-
Notifications
You must be signed in to change notification settings - Fork 435
uBlock and others: Blocking ads, trackers, malware
Hard data.
Latest benchmark: 16 February 2015 (raw data spreadsheet).
Previous benchmarks: 2014-09-30, 2014-07-22
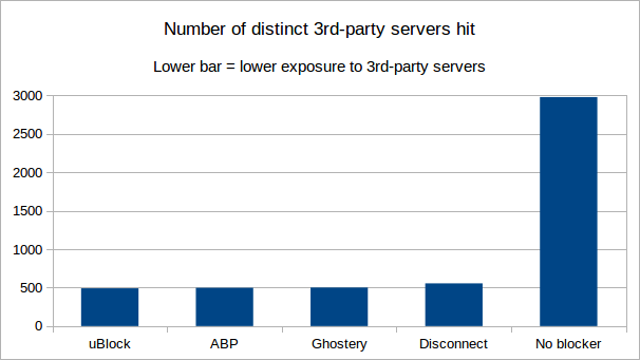
This benchmark is to measure privacy exposure, by counting the number of distinct 3rd-party domains which have been hit by net requests during the benchmark. The lower the number of distinct 3rd-party domains hit, the better.
Some benchmarks measure the amount of requests blocked, which is of little value as a useful measure of privacy exposure. The number of requests blocked is no guarantee of less distinct 3rd-party domains being hit (and leaving a trace in the servers' logs).
Measuring the number of distinct 3rd-party domains which were hit is a more relevant measurement for comparison of privacy protection efficiency.
Caveat: "3rd-party" is defined as a domain which doesn't match the domain of the web page. Many
domains reported as "3rd-party" actually belong to the same entity which owns the page domain (for example, yimg.com is owned by yahoo.com). There is no easy way for the benchmark code to know this, unless using a database of who owns which domain. Although not perfect, the benchmark is useful when comparing blockers among themselves and versus the absence of a blocker.
The URLs (84) from the reference benchmark were used.
Results -- figures are "3rd party / all". Ordered from least 3rd-party hits to most 3rd-party hits. Privacy-wise, lower numbers are better.
- Distinct 1st-party/3rd-party pairs: 491
- Scripts: 980 / 1635
- Outbound cookies: 58 / 269
- Net requests: 3,987 / 7,956
- Distinct 1st-party/3rd-party pairs: 497
- Scripts: 1009 / 1733
- Outbound cookies: 67 / 284
- Net requests: 4,069 / 8,166
- Distinct 1st-party/3rd-party pairs: 501
- Scripts: 882 / 1619
- Outbound cookies: 120 / 370
- Net requests: 4,031 / 8,218
- Distinct 1st-party/3rd-party pairs: 555
- Scripts: 1186 / 1685
- Outbound cookies: 130 / 382
- Net requests: 4,462 / 8,219
- Distinct 1st-party/3rd-party pairs: 2977
- Scripts: 3800 / 4647
- Outbound cookies: 1641 / 2097
- Net requests: 12,131 / 16,851
The figures show the number of requests allowed, thus lower numbers are better. The point is to count the number of distinct 3rd-party/1st-party pairs after running the reference benchmark (repeated twice in the same instance).
The less distinct 3rd-party/1st-party pairs, the better.
This shows the differences in what was not blocked. If something appears on side A but not on side B, this mean side B blocked something not blocked by side A, and vice versa.
- uBlock/ABP: https://www.diffchecker.com/czy6h5lq
- uBlock/Ghostery: https://www.diffchecker.com/zapbh5b9
- uBlock/Disconnect: https://www.diffchecker.com/386c367m
These diffs may help you in deciding whether you should complement uBlock with another blocker, though keep in mind, you can always ask uBlock to block more (dynamic filtering can be handy for this).
Using the data diffs, one can observe that with uBlock + default settings, there are large areas of privacy exposure related to:
-
facebook.net(45) -
facebook.com(44) -
googletagservices.com(39) -
twitter.com(34) -
taboola.com(11)
If this concerns you, the best way to block these is to use dynamic filtering. Here are the rules which can block all these 3rd-parties, except when used as a 1st-party:
* facebook.com * block
* facebook.net * block
* googletagservices.com * block
* taboola.com * block
* twitter.com * block
facebook.com facebook.com * noop
facebook.com facebook.net * noop
twitter.com twitter.com * noop
With these few dynamic filtering rules, you would lower the "distinct 1st-party/3rd-party pairs" figure for uBlock to 318 (from 491). As a bonus, pages will load markedly faster.
Any of the blocked domains above can easily be unblocked for a specific site. For example, if you ever want Twitter widgets to work when visiting AnandTech, just set twitter.com to a local noop for that site (quickly achieved with a point-and-click when using the dynamic filtering matrix).
All blockers were configured in such a way as to compare apples-vs-apples:
- Ghostery: Select all trackers except "Widgets". "GhostRank" not checked. "Update now" clicked (and ensured whatever new filters were used).
- uBlock: Out-of-the-box settings -- no change.
- Adblock Plus: "EasyList" + "EasyPrivacy", "Peter Lowe's list", "Malware Domains" checked. "Acceptable ads" unchecked. "Update now" clicked.
- Disconnect: Out-of-the-box settings -- no change.
Browser settings (if you mind your privacy, there is no way around these settings):
- "Click to play" enabled.
The tester (gorhill) forgot to check "Block third party cookies and site data", so 3rd-party cookies were allowed during the benchmark.
Sessbench was used to run the benchmarks, and each extension was tested as the only active extension in the browser.
The official Public Suffix List was used to determine the domain of a URL.
###Removing Experimental Bias
Although these benchmarks are useful to see "out of the box" blocking functionality, adding more filter lists to any blocking tool will give it better results. These tests were conducted with "out of the box" filters, and uBlock happens to include many default filter lists.
Configuring other blocking tools with the same lists would likely generate the same results as uBlock. Consequently, the benchmarks are only valid for people that use the default lists and choose not to add other lists or filters.
A real advantage that uBlock may have is that it can use host files. Host files, however, have their pros and cons: they are easy to create, but they have a tendency to break sites because they do not offer the granularity available in other types of filtering lists.