-
Notifications
You must be signed in to change notification settings - Fork 135
Rotating KRA Transport Key
KRA transport key and certificate generation is part KRA Transport Key Rotation process.
Here is the manual process for KRA transport certificate generation and KRA configuration update.
-
Stop KRA
$ systemctl stop [email protected]
-
Go to KRA’s NSS database directory
$ cd /var/lib/pki/pki-tomcat/conf/alias
-
Create subdirectory
$ mkdir saved
and save all NSS database files
$ cp *.db saved
-
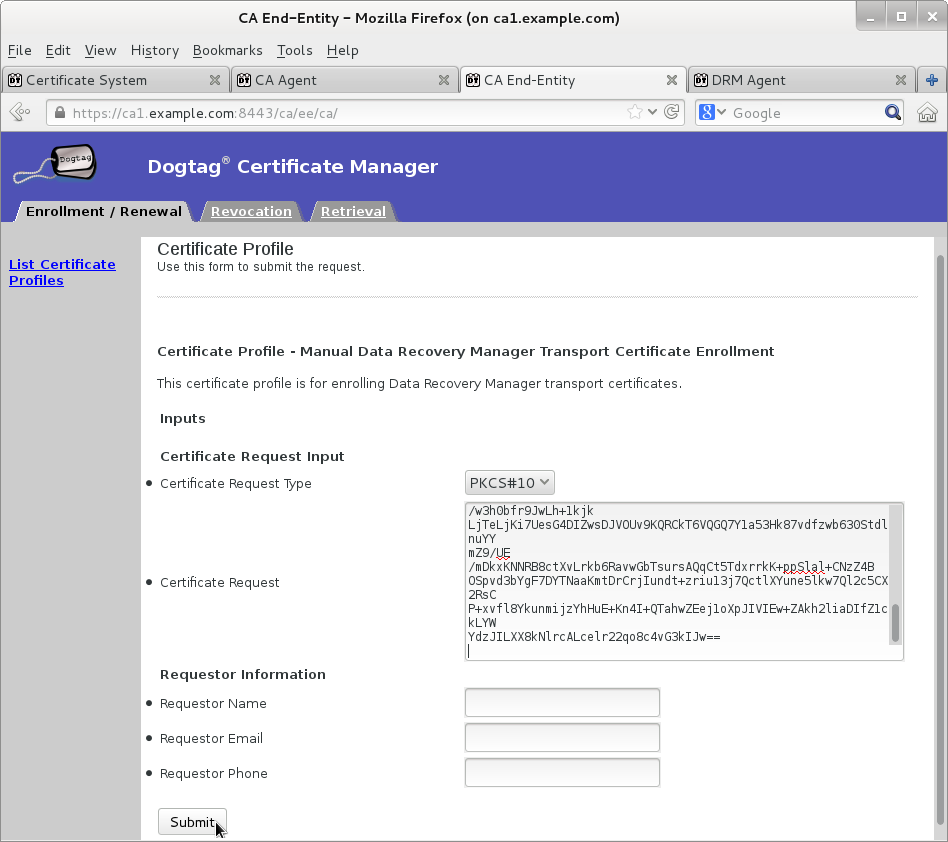
Create new request by running the following command
