-
Notifications
You must be signed in to change notification settings - Fork 139
Configuring Randomized Validity
Randomizing validity is one of the methods allowing to add entropy to certificates in order to make it more difficult attacks on cryptographic hashes. RFC 4270 (written by P. Hoffman and B. Schneier) provides three suggestions to reduce the likelihood of hash-based attacks:
-
making part of the certificate serial number unpredictable to the attacker
-
adding a randomly chosen component to the identity
-
making the validity dates unpredictable to the attacker by skewing each one forwards or backwards
CA’s profile framework is based on plug-ins. One type of the plug-ins is responsible for setting defaults and verifying constraints for in the process of populating validity. Simple replacement of validity plug-in in a profile with new one randomizing validity allows to generate certificates with randomized validity when using enrollment with modified profile.
Process of profile editing in order to replace validity plug-in is described below.
Typical certificate profile configuration includes section configuring ValidityDefault and ValidityConstraint plug-ins.
Sample below shows default configuration included in caUserCert profile (/usr/share/pki/ca/profiles/ca/caUserCert.cfg).
ValidityDefault plug-in configuration in caUserCert.cfg:
... policyset.userCertSet.2.default.class_id=validityDefaultImpl policyset.userCertSet.2.default.name=Validity Default policyset.userCertSet.2.default.params.range=180 policyset.userCertSet.2.default.params.startTime=0 ...
ValidityConstraint plug-in configuration in caUserCert.cfg:
... policyset.userCertSet.2.constraint.class_id=validityConstraintImpl policyset.userCertSet.2.constraint.name=Validity Constraint policyset.userCertSet.2.constraint.params.notAfterCheck=false policyset.userCertSet.2.constraint.params.notBeforeCheck=false policyset.userCertSet.2.constraint.params.notBeforeGracePeriod=0 policyset.userCertSet.2.constraint.params.range=365 ...
Profile needs to be disabled to initiate profile editing.
Here are sample steps:
-
Selecting
caUserCertprofile (Manual User Dual-Use Certificate Enrollment)
-
Disabling
caUserCertprofile (Manual User Dual-Use Certificate Enrollment):
Disabled profile can be edited.
Here are sample steps:
-
Selecting
caUserCertprofile for editing
-
Editing
caUserCertprofile
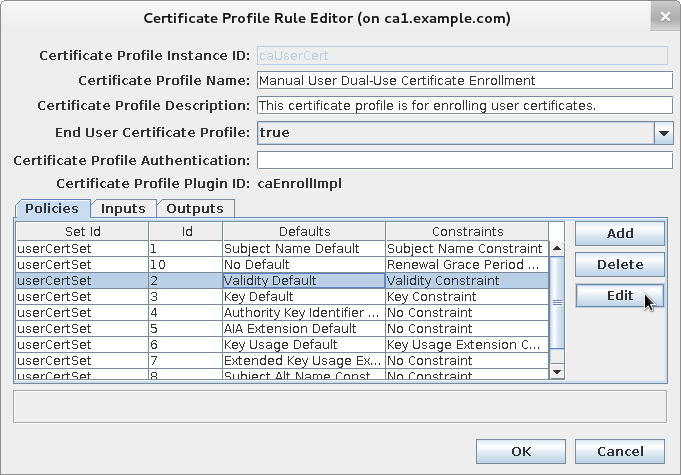
Review current validity configuration before replacing it with randomized validity plug-in.
