Add summary, submit sources correctly #12
Merged
Add this suggestion to a batch that can be applied as a single commit.
This suggestion is invalid because no changes were made to the code.
Suggestions cannot be applied while the pull request is closed.
Suggestions cannot be applied while viewing a subset of changes.
Only one suggestion per line can be applied in a batch.
Add this suggestion to a batch that can be applied as a single commit.
Applying suggestions on deleted lines is not supported.
You must change the existing code in this line in order to create a valid suggestion.
Outdated suggestions cannot be applied.
This suggestion has been applied or marked resolved.
Suggestions cannot be applied from pending reviews.
Suggestions cannot be applied on multi-line comments.
Suggestions cannot be applied while the pull request is queued to merge.
Suggestion cannot be applied right now. Please check back later.
feat: Add summary of issues that includes the MythX group ID and report UUID:
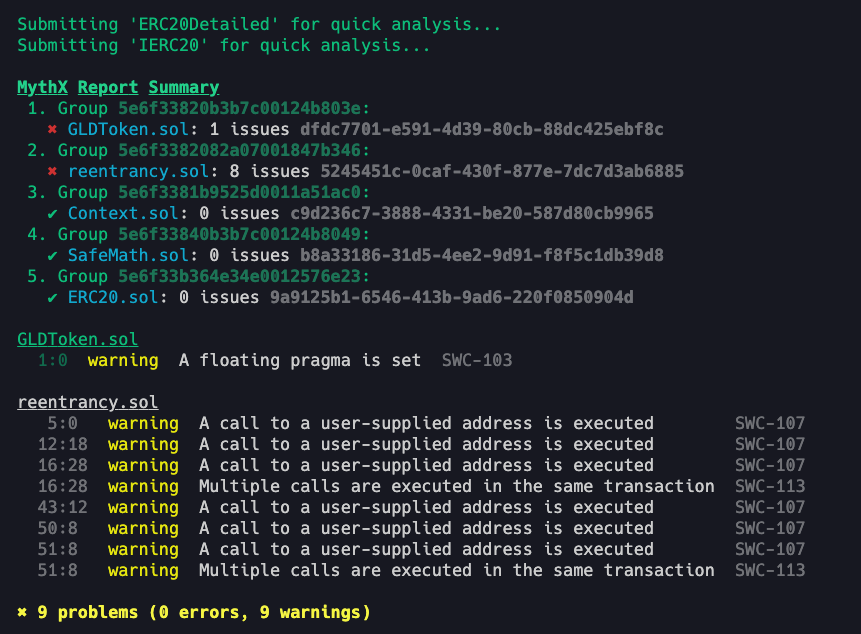
fix: Only source files in the AST are submitted as part of the MythX analysis
Previously, for every contract file submitted to MythX for analysis, all source contract files in the DApp were submitted as part of the MythX analysis job. This PR updates this functionality, such that only source files in the contract's AST are submitted along with the contract file as part of the MythX job. For example, if
ContractAimports and inheritsContractB, when submitting a job to MythX forContractA,ContractBwould also be submitted in that job as as source file ofContractA.If we had two completely mutually exclusive contracts,
ContractAandContract123. WhenContractAis submitted to MythX for analysis, only theContractAsource file will be submitted. Likewise forContract123.Notes
undefinedinstead. I'm not exactly sure what the source of this error is.embark-mythxare not matching those listed in the MythX portal. This was raised in Results inembark-mythxconsole are different than in the MythX portal #10.Testing setup
This PR was tested with the following setup:
OpenZeppelin contracts
Contracts
reentrancy.solcontracts/GLDToken.sol:config/contracts.sol:embark.json: