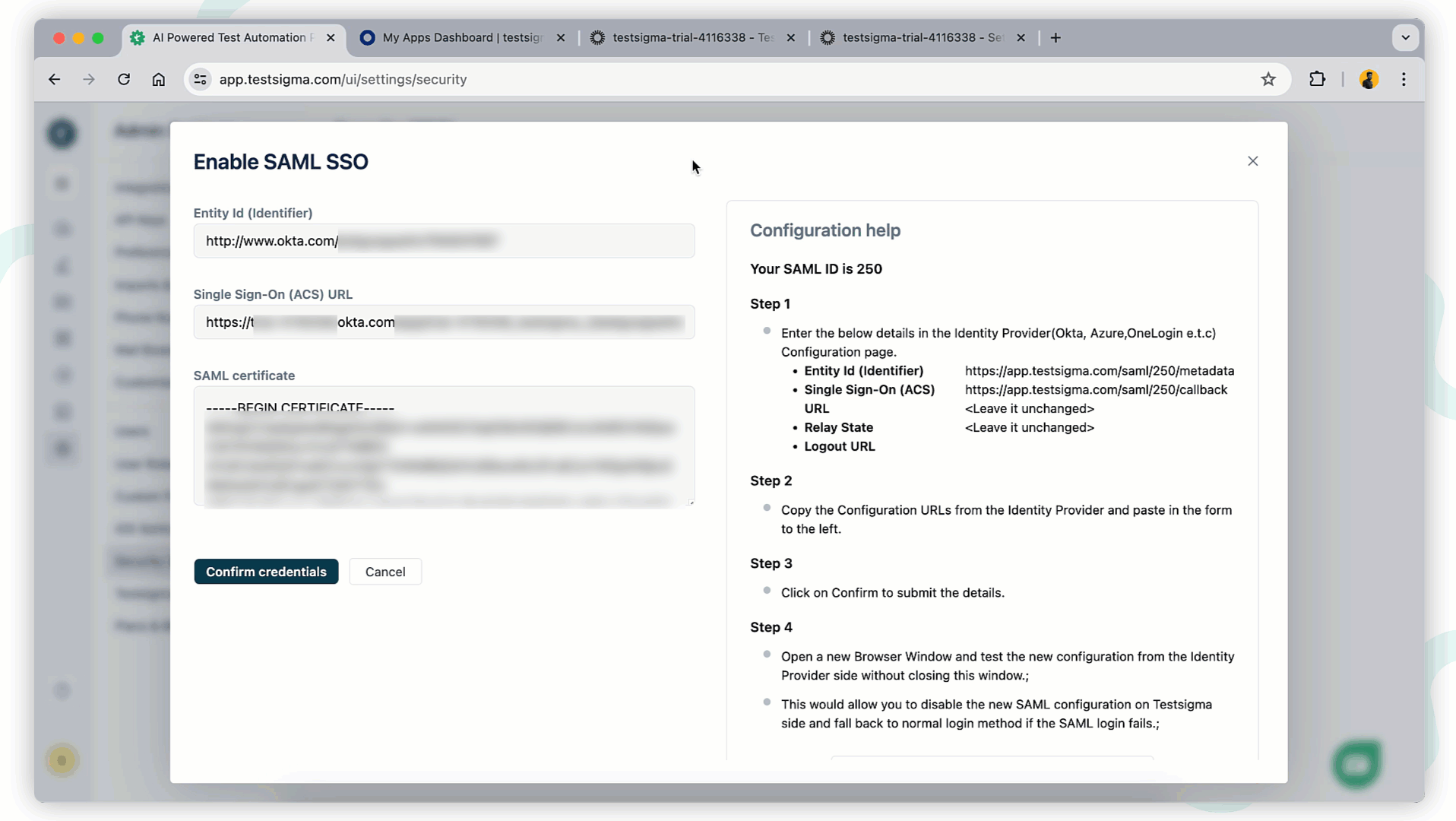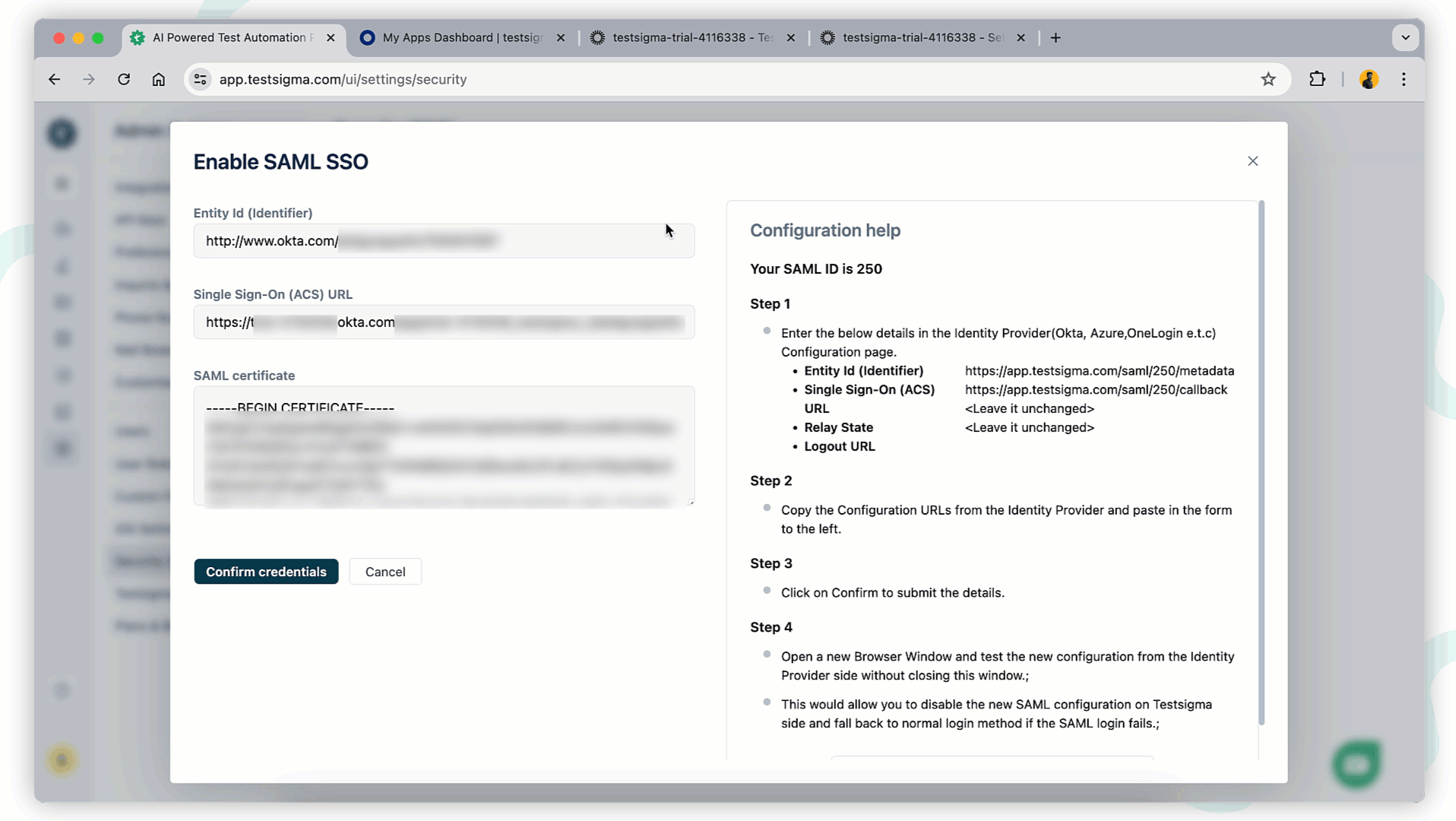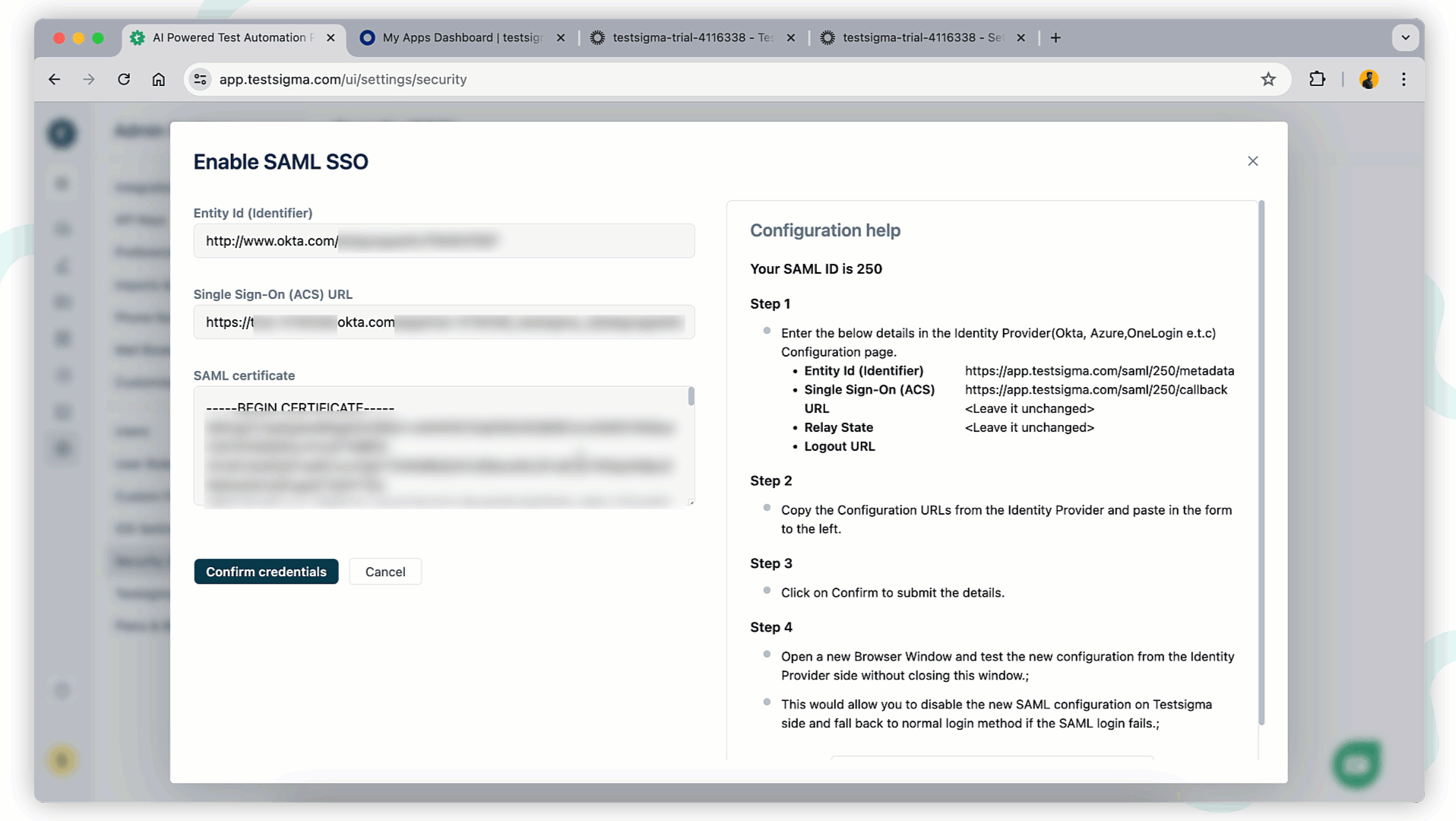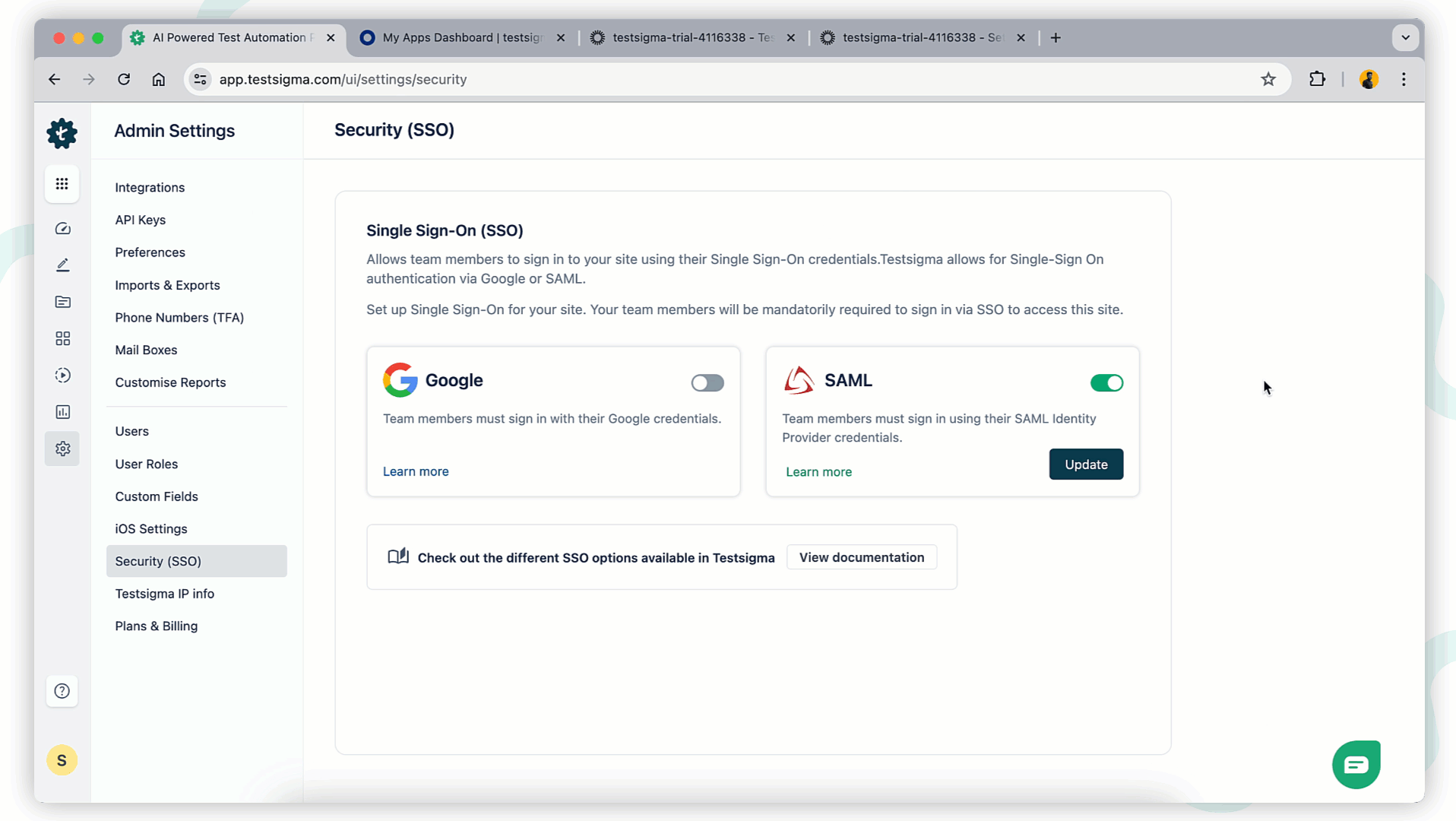
-* **Entity Id (Identifier)** is the same as **Identity Provider Issuer**