Here are sample steps:
-
Check current validity defaults
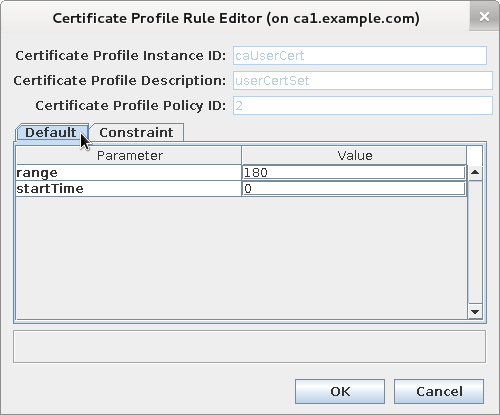
-
Check current validity constraints
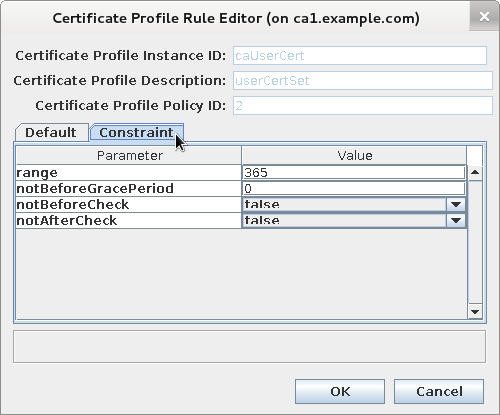
Delete current validity plug-in.
Here are sample steps:
-
Select current validity plug-in
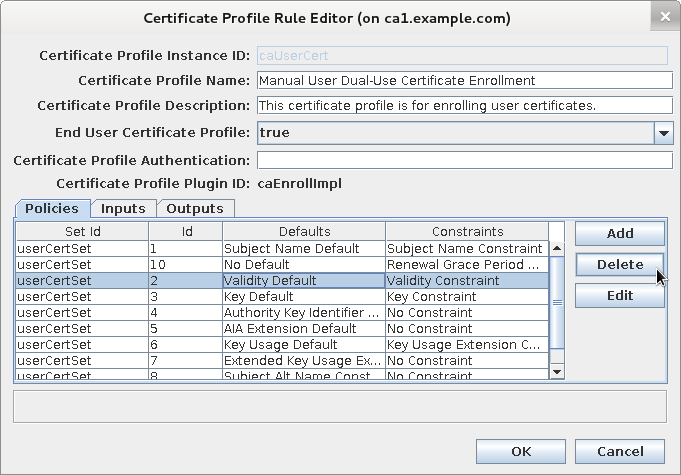
-
Confirm validity plug-in removal
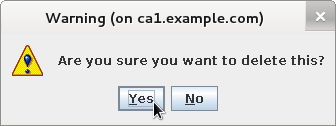
-
Check if validity plug-in was deleted.
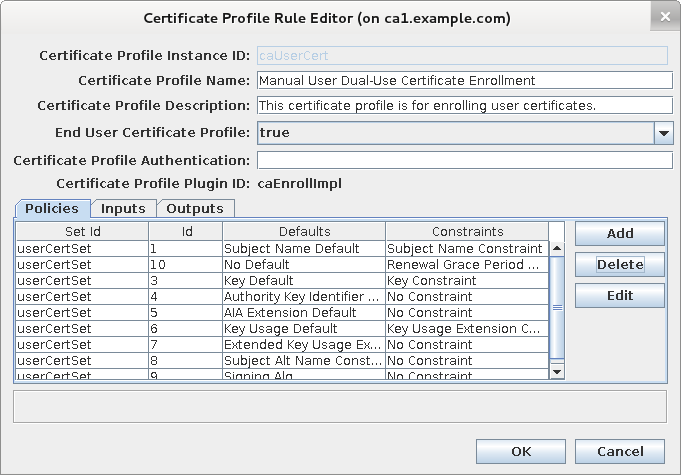
Add randomized validity plug-in.