$ PKCS10Client \
-d . \
-p <password> \
-o req.txt \
-n "CN=DRM Transport 2 Certificate,O=example.com Security Domain"
or
$ certutil -R \
-d . \
-f <password-file> \
-k rsa \
-g 2048 \
-s "CN=DRM Transport 2 Certificate,O=example.com Security Domain" \
-o <transport-certificate-request-file> \
-a
-
Start KRA
$ systemctl start [email protected]
-
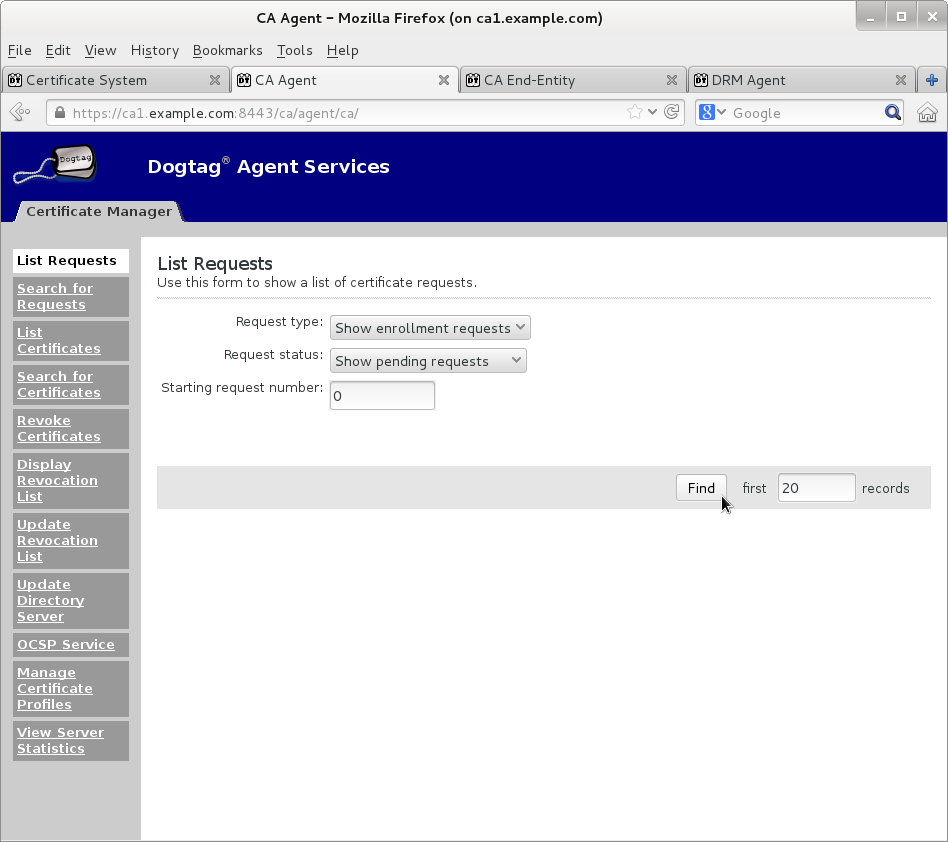
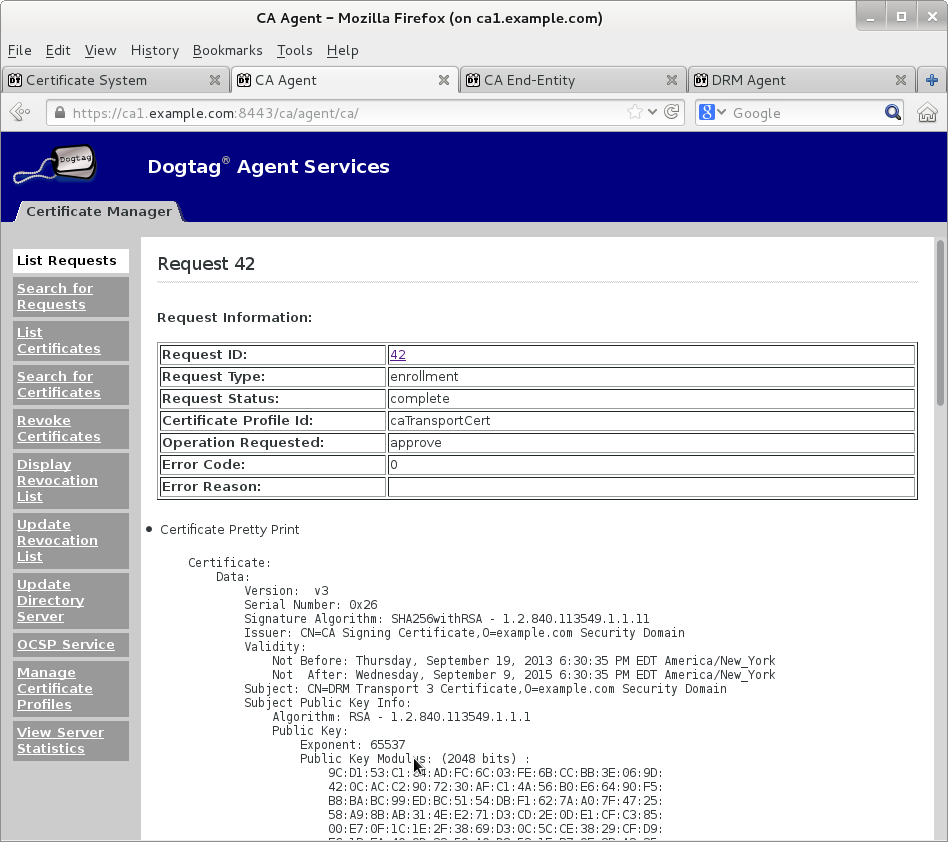
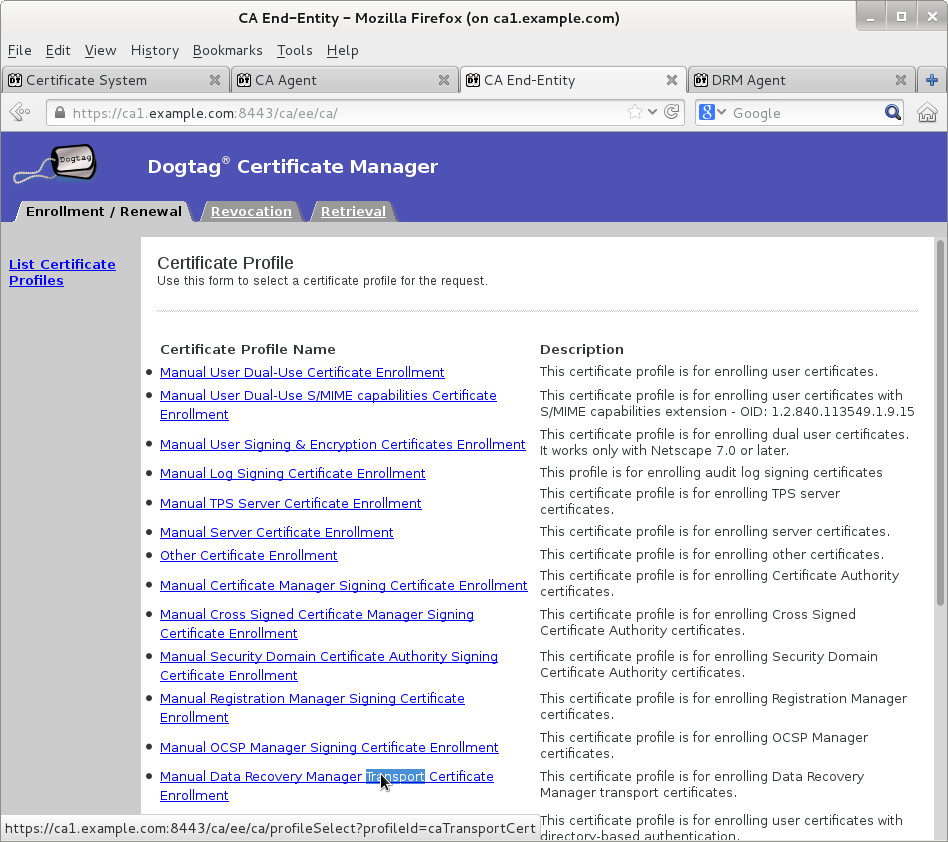
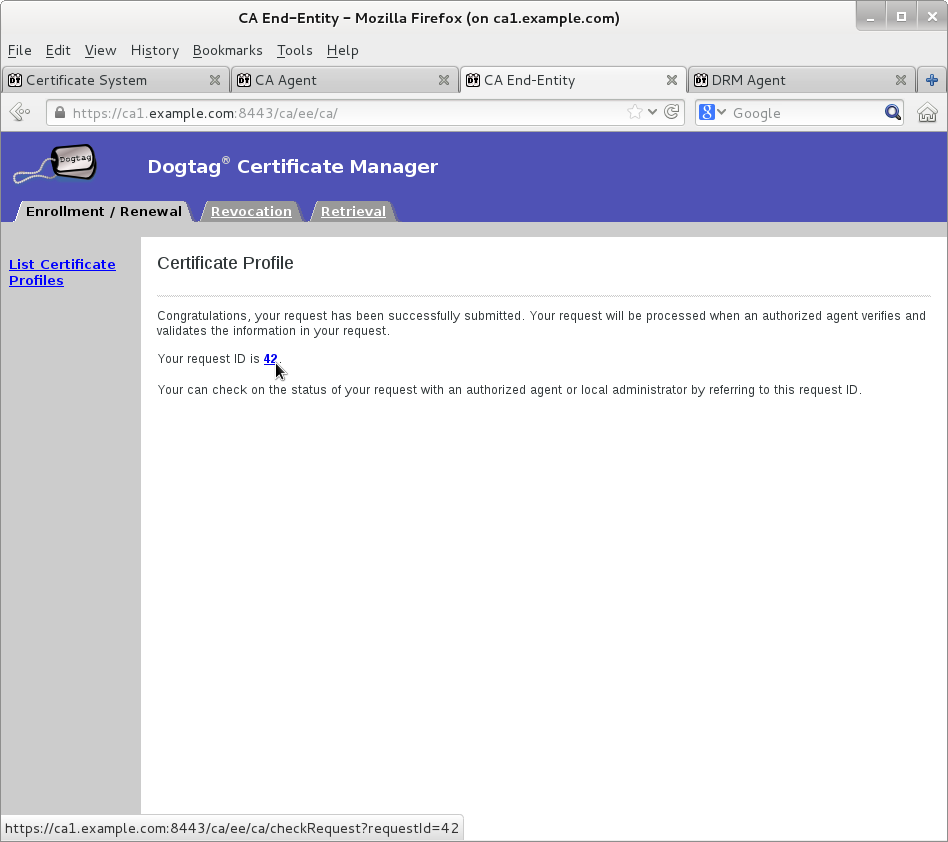
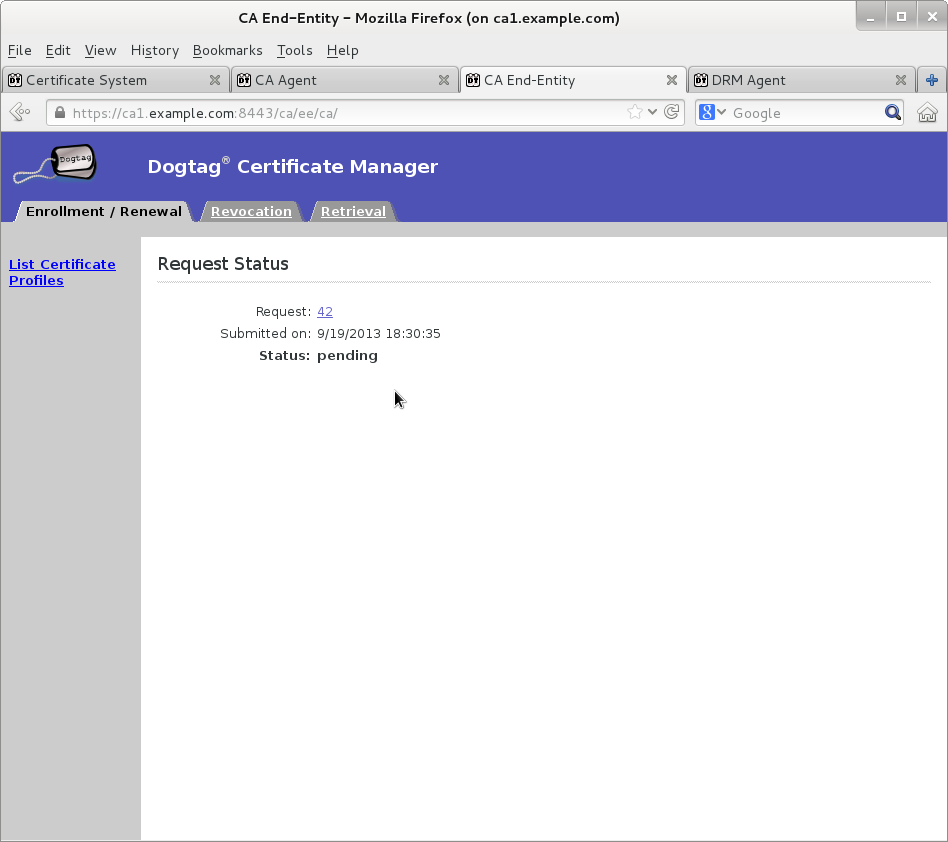
