-
Notifications
You must be signed in to change notification settings - Fork 0
Lab 6. Storage Security
In the previous section, one of the Azure Security Center recommendations is to apply disk encryption to the deployed Virtual Machines. Although the disk image files are encrypted within the Azure Storage Account using Storage Service Encryption as standard, there may be an additional requirement to encrypt the contents of the disk. This is possible using Azure Disk Encryption with the help of Azure Key Vault.
Azure Key Vault is a service which provides a centralised method of securely storing and managing encryption keys, secrets (passwords, tokens, API keys etc) and SSL Certificates. These keys are protected by built-in Azure security controls whilst the system can log access and usage. Further security can be applied by restricting access to the Key Vault to known networks only.
Full details about Azure Key Vault can be found here: https://azure.microsoft.com/en-us/services/key-vault/
Section 6.1.1 covers the creation of a Key Vault using the Azure Portal, whilst section 6.1.2 details the Azure CLI command required to achieve the same objective.
Whichever option is chosen, the following is important when creating a Key Vault:
-
For Azure Disk Encryption to work, the Key Vault and the Virtual Machines must be located in the same Azure region and subscription.
-
The Key Vault name must adhere to the following convention:
- Vault name must only contain alphanumeric characters and dashes and cannot start with a number.
- Vault name must be between 3-24 alphanumeric characters. The name must begin with a letter, end with a letter or digit, and not contain consecutive hyphens.
Create a new Key Vault from the portal following the steps below:
-
In the Azure Portal, click on Create a resource from the side panel (it is typically at the very top).
-
On the New panel, enter Key Vault in the Search the Marketplace field. The option Kay Vault should pre-populate as you type. Select this option.
-
Click Create on the next screen to begin the creation process.
-
Complete the Create key vault screen with details similar to those shown below (the Key Vault Name must be unique to be valid within Azure DNS services), selecting the relevant subscription, Resource Group etc.
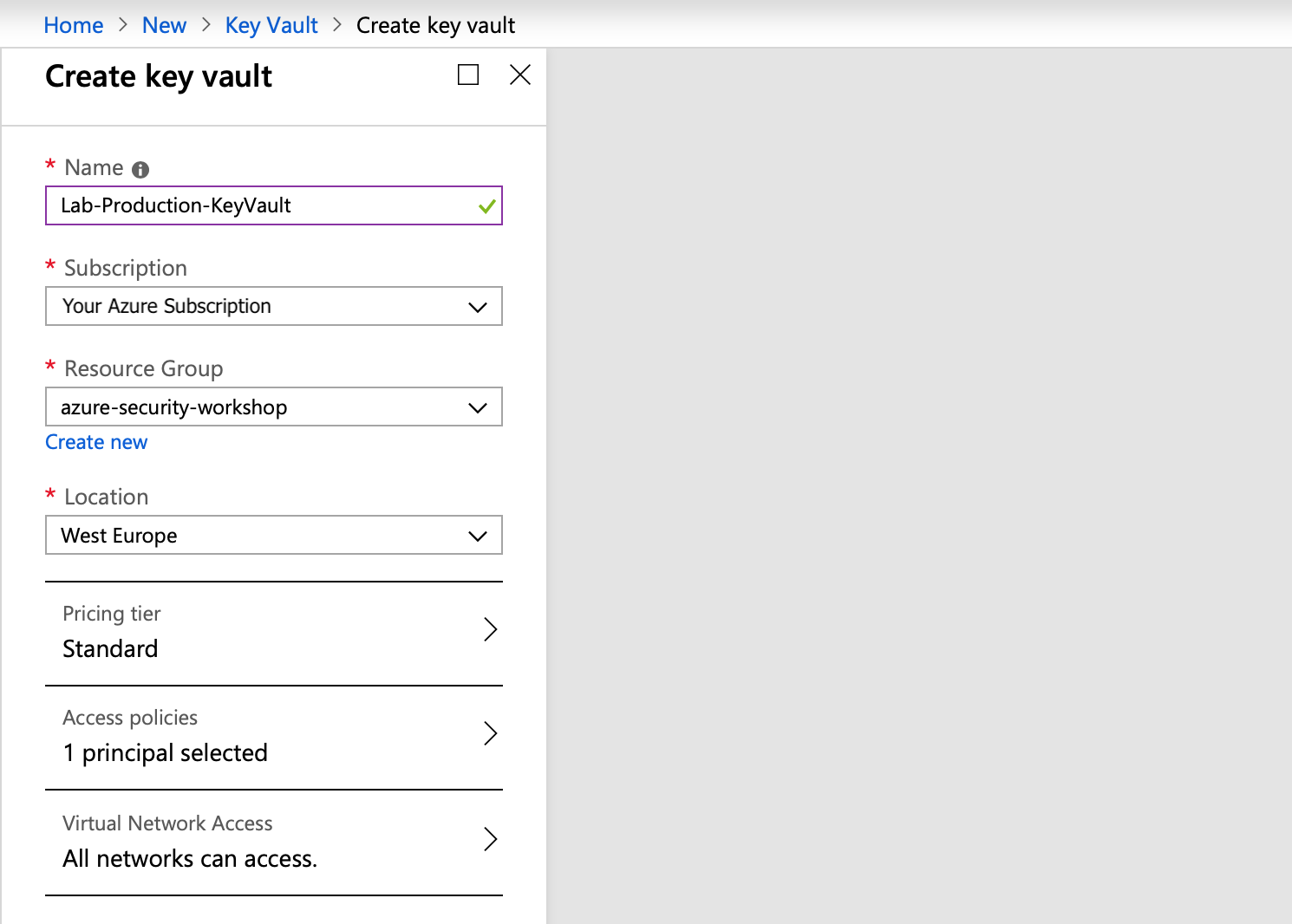
Deployment of a Key Vault should take less than a minute.