Here are sample steps:
-
Press add button in profile editor
-
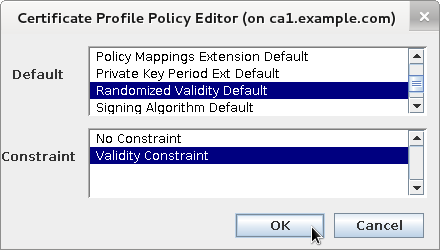
Select "Randomized Validity Default" and "Validity Constraint"
-
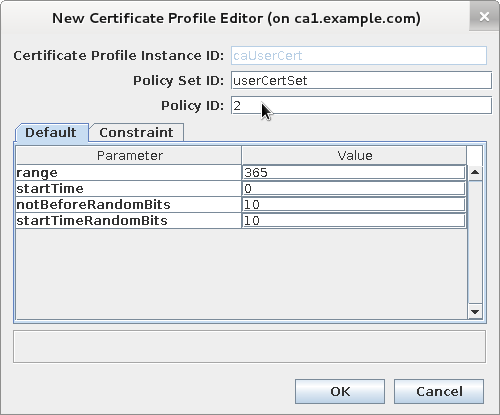
Enter "Policy ID"
-
Update "Validity Default" configuration
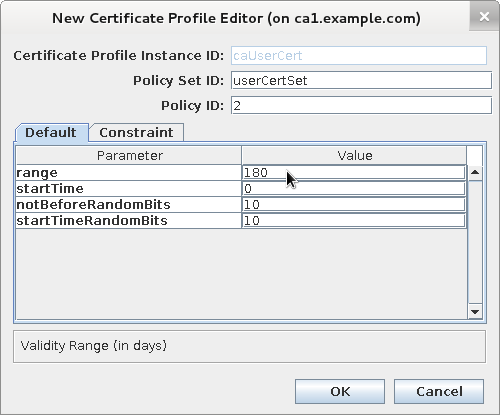
-
Update "Validity Constraint" configuration and save configuration updates
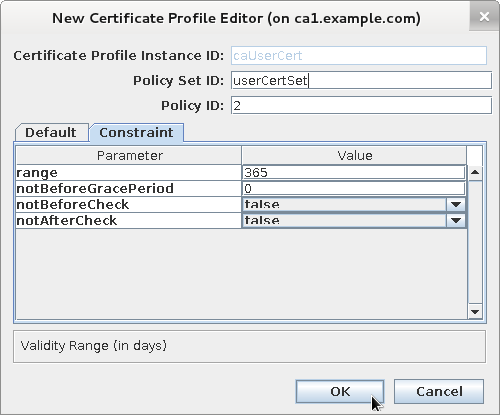
-
Check new randomized validity plug-in
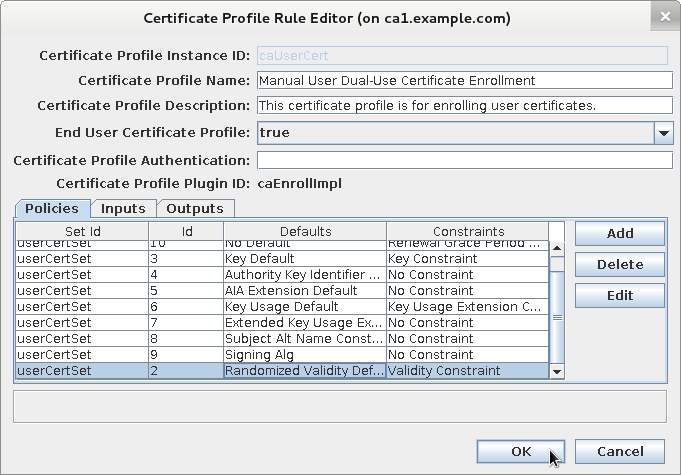
-
Select
caUserCertprofile (Manual User Dual-Use Certificate Enrollment)

-
Approve update
caUserCertprofile (Manual User Dual-Use Certificate Enrollment)
Sample below shows updated caUserCert profile configuration including randomized validity plug-in;
policyset.userCertSet.2.default.class_id=randomizedValidityDefaultImpl policyset.userCertSet.2.default.name=Randomized Validity Default policyset.userCertSet.2.default.params.notBeforeRandomBits=10 policyset.userCertSet.2.default.params.range=180 policyset.userCertSet.2.default.params.startTime=0 policyset.userCertSet.2.default.params.startTimeRandomBits=10
|
Tip
|
To find a page in the Wiki, enter the keywords in search field, press Enter, then click Wikis. |