Submit transport certificate request on Manual Data Recovery Manager Transport Certificate Enrollment page
-
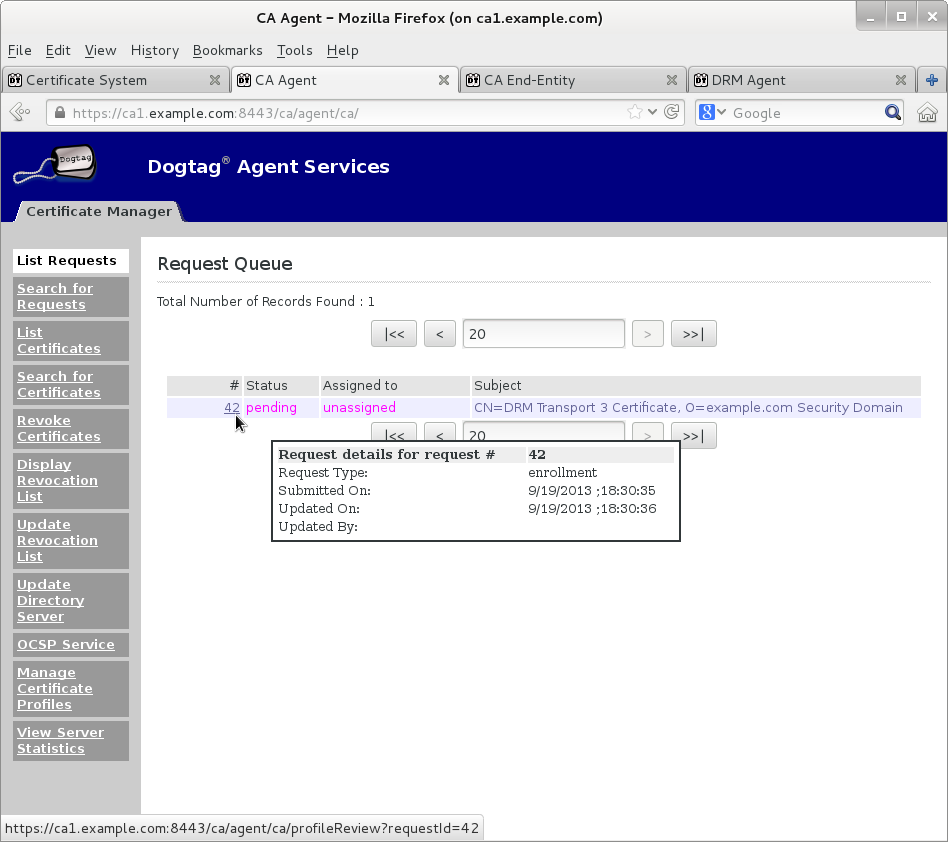
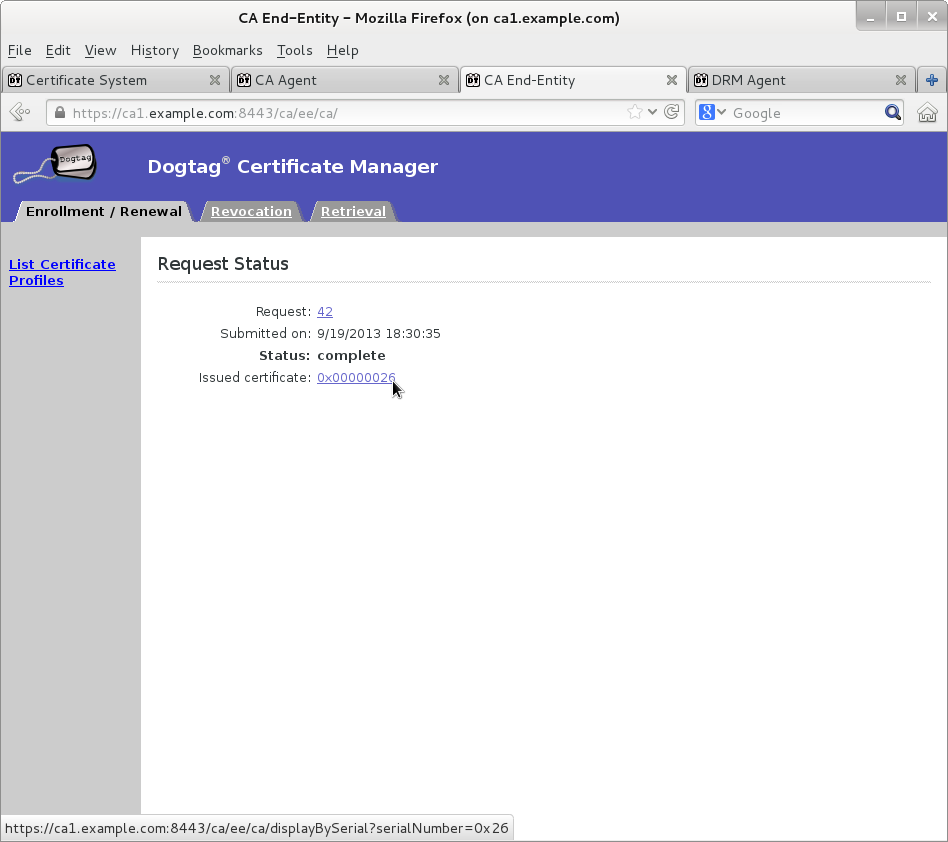
Wait for agent approval of submitted request to retrieve certificate by checking request status on EE retrieval page
-
Go to KRA’s NSS database directory