Proceed to step 6.2
In the Azure Cloud Shell, ensure the shell is set to Bash and use the following command to create the Key Vault:
Parameters:
- --resource-group: The resource group used throughout the workshop
- --name: This is the name given to the new Key Vault. Ensure the naming standards shown above are followed
- --sku: Determines the pricing model used for the Key Vault. Use standard
- --location: The region the Application Gatway will be created in. Enter westeurope
Command:
az keyvault create --resource-group <resource-group-name> --name <new-keyvault-name> --sku standard --location westeuropeDisk encryption is enabled by using a template, PowerShell cmdlets, or CLI commands. This section explains in detail how to enable Azure Disk Encryption, and some of the steps required to prepare the Azure environment for this task.
For a full description of the prerequisites for Azure Disk Encryption, including supported operating systems, please visit the Microsoft documentstion:
https://docs.microsoft.com/en-us/azure/security/azure-security-disk-encryption-prerequisites
The Azure platform needs access to the encryption keys or secrets in the Key Vault to make them available to the Virtual Machine for booting and decrypting the volumes. Enable disk encryption on the Key Vault otherwise the encryption will fail.
Using the Azure CLI
The az keyvault update command is used together with the enabled-for-disk-encryption parameter
az keyvault update --name <key-vault-name> --resource-group <resource-group-name> --enabled-for-disk-encryption "true"When the command runs, scroll back through the properties of the Key Vault and check for the enabledForDiskEncryption property, which should be set to true.
Setting the properties via the Azure Portal
To view or set the advanced access policies in the Azure Portal:
-
Navigate to your Key Vault resource, and under Settings, click on Access Policies.
-
On the Access Policies pane, click the link labelled Click to show advanced access policies.
- Tick the box labeled Enable access to Azure Disk Encryption for volume encryption, then click Save.
Before encrypting the disk, verify the encryption state of the WebServer-01 disk in the Azure Portal by calling up the properties of the Virtual Machine, and under Settings, click Disks. The operating system disk encryption should be listed as Not enabled.
Alternatively, running the az vm encryption CLI command against the Web Server will bring back the same result: Azure Disk Encryption is not enabled
Enter the command as follows:
az vm encryption show --name WebServer-01 --resource-group <resource-group-name>
IMPORTANT: Ensure that the Web Server is running. The Virtual Machine must be running when applying disk encryption.
-
Run the encryption command as follows, replacing the
--resource-groupand--disk-encryption-keyvaultparameters with the Resource Group and the Key Vault name respectively...az vm encryption enable --resource-group <resource-group-name> --name "WebServer-01" --disk-encryption-keyvault <key-vault-name> --volume-type OS -
Once the disk has been encrypted, the command prompt will reappear. Without needing to go and check the disk resource in the Azure Portal, the disk encryption status (together with other useful information) can be obtained from the command line.
Run the following command...
az vm encryption show --name WebServer-01 --resource-group <resource-group-name>The command returns the information about the server disk encryption:
{ "disks": [ { "encryptionSettings": [ { "diskEncryptionKey": { "secretUrl": "https://lab-production-keyvault.vault.azure.net/secrets/391A81D8-8100-4B23-8C30-3A6647A50FCC/3733aa08dfa3412ea3d9864344a9b628", "sourceVault": { "id": "/subscriptions/xxxxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxx/resourceGroups/azure-security-workshop/providers/Microsoft.KeyVault/vaults/Lab-Production-KeyVault" } }, "enabled": true, "keyEncryptionKey": null } ], "name": "WebServer-01-OSDisk", "statuses": [ { "code": "EncryptionState/encrypted", "displayStatus": "Encryption is enabled on disk", "level": "Info", "message": null, "time": null } ] } ], "status": [ { "code": "ProvisioningState/succeeded", "displayStatus": "Provisioning succeeded", "level": "Info", "message": "", "time": null } ], "substatus": null }Interesting points to note in this output text are the following values:
-
encryptionSettings shows the new encryption key used to encrypt this disk. Notice that the URL points to a value in the Key Vault previously created. This is where the new key has been stored.
-
statuses shows the displayStatus as
Encryption has been enabled on disk
-
In the Azure Portal, revisit the recommendations given by Azure Security Center. Once it has updated (this may need a little time), the recommendations panel we will no longer provide the recommendation on the Web Server Virtual Machine to apply disk encryption.