-
Notifications
You must be signed in to change notification settings - Fork 278
4.3.0 Upgrade Guide
We added new features to the Mirth Connect Setup Wizard that include, but are not limited to, the following:
- We added more information on the screens with links to the What's New, Upgrade Guide, and documentation. This helps users understand what options to enter on the screens.
- We added the ability to install your extensions at the time Mirth Connect is installed or upgraded. This simplifies the process so that users no longer have to install extensions manually and restart the service.
- We added the ability to enter your license key for extensions. This will default to the
license.keyvalue from yourmirth.propertiesfile during an upgrade. - We added our new logo and a list of each dialog screen so that users know exactly where they are in the process.
Resources now load classes "child-first" instead of "parent-first" by default. In cases where a resource uses a class that is already included with Mirth Connect (for example a PostgreSQL driver), previously the class from the parent classloader was loaded instead of the custom class that the user wanted to use. By loading "child-first" now, users can achieve the desired behavior.
If you still need to load "parent-first", you can enable the "Load Parent-First" option on individual resources.
The OpenJDK and AdoptOpenJDK base images were deprecated, so we now build Mirth Connect with the eclipse-temurin image instead. If you were customizing your Mirth Connect Docker containers, you may need to update your configuration to be compatible with eclipse-temurin. Additionally, all images are now built using Java 17.
The default encryption algorithm has been updated from AES to AES/CBC/PKCS5Padding. In addition, before being encrypted, strings will be encoded using UTF-8 instead of the JVM default charset.
-
If you did not have
encryption.algorithmalready overridden in mirth.properties, then no action is required. Any newly encrypted data will just use the new default algorithm, and old encrypted data will still be able to be decrypted (using the old default algorithm). -
If you had
encryption.algorithmoverridden and set toAES, then you should consider updating that, for example toAES/CBC/PKCS5PaddingorAES/GCM/NoPadding. Mirth Connect will warn you on startup with this message as well. Support forAES(without any mode/padding specified) will be removed in a future version.
Default TLS cipher suites have been updated. Weaker, potentially exploitable cipher suites have been disabled as a best practice.
The following cipher suites have been disabled:
- TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA384
- TLS_ECDH_ECDSA_WITH_AES_256_CBC_SHA384
- TLS_ECDH_RSA_WITH_AES_256_CBC_SHA384
- TLS_DHE_DSS_WITH_AES_256_CBC_SHA256
- TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA
- TLS_ECDH_ECDSA_WITH_AES_256_CBC_SHA
- TLS_ECDH_RSA_WITH_AES_256_CBC_SHA
- TLS_DHE_DSS_WITH_AES_256_CBC_SHA
- TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA256
- TLS_RSA_WITH_AES_128_CBC_SHA256
- TLS_ECDH_ECDSA_WITH_AES_128_CBC_SHA256
- TLS_ECDH_RSA_WITH_AES_128_CBC_SHA256
- TLS_DHE_DSS_WITH_AES_128_CBC_SHA256
- TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA
- TLS_ECDH_ECDSA_WITH_AES_128_CBC_SHA
- TLS_ECDH_RSA_WITH_AES_128_CBC_SHA
- TLS_DHE_DSS_WITH_AES_128_CBC_SHA
If you had updated your https.ciphersuites in mirth.properties previously, you will see a https.ciphersuites.old property which contains your previous values. If you had not updated https.ciphersuites then https.ciphersuites will have been updated removing the cipher suites above.
If any of your connectors, either connecting to external servers, or allowing clients to connect were using these older cipher suites then it is possible they may fail a TLS handshake after upgrading to 4.3.0.
If you encounter a TLS handshake error after upgrading it is best to let the external entity know they need to switch to a more secure cipher suite.
If this is not possible:
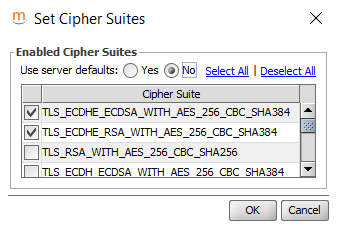
If you are using the SSL Manager commercial extension, you can select a weaker cipher suite for the connector(s) which need to allow these weaker legacy cipher suites.
If you are not using the SSL Manager commercial extension, you can manually add back any of the cipher suites removed above to your https.ciphersuites property (in mirth.properties) to restore previous, less secure, behavior for all of your connectors.
We removed the View User Guide option from the Other menu. The Help option will continue to navigate to docs.nextgen.com to allow access to our new online documentation tool.
Mirth Connect 4.3.0 is signed with an updated certificate, so you will need to update the Administrator Launcher to the latest version, 1.3.1, to avoid seeing security warnings.
- Home
- Frequently Asked Questions
- Source Code Contribution
- Java Licensing
- How to Contribute to the Wiki
- Administrator Launcher (MCAL)
-
Mirth Connect
-
Release Notes
- 4.5.0 - What's New
- 4.4.0 - What's New
- 4.3.0 - What's New
- 4.2.0 - What's New
- 4.1.0 - What's New
- 4.0.0 - What's New
- 3.12.0 - What's New
- 3.11.0 - What's New
- 3.10.0 - What's New
- 3.9.0 - What's New
- 3.8.0 - What's New
- 3.7.0 - What's New
- 3.6.0 - What's New
- 3.5.0 - What's New
- 3.4.0 - What's New
- 3.3.0 - What's New
- 3.2.0 - What's New
- 3.1.0 - What's New
- 3.0.0 - What's New
- Upgrading
-
Release Notes
- User Guide
- Commercial Extensions
- Examples and Tutorials