$ cd /var/lib/pki/pki-tomcat/conf/alias
-
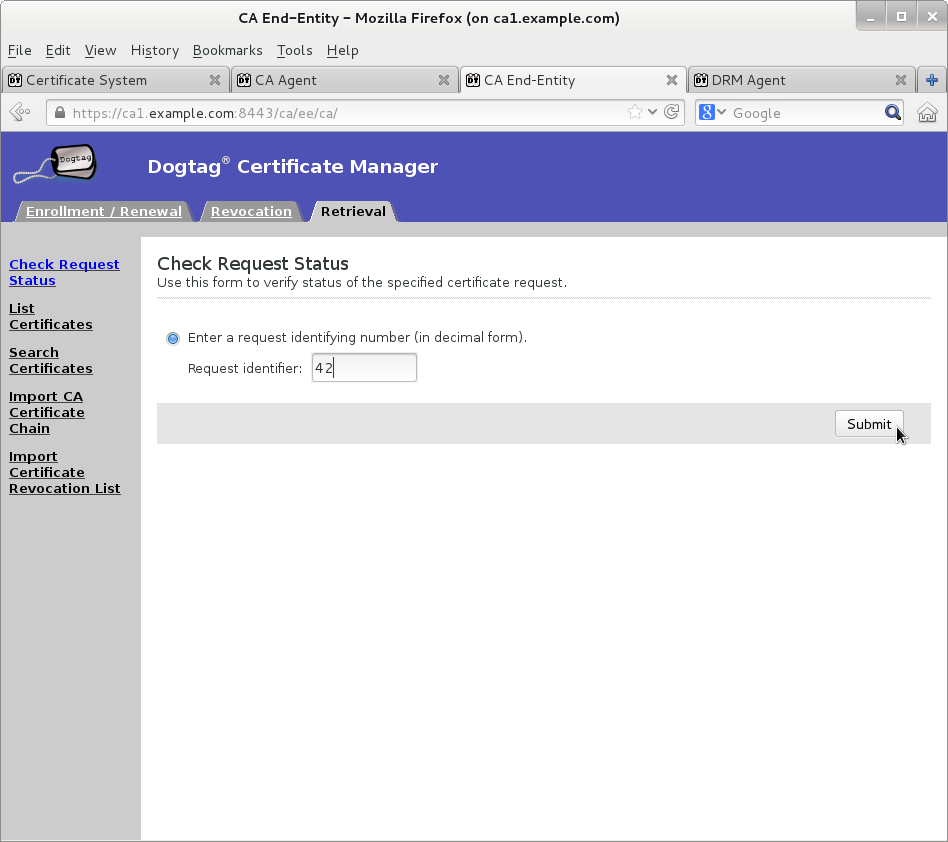
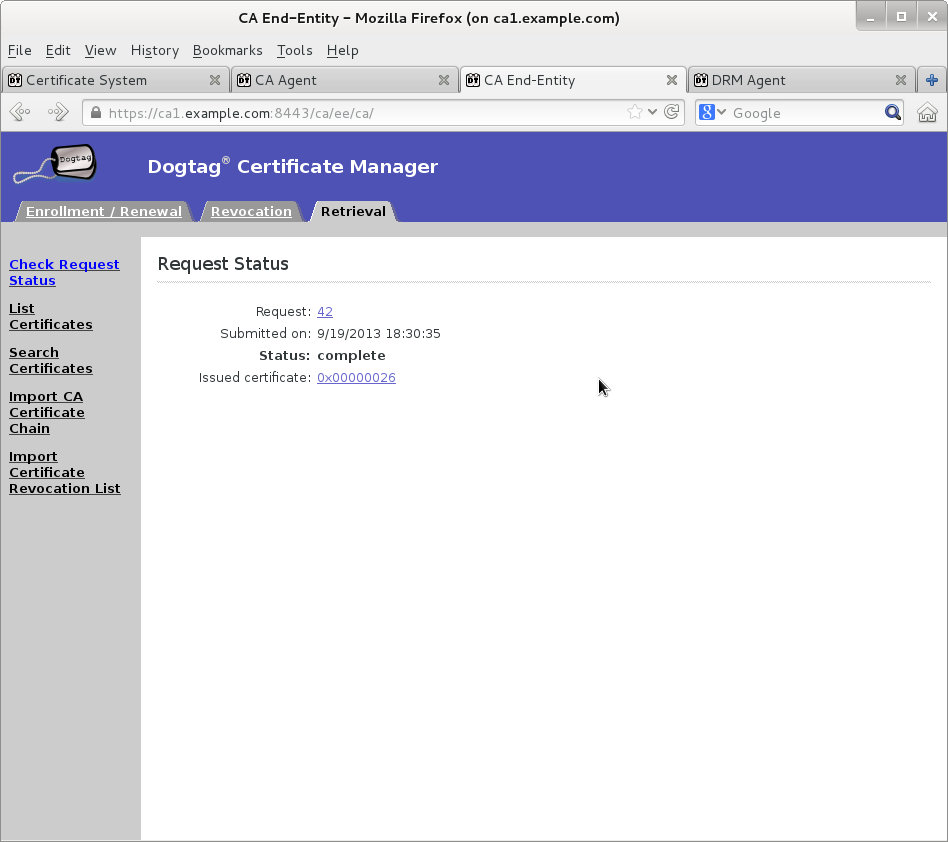
Wait for agent approval of submitted request to retrieve certificate by checking request status on EE retrieval page
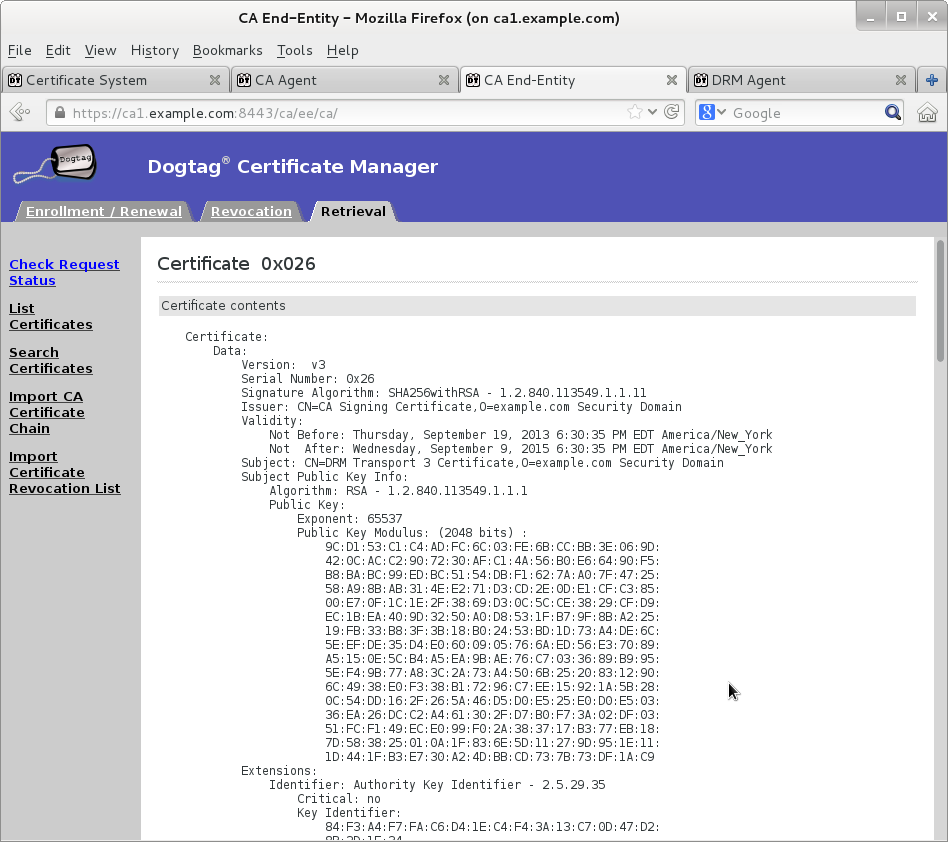