-* **Identity Provider Single Sign-On URL** is same as **Single Sign-On (ACS) URL**
-* **SAML Certificate** is referred to as **X.509 Certificate in Okta**
-
-
+---
+## **Sign in to Testsigma with SAML SSO**
-Enter the details and click **Confirm**.
+After configuring your Testsigma account with SAML, you can log in using SSO.
+1. Click **Sign in with SSO** on the Testsigma login page.
+2. Enter the **email ID** configured with SSO with the account and click **Sign in**. 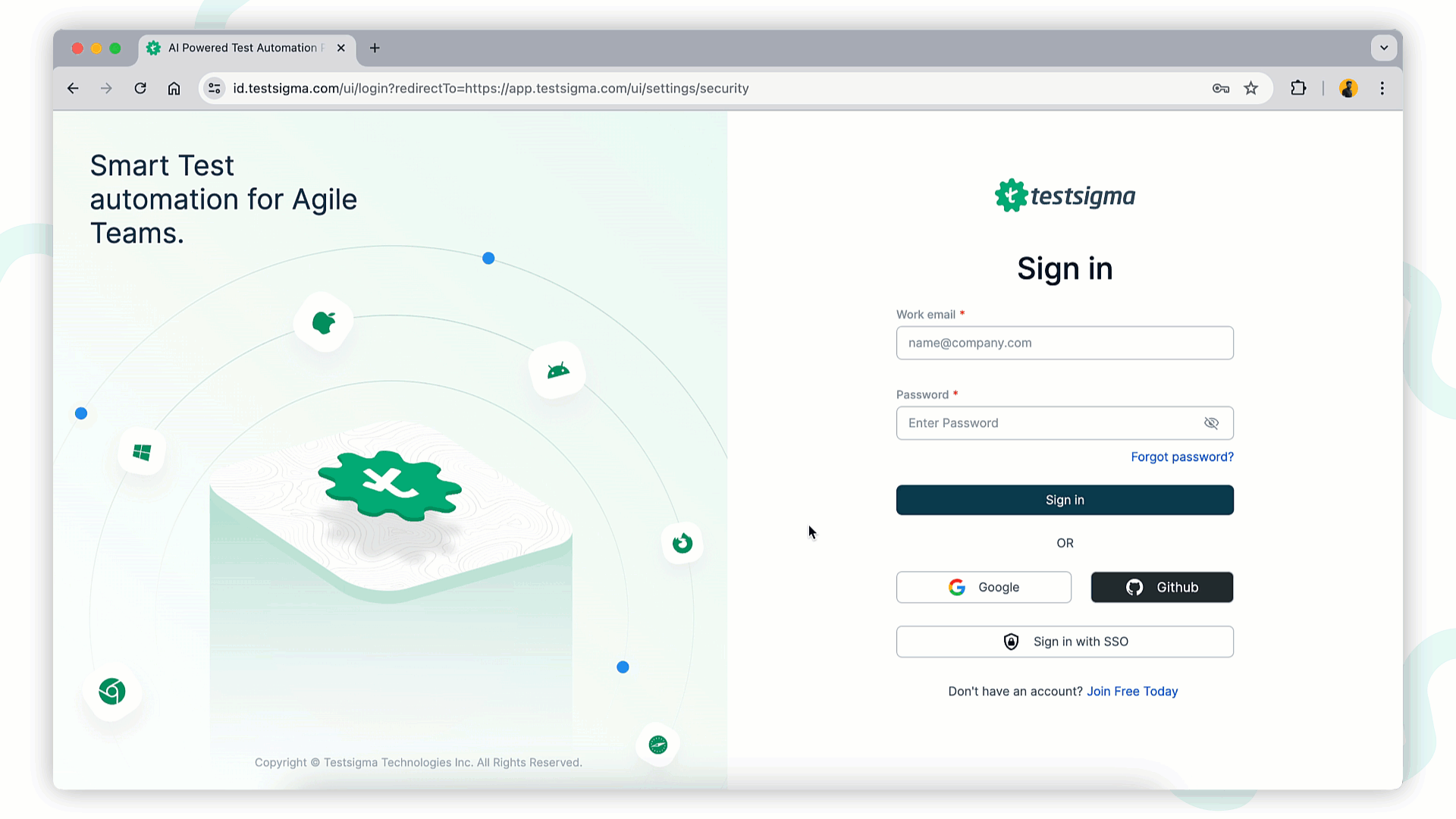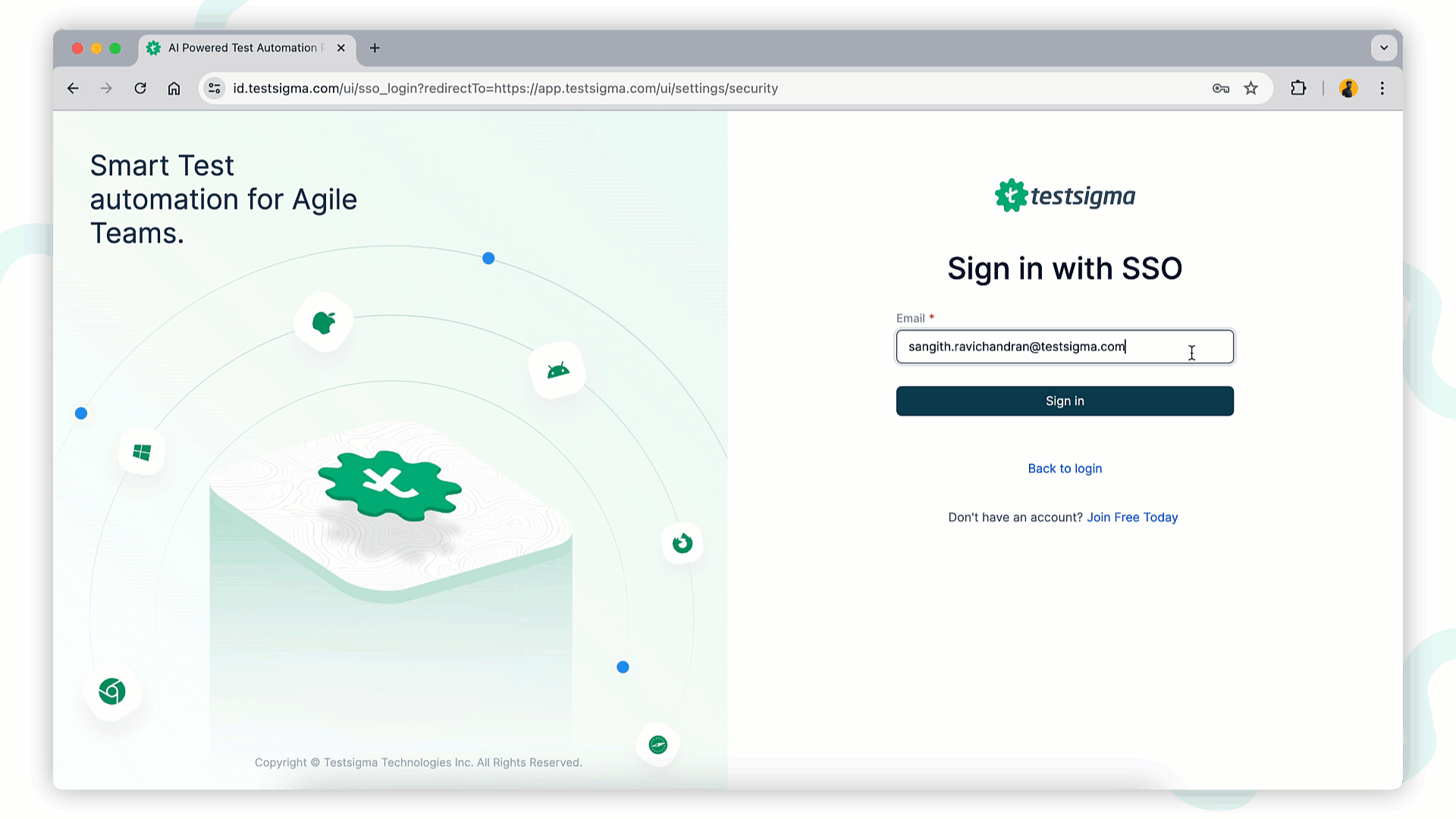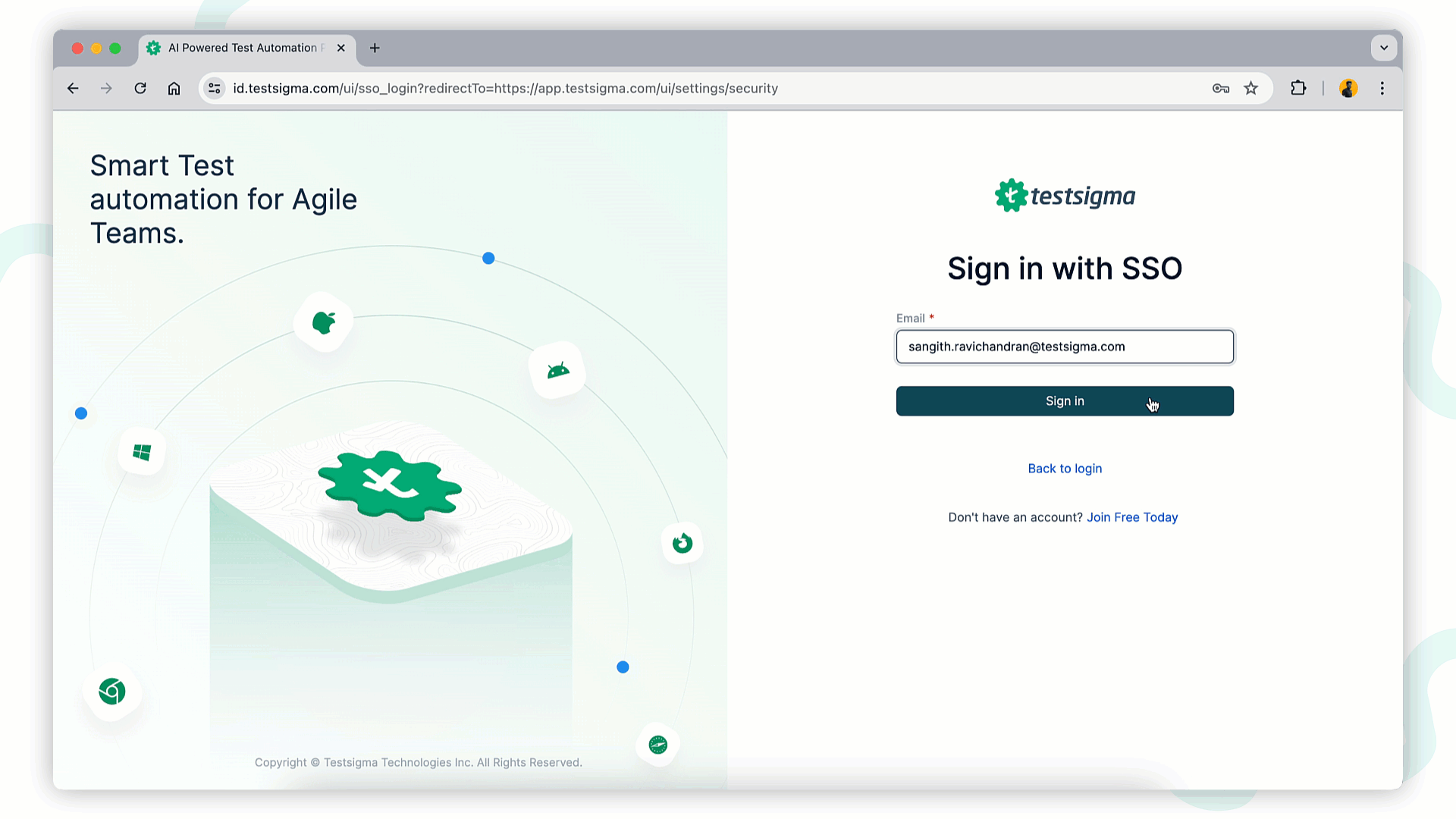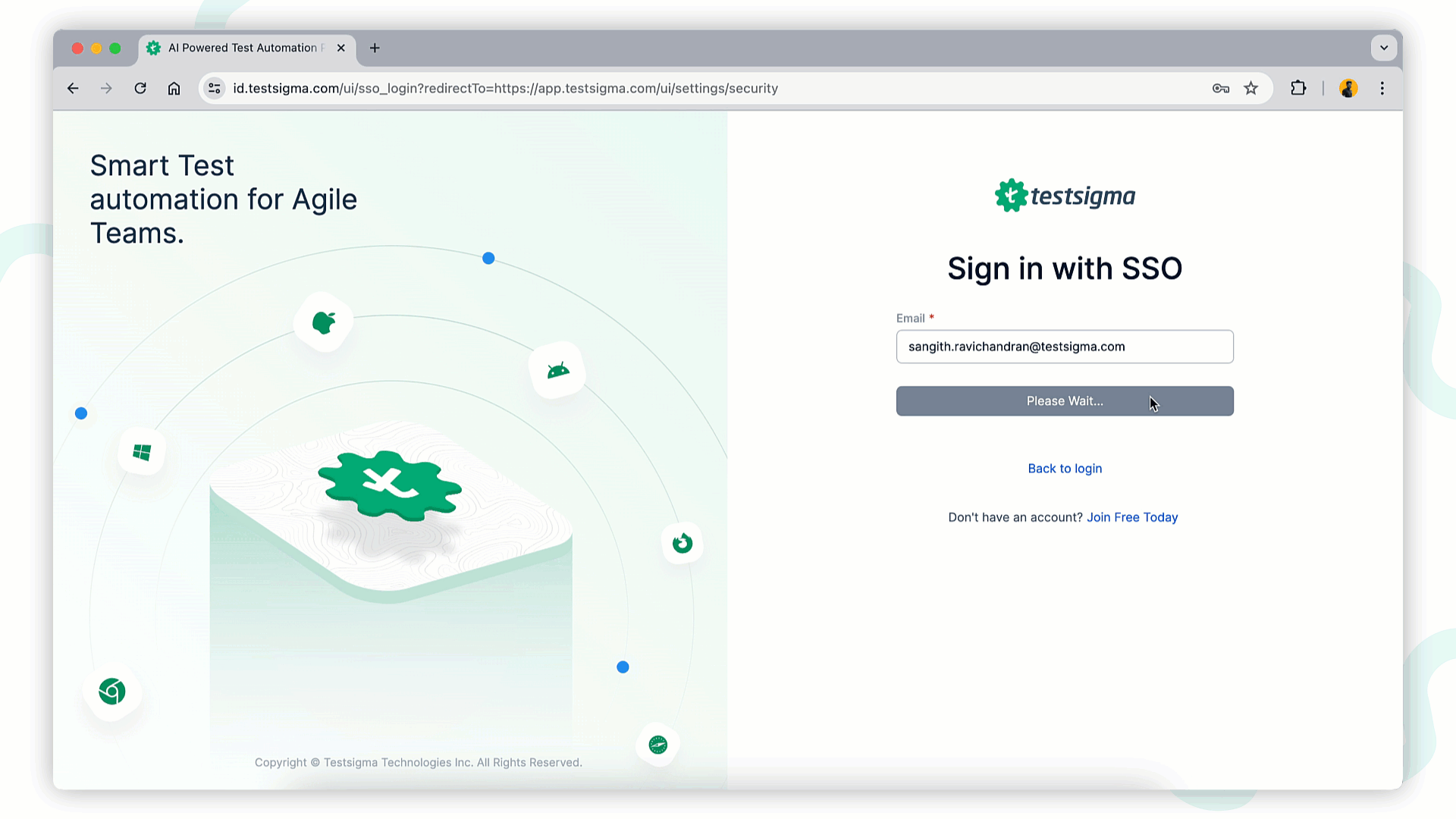