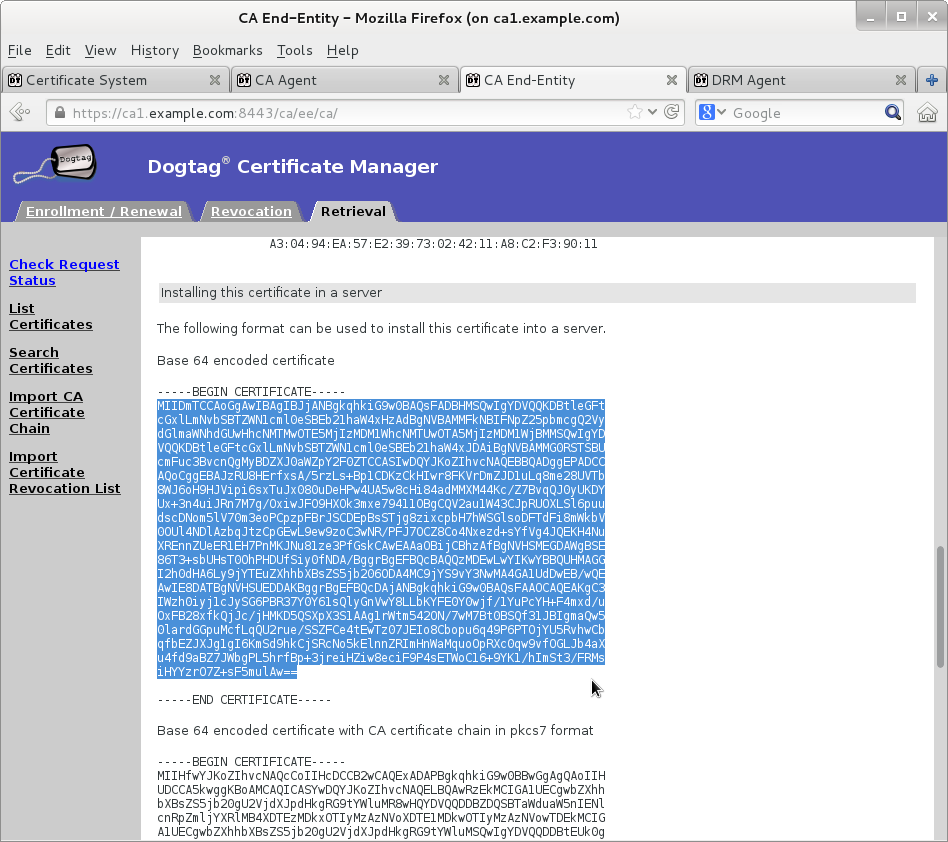
-
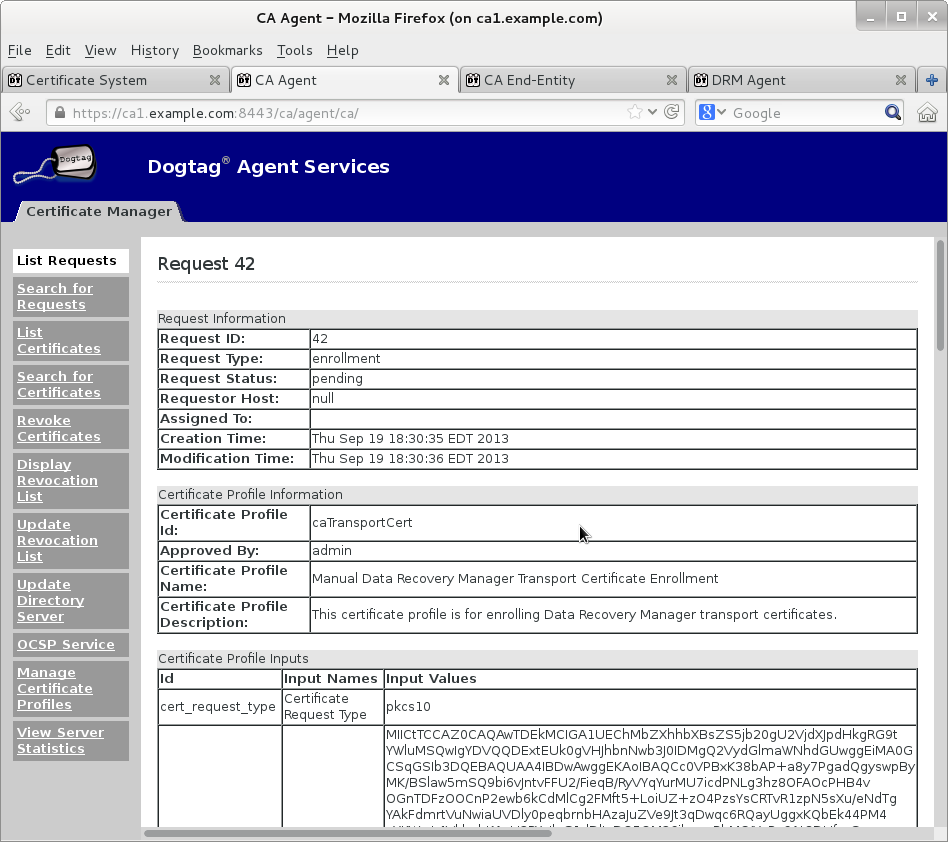
Once new KRA transport certificate certificate is available then paste its base64-encoded value into a text file
cert-<serial-number>.txt. Do not include header-----BEGIN CERTIFICATE-----or footer-----END CERTIFICATE-----.
-
Go to KRA’s NSS database directory
$ cd /var/lib/pki/pki-tomcat/conf/alias
-
Stop KRA
$ systemctl stop [email protected]
-
Import transport certificate into KRA’s NSS database by:
$ certutil -A \
-d . \
-n "transportCert-<serial-number> cert-pki-tomcat KRA" \
-t "u,u,u" \
-i cert-<serial-number>.txt \
-a
-
Go to KRA’s NSS database directory
$ cd /var/lib/pki/pki-tomcat/conf/alias
-
Stop KRA
$ systemctl stop [email protected]
-
Verify if new KRA transport certificate is imported by running
$ certutil -L -d .
followed by
$ certutil -L -d . -n "transportCert-<serial-number> cert-pki-tomcat KRA"
-
Edit
/var/lib/pki/pki-tomcat/kra/conf/CS.cfgto add the following line:
kra.transportUnit.newNickName=transportCert-<serial-number> cert-pki-tomcat KRA
-
Start KRA
$ systemctl start [email protected]
Here is how to transfer new transport key and certificate to KRA clone:
-
Go to KRA’s NSS database directory
$ cd /var/lib/pki/pki-tomcat/conf/alias
-
Stop KRA
$ systemctl stop [email protected]
-
Verify if new KRA transport certificate is present by running
$ certutil -L -d .
followed by
$ certutil -L -d . -n "transportCert-<serial-number> cert-pki-tomcat KRA"
-
Export KRA’s new transport key and certificate by
$ pk12util -o transport.p12 -d . -n "transportCert-021 cert-pki-tomcat KRA"
-
Verify exported KRA’s transport key and certificate by
$ pk12util -l transport.p12
-
Transport
transport.p12file including transport key and certificate to KRA’s clone location. -
Go to clone’s NSS database directory
$ cd /var/lib/pki/pki-tomcat/conf/alias
-
Stop KRA clone
$ systemctl stop [email protected]
-
Check content of clone’s KRA database by running
$ certutil -L -d .
-
Import clone’s new transport key and certificate by
$ pk12util -i transport.p12 -d .
-
Edit clone’s configuration file
/var/lib/pki/pki-tomcat/kra/conf/CS.cfgto add the following line:
kra.transportUnit.newNickName=transportCert-<serial-number> cert-pki-tomcat KRA
-
Start KRA clone
$ systemctl start [email protected]
-
Go to KRA’s NSS database directory
$ cd /var/lib/pki/pki-tomcat/conf/alias
-
Stop KRA
$ systemctl stop [email protected]
-
Verify if new KRA transport certificate is imported by running
$ certutil -L -d .
followed by
$ certutil -L -d . -n "transportCert-<serial-number> cert-pki-tomcat KRA"
-
Edit
/var/lib/pki/pki-tomcat/kra/conf/CS.cfgby replacing nickName included in line
kra.transportUnit.nickName=transportCert cert-pki-tomcat KRA
with newNickName included in line
kra.transportUnit.newNickName=transportCert-<serial-number> cert-pki-tomcat KRA
to obtain
kra.transportUnit.nickName=transportCert-<serial-number> cert-pki-tomcat KRA
-
Edit
/var/lib/pki/pki-tomcat/kra/conf/CS.cfgby removingnewNickNameline
kra.transportUnit.newNickName=transportCert-<serial-number> cert-pki-tomcat KRA
-
Save updated
/var/lib/pki/pki-tomcat/kra/conf/CS.cfg -
Start KRA
$ systemctl start [email protected]
Here is how to update CA configuration with new KRA transport certificate:
-
Stop CA
$ systemctl stop [email protected]
-
Get the KRA transport certificate file
cert-<serial-number>.txtobtained in Ticket #734 comment #2 -
Convert base64-encoded certificate included in
cert-<serial-number>.txtto single line file by
$ tr -d '\n' < cert-<serial-number>.txt > cert-one-line-<serial-number>.txt
-
Edit
/var/lib/pki/pki-tomcat/ca/conf/CS.cfgby replacing certificate included in line
ca.connector.KRA.transportCert=...
with certificate included in cert-one-line-<serial-number>.txt
-
Save updated
/var/lib/pki/pki-tomcat/ca/conf/CS.cfg -
Start CA
$ systemctl start [email protected]
|
Tip
|
To find a page in the Wiki, enter the keywords in search field, press Enter, then click Wikis. |