+[[info | NOTE:]]
+| - Install the Okta mobile app for the first-time authentication.
+| - You cannot log in through SSO without configuring your email.
-And, you are done.
+---
+## **Disable Configured SSO**
-To disable the SSO login using Okta, click the **Disable** button on the SAML option anytime.
+To disable SSO login using Okta, turn off the toggle to disable SAML SSO at any time. A disable SAML SSO warning prompt will appear. Click **I Understand and Disable** to remove the SSO configuration from your account. 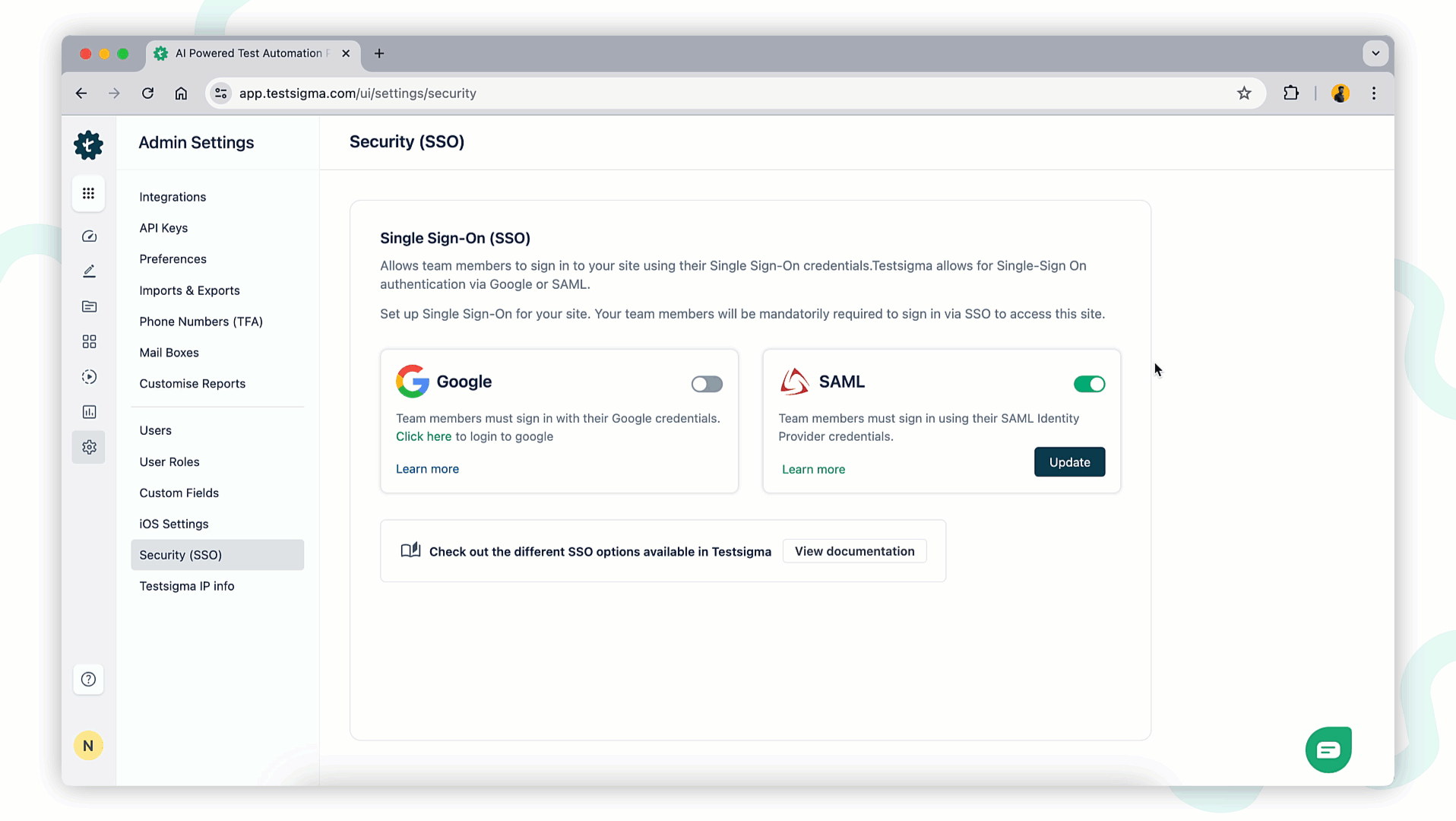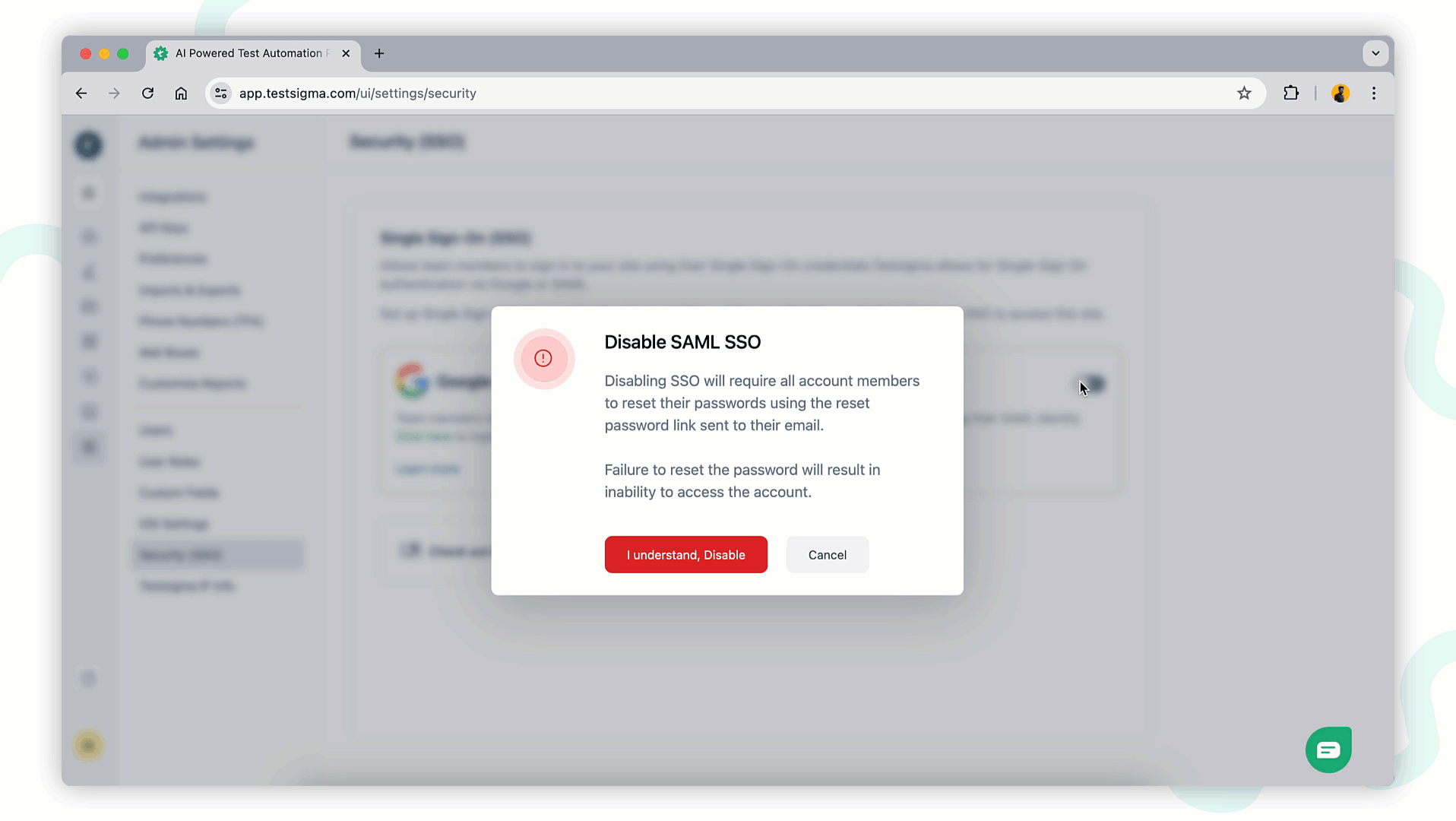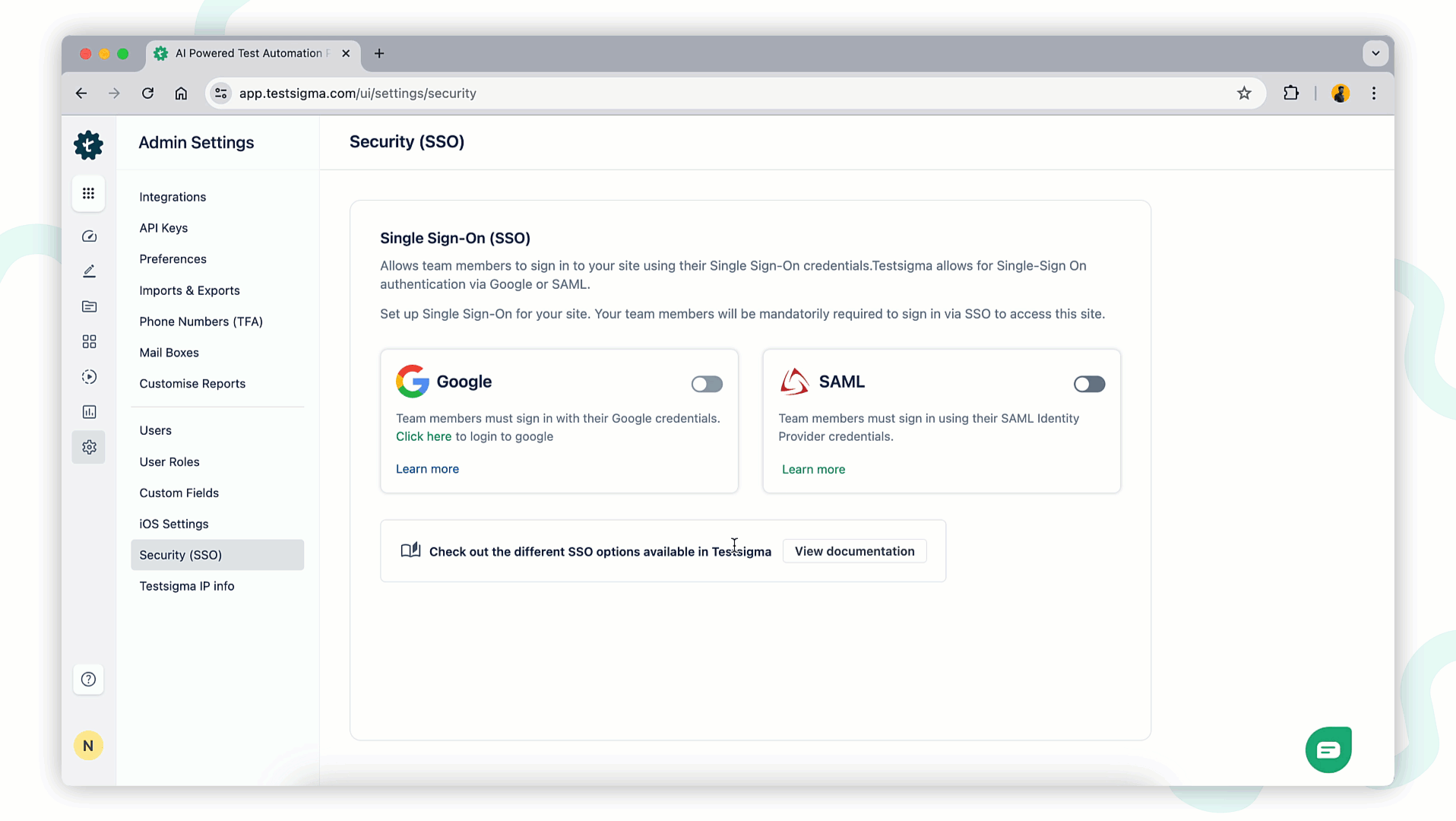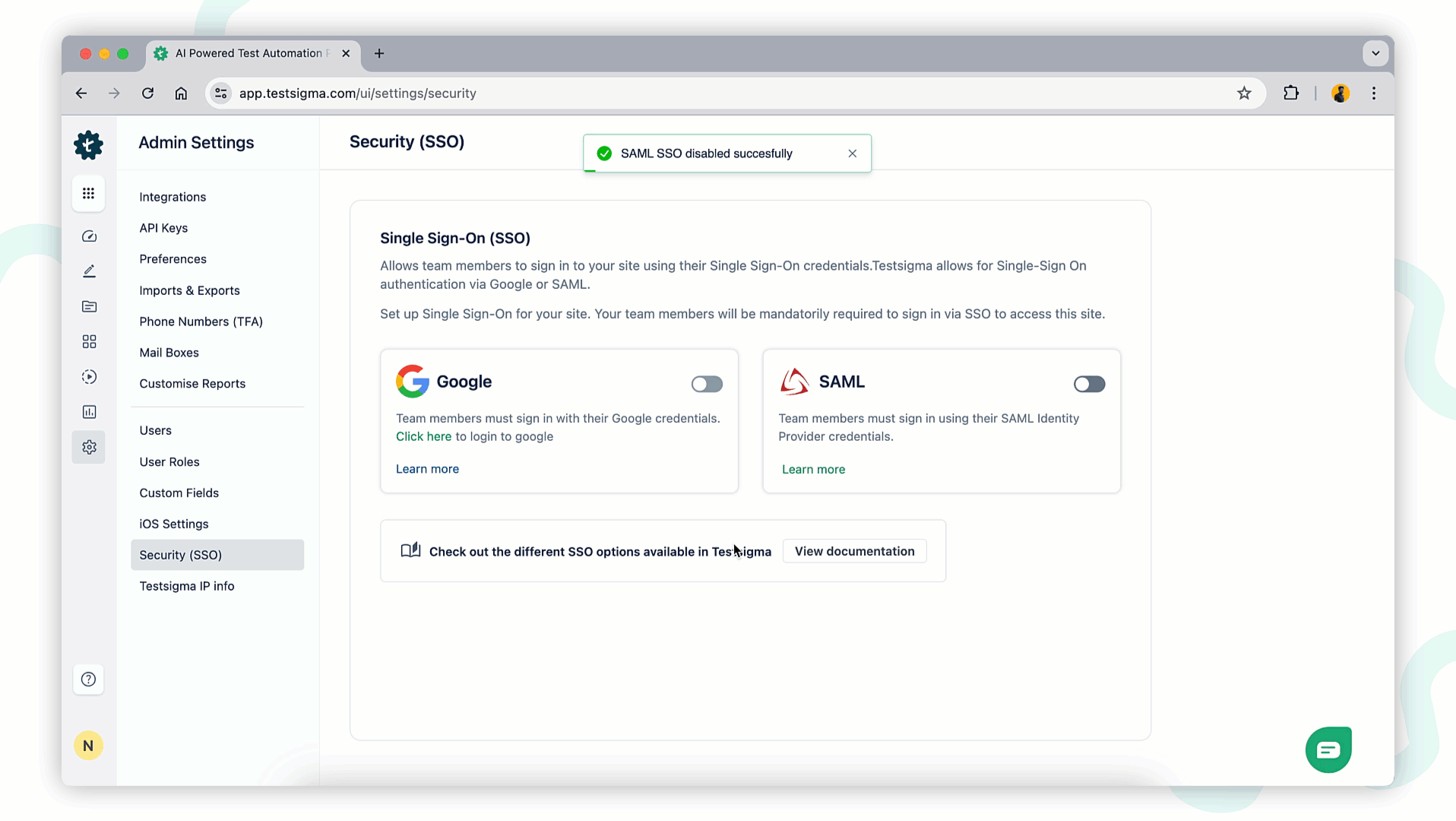
-After this, every user in your account would need to log in to Testsigma via the Okta Dashboard once logged out from the current session.
\ No newline at end of file
+---
\ No newline at end of file